Listen to the Podcast
19 Jan 2024 - Podcast #865 - (17:49)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Two applications from Sysinternals sound alike, have substantially different functions, and play together well when you’re looking for the cause of a problem with a Windows computer. Process Monitor and Process Explorer were created by Mark Russinovich and Microsoft quickly saw the value of the Sysinternals suite and acquired the company. It’s been part of Microsoft since 2006.
A bit of background first, if I may. When released in 1996, the suite of tools intended to diagnose, troubleshoot, and monitor Windows systems was called NT Internals. The suite is free and can be downloaded from Microsoft. The applications are not installed. Instead, users simply run the ones they need when they need them and the suite contains the 74 utilities used for troubleshooting and monitoring. (AccessChk, AccessEnum, AdExplorer, AdInsight, AdRestore, Autologon, Autoruns, BgInfo, BlueScreen, CacheSet, ClockRes, Contig, Coreinfo, Ctrl2Cap, DebugView, Desktops, Disk2vhd, DiskExt, DiskMon, DiskView, Disk Usage (DU), EFSDump, FindLinks, Handle, Hex2dec, Junction, LDMDump, ListDLLs, LiveKd, LoadOrder, LogonSessions, MoveFile, NotMyFault, NTFSInfo, PendMoves, PipeList, PortMon, ProcDump, Process Explorer, Process Monitor, PsExec, PsFile, PsGetSid, PsInfo, PsKill, PsList, PsLoggedOn, PsLogList, PsPasswd, PsPing, PsService, PsShutdown, PsSuspend, PsTools, RAMMap, RDCMan, RegDelNull, RegHide, RegJump, Registry Usage (RU), SDelete, ShareEnum, ShellRunas, Sigcheck, Streams, Strings, Sync, Sysmon, TCPView, VMMap, VolumeID, WhoIs, WinObj, ZoomIt)
A few other utilities from Sysinternals are also available, but are not needed for troubleshooting or monitoring, so they are not included in the suite.
It’s important to understand the differences between these two similar sounding applications:
Process Monitor lets the viewer see detailed information about all processes running on the system. It shows details about events triggered by specific processes and displays, by default: details, operation, path, process ID (PID), process name, result, and time. Twenty additional fields are available to display more information about each process. The user can set filters on any field to limit what data is displayed and log events for troubleshooting. There’s also a process tree that shows how parent and child processes are related.
Process Explorer helps users understand how various applications are working on the computer. Using a tree structure, it shows the files, directories, and other processes each parent process controls. A “handle mode” shows which window handles each process has opened and “DLL mode” lists the DLLs (dynamic link libraries) and memory mapped files each process has opened.
Process Monitor is a good choice when you need to track how various processes interact by monitoring and logging events that are triggered by each process. It captures an immense amount of data, so Process Monitor is most useful when the user explicitly limits what is collected by carefully starting and stopping the utility and by setting filters. Process Explorer aims to reveal the relationships between parent and child processes so the user can examine properties and parameters for each process.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
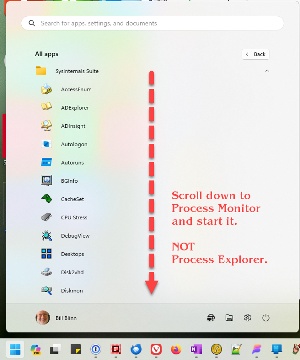 Get started with these two utilities by downloading the individual apps or, preferably, by downloading and unpacking the entire Sysinternals suite, which will then appear in the Start Menu’s All Apps section. Then scroll down to the utility you want to use and select it. For now, we’ll look at Process Monitor. You’ll get better results by running both as Administrator.
Get started with these two utilities by downloading the individual apps or, preferably, by downloading and unpacking the entire Sysinternals suite, which will then appear in the Start Menu’s All Apps section. Then scroll down to the utility you want to use and select it. For now, we’ll look at Process Monitor. You’ll get better results by running both as Administrator.
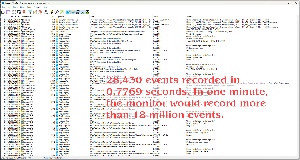 What you’ll see immediately is a huge list of events, and by “huge” I mean a list of nearly 30,000 events collected and logged in less that one second. How can anyone make sense of that much data? Clearly Process Monitor is not a utility you want to run for a day or two to collect clues. By extrapolation, it would log more than 18 million events per minute on my computer. Any individual event would be a minuscule needle in an unimaginably gigantic haystack. Too much information is just as bad as too little information.
What you’ll see immediately is a huge list of events, and by “huge” I mean a list of nearly 30,000 events collected and logged in less that one second. How can anyone make sense of that much data? Clearly Process Monitor is not a utility you want to run for a day or two to collect clues. By extrapolation, it would log more than 18 million events per minute on my computer. Any individual event would be a minuscule needle in an unimaginably gigantic haystack. Too much information is just as bad as too little information.
The trick to using Process Monitor involves shutting it down and clearing the log immediately after starting it, establishing some filters, and opening the application that has a problem you’re trying to troubleshoot. Then it’s time to enable Process Monitor, perform the task that generates an error, and quickly halting Process monitor.
The filter should be set to log operations only for the troubled application.
You’ll find lots of videos online that cover the details of how to use Process Monitor and, I’ll avoid the temptation to include details here because the techniques will vary depending on what specific kind of problem you’re trying to identify. Basically, though, limiting Process Monitor’s log time and carefully filtering the captured events will return a manageable list.
Start Process Explorer by opening the Start Menu, selecting Sysinternals from the All Apps list and then scrolling down to select Process Explorer and run it as Administrator.
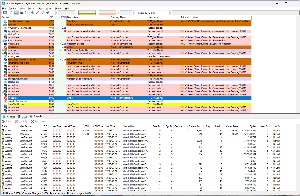 Process Explorer displays all running processes in the top pane and you may be astonished by how busy the computer is even when it only sitting there waiting for you to type something. This utility can be thought of as Task Manager’s big sister. It does everything Task Manager can do and a lot more.
Process Explorer displays all running processes in the top pane and you may be astonished by how busy the computer is even when it only sitting there waiting for you to type something. This utility can be thought of as Task Manager’s big sister. It does everything Task Manager can do and a lot more.
The bottom pane can be hidden or used to display handles, DLLs, or threads.
Process Explorer’s Process tab lets the user kill, suspend, or restart any process, as well as view the process’s properties, investigat the process via VirusTotal.com, or perform a web search for information about the process.
To get a better understanding of how these two utilities can help you identify and solve problems with your computer, I recommend two YouTube videos by Windows IT Pro. For Process Monitor, see a video by Sami Laiho. The video is slightly less than 30 minutes long. And for a better understanding of Process Explorer, see the video by Pavel Yosifovich, which runs just a bit more than 30 minutes.
These two utility functions from Sysinternals won’t solve every problem a computer might have, but they will provide useful insights that reduce the time needed to identify and resolve issues.
Sounds are important. Take a look at the credits following a motion picture and you may see the word “foley”. That’s the term that describes the person who makes the action seem real. Sounds are also important for podcasts and for radio programs.
Foley refers to the reproduction of everyday sound effects that are added to films, videos, and other media in post-production to enhance audio quality. Last century when I was a student at (the) Ohio State University, the instructor of a film course I was taking played two versions of a scene from the television program “Gunsmoke”. The scene involved a fight and the first version’s sound effects were horrible. Laughable. The fact that I remember this more than 50 years later shows how much of an effect it had on me.
Sadly I don’t remember the name of the instructor, but I do remember the point he was making—that sounds were critical to the audience’s perception of the scene.
Sound-effects artist Jack Foley is the person the work is named after. Foley effects are subtle, the swish of clothing, footsteps, squeaky doors, and more. Often they’re so subtle that you don’t even notice they’re there. National Public Radio long-form reports often make excellent use of Foley effects by laying sounds recorded on scene behind the reporter and those being interviewed.
When things go wrong, the results are laughable. A radio blooper from the 1950s or earlier has one actor threatening to shoot another. The Foley artist either had a problem with the gunshot effect or wasn’t paying attention, so the actor improvised by threatening to stab the victim. Then there was a gunshot. Oops.
Successful Foley effects, just as successful typography, must not call attention to itself. If someone who is reading a magazine or other article thinks about how attractive the typeface is, the designer has failed. If a listener or viewer recognizes sounds as a sound effect, the Foley artist has failed.
So one important thing to consider is how loud the effect is. I use the sound of the late Chloe Cat in both the donation request and the program close. I think the loudness of the meow is OK because I explicitly reference it in the recording, but it’s louder than it should be if it was intended to be there only to indicate the presence of a cat.
Several resources exist online to provide Foley effects and instrumental effects such as a “cinematic into” from Pixaby.
Or maybe you need a tympani (kettle drum) effect from Freesound.
There’s no shortage sources for free sound effects. They’re not as complete or as good as sources that you’ll need to pay for, but they may be adequate if you’re careful about adding sounds to your productions. Examples:
Some Windows users like to keep all of their commonly used applications on the desktop. That has never been my preferred method, but one of the applications included in Stardock’s Object Desktop suite has convinced me to make better use of the Desktop.
Icons inside Fences containers can appear and disappear, and that is the primary advantage the utility brings to your computer. I have never been a fan of placing icons on the Desktop because the only way to use them involves closing or minimizing applications that are running. That’s unacceptably inefficient for me because I usually have a dozen or more apps open. Fences fixes that.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
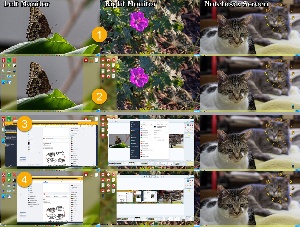 The image shows all three screens on my system. (1) When Fences is hiding, the Desktop is clean. Double-clicking anywhere on the Desktop (2) reveals the icons and double-clicking any blank area of the Desktop hides them again. This functionality can be turned on or off at the user’s discretion.
The image shows all three screens on my system. (1) When Fences is hiding, the Desktop is clean. Double-clicking anywhere on the Desktop (2) reveals the icons and double-clicking any blank area of the Desktop hides them again. This functionality can be turned on or off at the user’s discretion.
Running applications naturally (3) appear above the Desktop icons whether the applications are full-screen or not, and this has been my long-time objection to using the desktop. The Peek function, which can be enabled or disabled by the user (4) displays the icons on top of the running applications when the user presses one of 11 specific keyboard shortcuts. The default is Win-Spacebar. The icons return to the background after the user has double-clicked one to launch an application or open a file, or clicks anywhere on any running application.
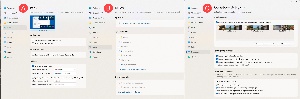 The extensive settings make Fences an uncommonly robust application. Most of the functions can be enabled or disabled and, when enabled, can be activated using one of several options. The Settings Panel has tabs for nine specific types of functions:
The extensive settings make Fences an uncommonly robust application. Most of the functions can be enabled or disabled and, when enabled, can be activated using one of several options. The Settings Panel has tabs for nine specific types of functions:
Version 5 of Fences is available in the Object Desktop subscription package, which includes about a dozen other useful apps that modify the Windows interface, but a perpetual license for Fences is also offered for $30. Otherwise, you can license it for $10 per year on one computer, $20 per year for up to five computers, or the full Object Desktop suite for $40 per year. And there’s a 30-day free trial period so you can give any application or the full suite a test drive.
For more information, visit the Stardock Fences 5 website.