Finding Your Computer If It's Been Stolen
At the risk of jinxing myself, I have never had a computer stolen even though I have left computers in hotel rooms in locations such as New York City, San Diego, Chicago, San Jose, Orlando, Atlanta, and Dallas. Generally I'm fairly careful about where and how I leave computers but my luck so far has been just that: Luck. Computers are attractive targets and they're easy to steal but you can protect yourself.
It would be bad to lose a computer. First, there's the cost of replacing it and the cost of replacing the software on it or convincing the software merchants that the device has been stolen and they should extend your license. But what about the data? If you've followed my recommendations, you have your critical files tucked away in a directory that's protected by encryption software such as TrueCrypt. And you have them backed up somewhere, too.
But you'll probably still want to find the computer and recover it if you can and that's what PreyProject is all about. It's a free application that can track your computer.
Installation is Easy
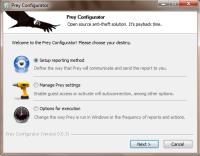 By default, the application installs in C:\Prey. A smart thief might know enough to look for this directory and destroy it but if the thief is that smart, he's probably also smart enough to look for Prey among the installed applications and remove it. I decided not to change the default directory. It also creates a standard entry in the Start Menu. I left that for the same reason.
By default, the application installs in C:\Prey. A smart thief might know enough to look for this directory and destroy it but if the thief is that smart, he's probably also smart enough to look for Prey among the installed applications and remove it. I decided not to change the default directory. It also creates a standard entry in the Start Menu. I left that for the same reason.
 After a few moments, Prey said that it has been installed and recommends that I configure the settings.
After a few moments, Prey said that it has been installed and recommends that I configure the settings.
The first order of business is to set up a reporting method. Without it, Prey won't do you any good. The two options are standalone and Web-based. The Web-based method allows you to monitor and control the computer from the Prey website. That's what I selected.
 The next step creates an account on the Prey server. You'll be asked for your e-mail address, which is what Prey will use to communicate with you, so be sure that you get it right. Then you create a password, give the computer an identity (the default for this is the computer's name), and specify whether the computer is a notebook or a desktop. Before the system will work, you will need to respond to the verification e-mail that the PreyProject sends you.
The next step creates an account on the Prey server. You'll be asked for your e-mail address, which is what Prey will use to communicate with you, so be sure that you get it right. Then you create a password, give the computer an identity (the default for this is the computer's name), and specify whether the computer is a notebook or a desktop. Before the system will work, you will need to respond to the verification e-mail that the PreyProject sends you.
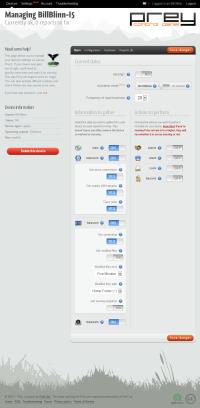 The setup is now complete and the device is being tracked. Easy? The control panel for Prey offers various settings for the computer.
The setup is now complete and the device is being tracked. Easy? The control panel for Prey offers various settings for the computer.
Prey uses the device's GPS if it has that functionality. If not, it will figure out where it is by looking at nearby Wi-Fi hotspots and triangulating. The accuracy is reported to be good but I haven't tested it. If you enable the function, Prey will attempt to connect to the nearest open Wi-Fi hotspot.
Prey allows you to activate any built-in camera, so you might be able to take a picture of the thief using your laptop's webcam. Police like it when you're able to give them this kind of information. You can also grab a screen shot of the thief's active session so you might be able to find an e-mail address or a Facebook account.
If you use Outlook or Thunderbird, you can tell Prey to remove stored passwords to keep the crook for using your identity or just lock down your PC, which makes it unusable until your password is entered.
It's Missing!
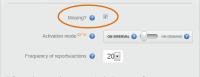 I went to the PreyProject website, logged in, and marked the notebook missing.
I went to the PreyProject website, logged in, and marked the notebook missing.
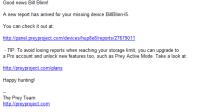 Then I turned on the computer, waited a few minutes and checked my e-mail. There were 2 messages from PreyProject: The first told me that I'd marked the machine missing. The second told me that it had some information. Naturally, I followed the link.
Then I turned on the computer, waited a few minutes and checked my e-mail. There were 2 messages from PreyProject: The first told me that I'd marked the machine missing. The second told me that it had some information. Naturally, I followed the link.
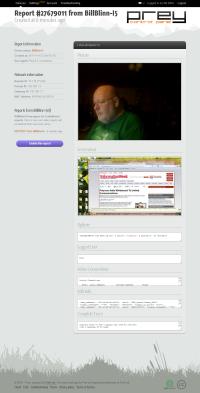 Wow! What do we have here. The report has my picture. That's because PreyProject activated the camera on the computer. (I didn't notice.) It also delivered a picture of what was on the screen.
Wow! What do we have here. The report has my picture. That's because PreyProject activated the camera on the computer. (I didn't notice.) It also delivered a picture of what was on the screen.
The logged-in user is "Bill" so the creep got my user name and password, too! That would be a bad thing if I wasn't the creep.
The computer is currently connected to the Internet (D'oh!) but because it's on a LAN, the IP addresses provided didn't do me any good, but I can see the MAC addresses of a couple of nearby Wi-Fi access points (xx added to obfuscate the addresses):
{"mac_address": "xx-xx-xx-xx-xx", "ssid": "FBI_Surveillance_4267", "signal_strength": "-45", "channel": "2432000", "signal_to_noise": "100"},
{"mac_address": "xx-xx-xx-xx-xx", "ssid": "WOW!617376", "signal_strength": "-73", "channel": "2462000", "signal_to_noise": "43"}
Traceroute might be helpful: Tracing route to www.l.google.com [209.85.145.105]
over a maximum of 30 hops:
1 10 ms 1 ms 7 ms 192.168.1.1
2 * * * Request timed out.
3 10 ms 12 ms 8 ms 10.35.25.30
4 9 ms 12 ms 9 ms 10.35.11.17
5 22 ms 21 ms 22 ms gi1-3.ccr01.cmh02.atlas.cogentco.com [38.104.22.5]
6 22 ms 22 ms 22 ms te3-4.ccr01.ind01.atlas.cogentco.com [154.54.24.253]
7 41 ms 22 ms 21 ms te3-7.ccr01.sbn01.atlas.cogentco.com [154.54.3.29]
8 21 ms 22 ms 23 ms te0-0-0-5.mpd22.ord01.atlas.cogentco.com [154.54.25.62]
9 22 ms 22 ms 21 ms te0-0-0-5.ccr21.ord03.atlas.cogentco.com [154.54.2.98]
10 21 ms 21 ms 22 ms te0-1-0-0.ccr22.ord03.atlas.cogentco.com [66.28.4.66]
11 41 ms 209 ms 204 ms te-9-1.car4.Chicago1.Level3.net [4.68.127.129]
12 27 ms 29 ms 30 ms GOOGLE-INC.car4.Chicago1.Level3.net [4.71.100.22]
13 28 ms 28 ms 29 ms 209.85.254.122
14 29 ms 29 ms 29 ms 72.14.237.108
15 40 ms 38 ms 38 ms 209.85.241.22
16 38 ms 38 ms 38 ms 216.239.43.217
17 50 ms 38 ms 39 ms 216.239.47.173
18 39 ms 37 ms 38 ms cbf02m01-in-f105.1e100.net [209.85.145.105]
Unfortunately, that doesn't give me very much, either. But the picture could be useful and watching what's on the screen might yield an e-mail address, user name, or password that would lead to the crook. If the computer was within range of any public Wi-Fi locations that could be used for triangulation, that information would be provided.
But notice at the left of the picture there's a remote IP address: 75.118.173.245. That is useful because it's identified as belonging to Wide Open West and WOW would be able to provide police with the name of the customer who had that IP address at the time the report was filed. Reports are filed every 20 minutes and the free service will retain the most recent 10 reports.
 I got a bit more insistent and turned on an alert. The alert message never showed up on the remote computer (probably an error on my part) but I've seen enough to consider this a worthwhile service.
I got a bit more insistent and turned on an alert. The alert message never showed up on the remote computer (probably an error on my part) but I've seen enough to consider this a worthwhile service.

 Maybe You Can Recover Your Computer If It's Stolen
Maybe You Can Recover Your Computer If It's Stolen
Free and easy to set up, the PreyProject monitor checks in when you tell the system your computer is stolen. Numerous configuration features make this a complete solution without making it needlessly complex.
For more information, visit the PreyProject website.
Protecting Your Connection
(No, not THAT kind of "connection"!) The RSA SecurID system is what's called a two-factor authentication system. If you work for some government agencies or for companies that handle sensitive data, you may already know what a two-factor authentication system is because you might be using one. If not, you might wonder how it works and why it could be important.
Two-factor systems such as the RSA's SecurID use something that you know (typically a password or a personal identification number) coupled with something you have (an authentication device that attaches to the computer or that provides additional information known only to the device and the system that's being protected). Effectively each time you log in using such a device, you have a one-time password.
The problem with individual, static passwords is that people choose weak passwords or write them down or use the same credentials for multiple systems. This makes the passwords easy for bad guys to obtain and use.
 The RSA SecurID changes your password every 60 seconds via a small device that is issued to the user. The user creates a password or PIN that remains the same. To log on, the user must have both the PIN and the 6-digit number displayed on the SecurID key.
The RSA SecurID changes your password every 60 seconds via a small device that is issued to the user. The user creates a password or PIN that remains the same. To log on, the user must have both the PIN and the 6-digit number displayed on the SecurID key.
The RSA solution isn't the only solution in the marketplace but it's the only one that I have experience using. Some companies depend on USB tokens or smart cards but these devices, if lost, can be used without a PIN or password.
RSA's SecurID is probably the market leader, possibly because the system is extremely easy to use. Once the user has created a PIN, logging on requires only the user ID, the PIN, and the ability to type 6 digits that are clearly displayed on the portable key.
Windows 8: Still in Pre Beta
Microsoft's upcoming hybrid operating system (the one that spans devices from phones to servers) still hasn't reached beta status but lots of people, including me, are trying to read into what is essentially alpha software what the final product will look like. This isn't entirely an exercise in futility and Microsoft is certainly paying attention to what is said in various forums by people who have downloaded and are using the operating system now.
Security and Usability
These are almost always two sides of the same coin. A highly secure system's usability will suffer and a highly usable system's security will suffer. Progress has been made in these areas but there's always some tension between developers on the security team and developers on the usability team.
When you first use Windows 8 PC, you'll be instructed (the system is really asking you but it's phrased more like an order) to use a Windows Live account with it. If you accept the recommendation, your Windows Live credentials are used to create your account. By using your Windows Live credentials, you can move from one computer to another and some of your settings will follow you.
The Windows Live credentials are fine on a desktop or notebook but typing what might be a long and complex password on a tablet will annoy some people. So if you have a tablet, you can specify a picture password. To authenticate yourself, you must select one picture from several that are shown and then complete three gestures: You might choose a picture of your cat, draw circles around his ears (1 gesture for each circle) and pull his tail (tap and drag, the 3rd gesture).
That's all good but the open source community is concerned about some other Windows 8 security measures—ones that might hamper users' ability to set up dual-boot systems with Windows 8 and Linux.
Windows 8 and Linux
Red Hat, Canonical, and the Linux Foundation have gone directly to hardware manufacturers with recommendations that they say will allow the two operating systems to be installed on a single computer.
But at least some Windows 8 computers will ship with Unified Extensible Firmware Interface (UEFI) secure booting enabled. This would make it more difficult either to replace Windows with a version of Linux or to dual-boot Windows and Linux. To display a Designed for Windows 8 logo, PCs must have the secure-boot feature enabled and this prevents any operating system that hasn't been signed by a trusted Certificate Authority from booting.
The feature can be enabled or disabled by the computer's standard boot setup but only if the hardware vendors provide the CMOS setting. The Linux community is concerned that manufacturers will enable secure boot and won't provide the option to disable it.
The problem is that UEFI is a great idea that protects users. But it's a feature that could impede users who want to use their computers in what the manufacturer might consider a non-standard way.
Red Hat and Canonical both concede that UEFI secure boot is a good security measure against malware because it protects against rootkits. The new technology also allows IT departments to specify which operating systems can be booted on specific computers.
My guess, and that's all it is at this point, is that manufacturers will serve both communities: For large corporate accounts and those who want to ensure that UEFI is always enabled, the manufacturer might provide a model that omits the option to disable it. For those who wish to create dual-boot systems, the protection could be disabled.
Read all Windows 8 reports here.
Short Circuits
Adobe's Interesting Week
Interesting weeks are not always good weeks and so it was with Adobe this week. The company announced plans to lay off hundreds of employees and also said that it will stop developing Flash for mobile devices. That will have significant repercussions for non-mobile devices, too.
Oddly, the layoffs come as Adobe has predicted record-setting revenue for the current quarter and it's not a small lay-off: 750 positions or about 7½% of Adobe's jobs. Not all of the changes will affect current employees; in some cases, Adobe will eliminate positions that are currently open.
Speaking for Adobe, Jodi Sorensen said that the reductions will be felt in all of the company's many business units. Adobe expects the layoffs to cost about $90 million with most of the money going to employees in severance payments and those costs will reduce the company's overall net income from what it had predicted. As a result of that, the company's stock took a pounding on Wall Street following the mid week announcement.
Flash in the Pan
Many Web applications depend on Flash but Apple refused to support Flash on its popular mobile devices and now Adobe says that it will halt development of the multimedia platform for mobile devices.
Flash became available for mobile devices only last year and never caught on as HTML5 and CSS3 brought Flash-like capabilities to browsers that support them. Despite being an important part of early Web technology when Macromedia developed it, Flash has run its course.
Adobe supports HTML5 in its Web development tools and says that HTML5 the best solution for creating and deploying content across mobile platforms.
Adobe carefully noted, though, that Flash will continue to be available for standard browsers running on standard desktop and notebook computers.
One might reasonably expect that a significant number of the layoffs announced this week will be directed at the Flash team.
Senate Goes for Net Neutrality
I was beginning to think that Net Neutrality might be a lost cause and maybe it is but for now it lives. President Obama will not be forced to veto a resolution that would have prohibited the FCC from implementing Net Neutrality rules because the Senate voted down that resolution this week.
Net Neutrality still doesn't have a clear path. The measure lost on Wednesday by just 6 votes—52 to 46—and 2 senators didn't vote.
The Net Neutrality rules were the FCC's response to a court ruling in 2008, won by Comcast, after the FCC fined the cable company for throttling some types of traffic. At the time the court said that the FCC's lack of rules on the subject meant they couldn't take action against Comcast.
So the FCC created rules that will apply to Comcast, the nation's largest cable company, and all other cable companies. Among the types of traffic Comcast impeded was peer-to-peer streams, including BitTorrent.
Oddly, opposition to the new rules comes not just from those who oppose the concept of Net Neutrality but also from those who want more of it. Activists at Free Press have filed suit against the FCC because of exemptions for mobile Internet providers that they say are illegal.
The debate is far from over. Verizon has filed suit to block the rules. In addition, a Republican in the White House would likely press the FCC, whose chairperson is a political appointee, to favor companies such as Verizon and Comcast over Net Neutrality.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
