Listen to the Podcast
16 June 2023 - Podcast #836 - (17:30)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
After writing about Google’s limited free VPN in May, I thought now might be a good time to review the advantages of a full-featured VPN. A virtual private network doesn’t ensure safety, but it helps.
It’s important to understand the trade-offs, though. Some websites may not work when a VPN is active, network performance will be at least slightly slower, and good VPN services aren’t free.
Until she retired, my wife worked from home using a computer provided by her employer. The computer connected via a VPN to the company’s servers. Without the VPN, the connection would be refused. I work from home and do not need to connect to enterprise servers. Any important websites I connect to use secure HTTP and I enable secure FTP and secure shell when I need to connect to the TechByter Worldwide server. But I still have a VPN for the computers.
Not, however, for our phones. Our cellular service is provided by Google Fi and includes a built-in, always-on VPN. It can be turned off, but I leave it on because it interferes with nothing. The home computers use Nord VPN and I had previously used that on the phone, but it interfered with a banking application.
Your computer and devices inside the network have private IP addresses, but the address on the internet side of the router is visible to any site you connect to. The address reveals your general location. In addition to encrypting all data, a VPN hides your IP address and makes it appear that you’re in another location.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 When Nord VPN connects, I generally allow it to select the location and that location is generally Chicago. I could pick another location such as New York, Buffalo, Toronto, Montreal, Dallas, Los Angeles, Seattle, Vancouver or even an address in Mexico, Columbia, Brazil, South Africa, Spain, Ireland, England, Ukraine, or Finland. Not Russia or China, though, but South Korea, Australia, and New Zealand are possibilities.
When Nord VPN connects, I generally allow it to select the location and that location is generally Chicago. I could pick another location such as New York, Buffalo, Toronto, Montreal, Dallas, Los Angeles, Seattle, Vancouver or even an address in Mexico, Columbia, Brazil, South Africa, Spain, Ireland, England, Ukraine, or Finland. Not Russia or China, though, but South Korea, Australia, and New Zealand are possibilities.
If you think that you might be able to stream BBC programs live by connecting to London, forget it. You also need to obtain a government television license and that requires having a physical address in Great Britain. In some cases, you may be able to access streaming media from one country even if it’s not allowed in your area, but some streaming services won’t function if they detect the presence of a VPN.
There are other advantages, though. Your internet service provider can see what you do on the internet and some ISPs collect information about users and sell it. Using a VPN eliminates the ability for services to do that.
As I described in last week’s program about browser fingerprinting, while a VPN doesn’t eliminate the ability for websites to collect enough information about your browser and your computer to identify your computer, it does improve your chances.
Whether you use a VPN at home may be optional, but any computer that’s used with a public Wi-Fi hotspot should absolutely have a VPN. Encryption protects data that could be viewed if you use public Wi-Fi access points in restaurants, coffee shops, and airports. If you travel frequently (or even infrequently) and use public access points, use a VPN. That doesn’t apply to a Wi-Fi system in your home or office.
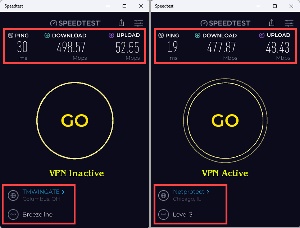 But what about downsides? Yes, some do exist. The most common is degraded downlink and uplink speeds, but this has not been a problem recently. We pay Breezeline (formerly Wide Open West) for a 500Mbps downlink and a 50Mbps uplink. In early June, SpeedTest showed 499Mbps downlink with the VPN off and 478Mbps with the VPN on. That’s less than a 4% difference. Results were similar for the uplink, 53Mbps with the VPN off and 48Mbps with the VPN on.
But what about downsides? Yes, some do exist. The most common is degraded downlink and uplink speeds, but this has not been a problem recently. We pay Breezeline (formerly Wide Open West) for a 500Mbps downlink and a 50Mbps uplink. In early June, SpeedTest showed 499Mbps downlink with the VPN off and 478Mbps with the VPN on. That’s less than a 4% difference. Results were similar for the uplink, 53Mbps with the VPN off and 48Mbps with the VPN on.
Oddly, the ping speeds were better with the VPN on, 19ms versus 30ms. Ping measures the amount of time required for one system to respond to another. Ideally, these times should always be single digits, but the two values I received are common for consumer-grade internet service.
Although the VPN doesn’t make it impossible to connect to one of my bank’s servers, it means that the bank’s computer is less certain that I am who I claim to be and it generates an out-of-band challenge that adds a few seconds to the login time.
Overall, it’s better to have a VPN than to forego it because of perceived downsides. Having a VPN can lead to a false sense of complacency, though. The VPN offers protections against being tracked or identified, but is largely ineffective against browser fingerprinting and completely powerless against phishing and social engineering. (More about that in Short Circuits.)
Free VPNs exist, but it’s better to pay a few dollars per month for a commercial service. The free VPN from Google is effective, but quite limited. Three recent VPN reviews are online and can help you choose the VPN that’s right for you. The articles are from Tom’s Guide, PC Magazine, and Wired.
The VPN I selected several years ago and recently renewed for two years is from Nord. Tom’s Guide ranks Nord second behind ExpressVPN, PC Magazine places Nord second behind Proton, and Wired says Nord is best for circumventing geographic restrictions but Surfshark is best for most people.
Check out the reviews and think about which features are most important for you.
It’s no longer the case, if it ever was true, that internet thieves are stupid. Some are, of course, and I like to laugh at the outrageously idiotic attempts, but even these fool some people despite an abundance of clues. Even careful, intelligent people can be fooled by social engineering scams.
Social engineering attempts to exploit human psychology instead of finding a way to break in to a building or a computer system. It’s easier to fool someone into handing over sensitive data than it is to find and exploit programming errors. Criminals can masquerade as someone from a company’s IT department, a bank, or a government agency such as Social Security or the IRS. We don’t need to have a degree in computer programming to thwart them, just the intelligence to spot a scam.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
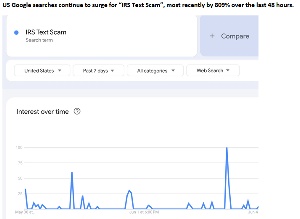 A report from Ideal Tax shows Google search instances in early June for the phrase “IRS Text Scam” and the chart shows a giant spike around 3 June and several smaller spikes around the end of May and on 1 June. This may be the result of a blast of email scam messages purporting to be from the IRS.
A report from Ideal Tax shows Google search instances in early June for the phrase “IRS Text Scam” and the chart shows a giant spike around 3 June and several smaller spikes around the end of May and on 1 June. This may be the result of a blast of email scam messages purporting to be from the IRS.
Scam emails and phone calls claiming to be from the IRS may threaten your arrest unless you immediately pay a tax penalty, often using gift cards to transfer the funds. Two huge red flags are present in that sentence: First the IRS never threatens an arrest by email. Never. Even if you’re already dealing with the IRS, they won’t make an arrest threat by email or phone. The key word here is “never”; that’s a 100% indicator that the message is a scam. And second, no government agency, business, or bank will ever demand payment via gift cards.
If the IRS has a question about your tax return, they will start by sending a letter. The IRS will call or come to a home or business only if there is an overdue tax bill, an unfiled tax return, or (for businesses) failure to make an employment tax deposit. But before anyone shows up on your doorstep, you’ll hear from the IRS first by mail—a letter in an envelope.
Even if an email appears to be legitimate, examine it carefully. Don’t believe the From field on an email because this can be spoofed. Ignore any links or telephone numbers in the email. Instead, visit the IRS government website or call the IRS 800-829-1040, 7 am to 7 pm local time.
The same is true if you receive an email or a phone call from Social Security, any other state or federal agency, a bank, or a business. Don’t trust links and phone numbers in emails. Go to the agency, bank, or business website and follow the instructions to contact someone. It’s much easier and less stressful to avoid a scam than it is to recover from one.
Most of the major software developers have transitioned from waterfall methods to agile. The older method depended on fully designing every aspect of an application, writing the code, and then releasing it. The danger of using what's called “waterfall” methods is creating an application that's not suitable. Agile methodology starts with a roadmap and then releases bits of code as they're available. Adobe has mastered the process.
On 19 April, I wrote about Adobe's Denoise feature in Lightroom and Camera Raw. I had planned to discuss some of the other additions to Creative Cloud, but Firefly and generative fill demanded my attention. Today, it's finally time to look at some of the other applications and their new features.
After Effects has several new capabilities. Animations have more controls that can be applied to text and shape layers in a new dialog. The interface has also been streamlined for enabling and disabling effects.
Premiere Pro can now export directly to social media, which makes the process faster. Producing an initial rough cut can be accomplished faster with text-based editing. The user can search source transcripts to identify content to be added to the Timeline.
Illustrator users will find that hyperlinks are retained when exporting a PDF file. The trace function has also been improved and an enhanced search function makes it easier to find layers and objects. A beta feature attempts to identify typefaces in raster components.
Artificial intelligence has been added to InDesign. An Auto Style feature examines text and attempts to add body text, headline, and subhead styles automatically. InDesign also now supports several additional graphics formats such as HEIC, HEIF, WEBP, and JP2K to eliminate the need for image conversion before being added to a document.
And, to come back to the photography applications, which always seem to garner the largest number of new features.:
In 2003, Nikon had loaned me a digital SLR camera. I had been using digital cameras since about 1999, but they were more like point-and-shoot cameras than the single-lens-reflex cameras I had used since the 1960s. I liked the D100 and wrote about it:
Nikon has loaned me a D100, the first true digital SLR from Nikon for under $2000 and I'm really angry. This camera fits my hand, works the way I work, does everything I could hope a digital camera might do (and then some). This makes me exquisitely angry. Why? Because I have to return it to Nikon. I will miss it.
There won't be time on this week's program to talk much about this camera, but it's been a delight to use. I first got to hold a D100 briefly when I visited B&H Photo and Video just before Christmas last year. Yossi Fogel asked if I'd seen the camera yet. When I said I'd seen it only in Nikon ads, he walked over to the sales counter, picked up a D100 and handed it to me. I didn't even have to look at the camera. The controls were all where they were supposed to be. I lifted the camera to my eye, composed an image, and pressed the shutter.
What happened next was amazing: The camera took a picture. Instantly. There was no "digital delay", something that most of us who use digital cameras have come to expect. This delay is no big deal if you're taking tourist snapshots of the Statue of Liberty or the Grand Canyon -- they don't move around much. But if you're trying to capture a fleeting expression, a sporting event, or a wedding, the delay can be the difference between an outstanding image and an unusable image.
I didn't return the camera to Nikon. Instead, I sent the company a check and I continued to use Nikon digital cameras until Nikon's service centers provided disappointing service. Currently I use Canon and Sony cameras, but most of my photographs are captured with a smartphone.