Listen to the Podcast
28 July 2023 - Podcast #842 - (20:12)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
It’s probably true that most scams are simply variants of a few basic frauds, but the scammers are proficient at putting new clothes on old scams. It seems to me that a bit of skepticism would allow most people to identify old frauds in new outfits. Let’s look ....
Fraudsters want your money. Regardless of the scam, that’s the objective, and you’ll find these creeps in your email inbox, hanging around automatic teller machines, on the phone, lurking under rocks on social media, maybe even in your US Postal Service mailbox, and in other locations that may be surprising.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Let’s say you find a parking ticket on your car. The ticket has a QR code that you can use to pay it, but no printed web address or option to pay by mail. Careful! QR codes are handy, but they can be used to disguise a fraudster’s website. Here’s what could happen: You scan the QR code and a website that seems legitimate appears on the screen. You enter credit card information to pay the ticket—after all, it’s just a few dollars—and you get a receipt that looks legitimate. But you didn’t just pay a parking fine. Instead, you gave the criminals your name, phone number, credit card number, billing address, and security code. Instead of stealing a small amount, they charge several large purchases to your credit card.
Let’s say you find a parking ticket on your car. The ticket has a QR code that you can use to pay it, but no printed web address or option to pay by mail. Careful! QR codes are handy, but they can be used to disguise a fraudster’s website. Here’s what could happen: You scan the QR code and a website that seems legitimate appears on the screen. You enter credit card information to pay the ticket—after all, it’s just a few dollars—and you get a receipt that looks legitimate. But you didn’t just pay a parking fine. Instead, you gave the criminals your name, phone number, credit card number, billing address, and security code. Instead of stealing a small amount, they charge several large purchases to your credit card.
Granted, the bank will probably reverse the charges for purchases made with your card, but somebody will lose money. If not the bank, then the merchant who won’t be able to collect the payment and will no longer have whatever the fraudster purchased. These thefts become part of the store’s cost of doing business and increases prices for everyone.
 I’ve laughed at a never-ending stream of feedback and survey scams that claim to be from every imaginable business.
I’ve laughed at a never-ending stream of feedback and survey scams that claim to be from every imaginable business.
<<< Three phony surveys that arrived within minutes of each other.
Usually you’ll be offered a fabulous prize worth hundreds of dollars for completing a short survey. Nobody should ever fall for one of these; if it seems too good to be true, it probably is.
 When you collect mail from your mailbox, you might find a package from a merchant you’ve never heard of. The US Postal Service says this may be a brushing attempt. These packages sometimes come from foreign addresses. The scammer will have obtained your name and mailing address from someone on the dark web. The merchant can then claim that you bought something from them, create a fake review that’s favorable in your name as a “verified” buyer.
When you collect mail from your mailbox, you might find a package from a merchant you’ve never heard of. The US Postal Service says this may be a brushing attempt. These packages sometimes come from foreign addresses. The scammer will have obtained your name and mailing address from someone on the dark web. The merchant can then claim that you bought something from them, create a fake review that’s favorable in your name as a “verified” buyer.
Although it seems that there’s no victim here, the real victims are those who read the favorable online reviews and buy shoddy merchandise from the scammers. The scammers may even try to get you to pay for the unwanted junk. Don’t fall for it! If you’ve received something you didn’t order and it’s not a mis-delivered package, it’s a gift. Keep it if you want, or throw it away.
And because I just mentioned online reviews, give them very little credence. An astonishingly large percentage of reviews are fake. It’s OK to glance at them, but watch for reviews that contain repetitive comments—almost as if they were written by the same person. Artificial intelligence is making this problem even worse because AI can create reviews that differ enough to seem like they’ve been written by real people.
If you want to know somebody’s opinion about a product or a service, ask people you know. Ask people you’re familiar with on social media. Be wary of reviews.
 Let’s get back out on the street. You need some cash, so you stop at an ATM and insert your debit card. The machine can’t read your card or the slot is jammed, but a helpful person who’s passing by tells you that machine hasn’t worked right for days, but you can use the “tap” function. So you tap the card, input your PIN, collect the money, and walk away. What a helpful person! But the person is trying to help themselves to your cash.
Let’s get back out on the street. You need some cash, so you stop at an ATM and insert your debit card. The machine can’t read your card or the slot is jammed, but a helpful person who’s passing by tells you that machine hasn’t worked right for days, but you can use the “tap” function. So you tap the card, input your PIN, collect the money, and walk away. What a helpful person! But the person is trying to help themselves to your cash.
Here’s the trick: If you take the money and walk away, you’re still logged in. When you insert a card, the machine ejects it when you’re done. Because you didn’t insert the card, you have to explicitly log out or wait until the machine logs you out after a minute or two. The “helpful” person reappears after you’ve gone but you’re still logged in and makes several more withdrawals up to the daily limit. Many banks will not refund money in cases like this.
 There are lots of scams that claim a service such as UPS, FedEx, DHL, or the US Post Office was unable to deliver your package. Most of these can be easily identified as scams. Two showed up in my spam catcher on the 9th of July, but I cleared them for delivery to my email program. The fraudsters didn’t even bother to spoof a FedEx or UPS address, the ID numbers displayed weren’t in the proper format, and the messages clearly were written by people who do not speak English as their first language.
There are lots of scams that claim a service such as UPS, FedEx, DHL, or the US Post Office was unable to deliver your package. Most of these can be easily identified as scams. Two showed up in my spam catcher on the 9th of July, but I cleared them for delivery to my email program. The fraudsters didn’t even bother to spoof a FedEx or UPS address, the ID numbers displayed weren’t in the proper format, and the messages clearly were written by people who do not speak English as their first language.
Social media is a scam magnet, too. Perhaps you make a comment on Facebook and someone compliments your logic and asks you to send a friend request. This is a long con. Your new “friend” is really an AI bot who will build up a relationship with you and then suddenly need money for an emergency.
A variant of that scam involves someone who hacks a friend’s or relative’s Facebook account or creates a clone account and convinces you to accept what is a redundant friend request. Later the friend or relative is “mugged” in a foreign country and needs money to tide them over until they can get new credit cards. Or they’ve been “arrested” and need money for bail. This is particularly effective when the fraudster pretends to be a grandchild and needs your help so their parents don’t find out.
These are both variants of phishing. Spotting basic phishing emails isn’t particularly difficult but AI makes them harder to identify. No matter how realistic a message appears, it’s always wise to take a few seconds to examine it.
If you think you’re dealing with a bot, ask it to do something a person could do easily. Example: If you are a real person type kitten. Your response will trigger the bot to respond, but probably not with the word kitten. This test probably will not be effective for long because AI can be taught to watch for challenges and respond appropriately. If you receive a message that might or might not be from a friend or relative, ask to be told something a scammer won’t know and a chatbot can’t figure out.. This eliminates things such as the mother’s maiden name or the name of a pet. But you could ask what city “Cousin Merle” lives in—where Merle can be any name that isn’t used in your family. If the person makes any guess at all, you’ll know they're a phony. Ask enough questions to confirm conclusively whether or not you know the person.
For email and text messages:
No matter what kinds of automated procedures you have in place, the most important protections are caution and common sense. Don’t allow scammers to fool you.
Today’s operating systems have graphical user interfaces that are intended to be easier to use than the old command line that was the only thing available until the mid-1980s. But the command line is sometimes faster and easier, even today, and may offer functions not available via the GUI.
Let’s look at a few random and totally unrelated command line tricks for Windows.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
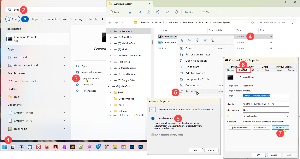 Because some of these tricks work better when the command line has Administrator privileges, let’s set CMD so that it always opens as Administrator. Press (1) the Win key, (2) type CMD, and choose (3) Open File Location. Right-click (4) Command Prompt (shortcut) and click (5) Properties. Make sure the (6) Shortcut tab is selected, click (7) Advanced, and select (8) Run as administrator. Then click OK until the dialogs close. CMD will now always run as Administrator.
Because some of these tricks work better when the command line has Administrator privileges, let’s set CMD so that it always opens as Administrator. Press (1) the Win key, (2) type CMD, and choose (3) Open File Location. Right-click (4) Command Prompt (shortcut) and click (5) Properties. Make sure the (6) Shortcut tab is selected, click (7) Advanced, and select (8) Run as administrator. Then click OK until the dialogs close. CMD will now always run as Administrator.
With that out of the way, let’s begin.
 Two useful commands provide power and battery information about the computer. The first, powercfg /energy, produces a report that displays information, warnings, and errors regarding applications and power management settings. The second, powercfg /batteryreport, summarizes battery usage and battery health. As such, this second command is useful only for computers with batteries.
Two useful commands provide power and battery information about the computer. The first, powercfg /energy, produces a report that displays information, warnings, and errors regarding applications and power management settings. The second, powercfg /batteryreport, summarizes battery usage and battery health. As such, this second command is useful only for computers with batteries.
The energy report creates a file called energy-report.html in C:\Windows\System32\. It’s important to note that not all entries in the Errors section really are errors. My primary computer is a notebook, but it runs on AC power at all times and I never want it to hibernate and the power settings I’ve selected give preference to performance. Several messages report settings that are intentional. Examples:
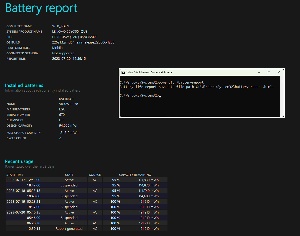 The same is true of most of the listings in the Warnings section. Several processes with CPU utilization in excess of what Microsoft expects generate warnings that can be ignored. If the computer has operational problems, the Warnings and Errors sections may help you find the cause.
The same is true of most of the listings in the Warnings section. Several processes with CPU utilization in excess of what Microsoft expects generate warnings that can be ignored. If the computer has operational problems, the Warnings and Errors sections may help you find the cause.
The Information section reports details such as the Power Policy in use, the power plan’s settings, details about processor power management, and some information about the battery.
The battery report creates a file called battery-report.html in C:\Windows\System32\.
This report is quite useful because it reports recent battery usage for the past three days, charts battery usage for the past three days, displays AC usage and battery usage and capacity, and shows battery life estimates. This information is useful if you thing the battery my need to be replaced soon.
 Maybe you’d like to hide a folder. You probably know that typing %appdata% in the address line of the Windows File Explorer will take you to C:\Users\YourUserName\AppData\Roaming, but if you navigate to C:\Users\YourUserName\, you won’t see the AppData directory. That’s because the Hidden attribute (H) is set. The Do Not Index (I) attribute is also set so the indexing service won’t examine the directory. Other attributes that can be set are Read-only (R), Archive (A), and System (S).
Maybe you’d like to hide a folder. You probably know that typing %appdata% in the address line of the Windows File Explorer will take you to C:\Users\YourUserName\AppData\Roaming, but if you navigate to C:\Users\YourUserName\, you won’t see the AppData directory. That’s because the Hidden attribute (H) is set. The Do Not Index (I) attribute is also set so the indexing service won’t examine the directory. Other attributes that can be set are Read-only (R), Archive (A), and System (S).
 The command attrib C:\Users\willi\AppData displays the attributes that are set and can be used to set or remove attributes on files and folders.
The command attrib C:\Users\willi\AppData displays the attributes that are set and can be used to set or remove attributes on files and folders.
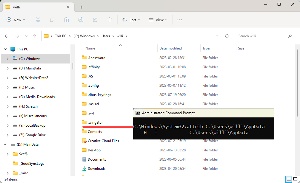
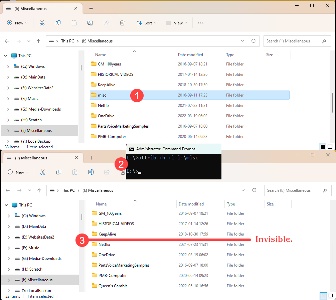
So if you want to hide a folder to keep people from seeing it, you can use the H and I attributes. Example: attrib +h +i i:\misc, where misc is the name of the directory to hide. Before applying the attributes, the folder is (1) visible in the File Explorer. The (2) command produces no confirmation, but the directory (3) disappears from the list of files.
Note, though, that this will hide the directory only from people who don’t know how to display hidden files and folders. In other words, it’s not a good choice if you’re hiding the details of your most recent crime spree. Any forensic computer specialist will spot your hidden trove in less than a minute. Essentially it’s a toy lock on a cardboard door.
You may occasionally need to email someone a copy of a printed document, but you’re not near a scanner. Or are you? Chances are, there’s one in your pocket.
You’re ahead of me, I’m sure. It’s the smartphone I’m thinking of. It has a camera, so you can just use the photo app and then send the resulting image. But there’s a better way. Microsoft Lens is one of several applications that are much better than the camera app.
It’s challenging to get a straight photo of a paper document, but Lens has a function that recognizes pages and straightens them automatically. That’s just the beginning.
Lens captures text, tabular data, contact information from a business card, and QR codes. It can also perform optical character recognition on the text and then read it to you. This works in English and 29 other languages. There are also settings for documents, whiteboards, business cards, and photos.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Besides doing a better job on printed materials than the camera app will do, Lens is easy to use. Start by (1) capturing an image of the page, getting it reasonably straight. Lens will then (2) show you where it thinks the edges of the page are and, if you don’t agree, you can drag the corner markers around on screen. By default, Lens will save the captured image to Microsoft OneDrive, but you can choose other locations.
Besides doing a better job on printed materials than the camera app will do, Lens is easy to use. Start by (1) capturing an image of the page, getting it reasonably straight. Lens will then (2) show you where it thinks the edges of the page are and, if you don’t agree, you can drag the corner markers around on screen. By default, Lens will save the captured image to Microsoft OneDrive, but you can choose other locations.
The portable scanner in your pocket can create a permanent record of a receipt, make a copy of a medical form for submission to an insurance company, or grab the contents of a white board from a meeting. Lens is available for Android and IOS phones. It does a lot more than just (3) capture a picture of a business card, document, or whiteboard. Besides recognizing text, the OCR function works even with handwritten text if it’s clearly written.
When capturing a business card, the OCR function can recognize first and last names, phone numbers, email addresses, and other common bits of data, then save the information to your phone’s Contacts app. See more about Lens for Android or Lens for IOS on Microsoft’s website. The app can be downloaded from the Apple Store or the Google Play Store.
SCO, the company that owned Unix, became known for its greed and earned the title “the most hated company in tech”. In 2003, SCO was suing everyone it could find. By 2012, it was dead.
This is an interesting tangle. SCO, the biggest name in Unix, is suing IBM because SCO says IBM owes SCO money for using Linux. Linux is the free, open-source version of Unix.
SCO says that IBM stole some code from Unix and incorporated it into Linux. IBM says that SCO can’t claim damages because it previously shipped its own version of Linux. Earlier this week SCO said Linux users must pay the company for a Unix license or face possible legal action, claiming that Unix code was illegally copied into Linux and that companies such as IBM illegally transferred improvements made to Unix into Linux.
SCO had already filed a $3 billion lawsuit against IBM. IBM’s vice president of systems sales, Bob Samson, told sales reps in a letter that SCO distributed Linux under the GNU General Public License (GPL), which grants a free copyright license and requires that users be granted the right to freely redistribute the code free of claims."
SCO’s position is that it is the Unix copyright holder and it never placed the copyrighted code in Unix under the GPL for Linux. This will be an amusing case to watch as it wobbles through the legal system.