Anybody who needs to send the same information by email to several people has several choices. One of these choices involves using Outlook's mail merge feature (which actually lives in Microsoft Word). There are many opportunities for improvement.
First, let's consider the options when you need to send identical information to many people.
The easiest option is nothing more than using the copy or blind-copy function of your email program. Depending on the company that provides email transmission services, this will work for groups up to several hundred. Most internet service providers and hosting providers cap the number of messages that can be sent per hour or per day. This is done to make standard email accounts unpalatable to spammers, but it can get in the way of a user's legitimate need to occasionally send a large number of messages.
The best option when you need to send the same information to hundreds (or thousands) of people at the same time is a mailing service such as the one used for the weekly TechByter newsletter: MailChimp. The service allows users to send up to 12,000 messages per month to a total of 2000 subscribers.
If you need to send attachments, most of the mailing services will allow something small -- an embedded 100KB image file, for example -- but not a multi-megabyte PDF document. Instead, you'll need to provide a link in the message to a file that has been uploaded to a public server.
Another option involves using Microsoft Word's merge function to create email messages. This allows each message to be personalized with the recipient's name and other information in the message. There's still the message limitation set by your internet service provider and if you want to include an attachment, you'll quickly learn that this isn't possible.
At least not without a little help from your friends.
Your friends in this case are in Russia (although they have a North American office in Vancouver, British Columbia). Useless but possibly interesting information: The company is located in Kaliningrad is on the Pregolya River, near where it empties into the Baltic Sea. Following the collapse of the Soviet Union, Kaliningrad Oblast became an "exclave" -- part of Russia, but geographically separated from Russia. Poland is on the south border, Lithuania on the north and east, and the Baltic Sea on the west.
Our friends have a name: MapiLab and they have concentrated for many years on development of software that works with Microsoft Exchange Server, Microsoft Outlook, and Microsoft Office. One of their products is the Mail Merge Toolkit, an add-in for Microsoft Office that extends the built-in mail merge capabilities of Outlook, Word, and Publisher.
Word is capable of creating a mail merge that includes personalized information in the message, but not in the subject line. One of the best ways to get a recipients' attention is to include their name in the subject like. Mail Merge Toolkit does this.
Additionally, if you want to include an attachment with the messages, the plug-in makes that possible, too -- and then makes things even better by allowing the included attachment to be a specific attachment per recipient.
Granted, this isn't something everybody needs -- but consider this situation: Let's say that you need to create a series of reports each month that will be sent to co-workers. In this situation, you have 50 co-workers and there are 10 reports. Each user should receive the single report that is relevant to their department. Not all users will receive every report every month.
That sounds like a lot of work if done manually.
The process begins with Excel, where you'll create a list that includes the essential information. Creating a list and setting up the merge document in Word is well known and widely documented, so I'll skip most of that.
My Excel document has columns for the user's first name, last name, phone number, email address, mailing indicator, and attachment name. The names, phone numbers, and email addresses were all randomly generated, but I have obscured the phone numbers and email addresses because some of them could, inadvertently, be real.
The spreadsheet may contain any number of columns -- whatever needs to be included in the merged messages.
Next, you'll set up the merge document in Word.
After linking the Excel file to the Word document, you'll have an opportunity to filter the records. This is a merge function within Word that allows the selection of records based on certain criteria. In this case, I want to send messages only when "Send" is TRUE.
After doing that, you will create the message. Any number of merge fields may be included in the message.
Then the process diverges from the standard Microsoft Word work-flow. Instead of selecting "electronic mail", you'll select "Mail Merge Toolkit".
The primary differences here are that you'll be offered an opportunity to add merge fields to the subject line and there's an option for attachments.
The attachments may be the same for all documents. If this is your choice, you will select a file name. The more powerful function is the ability to choose a specific attachment for each message based on a value in the Excel document. If that's what you want to do, you'll specify a field. I have cleverly named that field "Attach".
Oops! What happened here? Two things, actually.
The certificate must be disabled when the plug-in is active. After sending the messages, you'll want to reactivate the certificate.
I have reported this bug to MapiLab.
Then the merge completes, attaches the appropriate file, and sends the messages. Of the 50 addresses on the test list, 33 were marked as eligible to send and that's the number of messages that were sent.
Here's a partial list of the sent messages.
 When you need more than a basic email merge, this is a good choice.
When you need more than a basic email merge, this is a good choice.If not for the incompatibility with the certificate used to digitally sign messages, Mail Merge Toolkit would easily be a 5-cat application. It's easy to use and adds powerful functionality to Microsoft Outlook.
Additional details are available on the MapiLab website.
CrashPlan is getting out of the home backup business a little more than a year from now to concentrate solely on the small office/home office (SOHO) market. That doesn't mean home users will have to stop using the backup service, but it does mean that they'll have to pay more.
"I'm really happy that I'm going to have to pay more for this service" said nobody ever, but some price increases are more palatable than others and this is in that category.
The price will double to $120 per year, but that's still just $10 per month. How much is data security worth to you? It's worth that much to me even though Crash Plan is just one part of my multi-part backup system.
CrashPlan is the name of the backup service from Code42. The company protects more than 47,000 organizations worldwide. The Minneapolis company says that it will honor all CrashPlan for Home subscriptions for the duration of the subscription and will help consumer customers transition. Subscriptions will also be extended by 2 months.
Users can migrate to the SOHO service at no additional charge for the remainder of the term. After that, there's a 75% discount for the first year on CrashPlan for Small Business.
The Code42 blog is currently filled with negative reactions, which is probably to be expected whenever anything changes -- particularly when the change also involves a price increase. One option Code42 is offering CrashPlan Home users is moving their backup to Carbonite.
Many of the commenters on the blog are former Carbonite users, as am I. When I left Carbonite several years ago, it was primarily because of exceedingly poor response from support. Perhaps that has changed, but those who used Carbonite in the past seem to be disinclined to use it again.
There are other options, of course. Acronis offers an on-line backup option in addition to its ability to create local backups and clone hard drives. In fact, I use Acronis True Image to maintain an image copy of my boot drive. True Image Premium costs $100 per year, but limits on-line backup to just 1TB.
This probably isn't a decision guided solely by Code42. Information from the company says that it is "backed by Accel Partners, JMI Equity, NEA, and Split Rock Partners." These are four venture capital firms, so you can guess who's calling the shots. As always, follow the money.
Code42 says that it has experienced 50% year-over-year recurring business revenue growth for the past 3 years and attributes much of that to its plans for businesses. "The small business, education and enterprise markets have proven to be significant growth areas for the company," according to a news release.
But despite who's calling the shots and why, is it a bad deal for users? Under terms of the service extension and a year's worth of the business-class service at a 75% discount, which makes it less expensive than the home version, users have 2 years to make a final decision. That's worth pointing out to those who have written on the Code42 blog that this is "absolutely devastating", often with many exclamation points.
The company says that the needs of home users differ from those of business users, but doesn't explain how. After all, a lost file is a lost file no matter whether you're a home or business user and threats are similar regardless.
But still -- I keep coming back to the fact that for most users, after 2 years, the price of the service will double. But that doubling moves the cost from $5 per month to $10 per month. What can you buy for $10 these days -- a single movie ticket, perhaps, or dinner for two at Wendy's. Maybe six bottles of good beer or 4 gallons of gasoline.
I'd hardly put this in the "devastating" category.
If you've ever clicked on the Speaker icon in the Notification area only to see no response, you're not alone. There's a workaround for this problem, but it's a problem that shouldn't exist.
 The Notification area of the Task Panel should display a speaker icon. Right-click it and you should be offered options to open the volume mixer, specify recording or playback devices, choose the sounds that are played when various event occur, and troubleshoot sound problems. Left-click and you should see a volume control.
The Notification area of the Task Panel should display a speaker icon. Right-click it and you should be offered options to open the volume mixer, specify recording or playback devices, choose the sounds that are played when various event occur, and troubleshoot sound problems. Left-click and you should see a volume control.
What if none of that happens?
That's something that shouldn't happen, but I started seeing this behavior about a week ago and researching to problem revealed that this is not an isolated problem. Lots of people have seen this problem.
The recommendations for resolving the problem include re-installing Windows!
As it turns out, this is not required and would be a bad solution. Instead, I offer thanks to Andy Lee, who posted a clear, concise, and easy solution on the Microsoft Community Forum website. Andy's final words in that post are: "Note to Microsoft. FIX IT."
Microsoft hasn't fixed it, at least not yet, so you can fix the problem by terminating Microsoft's File Explorer and restarting it. The process is as simple as it is unnecessary and we can only hope that Microsoft will follow Lee's recommendation to fix it.
Here's the solution:
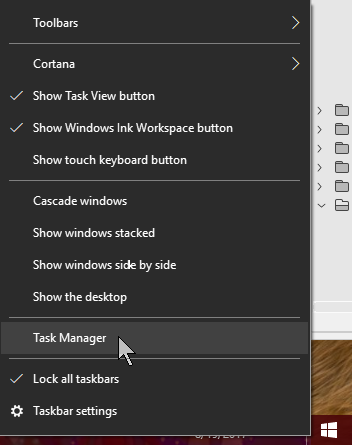 Right click on Task bar.
Right click on Task bar.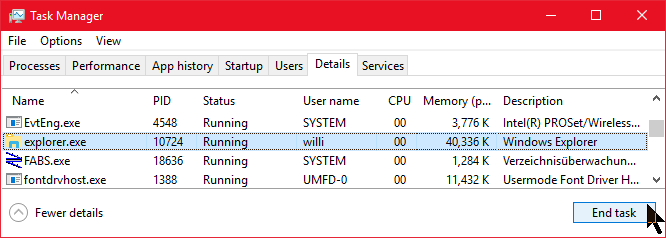 Click on the Details tab and sort the list by name.
Click on the Details tab and sort the list by name.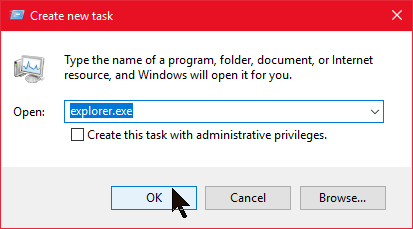 Still in Task Manager, click File > Run new task
Still in Task Manager, click File > Run new taskThe volume control will now operate as expected and I echo Andy Lee's recommendation to Microsoft: "FIX IT!"
Here's how it works, by the way: When you use the Task Manager to close the Windows Explorer, you've constructively forced it to crash. If you make the mistake of closing the Task Manager before performing the next step, you will have no way to access the Start Menu, run applications, or shut the computer down.
Creating a new Explorer task forces Windows to refresh the icons in the Task Bar and Notification Area. The Speaker icon that had stopped working will be replaced with a functioning version. Note that if you have any applications that place icons in the Notification Area when they start, you may need to restart them to get those icons back.
This is the kind of correction that nobody should need to deal with.
Maybe you've used an ATM and noticed somebody standing uncomfortably close to you. Or maybe you didn't notice. If you used a drive-up ATM, you could still be observed by a well placed camera. This is called "shoulder surfing" and it's yet another way that crooks can obtain information you don't want them to have.
Researchers at the New York University Tandon School of Engineering say they've invented something that can eliminate the threat.
Computer science and engineering professor Nasir Memon says they're calling the new technology "IllusionPIN". It uses an on-screen keyboard that displays one image to a viewer who is less than 3 feet away and something else to those who see the screen from a greater distance.
The underlying technology "blends one image of a keyboard configuration with high spatial frequency and a different keyboard configuration with low spatial frequency." In plain English, that means that the visibility of each image is dependent on the distance from which it is viewed.
Memon says the traditional configuration of numbers on a keypad is so familiar that it's possible for an observer to discern a PIN or access code after several viewings of surveillance video. "The user sees one configuration of numbers, but someone looking from a distance sees a completely different keypad."
So all the crook needs to do is view the screen up close and note the configuration of numbers, right? Well, no. IllusionPIN reconfigures the keypad for each authentication or login attempt.
The research team performed 84 attempted shoulder-surfing attacks on 21 participants, none of which was successful using their new technology. When they attempted 21 shoulder-surfing attacks on unprotected phones using the same distance parameters, all 21 attacks were successful.
There are no reliable statistics on the prevalence of shoulder surfing attacks, but a 2016 study conducted by the team found that 73% of mobile device users surveyed reported that they had observed someone else's PIN -- although not necessarily with malicious intent.
PIN authentication is popular because PINs are easy to use and remember. The research team plans to further refine IllusionPIN, with the goal of commercializing the technology. An article about the technology (IllusionPIN: Shoulder-Surfing Resistant Authentication Using Hybrid Images) was published by the Institute of Electrical and Electronics Engineers.