Listen to the Podcast
24 February 2023 - Podcast #820 - (19:24)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
A lot of people waste time on the internet. I'd say everybody instead of a lot of people, but there may be somebody who doesn't wander around the internet. All this wandering around makes me think back to when libraries had card catalogs.
Remember library card catalogs? Serendipity occurred there when the user found a card for a book near the card for the book they were looking for. I'm not sure if that's feasible with today's online catalogs, but wandering aimlessly on some sites can be relaxing, amusing, and educational. What's not to like about that?
 Wikipedia is probably the largest rabbit hole. Whether you're looking for one of the sieges of Thessalonica that occurred in 254, 617, 676, 1185, and 1422; the recording career of Muddy Waters; Lyndon Johnson's 1964 "Daisy" political ad; or the life story of a porn star (male or female), you'll probably find it in Wikipedia.
Wikipedia is probably the largest rabbit hole. Whether you're looking for one of the sieges of Thessalonica that occurred in 254, 617, 676, 1185, and 1422; the recording career of Muddy Waters; Lyndon Johnson's 1964 "Daisy" political ad; or the life story of a porn star (male or female), you'll probably find it in Wikipedia.
 Another treasure chest is How Stuff Works where you can learn the difference between sugar and white sugar, why the number 137 is special, how long squirrels live, and why multifactor authentication is important.
Another treasure chest is How Stuff Works where you can learn the difference between sugar and white sugar, why the number 137 is special, how long squirrels live, and why multifactor authentication is important.
How Products are Made (address: http://www.madehow.com) explains how products are made, but the site hasn't enabled secure HTTP so I haven't included a direct link here. Doing so would cause most browsers to report that this page is not secure. Just copy the link and paste it into the address line of your browser. You can learn how beer cans, beer, and barbed wire are made. Or read about how bedsheets, cough drops, and vinegar are created.
 Dictionary, Thesaurus, and Merriam-Webster are helpful when you need a definition or a word with a similar meaning, but just wandering around can be fun. Merriam-Webster updates a list of the top 10 words people are looking up every half minute. On the 23rd of January, endemic was the word of the day and the top 10 words people were looking for were abomination, faction, pusillanimous, woke, advocate, conjectures, metaphor, apathy, dragonfly, and abbreviation. There are also quizzes that check both fun and educational boxes. In "Which Came First" I learned (to my surprise) that chillax (1994) entered the language before dumpster fire (2006).
Dictionary, Thesaurus, and Merriam-Webster are helpful when you need a definition or a word with a similar meaning, but just wandering around can be fun. Merriam-Webster updates a list of the top 10 words people are looking up every half minute. On the 23rd of January, endemic was the word of the day and the top 10 words people were looking for were abomination, faction, pusillanimous, woke, advocate, conjectures, metaphor, apathy, dragonfly, and abbreviation. There are also quizzes that check both fun and educational boxes. In "Which Came First" I learned (to my surprise) that chillax (1994) entered the language before dumpster fire (2006).
 The Internet Movie Database is more useful only if you're a member, but basic memberships are free. You can find out who acted in a movie or television program, what other programs or motion pictures they've been in, and whether they've also worked as a writer, producer, or director. For television programs, you can find out whether it's available on a streaming service.
The Internet Movie Database is more useful only if you're a member, but basic memberships are free. You can find out who acted in a movie or television program, what other programs or motion pictures they've been in, and whether they've also worked as a writer, producer, or director. For television programs, you can find out whether it's available on a streaming service.
 If you're looking for news without a bias or a paywall, there are several options including Associated Press News, the BBC, National Public Radio, and Reuters.
If you're looking for news without a bias or a paywall, there are several options including Associated Press News, the BBC, National Public Radio, and Reuters.
Thinking with Type is another site that hasn't enabled secure HTTP, so the address for the site (http://thinkingwithtype.com) isn't a live link. You can learn about the anatomy of letters (cap height, x height, baseline, stem, ascenders and descenders, bowl, spine, ligature, serifs, and more). There are also articles on publication design, text, editors' markup symbols, and proofreaders' symbols.
 Make Use Of covers hardware, software, and tech news primarily, but there are also sections labeled "Free Stuff" and "Lifestyle". It's an excellent source of information on a wide variety of topics such as 8 Ways to Fix Slow Boot Times in Windows 10, 12 Video Sites That Are Better Than YouTube, and even 10 Free Mobile Ringtones That Sound Like Real Phones.
Make Use Of covers hardware, software, and tech news primarily, but there are also sections labeled "Free Stuff" and "Lifestyle". It's an excellent source of information on a wide variety of topics such as 8 Ways to Fix Slow Boot Times in Windows 10, 12 Video Sites That Are Better Than YouTube, and even 10 Free Mobile Ringtones That Sound Like Real Phones.
 You'll find A Sample Complaint Letter For When You Don’t Know What To Say, 17 Commercial Failures From Brands With Spectacularly Bad Ideas, and Please Don’t Press Any Buttons When You Get A Scammy Robocall on the Consumerist website, which is operated by Consumer Reports. There are categories for articles on retail services, education, crime and fraud, data and privacy, pharma, and more.
You'll find A Sample Complaint Letter For When You Don’t Know What To Say, 17 Commercial Failures From Brands With Spectacularly Bad Ideas, and Please Don’t Press Any Buttons When You Get A Scammy Robocall on the Consumerist website, which is operated by Consumer Reports. There are categories for articles on retail services, education, crime and fraud, data and privacy, pharma, and more.
 If you're looking for reading suggestions, take a look at Good Reads where you can share your opinion of books you've read, keep track of books you want to read, and download free or low-cost books that frequently are from new authors who are trying to build an audience.
If you're looking for reading suggestions, take a look at Good Reads where you can share your opinion of books you've read, keep track of books you want to read, and download free or low-cost books that frequently are from new authors who are trying to build an audience.
 ProPublica, bills itself as "investigative journalism in the public interest." The site has well investigated and carefully written articles such as Websites Selling Abortion Pills Are Sharing Sensitive Data With Google, How Congress Finally Cracked Down on a Massive Tax Scam, and What to Know About the Risks of Gas Stoves and Appliances.
ProPublica, bills itself as "investigative journalism in the public interest." The site has well investigated and carefully written articles such as Websites Selling Abortion Pills Are Sharing Sensitive Data With Google, How Congress Finally Cracked Down on a Massive Tax Scam, and What to Know About the Risks of Gas Stoves and Appliances.
 And finally, Google Maps might be the rabbit hole to end all rabbit holes. Want to take a look at Pyongyang, North Korea? There aren't any street view options, but there are some photos of transit stations, shopping malls, and parks. If you want street views, check out Bellefontaine, Ohio, along with New York City, London, Berlin, Tokyo, Canberra, Paris, Barcelona, Moscow, Rome, and even a few limited areas of Beijing. Combined with the free Google Earth application, Google Maps can easily consume an entire day as you travel virtually.
And finally, Google Maps might be the rabbit hole to end all rabbit holes. Want to take a look at Pyongyang, North Korea? There aren't any street view options, but there are some photos of transit stations, shopping malls, and parks. If you want street views, check out Bellefontaine, Ohio, along with New York City, London, Berlin, Tokyo, Canberra, Paris, Barcelona, Moscow, Rome, and even a few limited areas of Beijing. Combined with the free Google Earth application, Google Maps can easily consume an entire day as you travel virtually.
And to return to the library card catalog analogy, yes you can scroll through a library's holdings. Find books to read at local libraries and you may be able to borrow ebooks from more distant libraries. For example, I live in the Columbus area, where more than a dozen libraries are part of a consortium that shares physical media. I prefer ebooks most of the time, so I also have library cards from Cleveland, Cincinnati, and Dayton in addition to Columbus, Worthington, Upper Arlington, Grandview Heights, and the State Library of Ohio. I can't borrow physical books from the distant libraries, but they do offer access the electronic media. That's helpful because sometimes one library will have a book that the others don't.
If you're looking for a way to amuse yourself or you'd like to learn something new, there are hundreds of websites you can turn to.
You receive an email requesting a favor. It appears to be from someone you know, but it might be a scam. Let's take a look at one such message that was a scam and deconstruct it so we can determine how the scammer did it.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
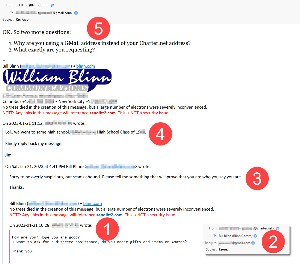 The message appeared to come from a high school classmate. Except for class reunions, our paths have crossed seldom since then. The subject of the message was Favor and the text said (1) "How are you? Hope you are good? I want to ask for a discrete assistance, do you order gifts and items on Amazon? Thank you."
The message appeared to come from a high school classmate. Except for class reunions, our paths have crossed seldom since then. The subject of the message was Favor and the text said (1) "How are you? Hope you are good? I want to ask for a discrete assistance, do you order gifts and items on Amazon? Thank you."
I'm sure that the writer wanted my discreet assistance, not my discrete assistance, but that kind of misspelling is common and doesn't account for much. Asking for my discrete assistance and then asking if I order gifts and items on Amazon (not from Amazon) raises a flag that might not be red, but it's definitely yellow.
Then I noticed the sender's address. The From address was the Charter.net address that I know is his, but (2) then I noticed the reply-to address: The user name was nearly the same, but had a numeral 1 at the end and, instead of being a Charter.net address, it was a GMail.com address.
I could think of no reason that the person the message claimed to be from would have to provide a different reply-to address. The yellow flag shifted a bit toward red.
So I replied: (3) "Sorry to be overly suspicious, but scams abound. Please tell me something that will prove that you are who you say you are."
A reply came quickly, but it was from the GMail address, not the Charter address. (4) "Lol.. we went to same high school. [Correct city name] High School Class of [correct year]." This might have been convincing except that the message had come from the wrong address.
I sent another reply: (5) "OK. So two more questions:
1 Why are you using a GMail address instead of your Charter.net address?
2 What exactly are you requesting?"
The response: Silence. Crickets. Nothing. Zero. Null. Dead air. Goose egg. Zip. Nil. Naught. Nada. Well, you get the idea. The message clearly had come from a scammer. But what was the game?
It's hard to say, but asking whether I order gifts and items from Amazon suggests some sort of commercial scam. Maybe the approach would be to tell me that he wants to order something for his wife, but it's a surprise and she'll see it if he orders using his own account. Could I order the item and have it shipped to him? He'll send me a check for the full amount and a little extra for my trouble. The check would never arrive, but he would have whatever I ordered for his "wife".
That could be the ploy, or maybe he'd double down on the scam. Perhaps I would receive a check and it would be for far more than the purchase price. Let's say he wanted a $2000 computer "for his wife" and would include an extra $100 "for my trouble", but the check is for $3100 instead of $2100. What then?
Well, of course, I could return the extra $1000 by purchasing a gift card and giving him the number. "Just go ahead and deposit the check," the scammer might say, "I want you to have your money as quickly as possible." So now the scammer has a $2000 computer that I paid for and $1000 that I've given him for the "overpayment". I have a check for $3100. Seems fair.
Won't I be surprised when the bank tells me, a week or two from now, that the account the check was drawn on has insufficient funds, or that the account doesn't even exist!
Again, I don't know that this is the way the scam would have played out, but it is one way the scam could have played out. So I didn't play the game.
The original message came from the Charter.net account (I checked the routing headers), which suggests that the crook had managed to place malware on my former classmate's computer or gained access to his online email account. That would give the scammer access to the classmate's email where he would find messages regarding class reunions.
Unfortunately, the person who sends class reunion messages places all addresses in the To line instead of using the BCC line. This provides a list of potential victims as well as information about the high school the recipients attended and what year they graduated.
Just like discerning what the scammer's intent was, figuring out the methodology is simply a guess, but the situation and actions described would work. This is why every message should be considered suspect until the sender proves its legitimacy.
I keep just a few icons on the Desktop and I'm annoyed when applications don't offer me an option to decline a Desktop icon and instead just place one there. It's even worse when an icon is placed repeatedly on the desktop even after I've deleted it. Case in point: Microsoft Edge.
 Edge is a decent browser, but I prefer Vivaldi, which — like Edge — is based on Chrome. I also use Firefox and have icons for Vivaldi, Edge, Firefox, and Opera on the Task bar, but I don't want icons for any of them on the Desktop. And yet there it is. Every time an Edge icon appears, I delete it, but Microsoft repeatedly restores it, apparently when Edge is updated.
Edge is a decent browser, but I prefer Vivaldi, which — like Edge — is based on Chrome. I also use Firefox and have icons for Vivaldi, Edge, Firefox, and Opera on the Task bar, but I don't want icons for any of them on the Desktop. And yet there it is. Every time an Edge icon appears, I delete it, but Microsoft repeatedly restores it, apparently when Edge is updated.
Two of the other icons on my desktop look like they're for Vivaldi, and they will open the Vivaldi browser, but they are links to browser bookmarks and a perpetual calendar I created a few months ago. The other icons at the top of the screen are links to a directory for the APO Equalizer that needs to be reinstalled after every Windows update, a list of complex passwords I can use, GoodSync Explorer, DOS Box, and a graphic showing portrait lighting techniques. Lower on the screen, there are links to restart and shut down the computer, a link to cancel the shutdown or restart process, the Recycle Bin, and a link to start Q-Dir with my preferred arrangement.
I don't want an Edge icon. It annoys me, and you've perhaps seen what I do with annoyances: Even if it takes an absurdly long time, I find a way to eliminate the annoyance. As it turned out, the research was fast and the correction was easy, although it does involve a Registry edit.
The information about the Registry modification is from GHacks and affects all four channels: Stable, Dev, Beta, and Canary. If you want to block icons from just one channel, GHacks describes the process that involves using globally unique identifiers (GUID) as parts of the key names.
Editing the Registry can be hazardous. Making a mistake can cause the computer to become unstable or even make it impossible for Windows to start. Be sure to edit the correct key because some keys have similar names. If you add a key or modify an entry, double check spelling, numbers, and key types.
Microsoft seems to place a new Desktop icon whenever Edge is updated. The real solution to this annoyance would be for Microsoft to stop doing stupid things. Because that's not likely, the solution involves adding a key to the Registry. It's an easy key to add.
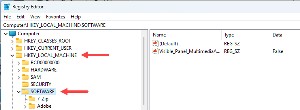 Start by opening the Registry Editor and and drilling down to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft.
Start by opening the Registry Editor and and drilling down to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft.
If there is no EdgeUpdate key, and there probably won't be, right-click Microsoft and choose New, Key. Name the key EdgeUpdate.
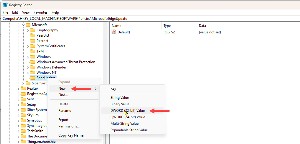 Create the new key as a Dword (32-bit) Value. The default value should be 0.
Create the new key as a Dword (32-bit) Value. The default value should be 0.
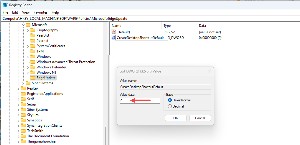 Double-click the key name to open a dialog box and confirm that the value is zero.
Double-click the key name to open a dialog box and confirm that the value is zero.
Now when Edge is updated, Microsoft will no longer place an icon on the Desktop. Note, though, that you may need to repeat this process following a Windows update. That's conjecture because Microsoft hasn't been willing to say anything about the process or the annoyance.
It's no big deal to send a photo an an email attachment these days, or to place the image in the body of the email itself. That wasn't the case 20 years ago. In 2003 we were beginning to see ways to accomplish this and I wrote about one option:
Anybody with a camera and an e-mail account has probably wanted to create an e-mail with photographs in it. Depending on what e-mail application you use, the task might be easy or difficult and the results might be successful. Or not. More times than often it was "or not." Now there's help.
Novatix has a program called SendPhotos that will help. The program's sole shortcoming is that it works only with Microsoft Outlook, Microsoft Outlook Express, or via the Novatix website. I don't like using any version of Outlook and I don't much care for sending mail via a website, but SendPhotos makes it easy anyway. I have set up one account on Outlook Express and, when I want to send an e-mail with embedded photos, I start Outlook Express and click on the SendPhotos icon that Novatix put in place when I installed the program.
The results are excellent, even with e-mail programs that often choke on embedded graphics. The best thing is that it's so easy to use. First, you chooses the photos you want to send. Next, you select the stationery design. (Novatix provides 50 templates and you can download more.) The third step involves adding a title, text, and captions. The final step is sending the message -- either via Outlook (Express) and your standard POP3 account or -- if you use AOL, Hotmail or Yahoo -- via the Novatix website.
The receiver can see your photos immediately. They are, of course, sent as attachments, but they appear within the body of the e-mail's text. You don't need to be a computer guru to send photos or to view them when they arrive.
SendPhotos isn't a shareware program. You'll pay $40 (introductory price $30) for it, but there's a 30-day guarantee. And besides, it's the kind of program that, once you've tried it, you won't return.
When I first tried using SendPhotos (version 1.11) I quickly noticed a frustrating bug: After I carefully typed clever and witty captions for my pictures (well, half-witty, anyway) the captions disappeared and messages arrived with photos captions this way: "Type here to insert caption." Not good. But relief was quick to arrive.
I received an e-mail message telling me that version 1.13 was available. When I clicked on the link to download the new version, the installation was automatic (I think I like that) and immediately my half-witty captions stayed with my messages. What a relief!
Besides being able to buy SendPhotos on the Novatix website, you can also have the system automatically send you 1 to 3 sample e-mail messages with images embedded. If you like to share pictures with your family and friends, but the process is needlessly confusing, give SendPhotos a try.
Novatix no longer exists and seems to have disappeared without a trace.