Listen to the Podcast
1 Mar 2024 - Podcast #871 - (17:20)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
It was an afternoon pretty much like any other when I received a message from one of my elder daughter’s high school friends. “Hi, Mr Blinn, I think Liz’ FB profile was hacked and someone is pretending to sell things on your behalf. Can you please let her know? I don’t have her cell.”
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
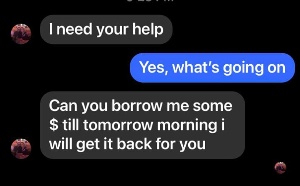 Oddly enough, I had just been having what appeared to be a conversation with Elizabeth. She was asking if I could loan her $300 until the next day. There were clues in the messages—lots of them—that a scam was afoot, but I missed them all. The messages had come from Elizabeth’s Messenger account because I could see previous discussions.
Oddly enough, I had just been having what appeared to be a conversation with Elizabeth. She was asking if I could loan her $300 until the next day. There were clues in the messages—lots of them—that a scam was afoot, but I missed them all. The messages had come from Elizabeth’s Messenger account because I could see previous discussions.
 But then Phyllis brought her phone to me. She had received similar messages. And then we got a copy of a post that “Elizabeth” had made in Facebook. She was offering about 25 items, including a big screen TV, furniture, a golf cart, and a riding mower for sale because, the post said, “we are clearing out items from my dad’s house (he got moved to aged care) and he is no longer in need of these items and he is glad to have the extra money for other expenses on coming holidays. We have a truck and can deliver at a small extra fee. Send a Dm if interested in any item...”
But then Phyllis brought her phone to me. She had received similar messages. And then we got a copy of a post that “Elizabeth” had made in Facebook. She was offering about 25 items, including a big screen TV, furniture, a golf cart, and a riding mower for sale because, the post said, “we are clearing out items from my dad’s house (he got moved to aged care) and he is no longer in need of these items and he is glad to have the extra money for other expenses on coming holidays. We have a truck and can deliver at a small extra fee. Send a Dm if interested in any item...”
A request to share the message had been added and then comments had been disabled so it would be impossible to add a comment calling out the scam. Then the penny dropped.
 Suddenly it was obvious that it was a scam and that someone had taken over her account. The clues were obvious and I should have recognized them immediately.
Suddenly it was obvious that it was a scam and that someone had taken over her account. The clues were obvious and I should have recognized them immediately.
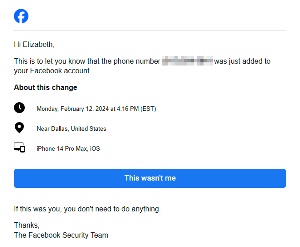 We came to this realization just a bit late, though, several people had reported the scam and by the time we started trying to take back the Facebook account, Facebook had shut it down. Elizabeth couldn’t sign into the account. When I found the expected warning from Facebook in her email and started the recovery process we were out of luck.
We came to this realization just a bit late, though, several people had reported the scam and by the time we started trying to take back the Facebook account, Facebook had shut it down. Elizabeth couldn’t sign into the account. When I found the expected warning from Facebook in her email and started the recovery process we were out of luck.
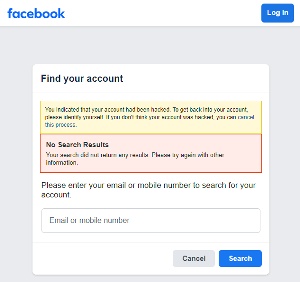 Facebook does have a procedure in place to give members a way to recover a stolen account, but it depends on a lot of things Elizabeth didn’t have. She hadn’t set up two-factor authentication and her government ID card shows neither the name Facebook knows her as or the address where she was living years ago when she signed up. We tried working through the process described on Facebook’s Hacked page as well as the Facebook Account Recovery page. We expected the process to fail and we were not disappointed.
Facebook does have a procedure in place to give members a way to recover a stolen account, but it depends on a lot of things Elizabeth didn’t have. She hadn’t set up two-factor authentication and her government ID card shows neither the name Facebook knows her as or the address where she was living years ago when she signed up. We tried working through the process described on Facebook’s Hacked page as well as the Facebook Account Recovery page. We expected the process to fail and we were not disappointed.
If something like this has happened to you and you need a comprehensive summary of how you might be able to recover the account, ReasonLabs has a good one.
Two bad things can happen to Facebook accounts. The account can be compromised. Some call this hacked or stolen; or it can be cloned. Recovering from a cloned account is easier because the crook has only created a facsimile of your account, not gained access to it.
Which has happened to you?
So we wanted to protect the new account from both cloners and hackers. The most effective way to avoid having your account cloned is to make it less attractive to cloners by making it impossible for anyone but you to see your friends list.
To make the friends list private, click the Facebook menu button, the down-pointing triangle in the upper right corner of the Facebook site, and choose Settings & Privacy from the menu. Click Settings on the next menu, and then choose Privacy on the settings page and type “friends” into the search box. Click Who can see your friends list? At the very least, change the setting to Friends, but the safer choice is Only Me.
That is the single most important change you can make. It’s the one that tells cloners they won’t find much joy in your account, but there are other steps that you should consider. Return to the Settings & Privacy menu and click Privacy Checkup. Work through each of the menu items on the Privacy Checkup page. Read the descriptions and decide what safeguards you’d like to establish. Plan to spend some time on this, reading the explanations and considering the alternatives.
Making your account undesirable to cloners will protect it.
But you really want to avoid the nastiest nasties, the ones that gain access to your account. Normally this is done using social engineering that tricks you into giving scammers your user name and password. We haven’t figured out how someone obtained Elizabeth’s credentials and probably we never will.
Unfortunately, she used the same weak password for Facebook, Instagram, Gmail, and financial accounts so the first task was changing passwords for the other accounts so that they would differ from each other but each would individually be strong. With that out of the way, we moved on to obtaining a password manager for her and setting two-factor authentication whenever possible.
Those are the best actions available to safeguard your Facebook account, too: Strong password, two-factor authentication, and a unique password for every account. I disagree with frequently heard recommendations to change passwords frequently. If you have strong passwords and don’t share passwords between accounts, changing passwords moves far down on the list. There are other tips such as always log out of Facebook when you’re done—especially on public computers, don’t use public Wi-Fi hotspots unless you have enabled a VPN, enable alerts for logins from new computers for all sites that support the option, and don’t ever click a link on a page on in an email that says it wants to “verify” your account information.
As usual, a little caution and well-advised paranoia go a long way in the battle to maintain control of your accounts and your money.
Hedy Lamar was, without a doubt a beautiful and talented actor from a time when female actors were called actresses. She starred in a lot of films, was arrested a couple of times for shoplifting, and invented things in her spare time.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 One of the things she invented was called a “Secret Communication System” and she filed a patent for it in June 1941, when World War II was underway in Europe, but the US hadn’t yet joined the battle. What the patent describes is a frequency-hopping communication system and was proposed as a way to make torpedos more accurate. Today we call the technique “spread spectrum frequency hopping” and it’s used in Bluetooth devices, mobile phones, and GPS systems.
One of the things she invented was called a “Secret Communication System” and she filed a patent for it in June 1941, when World War II was underway in Europe, but the US hadn’t yet joined the battle. What the patent describes is a frequency-hopping communication system and was proposed as a way to make torpedos more accurate. Today we call the technique “spread spectrum frequency hopping” and it’s used in Bluetooth devices, mobile phones, and GPS systems.
 1941 is 83 years in the past. If computers were being thought of at all, they were envisioned as devices that weighed tons and filled large rooms. During spare time on movie sets, Lamarr sketched out ideas for better traffic signals, a tablet that could be dropped into water to create a fizzy drink, and systems intended to control torpedos and sink Nazi ships.
1941 is 83 years in the past. If computers were being thought of at all, they were envisioned as devices that weighed tons and filled large rooms. During spare time on movie sets, Lamarr sketched out ideas for better traffic signals, a tablet that could be dropped into water to create a fizzy drink, and systems intended to control torpedos and sink Nazi ships.
The German navy was proficient at jamming radio signals that guided torpedos, but Lamarr suggested that a communications system that frequently changed from one frequency to another would be harder to jam. That sounds simple but it’s much more complex in practice because both the sender and the receiver must switch between frequencies at exactly the same time and they must do so apparently at random.
The work was in vain for World War II, but the US Navy used the technology during the Cuban Missile Crisis in 1962, and today just about everybody carries a bit of the technology with them every day.
You may already have heard this story. It’s certainly not a secret, but Lamarr was an actor (sorry, “actress”) and inventing isn’t something motion picture stars are known for. Even though reports like this one crop up every so often, Hedy Lamarr’s contributions to modern technology aren’t as well known as they should be.
I’m amused by what is termed “bloatware”. It seems that any computer technology someone doesn’t like, doesn’t understand, or fears gets that label. The same term has been applied for at least a couple of decades to new features that Microsoft has added to Word and Excel.
But how did all that bloatware get into Word and Excel? I don’t dispute that these applications have many features that are unnecessary from my perspective. Those last three words are important: “from my perspective”. Those useless (to me) functions were added because users asked for them.
Should a word processor be able to create layouts with multiple columns and images? In my world, no. That’s because these are publishing and layout functions that are better handled by an application such as InDesign, or even by Microsoft Publisher. But some users wanted to be able to create newsletters and such using a word processor. What is bloatware to one person is an essential feature for another.
It’s not clear that anybody asked Microsoft to add AI features like Copilot to Windows, but it’s a good bet that some users will like it a lot. Speech recognition, autocorrect, predictive keyboard functions aren’t new. Some of the technologies go back more than 20 years, but they’re much better now than they were. That doesn’t mean they’re perfect, and it’s still a trivial effort to locate and laugh at idiotic errors.
One pundit was promoting BloatyNosyAI, an application intended to remove AI apps. The problem is that using it may be more troublesome than just ignoring the AI apps. Ashwin, writing on ghacks.net, described it this way: “Compared to regular programs, BloatynosyAI is not a straightforward app, as in it does not have a normal interface with buttons that you can click on to disable the bloat. Instead, you will need to interact with it just like you would with an AI assistant. That’s ironical [stet], using an AI-powered app to remove an AI app is some sort of 4D chess move.”
So you don’t like AI, but you’re willing to entrust AI with decisions about what is AI bloatware on your computer so that you can remove it. Really? That sounds a lot like walking into a Toyota dealership and asking why you shouldn’t buy a Volkswagen. Or perhaps like asking the CEO of Exxon to explain why electric cars are better than those powered by gasoline.
The influence of artificial intelligence will continue to expand and the systems will become more useful in the coming weeks and months. If you’re not a fan of AI, though, just don’t use it. The concept of using AI to remove AI just seems so illogical.
