Listen to the Podcast
2 June 2023 - Podcast #834 - (24:12)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Tiny apps that solve highly specific problems have always been my favorites, so let’s look at offerings from three sources this week.
These small apps are generally known as “utilities”, but that name can apply to large applications such as text editor Notepad++, FTP client Filezilla, media player VLC, and ebook organizer Calibre. These are all large applications and some of them have multiple functions. Today I’m concentrating on a few of Nir Sofer’s dozens of NirSoft specialized apps, some of Nenad Hrg’s SoftwareOK utilities, and the latest additions to Microsoft’s PowerToys.
It may seem that Microsoft doesn’t belong here, but the PowerToys utilities are developed independently and are available for download from GitHub as well as from the Microsoft Store. Nirsoft and SoftwareOK apps are created by individual developers. Nir Sofer, for example, has more than 200 utilities and Nenad Hrg has published well over 100 utilities at SoftwareOK.
I can’t describe all of these utilities, or even name all of them. But it’s easy to visit the sites and pick the applications you want. For PowerToys, you’ll download the full package, install it, and the activate the components you want to use.
I’ve described this handy collection of utilities before (April 2022 and earlier), so check one of the earlier articles for information about 17 functions that have been around for a while. Today we’ll look at just the two most recent additions: Paste As Plain Text and Registry Preview.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
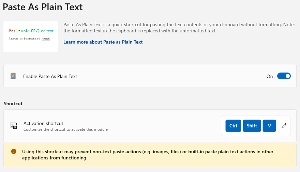 Many applications that accept pasting text from the Clipboard include a mechanism for stripping out images, formatting, and other non-text components. The trouble is that the keystrokes used to accomplish this vary between programs. The PowerToys Paste as Plain Text function overrides them all with the Windows key plus Ctrl-Alt-V. Fortunately that key sequence can be changed because four-key chords are difficult to type. Ctrl-Win-Alt-V is nearly impossible for me to type. I have to stop, look at the keys, and concentrate to do it with just my left hand. It’s a bit faster if I press Cltr-Win-Alt with the left hand and then V with the right. I tried changing the key sequence to Shift-Ctrl-V and PowerToys warned that this could interfere with key sequences used by other applications. It hasn’t created any problems so far and having just a single sequence to remember is a plus.
Many applications that accept pasting text from the Clipboard include a mechanism for stripping out images, formatting, and other non-text components. The trouble is that the keystrokes used to accomplish this vary between programs. The PowerToys Paste as Plain Text function overrides them all with the Windows key plus Ctrl-Alt-V. Fortunately that key sequence can be changed because four-key chords are difficult to type. Ctrl-Win-Alt-V is nearly impossible for me to type. I have to stop, look at the keys, and concentrate to do it with just my left hand. It’s a bit faster if I press Cltr-Win-Alt with the left hand and then V with the right. I tried changing the key sequence to Shift-Ctrl-V and PowerToys warned that this could interfere with key sequences used by other applications. It hasn’t created any problems so far and having just a single sequence to remember is a plus.
 The name of the PowerToys Registry Preview is a bit misleading. It’s not intended to examine the entire Registry; in fact, it can’t even if you export the full Registry to a file. The Registry will be huge. Exporting the Registry on my primary computer creates a file that’s nearly 500MB and the Registry Preview utility is limited to loading files no larger than 10MB. It’s intended to allow users to examine a key, edit a key. or create a key to be added to the Registry. So you need a file that contains a Registry key. I started with the Mozilla key in Computer\HKEY_CURRENT_USER\Software.
The name of the PowerToys Registry Preview is a bit misleading. It’s not intended to examine the entire Registry; in fact, it can’t even if you export the full Registry to a file. The Registry will be huge. Exporting the Registry on my primary computer creates a file that’s nearly 500MB and the Registry Preview utility is limited to loading files no larger than 10MB. It’s intended to allow users to examine a key, edit a key. or create a key to be added to the Registry. So you need a file that contains a Registry key. I started with the Mozilla key in Computer\HKEY_CURRENT_USER\Software.
Many people will find the Registry Preview layout easier to understand. Making changes to the file being examined requires using a text editor. The Edit function from the utility will open Notepad, but the file can be opened in any other text editor. After making changes, the file must be imported into the Registry. Unless you’re fully familiar with the Registry, a good motto here would be Look, but don’t touch!
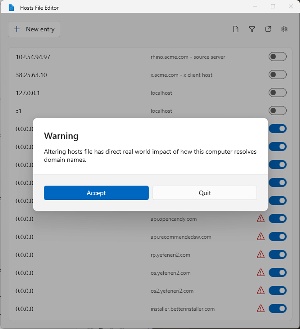 Another recent addition to PowerToys is the Hosts File Editor. Windows includes a local Hosts file in the C:\Windows\System32\drivers\etc\ directory. Hosts contains domain names and their matching IP addresses to identify hosts on IP networks. Network applications check the Hosts file before sending a query to the domain name server (DNS). The Hosts file is often used to eliminate access to advertising sites and known bad actors by assigning the domain name either to local host (127.0.0.1) or to an unspecified, unrouteable address (0.0.0.0). 0.0.0.0 is the better choice.
Another recent addition to PowerToys is the Hosts File Editor. Windows includes a local Hosts file in the C:\Windows\System32\drivers\etc\ directory. Hosts contains domain names and their matching IP addresses to identify hosts on IP networks. Network applications check the Hosts file before sending a query to the domain name server (DNS). The Hosts file is often used to eliminate access to advertising sites and known bad actors by assigning the domain name either to local host (127.0.0.1) or to an unspecified, unrouteable address (0.0.0.0). 0.0.0.0 is the better choice.
If there’s a domain you want to avoid, create a new entry, specify 0.0.0.0 as the address, type the domain name to avoid (media.opencandy.com, for example), and add a note if you wish. "OpenCandy is an adware module and a potentially unwanted program classified as malware by many anti-virus vendors. It is designed to run during installation of other desired software. OpenCandy’s various undesirable side-effects include changing the user’s homepage, desktop background or search provider, and inserting unwanted toolbars, plug-ins and extension add-ons in the browser. It also collects and transmits various information about the user and their Web usage without notification or consent." -Source: Wikipedia
Since 2001, Nir Sofer has been creating useful utilities for Windows. These range from password and system tools to utilities for browsers and networks. There are utilities designed for programmers and for regular users. Overall, there are more than 200 utilities, all provided without cost and he even refuses to request donations.
Some of the utilities trigger false positives from poorly written antivirus applications and a few are blocked by Windows. ProductKey, for example, once could be used to obtain the Windows installation key. If downloaded, it will now be deleted by Windows Security. That’s not a significant problem for Windows users because the key will be displayed when the user opens a Command window and types wmic path softwarelicensingservice get OA3xOriginalProductKey.
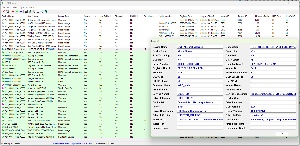 USB Device View displays information about USB devices that are or were connected to your computer. My computer has 28 active USB devices (shown in green) and nine that have been connected, but currently are not. Double-click one of the devices for more information. It’s also possible to specify commands that should be run when a USB device is attached or detached and to have the application create a log showing when devices are connected or disconnected.
USB Device View displays information about USB devices that are or were connected to your computer. My computer has 28 active USB devices (shown in green) and nine that have been connected, but currently are not. Double-click one of the devices for more information. It’s also possible to specify commands that should be run when a USB device is attached or detached and to have the application create a log showing when devices are connected or disconnected.
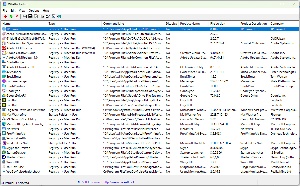 Although there are other applications that show which programs are started with Windows (including one that’s built in to Windows), NirSoft’s WhatInStartup shows the startup type, command-line string, product name, file version, company name, startup location in the Registry or file system, and more. The startup type is helpful because there are several ways to start an application when Windows starts. Applications can be started by the Registry as machine run, machine run once, user run, or user run once. There can also be references in the startup folder for the user or for all users. If an application starts and you don’t want it to, figuring out where to look for the launch command can be time consuming. To disable an unwanted application, choose Disable or Delete. Before deleting a startup application, disable it, restart Windows, and run the machine for a while. If disabling the application creates no problems, you can leave it disabled or go back and delete it. The safer method is just to leave it disabled so that you can enable it again if you change your mind.
Although there are other applications that show which programs are started with Windows (including one that’s built in to Windows), NirSoft’s WhatInStartup shows the startup type, command-line string, product name, file version, company name, startup location in the Registry or file system, and more. The startup type is helpful because there are several ways to start an application when Windows starts. Applications can be started by the Registry as machine run, machine run once, user run, or user run once. There can also be references in the startup folder for the user or for all users. If an application starts and you don’t want it to, figuring out where to look for the launch command can be time consuming. To disable an unwanted application, choose Disable or Delete. Before deleting a startup application, disable it, restart Windows, and run the machine for a while. If disabling the application creates no problems, you can leave it disabled or go back and delete it. The safer method is just to leave it disabled so that you can enable it again if you change your mind.
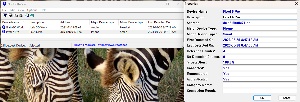 The Bluetooth Viewer utility watches for nearby Bluetooth devices. For each detected Bluetooth device, it displays the device name, Bluetooth address, device type, first detection time, last detection time, and other parameters. When run in the background, it can notify you when a new Bluetooth device is detected by displaying a balloon in the Taskbar or by sounding a beep.
The Bluetooth Viewer utility watches for nearby Bluetooth devices. For each detected Bluetooth device, it displays the device name, Bluetooth address, device type, first detection time, last detection time, and other parameters. When run in the background, it can notify you when a new Bluetooth device is detected by displaying a balloon in the Taskbar or by sounding a beep.
The utility allows you to connect to a Bluetooth device for testing. It doesn’t send any information to the device, but confirms operation by connecting. Once the connection has been made, the Bluetooth device will ask if you want to accept data and this confirms that the connection is operational.
Those are just a few of the NirSoft utilities that reveal information about the computer or perform useful tasks. Visit the NirSoft website and scroll through the list to see the others.
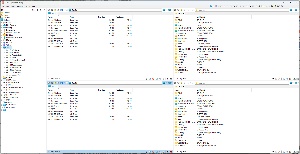 Nenad Hrg is the author of Q-Dir, which I’ve written about several times. I gave Q-Dir a try around 2006 and it immediately became my favorite file explorer and I’ve installed it on every computer I’ve owned since then. Moving files from one directory to another or comparing directories is clumsy with Windows Explorer because it shows only a single directory at a time. Microsoft has partially addressed this by adding tabs, but Q-Dir lets me explore up to four directories simultaneously and defining Favorites provides quick access to frequently used locations.
Nenad Hrg is the author of Q-Dir, which I’ve written about several times. I gave Q-Dir a try around 2006 and it immediately became my favorite file explorer and I’ve installed it on every computer I’ve owned since then. Moving files from one directory to another or comparing directories is clumsy with Windows Explorer because it shows only a single directory at a time. Microsoft has partially addressed this by adding tabs, but Q-Dir lets me explore up to four directories simultaneously and defining Favorites provides quick access to frequently used locations.
 Icons can move around when the user changes the screen’s resolution, but they can also move around sometimes just because Windows is Windows. DesktopOK eliminates that problem by recording the location of icons on the Desktop and putting them back in place each time Windows starts.
Icons can move around when the user changes the screen’s resolution, but they can also move around sometimes just because Windows is Windows. DesktopOK eliminates that problem by recording the location of icons on the Desktop and putting them back in place each time Windows starts.
 AeroClock places an analog clock on the Desktop and can be set so that it’s always visible (or “always on top”). Because my system has three screens, I place a large version of the clock on the laptop screen. It can be made any size and the clock’s color and transparency are adjustable. This is perfect for those of us who still prefer analog clocks.
AeroClock places an analog clock on the Desktop and can be set so that it’s always visible (or “always on top”). Because my system has three screens, I place a large version of the clock on the laptop screen. It can be made any size and the clock’s color and transparency are adjustable. This is perfect for those of us who still prefer analog clocks.
 Several system test tools are included. QuickMemoryTestOK can identify faulty memory if you believe that a computer has a problem that appears to be memory related. Or, if there are no problems with installed memory, running the utility allows memory to be ruled out as a cause.
Several system test tools are included. QuickMemoryTestOK can identify faulty memory if you believe that a computer has a problem that appears to be memory related. Or, if there are no problems with installed memory, running the utility allows memory to be ruled out as a cause.
FontViewOK. Most font viewers and managers can show only a single window of typefaces, but FontViewOK can show two panels to make comparing one typeface with another easier. You can view either the installed system typefaces or view all of the typefaces that are on the computer, but not installed.
Visit the SoftwareOK website to see if there’s an application you’d like to use.
Adobe is moving so fast that it’s nearly impossible to keep up. Firefly was released in beta just a few weeks ago and the technology was released in a beta version of Photoshop before the end of May.
I had planned to talk about some of the many other advancements that have come to Adobe products this week, but I’ve postponed that because the addition of this specific Sensei technology is astonishingly great and terrifically worrisome.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 “Generative Fill” is what Adobe calls it. Starting with a blank image, I typed “Create a cat sitting on a chair beside a table with a lamp in and old fashioned room.” The first few images did a good job with the room and the lamp, but all of the cats had extraordinarily odd faces. One of the resulting images had no cat (unless perhaps the cat was hiding under the chair). I did say that this is beta software after all.
“Generative Fill” is what Adobe calls it. Starting with a blank image, I typed “Create a cat sitting on a chair beside a table with a lamp in and old fashioned room.” The first few images did a good job with the room and the lamp, but all of the cats had extraordinarily odd faces. One of the resulting images had no cat (unless perhaps the cat was hiding under the chair). I did say that this is beta software after all.
Each iteration gives the users three images to choose from. When I had nine images, the best choice seemed to be one from the first set.
To experiment with the new technology, you’ll need to be enrolled in one of Adobe’s Creative Cloud programs that includes Photoshop. Downloading the beta version of Photoshop installs it in addition to the release version.
At its most basic Generative Fill translates words into images or parts of images. Currently this means still images, but Adobe says the technology already applies to or will soon apply to creating “videos, documents, and digital experiences as well as rich images and art.” It’s also useful in creating “building blocks” such as brushes, vectors, and textures that artists and designers can use to create content.
Chat GPT is trained on gigantic language data sets. Similarly, Firefly technology is trained on hundreds of millions of images. This allows it to learn patterns that can be used to create images based on what it has learned.
Although the test in which I tried to create an image of a cat on a chair beside a table with a lamp in an old fashioned room didn’t result in usable art, the result was surprisingly good. The room was old fashioned. There was a chair and the room had one or more tables with lamps. Sometimes the geometry was off a bit and the cats’ heads were definitely odd. But most of what Firefly presented was right.
Adobe describes Generative Fill as being most useful for several specific tasks:
 One of my concerns is that AI will be used to create so-called “photographs” of events that never happened. What if I could make it appear that Joe Biden was a member of my younger daughter’s wedding party? So I started with a photo of the groomsmen, selected the space at the right of the groomsman on the right, and asked Photoshop to add Joe Biden there.
One of my concerns is that AI will be used to create so-called “photographs” of events that never happened. What if I could make it appear that Joe Biden was a member of my younger daughter’s wedding party? So I started with a photo of the groomsmen, selected the space at the right of the groomsman on the right, and asked Photoshop to add Joe Biden there.
 None of the six images included Joe Biden and several of them had significant problems. Many of the inserted characters had faces with odd expressions. Attempts two, four, and five were women and none were dressed in wedding attire. Attempts one, three, and six were all men and all were in wedding attire. One arm of the women in attempts two and four were rendered abnormally. The man in attempt two and the woman in attempt three had exceptionally odd expressions and the man in attempt six was holding hands with someone who wasn’t there.
None of the six images included Joe Biden and several of them had significant problems. Many of the inserted characters had faces with odd expressions. Attempts two, four, and five were women and none were dressed in wedding attire. Attempts one, three, and six were all men and all were in wedding attire. One arm of the women in attempts two and four were rendered abnormally. The man in attempt two and the woman in attempt three had exceptionally odd expressions and the man in attempt six was holding hands with someone who wasn’t there.
 I tried something that seemed like it would be easier by asking for a cat to be placed behind the groomsmen. That worked reasonably well. I specified an orange cat and the first few attempts had the cat’s back to the camera. When I told Firefly I wanted the cat to be turned the other way, the result was better, but I wasn’t able to get the cat to look up at the subjects of the photo. A few more iterations probably would have done it.
I tried something that seemed like it would be easier by asking for a cat to be placed behind the groomsmen. That worked reasonably well. I specified an orange cat and the first few attempts had the cat’s back to the camera. When I told Firefly I wanted the cat to be turned the other way, the result was better, but I wasn’t able to get the cat to look up at the subjects of the photo. A few more iterations probably would have done it.

 Next, I started with an image of a meadow and asked for meteor. The first few attempts had what appeared to be laser beams shooting out of the meteor toward the ground. Virtually all of the attempts were unusable, but eventually I got one that was more or less acceptable.
Next, I started with an image of a meadow and asked for meteor. The first few attempts had what appeared to be laser beams shooting out of the meteor toward the ground. Virtually all of the attempts were unusable, but eventually I got one that was more or less acceptable.
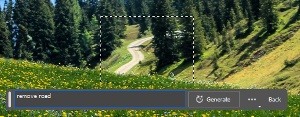 The image also had two sections of roadway and I asked Photoshop to remove the road. The results were perfect.
The image also had two sections of roadway and I asked Photoshop to remove the road. The results were perfect.
 So here’s the result with the phony meteor, which looks more like it’s taking off than crash landing and the two areas where the road has been removed.
So here’s the result with the phony meteor, which looks more like it’s taking off than crash landing and the two areas where the road has been removed.
I also wanted to try extending an image and found a good prospect among some photos from Inniswood Metro Gardens in Westerville. My premise was that I wanted a wider image, and I wanted to eliminate the dead leaves on the right.
 After extending the canvas to the left, I selected the blank area and, without giving Photoshop any instructions, had it perform a fill operation. The result extended the flowers in a convincing pattern.
After extending the canvas to the left, I selected the blank area and, without giving Photoshop any instructions, had it perform a fill operation. The result extended the flowers in a convincing pattern.
Next it was time to get rid of the dead brown leaves on the right. After selecting the area that includes the brown leaves, I told Photoshop to remove them. The resulting image is quite good. One of the other suggestions had more flowers in the repaired area, but the image I selected was more convincing. Additional iterations might have created an even better result, but the test had shown me how well the process works even though the technology is still new and is officially still in beta.
If you have questions about the ethics of making changes to photographs, you’re not alone. Those who want to use photos to lie will have more options and will be able to perpetuate lies more easily. Removing a road? If it's a photo you took while on vacation, I see no problem. After all, you will remember the vista, not the road. If you’re a real estate agent, removing a road is questionable ethically.
The technology is only going to become more powerful, and that’s going to happen quickly. Use the technology honestly and with care; and when looking at a photograph, consider the source and the source’s honesty
When somebody includes an attachment in an email, even somebody you know, it’s wise to check the file out before opening it. Even if your computer has an anti-malware application installed, getting a second or third opinion is a good idea. But how?
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 It’s an exceptionally bad idea to install more than one anti-malware application, but the Jotti Malware Scan shows files to 14 protective applications. You still have to decide what to do if 13 of the applications say the file is OK but one says it’s not. In most cases, a lopsided score like that means that one vendor is reporting a false positive.
It’s an exceptionally bad idea to install more than one anti-malware application, but the Jotti Malware Scan shows files to 14 protective applications. You still have to decide what to do if 13 of the applications say the file is OK but one says it’s not. In most cases, a lopsided score like that means that one vendor is reporting a false positive.
When you have a file that you’d like to check, just visit the Jotti website and upload the file. You’ll have the results in less than a minute. Then it’s up to you to make the right decision.
Another in the occasional series of scams perpetrated by idiots.
I really like the domain name: Jinx, hush, cry.

In 2003, Kodak was still trying to rebrand itself as the picture company, but was feeling intense pressure from the increasing acceptance of digital cameras that use no film. I wrote about an acquisition Kodak made:
Kodak is buying the assets of Applied Science Fiction, one of my favorite companies if for no other reason than its name.
ASF’s products include Digital PIC, Digital ICE, and Digital ICE3. These are technologies for film and flatbed scanners that automate restoration and correction of damaged images and Digital PIC rapidly develops standard color negative film without chemical mixing or plumbing. The process simultaneously renders digital image files that can be used to print photographs.
Kodak will integrate Applied Science Fiction’s technologies and personnel into its Consumer Imaging business. Specific details about product plans are "currently under development and will be disclosed at a later date." (I believe that translates to "Well, we just bought this stuff. Now what do we do with it?")