“Hi! This is Dave from the fulfillment department!” You probably receive calls like that every day – calls that are nothing more than scams. The problem seems to be worsening, but there’s some hope.
Protections exist for cell phones and for most voice over IP (VOIP) systems, but land lines don’t even include caller identification unless you pay extra for it. Increasingly, crooks have found ways to fool caller ID, too. I don’t bother with caller ID on the land line, but it comes without additional charge on most cellular plans.
The federal Do Not Call Registry was created during the early years of the second Bush administration and was intended to enforce the 1991 Telephone Consumer Protection Act. We could add our phone numbers to a federal list and turn off marketing calls. That worked for a while, and still works with honest marketers, but not with scammers who use robocalls to spew their deceitful scams. A few years ago, I told a live scammer that my number was on the Do Not Call list. "How's that working out for ya?" he said. Phone scams are skyrocketing and they cost American consumers billions of dollars each year.
In many ways, the Do Not Call Registry was doomed from the outset. In addition to the fact that crooks generally don't obey laws that are intended to hinder their operations, there's the fact that whole classes of unwanted callers are free to ignore the Do Not Call Registry legally. These include political organizations, polling companies, charities, and anyone who can claim an "ongoing relationship" with you.
Most of the scammers are free to do what they want because they use voice over internet protocol (VOIP) services to make inexpensive calls from outside the United States. They don't even have to know your number. Robocallers can call every number in every exchange of every area code in the country. No wonder the Do Not Call Registry doesn't work!
One of the more recent tricks is to have the call spoof a number in your local exchange. Exchange is the 3-digit number between the phone’s area code and the line number. This is all defined in the North American Numbering Plan (NANP) that was defined in the 1940s by AT&T for the Bell Telephone System and is used in the United States, Canada, many Caribbean nations, and US Territories.
Phone numbers consist of country codes (1 for nations that use the NANP), a 3-digit area code (614 is one of two overlapping codes in central Ohio), a 3-digit exchange code (888 and 785 are two of many that area used in my area), and a 4-digit line or station number (0000 through 9999).
When a call to my cell phone comes from a number that begins with 1-614-785, it appears to be from a local caller. Scammers know that many people will trust what appears to be a local call even if they don’t recognize the number, so they have learned how to make the call look like it’s coming from a local number. The usual response to spam calls involves blocking the number, but that no longer works because the scammer can randomize the calling number with every call.
Several applications exist for IOS and Android phones. Some also work with voice over IP systems. None that I’ve found work with standard (“plain old telephone service” – POTS) lines. After trying a couple of them, I signed up for the paid version of one.
Both RoboKiller and NoMoRobo have won contests by the Federal Trade Commission to block unwanted calls.
RoboKiller is currently available only for Apple phones, so I had expected NoMoRobo to be the one I’d sign up for. I signed up for TrueCaller, though, because NoMoRobo’s performance was disappointing. If you decide to try one of these apps, be sure to download it via the Apple App Store or the Google Play Store. Downloading from the provider’s website would also be safe if you’re absolutely certain that you’re on the developer’s site.
Although I signed up for TrueCaller, I’d recommend taking a look at RoboKiller if you have an Apple phone. RoboKiller’s process is designed to waste the time of spam callers. So for now I’m using TrueCaller on a month-to-month basis and hoping that RoboKiller will eventually be released for Android.
Ethan Garr, vice president at TekTech Systems, RoboKiller’s developer, says the company is in the process of building an Android version and expecting to launch it before April. The RoboKiller Android app “will not only block more than 100,000 spammers from ever ringing on your phone, but it will also allow users to unleash our Answer Bots on spammers. These are recordings which talk back to the spammers and waste their time.”
Wasting a scammer’s time is important, Garr says, because it's the economics of cheap calls that’s driving the scourge of scam calls.
Most of the call blocker apps offer a brief trial period and then cost $2-$3 per month for continued service. The trial periods are all too short for users to develop a full understanding of how the system works.
RoboKiller is the app I’m most interested in trying, but TrueCaller is a workable alternative for now. It’s more of a traditional caller ID application, but it offers to block known spammers and to allow users to specify numbers they want to block.
Because I currently receive no legitimate phone calls from any user in my cell phone number’s exchange, I have blocked all numbers that start with 1-614-785. That’s easy to do with TrueCaller, but there is no option to selectively allow individual numbers within the blocked range. That means that if I need to receive calls from someone in the 785 exchange, I’ll have to unblock all of the numbers.
I had also looked at MrNumber. The app blocks known spam numbers and allows users to report numbers that will then be added to the list of spammers. There are also options to add individual numbers you want to block, to block any call that hides the originating number, to block international calls, or to block calls from anyone not in your contact list.
TrueCaller displays a notification for inbound calls that are not automatically rejected as spam. If the caller’s name it available, it will be displayed, as will the number and the date of the last call received from that number. You then have the option of accepting the call or rejecting it.
There’s also a screen that shows a list of received calls, the numbers they’re from, and any available identifying information. TrueCaller has reduced the number of scam calls and SMS messages to my cell phone, but I’m still looking forward to seeing what RoboKiller will have to offer on an Android device.
This is a topic I’ll revisit when RoboKiller has been released for Android. Until then, my recommendation is TrueCaller for those with Android devices and RoboKiller for those with Apple devices.
Online crooks are nothing if not inventive. By now your operating system (MacOS, Linux, or Windows) has probably been updated to reduce hardware dangers associated with attacks called Spectre and Meltdown, but now there's another threat.
Malwarebytes has reported a fake patch that attempts to install malware called Smoke Loader. A fake website that claims to be part of the German Federal Office for Information Security (BSI) is the source.
So far, the threat seems to be limited to Germany and German speaking users, but it's a safe bet that the attack will be widened. Users receive an email that claims to be from the German federal government and the message directs them to download and install a patch, which is actually malware.
The blog post says "It’s always important to be cautious, especially when urged to perform an action ([e.g.], calling Microsoft on a toll-free number, or updating a piece of software) because there’s a chance that such requests are fake and intended to either scam you or infect your computer. There are very few legitimate cases when vendors will directly contact you to apply updates. If that is the case, it’s always good to verify this information via other on-line resources or friends first."
Crooks keep an eye on the news and when they see something that can be exploited (a natural disaster that lets them set up a fake donation site or a hardware flaw that makes it possible to offer malware disguised as a legitimate patch), they act quickly.
The German exploit starts with an email that directs users to a fake website that offers a link to "Intel-AMD-SecurityPatch-11-01bsi.zip" The file extracted from the archive file is "Intel-AMD-SecurityPatch-10-1-v1.exe" and, despite the name, is malware that installs Smoke Loader, which can then install other malware and send data from the computer to crooks.
To make the exploit more believable, the fake site uses a secure (HTTPS instead of HTTP) connection, but this only means that the between your computer and the site is secure and does not indicate that anything on the site is legitimate, trustworthy, or safe.
You've doubtless noticed that many sites now display a message that says the site uses cookies. These have become increasingly prevalent in the last year or so, mainly as the result of a law in the European Union. In fact, the EU has been driving most advances in privacy and security matters as the United States continues to fall behind.
The most common version of the cookie notice simply says that the site uses cookies and gives the user a single option: "OK" or "Got it" or something along that line. In some cases, the explanations are a bit more involved. For example, this notice on CookieLaw.org, a site that provides a paid service for companies that need to ensure compliance with the EU law.
You haven't seen one of these notices on the TechByter Worldwide site because I don't use cookies. For this site, there's no particular benefit that cookies would offer me as a website designer or you as a website user. In some cases, cookies can benefit the website developer, the user, or both.
Consider a bank that I use as an example. The bank sets a cookie after I have successfully logged on with a user name, password, security question, and two-factor authentication. As long as I leave the cookie in place, subsequent logins from the same browser on that computer will omit the need for two-factor authentication because the bank's website recognizes the browser I'm using.
If I use a different browser on the same computer or a different computer (even with the same browser), I'll have to go through the two-factor authentication process again. And if I delete the bank's cookie, my browser will no longer be recognized and the log-in will be needlessly delayed by the validation requirement.
I know people who seem to have a deathly fear of cookies and they immediately delete them or don't allow them to be set. Then they complain about how hard it is to use a site that expects cookies. Basic cookies are just text files that serve as short-term memory for your browser. Cookies can be more complicated than that and they can serve advertisers' goals more than yours, so some level of caution is reasonable.
There are ways to eliminate all existing cookies and block future ones, but deleting all of your browser's cookies will probably cause some pain for you. Most browsers offer some level of control. I'll demonstrate Firefox's options here.
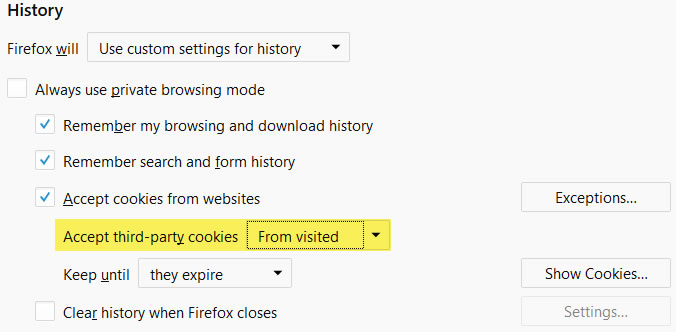
Third-party cookies are ones that are created by a site other than the one you're visiting. For example: XYZ Marketing might set a cookie when you visit foo.com. I accept these kinds of cookies and any cookie that the website I'm visiting sets. However, if I visit foo.com and XYZ Marketing attempts to set a cookie for bar.com, I want to block it because the third party is trying to create a cookie for a site I haven't visited.
Most browsers have third-party cookie settings and the most common options are accept all, reject all, and accept from visited sites. Applications such as CCleaner have options to allow cookie deletion on a per-browser basis. I always disable this because it deletes all cookies when it's enabled.
Refusing all cookies will make your internet life harder than it needs to be, but keeping an eye on who's writing cookies to your computer is a good practice.