|
|||||||||||||||||||||||||||||||||||||||||||||||||||||
| Previous page | Do you use a pop-up blocker? If so, please read this. | ||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||
| Show Date: 2007.05.27 | |||||||||||||||||||||||||||||||||||||||||||||||||||||
The Bat continues to fly highI've been using an e-mail program called The Bat since 2002, if not before. In 2003, I wrote "I'm a fan of The Bat and ... Version 2 has been in development for at least 2 years." Now RIT Labs (Moldova) is heading for version 4, having just released version 3.99. In 2003, I said "[v]ersion 2.0 looks and feels a lot like the version 1.6 . I can see some new features and some improvements, but overall the program hasn't been upgraded beyond all recognition. This is good." More than a dozen releases of version 3 have continued along improvement path, slow and steady. I suspect and hope that version 4, whenever it's released will be evolutionary instead of revolutionary.
I go through the e-mail accounts and pitch old messages from time to time, but I keep a lot of reference materials in the program because The Bat has a superb search feature (far better than the one in Outlook, which I use at the office.) There's a certain amount of trust involved in storing 16,000 messages that go back 5 years and The Bat has earned that trust over the years. My favorite featuresIn no particular order, here are features that I find particularly useful: The ability to examine any part of an inbound message and, with a remarkable set of of logical comparisons, decide whether to put the message in a special folder, highlight it, delete it immediately, reply to it with a special message, play a sound, print the message, forward the message to someone else, or do some combination of those acts (and more). And when it comes to identifying messages, here's an example of a relatively simple rule (in plain English): If the subject line contains either "[This]" or "[That]" and the "from" part of the header is "Joe" or "Jean" or "Bob", then delete the message from the server and delete it from the program." It's easy to build stacks of comparisons bad on "and", "or", "and not", and "or not". This feature alone saves several minutes per day. These filters can be applied to inbound messages, outbound messages, messages once they've been read, and to replies. If the existing headers are insufficient for sorting, you can add your own. In most cases, my outbound messages go to a folder called "to be deleted". That's because most of my messages aren't particularly important. After a week or two, they can safely be deleted. But messages to clients, family members, and the like should be saved. I created a special header called "X-Save" and if I'm sending a message I want to save, I write the name of a folder in the field and when The Bat sends the message, it puts my copy in the folder I specified. If the field is empty, the message goes to the "to be deleted" box. Easy. When I write a message as the technology tsar, I'd like my signature to reflect that; when I write a personal message from my personal account, the signature should reflect that; and when I send a message to a discussion list, I'd like a completely different signature. The Bat accommodates this with ease because signatures (and other account information) may be specified either by account or by folder within an account. The Bat has quick templates. These make it possible for me to send short or long (sometimes very long) messages to people with just a few keystrokes. A few years ago, my gall bladder and I had a little run in and I spent a few days in the hospital. When I got back, I found a lot of messages asking what happened, so I created a quick template that I called "sick". To reply to an inquiry, all I had to do what hit Ctrl-R to reply to the message, type "sick", and press Ctrl-spacebar. The result: If you've noticed an excess of nothing from me for a few weeks, that's because I've been sick. Gallstones feel rather like what I would imagine it feels like to be shot in the stomach at close range, but I'm hoping not to make that actual comparison. Surgery is in my future, but all is well now following a night in one of the local hospital's emergency room and 3 more days in a room where people kept waking me up to stick needles in. I used the experience to write a short report about how much medical technology has changed. If you're interested, it's here: http://www.techbyter.com/2004/20040404.shtml and if you're not interested, it's still there. Easy to learn? Not exactlyIn 2003, I complained that "documentation is still a sore spot. The Bat is astonishingly powerful and almost infinitely customizable. The problem is that the documentation doesn't reveal the application's strengths and Microsoft has slammed Outlook Express onto every Windows computer, so that's what a lot of people use even though the Toronto Star once referred to the application as LookOut." Documentation is better than it was (no manual, of course; it's all on-line) but it still covers only a tiny fraction of what the program is capable of doing. Generally, if you can think of something you'd like an e-mail program to do, The Bat probably does it. The challenge is finding out how to make it work. Overall: The Bat is the most powerful e-mail application you'll find on this planet, but you'll have to deal with minimal documentation.
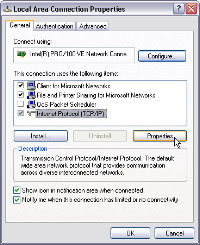
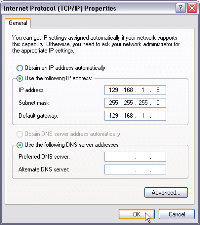
I'd really like to give The Bat a 5-cat rating, but the lack of good documentation limits the rating to "just" 4 cats. For more information, visit the RIT Labs. Networking problemsLate last week, I sat in the Jet Blue terminal at JFK airport in New York City. When I tried to connect to the free WiFi hotspot that Jet Blue provides, the result was a connection but no ability to reach any e-mail or website services. A quick analysis of the situation revealed that the problem was not with my Apple Powerbook. All around me, I saw people with Mac and Windows machines trying to connect and failing; some of them were more persistent than I was, but nobody was successful. In another part of the terminal, the WiFi system was operating properly. It would have been helpful if JetBlue personnel had let people know about the problem. The most frustrated users seemed to be those with Windows machines, but it wasn't a Windows problem. Networking can be frustrating. As I watched the scene play out at JFK, I thought about a problem I was trying to help a client with several weeks ago. He was having trouble getting two machines on his local network to see each other. Here are some of the suggestions that we sorted through: Try creating a new user make him a member of administrators local group (for testing) on both machines. Use the exact same name on both machine and the exact same password. I think you're using the machines without user IDs and logins and this may create problems with networking, which is assumed to want security. Also, I would enable netbios over TCP/IP. Local area connection properties--TCP/IP properties--Advanced then under WINS tab. Try to map a network drive to other computer's share go to command prompt type NET USE x: \\computer2\share1 After mapping, try to explore. If you can access the files, then the problem was with name resolution and you should edit your HOSTS file.
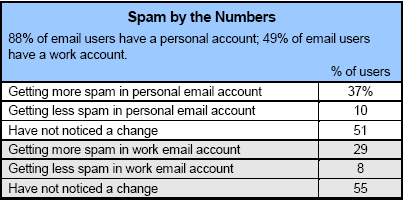
The solution? Easy. He hired a network security consultant to visit the site and sort things out. When you're approximately 1947 miles from the client, it's hard to do the kind of job that should be done on-site. Nerdly NewsApple's anti-theft patent approvedApple filed a patent application in 2004 for an anti-theft system that the company says will protect mobile devices. Laptop computers, Ipods, mobile phones, and other small but valuable devices are common targets of theft. Apple's idea is for the mobile device to track its own motions and to watch for unusual motions. Apple says that when a mobile device is being stolen, unusual movements occur--bumping and shaking for example. A device that detects these unusual motions could lock itself or sound an alarm. Having just returned from a week in New York City where approximately 30% of all subway riders seem to be sporting Ipods, I have to wonder how the devices will tell the difference between theft-related bumping and shaking and the bumping and shaking that occur on a subway, in a bus or car, or on a bike. Individuals have generally detectable typing patterns and it's possible for a security system to observe typing patterns and to shut down the system if the usual user isn't typing. That technology isn't included in Apple's US patent, but it's an example of technology that works properly but can fail in a widespread implementation. In a corporate environment where individual users have assigned computers, such a system can detect unauthorized use. But the system can cause problems when a user forgets the detection system is active, allows someone else to use the computer, and then has to figure out how to unlock the system. Apple would address the mass transit issue by providing software to adjust the sensitivity of the anti-theft software. Users could also turn it off. And after approximately one false alarm, that's probably what some users will do. Spam increases, but we're dealing with itA comprehensive survey by the Pew Internet & American Life Project says we're getting more spam than ever, but we're less concerned about it because we're getting smarter about controlling the spew. The survey reports that 71% of e-mail users use filters offered by their e-mail provider or employer to block spam. Several years ago, I said that unchecked spam could effectively kill the Internet. The useless CAN-SPAM act has had little effect, but users themselves have adapted. Even so, 55% of e-mail users say they have lost trust in e-mail because of spam. That's sad because spam is so easily recognized that it need not be a source of confusion or lost trust. Pew conducted the phone survey between February 15 and March 7, 2007, among a nationally representative sample of 2,200 American adults. In the sample 1,405 of the respondents were e-mail users and the margin of error on this group is plus or minus 3 percentage points. More than one third (37%) of e-mail users said spam had increased in their personal e-mail accounts and 29% said they had seen an increase in work accounts. Both of those figures increased from what users reported 3 years ago in a similar study.
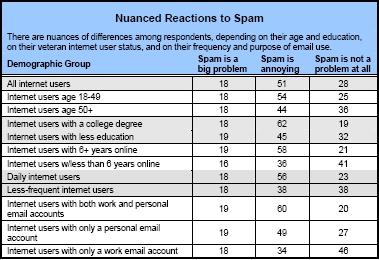
What has changed?Attitudes. Three years ago, 25% of users said spam was a big problem for them. Now only 18% of users feel that way and 28% (up from 16%) say spam is not a problem for them. That parallels my experience. Three years ago, I considered spam to be a big problem. Today, because of some sophisticated filtering, it is no longer a problem. In the middle, about half of all e-mail users consider spam an annoyance, but not a big problem.
According to the Pew researchers, "There appear to be several reasons fewer people say that spam is a big problem for them. First, the volume of most offensive kind of spam has decreased. And second, people are becoming more knowledgeable about spam, and they know better how to handle it." More than two thirds of users (68%) say they almost never unintentionally open an e-mail message without realizing it is spam and 27% say they do that occasionally. Only 5% say they often open a spam message without realizing what it is. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||
| Home • Programs • Reference • Subscribe to Technology Corner News • Contact Us • Terms of Use ©2007 by William Blinn Communications. All rights reserved. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||
This is the only ad you'll ever see on this site. It's for my website host, BlueHost in Orem, Utah. Over the past several years, they have proven to be honest, reliable, and progressive. If you need to host a website, please click the banner below to see what BlueHost has to offer. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||

|
|||||||||||||||||||||||||||||||||||||||||||||||||||||

 The screen graphic shows the changes made between version 3.98.4 and 3.99.3. As you can see, it's a long list and these are just the changes between two minor step releases separated by about 45 days. One thing that has always impressed me about the way RIT Labs works is that they're not afraid to call a bug a bug: "The option in the account properties to use non-encoded 8-bit characters in the message header now works properly." The release notes included with each new version always differentiate clearly between major improvements, added features, improved/changed features, and bug fixes. If you want to see the list, it's
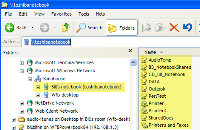
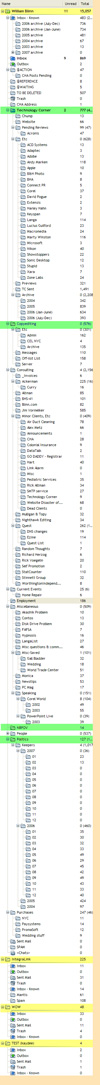
The screen graphic shows the changes made between version 3.98.4 and 3.99.3. As you can see, it's a long list and these are just the changes between two minor step releases separated by about 45 days. One thing that has always impressed me about the way RIT Labs works is that they're not afraid to call a bug a bug: "The option in the account properties to use non-encoded 8-bit characters in the message header now works properly." The release notes included with each new version always differentiate clearly between major improvements, added features, improved/changed features, and bug fixes. If you want to see the list, it's  The image at the left (sorry, but you can't click this one to see a larger version; it's a security issue) shows all of my e-mail accounts, sub-accounts, and folders. The sections I've highlighted in yellow show my primary (actual) accounts. Those lines shown with a green overlay are special addresses that are forwarded to the main account and then sorted separately on arrived. The lines that have no special coloring are folders within the accounts.
The image at the left (sorry, but you can't click this one to see a larger version; it's a security issue) shows all of my e-mail accounts, sub-accounts, and folders. The sections I've highlighted in yellow show my primary (actual) accounts. Those lines shown with a green overlay are special addresses that are forwarded to the main account and then sorted separately on arrived. The lines that have no special coloring are folders within the accounts.