This year has seen an increase in numerous kinds of threats designed by people who want information that's on your computer, money that's in your bank, or both. The problem gets worse every year, so we'll see more threats in 2018. Now is a good time to consider some of them.
When I answered the phone this week, a computer-generated voice said "THIS IS AN EMERGENCY." Some government agencies use systems like these to warn citizens of danger, so I continued listening. Then I terminated the call after the next 7 words.
Those words weren't "This is a call from a crook." Instead, they were "The activation key for your Microsoft software...."
If you've listened to the podcast or read TechByter Worldwide for very long, you already know that Microsoft doesn't place outbound calls like this. That's not to say Microsoft doesn't call users. The company does call, but only if the user has first contacted Microsoft with a problem that needs further investigation. The technician will also have a case number that you should recognize.
Unfortunately, though, Microsoft has blurred the line a bit between legitimate calls and scammers. When scammers call, they'll try to sign you up for a paid maintenance program. Microsoft technicians also do this, but they'll stop pushing and help solve the problem once you tell them you're not interested.
The crooks do something else that no Microsoft technician will do. Scammers will instruct you to open the Windows Event Viewer. The Event Viewer logs show informational messages, warnings, and errors. These can appear to be ominous when a crook has you look at them. Here's a screen shot that shows a flood of disturbing error messages, along with some warnings and a couple of informational messages. The scammer will try to convince you that the computer has serious problems.
In general, it's good to avoid the Event Viewer unless you know what you're looking for. Many of the warnings and errors are trivial. The one I've highlighted is identical to the other error messages shown and it's not a serious problem. It's an ownership issue. That is, the owner of the process has been changed to the user of the computer and not the Administrator account. The messages are annoying, but the problem doesn't need to be fixed. There are ways to fix it, but it will return following the next big Windows update.
The Event Viewer is helpful when an application terminates abnormally or Windows crashes because it can be used to identify the component that caused the problem. But just scrolling through the Event Viewer randomly does nothing but cause needless worries.
The scammers have various approaches. Some use the phone and others send alarming email messages, but prevention is relatively easy: If you haven't contacted Microsoft with a request for assistance, they won't contact you. Neither will your internet service provider. And anybody who contacts you with a request to "confirm" account credentials can be presumed to be up to no good.
Malware and ransomware are concerns, of course, but they are now almost always the second part of an attack. The primary part will now probably be an email. Email has for a long time been the most common vector for attacks -- messages that appear to come from a friend or co-worker.
We humans are almost always the weak link in any security system. After all, why should crooks use brute-force methods that might attract unwanted attention when they can persuade people to give them the information they need?
Mimecast's most recent Email Security Risk Assessment (ESRA) report reviewed more than 50 million email messages. More that 12 million were spam and that number actually seems low. Some experts believe that 80% or more of email traffic on the internet is spam. The low number (about 25%) reported by the Email Security Risk Assessment may be the result of upstream anti-spam functions that identify and delete spam when it's still in transit.
Of the 12 million files that were spam, more than 9000 contained harmful files and more than 2500 included malware, but nearly 19 thousand were what are called "impersonation attacks". While 19 thousand might seem like a small number, the increase is concerning: These kinds of attacks increased by 50% over 2016.
Many of the impersonation attacks target company employees and claim to come from the chief executive officer, the chief financial officer, or other C-suite manager. The messages may explain that the company has secretly agreed to acquire another company and certain fees must be paid immediately and quietly. The crooks who send these kinds of messages spend the time needed to learn who the managers are and what the company's email messages look like.
These are textbook spear-phishing email messages: Carefully crafted and targeted for specific individuals in a company -- the right message from the right person to the right person. These kinds of messages can be highly effective and the Email Security Risk Assessment says that the average loss is just under $140,000.
Impersonation attacks offer the crooks a huge advantage: Protective applications can stop messages that contain malware most of the time, but there's no clear indicator that would identify an impersonation attack. These kinds of attacks are usually aimed at businesses or government agencies, but similar kinds of attacks can be designed to target wealthy individuals.
A researcher at the University of Birmingham (England) has identified 5 Android and IOS mobile banking applications that are vulnerable to "man-in-the-middle" attacks that can be used to steal banking credentials.
The full report is on the university website. The apps are used by HSBC, Bank of America, Meezan Bank, and Smile Bank. The apps have tens of millions of users worldwide.
Bank of America says that it discovered and corrected the flaw in January of 2016 and the app shouldn't even have been in use when the University of Birmingham tests were conducted this year.
A man-in-the-middle attack (also known as a Janus attack) places the attacker between two people who believe they are communicating directly with each other. The man-in-the-middle can simply read the communications or modify them. Wikipedia offers an example.
The researchers cite "certificate pinning" as part of the problem. A pinned certificate is accepted only if it is signed by a single certificate authority root certificate and the technique is often used for transport layer security (TLS) connections. The report says that a flaw in pinning can obscure the lack of host-name verification and thus make man-in-the-middle attacks possible. An attacker who thoroughly understands the system can spoof the certificate, read the communications, and optionally change what either party sees.
The researchers created a process they call "Spinner" that attempts to run a man-in-the-middle attack. They tested 400 apps and 392 of them performed acceptably. The other 8 did not.
All 8 of the apps with vulnerabilities have been patched, but underlying vulnerabilities still exist. Spinner redirected traffic to websites that use similar certificates and then analyzed the encrypted traffic to determine whether the host-name check was done right. It was able to obtain information without needing a single certificate.
This is yet another reason to update applications in a timely manner!
The first program of 2018 (Podcast #574 on 7 Jan 2018) will feature predictions by Sam Curry, the chief security officer at Cybereason.
Those who have cell phones that use a data plan (and that seems to be about 90% of us) may occasionally be shocked by how much data some apps use. Google has a new application that not only identifies which applications use the phone's data plan and how much the apps use, but also gives users a way to control the usage.
I spend very little time at locations without Wi-Fi, so excess data plan usage isn't an issue for me. The Google-Fi plan I signed up for about a year ago costs $20 per month for calls and texts, but otherwise without data. Adding 1GB of data per month adds $10, but I rarely use that much, so the plan pro-rates the data fee and I rarely pay more than $25 per month. This compares to my previous plan that cost $50 per month and included only 500MB of data. My usage is rarely more than 500MB per month because most of the data transfer happens on Wi-Fi.
Those who spend more time away from Wi-Fi and want to save money on their data plan might find that Google's "Datally" app helpful. I presume the name is supposed to be a portmanteau of "data" and "ally", but "datally" just doesn't look very good and it's unclear how Google wants people to pronounce it: DAT-ally? dat-ally? data-LEE? da-TALLY?
Whatever we call it, we can't call it new because the concept has been around for a while. I've used other applications that monitor data usage, but Google's entry (despite its puzzling name) is easy to set up and straightforward to use.
For testing, I turned off my Wi-Fi connection after installing Datally. By default, the application blocks data plan usage by most applications other than those needed by the operating system. It's up to you to decide which applications you want to give data plan access to. The e-mail application I used (Aqua Mail) was unable to log on to my mail servers when Datally was active, even though I had cleared it to use the data plan, until I rebooted the phone. After that, it was fine. This is probably an Aqua Mail issue because it also has trouble connecting via Wi-Fi when I have the VPN turned on.
Datally shows how much of the data plan you've used on its main screen. After turning Wi-Fi off, I managed to use 28MB of data one morning instead of my usual few hundred kilobytes per day. That's a good overall view, but the real power comes from the application's display that shows how much data individual apps use.
During the set-up process, Datally will request permission to send, receive, and read SMS messages, track your location, and access phone features that allow it to know the phone number and device ID, determine whether a call is active, and identify remote number of any call. It will also set up a VPN (but only for mobile data, not Wi-Fi) and then use the VPN to block data plan access for apps you haven't approved.
I played a single game of Solitaire on the phone and was surprised that this used 13MB of data. Apparently the files that are downloaded for each winnable game are a lot less compact than it seems they should be.
Using the Manage Data tab allows the user to examine every application on the phone and explicitly allow or block access to the cellular data plan.
Even if you have an "unlimited" plan, you may find that your provider throttles the plan to an unacceptably slow speed once your monthly usage exceeds a certain amount. The plan will still be "unlimited" but the connection will also be unusable. Datally can help users by refusing to allow non-essential applications to have access to the data plan.
If you need to give a blocked app access to the data plan, it's easy to just turn Datally off for a few moments, use the normally blocked app, and then turn the Google app back on. You could also temporarily or permanently allow an app to have access to the data plan.
Datally also includes a Wi-Fi finder that lists nearby locations that have Wi-Fi hot-spots and whether there's a login process or the hot-spot is entirely open. Keep in mind that there is no security difference between "web login" and "no password". The connections are not encrypted and using a Wi-Fi hot-spot is dangerous unless you enable a VPN.
You'll find Datally in the Google Play store.
Windows continues to have 2 Control Panels -- the traditional desktop application and the one that was introduced with the Modern interface. The new Control Panel offers access to the old Control Panel because some settings still haven't been incorporated into the new Control Panel. Until the Fall Creators Update, the old Control Panel was what you'd find on the WinX menu. Now you get the new one.
Maybe you want easier access to the old Control Panel.
If you still get to the Control by pressing the Windows key, typing "Control", and then clicking "Control Panel (desktop app)", you can stop reading right now and just keep doing that. But if you press the Windows key and X to display the useful WinX menu, the Control Panel listed there is now the new one.
Restoring the old Control Panel to the WinX menu is possible, but it's not easy and it's a bad idea because Microsoft will eventually migrate all of the settings to the new Control Panel.
Instead, if you really need to have quick and easy access to the old Control Panel, why not just pin it to the Taskbar? The process is easy.
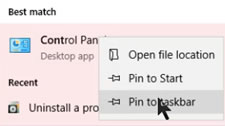 Search for the Control Panel by pressing the Windows key and typing control. You'll see Control Panel at the top of the list.
Search for the Control Panel by pressing the Windows key and typing control. You'll see Control Panel at the top of the list. Move the resulting icon to whatever position you prefer on the Taskbar.
Move the resulting icon to whatever position you prefer on the Taskbar.This same technique works for any other application that you'd like to place either on the Start Menu or the Taskbar so that you'll have quick access to it.
This is the final program for 2017. We'll take next week off (although you can expect a New Year's greeting) and then we'll be back on January 7th with new content, some new music, and more of the same 60 minutes worth of technology news in about 20 minutes.