Without a doubt, Lynda.com is the biggest general information learning site on the Web. There are others that provide more in-depth information on specific topics, but Lynda.com covers a wide range of basics and dives deep into some areas.
But it's expensive for the casual learner, the person who may decide to learn something new every few months. Expensive is relative, of course. The plans cost $25 per month or $35 per month, with the more expensive option providing access to exercise files.
Compared to college-level classes, the cost is modest -- enrollment for an entire year for the cost of just one college course. Lynda.com awards certificates when the student reports completion, but there's no testing and the certificates have no value toward continuing eduction credits required by some professions.
But still, it's a superb resource. Photographer Ben Long is one of my favorite instructors on Lynda.com, but there are many others, including Chris Orwig, who is a college instructor, Jan Kabili, Deke McClelland, Adobe's Julieanne Kost, and literally dozens of others on various aspects of photography. And that's just one area.
Maybe you want to learn about email marketing, the Python programming language, microphones and sound editing, search engine optimization, accounting, word processing, creative writing, time management ...... Well, you get the idea.
Previously an independent company, Lynda.com was acquired by LinkedIn and LinkedIn was eventually gobbled up by an even larger fish called "Microsoft".
The service offers a 30-day free trial. Sign up and you can watch any of the courses for the next month. But then what? Maybe you'd prefer the permanently free option.
Your library may offer access to Lynda.com and to many other educational resources. Two library near me do this: The Worthington Public Library and Columbus Metropolitan Library. Other central Ohio libraries may also include Lynda.com among their resources.
To log on, all I need is my Worthington or Columbus library card number and its associated PIN. But what if your library doesn't offer access to Lynda.com? Look around. A friend in California said that the library in his town didn't list Lynda.com, but a nearby town's library did. Many libraries issue cards to those who live within a certain area whether they are in that particular library district or not, so a nearby library may be able to help.
Licensing for some on-line resources require that they be used only from the library, but Lynda.com isn't one of these. Just log on from home using your library credentials. I have full access and that includes the exercise files that are provided by many of the classes so that students can work along with the instructor.
This is both another reason to support libraries and an excellent way to learn about something that interests you.
"Hello, I'm from Windows Support" isn't as effective as it once was for scammers. Most people have learned that Microsoft doesn't call people to tell them about a problem with their computer. But phony email messages about missing packages and canceled orders are still effective. The scammers are combining the ploys.
Microsoft's TechNet blog describes a new way for crooks to score.
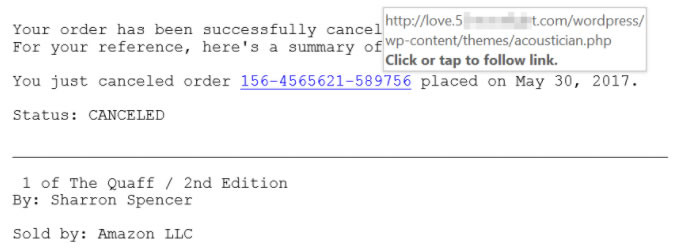
Let's say you receive a message that claims to come from Amazon and confirms cancellation of your order. It doesn't address you by name. It's in plain text. It describes something you didn't purchase or cancel. So why would you click the link? That's a good question, but people do.
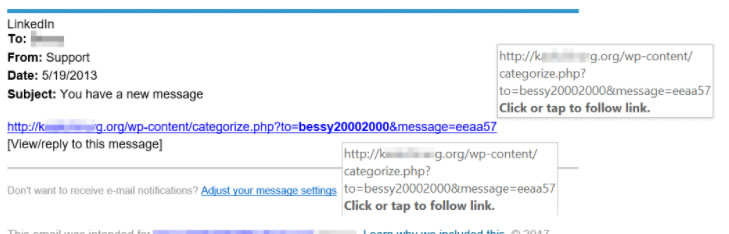
Perhaps a bit more convincing: A message that claims to come from LinkedIn. First, do you have a LinkedIn account? If not, then it's clearly a scam. Hover the mouse above the link and if the domain is something other than LinkedIn, it's a scam. The key to staying safe involves paying close attention to your surroundings and watching for clues that a message is fraudulent.
If you follow one of these links, several things could occur and they're all bad. It might be a link to a site that installs malware. Or it could lead to a fake site that tries to impersonate Microsoft. Here's one that the TechNet blog displayed.
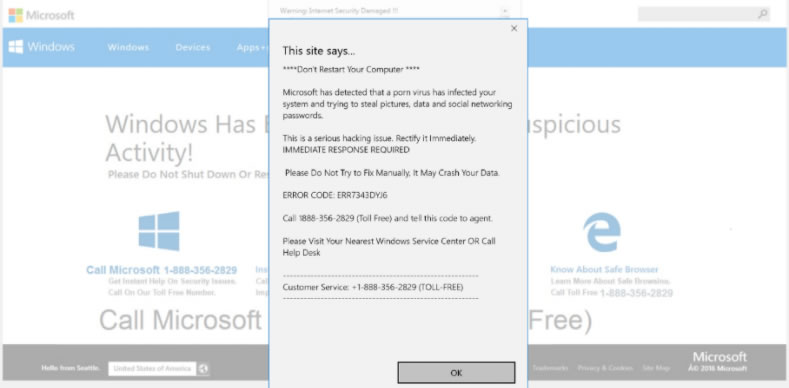
There are several blatant clues that this is false. Most of the clues are in the wording of the pop-up message. Does this message look like something a native English speaker would write? Microsoft has a lot of people on staff who deal with external communications and a message this poorly written would never be seen.
The technical support scam websites use social engineering techniques to convince users to call. You might be told malware is on the computer, or a license has expired, or there are system problems. Some of these pop-up messages essentially lock the browser by displaying a new message (or re-displaying the previous message) whenever the user tries to close the dialog box.
If you see this kind of behavior, you can try to close the browser window. If that doesn't work, open Task Manager (Ctrl+Shift+Esc), select the browser under Apps, and click End Task. And if a pop-up box tells you to call a "hotline" number, don't. Error and warning messages from Microsoft do not contain support numbers.
The blog notes that Windows 10 is more secure than previous versions of the operating system and that the operating system defends against multi-faceted threats. "Microsoft will not proactively reach out to you offering unsolicited technical support. To reach our technical support staff, visit the Microsoft Answer Desk."
Following a Windows update two problems appeared on my primary computer, but not on any of the others: Outlook crashed on open, attempting to open Outlook in safe mode crashed on open, and attempting to open Outlook repair crashed on open. In short, Outlook would not start. Second, the Windows Start Menu was inaccessible -- neither tapping the Windows key nor clicking the Windows icon would open it.
Although I could have resolved the problem on my own, I wanted to see what a Microsoft support session looks like these days. The Microsoft website offered a chat option and that's what I selected. The technician (Michael C) asked for remote control and I granted the request.
This is safe for two reasons: First, I originated the contact via Microsoft's website. Second, the technician used a Microsoft-branded version of LogMeIn Rescue.
The technician followed essentially the same steps I would have using the deployment image service management tool (DISM) with a "restorehealth" option and the system file checker (SFC), but he also had some tools designed explicitly for Start Menu problems.
Nothing worked and the technician suggested a $150-per-year plan that covers 5 computers. In fact, this is a valuable option if you're uncomfortable with troubleshooting because it provides access to level 2 tech support. But the level 1 technician started an in-place upgrade -- essentially reinstalling Windows over the existing installation while leaving all files and applications untouched.
A couple of hours later, everything was back to normal.
If you're an aspiring crook, you might want to know about the Ovidiy Stealer. For about $10, you can license the application that steals credentials. The price range seems to be $7 to $13. If you're interested, the line forms over here on the right.
Admittedly, it's not the most sophisticated malware on the planet, but what do you expect at that price?
Ovidiy Stealer is currently being marketed primarily in areas where Russian is spoken. That doesn't keep it from being adopted by crooks in areas where French, German, or English is spoken.
Up-to-date anti-malware applications generally spot this malware, but not everybody keeps these applications updated. Proofpoint says that the malware is being spread via email as executable attachments, compressed executable attachments, and links to an executable download. "It is also likely spread via file hosting / cracking / keygen sites, where it poses as other software or tools."
Ovidiy Stealer is offered for sale on a Russian site that is also the command and control domain. The malware offers reasonably robust support via a control panel that shows statistics on infected machines, allows the user to view logs, build more stubs, and manage the account.
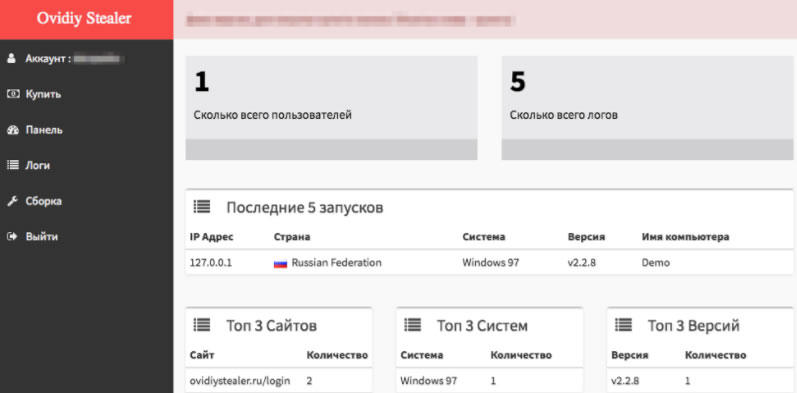
Proofpoint explains how the malware market works these days: "Like many other markets with many choices, the malware market is competitive and developers must market the strengths and benefits of their products in order to attract buyers. To help drive sales, the development team includes statistics on the progress of certain modules, and other plans for future releases of the malware. In addition, the site includes 'testimonials' from satisfied customers, presumably to demonstrate to other would-be criminals that they can be profitable when using Ovidiy Stealer."
So if you were looking for something else to worry about, there you go.
This month's updates from Microsoft eliminated some nasty bugs. This is the update I mentioned earlier that caused operational problems on one computer.
The most serious fix deals with a flaw that exposed all current versions of Windows to malware that could take over a PC and then spread to other machines on the network.
Microsoft says that the flaw, if left unpatched, is likely to be exploited. It would allow an attacker to take control the computer, and that includes the ability to install software, run programs, and delete files.
Trend Micro's Zero Day Initiative blog says that the flaw is dangerous because it can be exploited remotely by an unauthenticated machine using the Server Message Block (SMB) networking protocol. The recent WannaCry and Petya attacks used SMB.
Overall, 48 security problems were resolved this month and 25 of the vulnerabilities were rated as critical security risks, Microsoft's highest rating.