Listen to the Podcast
27 January 2023 - Podcast #816 - (16:51)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Have you ever signed up for a newsletter or made a purchase from a company you've not dealt with before only to find your email inbox stuffed with questionable offers and spam? Maybe you've wished you could use a disposable address.
There are services that do this, but DuckDuckGo includes some worthwhile extras. LifeWire lists some of the best choices in Top 6 DisposabIe Email Address Services, but the email service provided by the Duck seems like an excellent choice.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
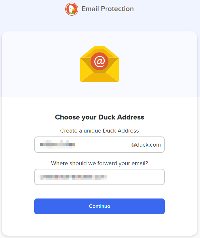 You'll start by creating an address with @duck.com as the domain. As part of that process, you'll tell the service where to send messages it receives. Typically this will be your primary email address. The advantage is that the Duck removes trackers before forwarding the message to you. Trackers tell the sender whether you opened the message, when, and possibly whether you clicked any links.
You'll start by creating an address with @duck.com as the domain. As part of that process, you'll tell the service where to send messages it receives. Typically this will be your primary email address. The advantage is that the Duck removes trackers before forwarding the message to you. Trackers tell the sender whether you opened the message, when, and possibly whether you clicked any links.
Truth in emailing: The weekly TechByter newsletter is sent via MailChimp and does contain a tracker that lets me know how many people read the email and how many clicked a link to proceed to the site. This information is helpful because it helps me to understand which topics are of the greatest interest to listeners. But I also understand why some people might not like this. I don't do anything underhanded with the information and you'll just have to trust me on that because it's impossible to prove a negative.
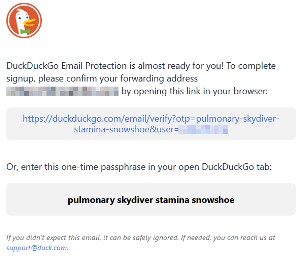 The Duck simply removes the tracking component if there is one and adds a note in the message explaining what it removed. It's a straight pass-through operation. Your messages are not written to disk and the only personal information retained is your duck.com address and the address you want messages forwarded to. That information is essential for the system to work.
The Duck simply removes the tracking component if there is one and adds a note in the message explaining what it removed. It's a straight pass-through operation. Your messages are not written to disk and the only personal information retained is your duck.com address and the address you want messages forwarded to. That information is essential for the system to work.
During the setup process, you'll receive a message from duck.com asking for your confirmation. This keeps someone from submitting your email address and having your messages forwarded to them and from submitting your address and then using it for nefarious purposes. If you don't respond to the message, no account will be created. End of story.
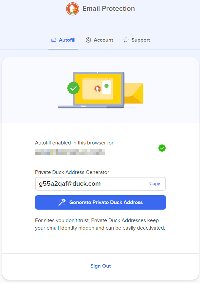
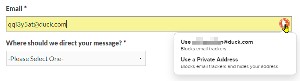 You also should add the DuckDuckGo Privacy Essentials extension to any browser you want to use. This enables the most powerful feature: Temporary addresses. When you sign up for a newsletter or buy something from a vendor you have no history with, you can have the Duck create a one-time address such as g55a2qaf@duck.com. A message sent to that address will be forwarded to you, but you can terminate the address at any time.
You also should add the DuckDuckGo Privacy Essentials extension to any browser you want to use. This enables the most powerful feature: Temporary addresses. When you sign up for a newsletter or buy something from a vendor you have no history with, you can have the Duck create a one-time address such as g55a2qaf@duck.com. A message sent to that address will be forwarded to you, but you can terminate the address at any time.
If the vendor turns out to be a less-than-honorable creep, delete the disposable address and you'll receive no more messages. But if the vendor is someone you want to hear from again, you can change your account information with the vendor to be either your duck.com address, which will eliminate any trackers, or give the vendor your real email address.
It's important to know that some trackers may slip through because new trackers are created frequently and blocking them may harm usability.
DuckDuckGo does not use third-party email services to forward messages because they developed their own software to send and receive email. The two bits of personal information the service retains are encrypted in the database which resides on an encrypted disk. The service also uses encrypted network connections wherever possible. In technical terms, this means that messages are encrypted at all times and that your identifying information is encrypted on the wire and at rest. A few (very few!) email servers still do not support encryption.
DuckDuckGo's Privacy Essentials extension can access your data for all websites, access browser tabs, and access browser activity during navigation. That sounds like a lot, and it is, but it needs these permissions to offer its protections such as eliminating trackers on websites, automatically enforcing encrypted connections, blocking the ability for companies to "fingerprint" browsers by creating a unique identifier for you, and blocking tracking cookies.
If you trust DuckDuckGo, and the company seems sincerely to be interested in providing a search function that doesn't sell your data and helping users improve their online security, then the Privacy Essentials extension and a duck.com email address are what you need.
If you've ever wished you could send and receive encrypted emails, you may have been stopped by the complexity. Encryption is easier than it used to be, but dealing with public keys and private keys can be confusing. And you need to get your recipients on board with receiving encrypted messages, public keys, and private keys. There is an easier way.
ProtonMail, which is headquartered in Switzerland, has both free and paid plans and users can send encrypted messages to anyone -- even those who don't have ProtonMail accounts.
Maybe you're wondering why you'd want to encrypt your email messages. After all, you're not a criminal or a terrorist and your messages are pretty mundane. But is that really true? You may not be a criminal or a terrorist, but probably not all of your messages are mundane. Have you ever sent a message that contains information you would prefer not to appear on a criminal's computer? A credit card number, bank account ID, or password?
The trouble with email is that, even when messages are transmitted on encrypted connections, they're still just plain text on most servers. Maybe you've used tricks like sending a user name in one email message and a password in another message or sending a credit card number in a series of four messages. These practices are better than placing all of the confidential information in a single message, but the process is clumsy and it's not really secure.
Even a free ProtonMail account, with its substantial limitations, makes the process easy. And the limitations aren't significant for casual users. Even free accounts give users a free email address, up to 1GB of storage, up to three labels and folders, and the ability to send up to 150 messages per day.
Paid plans, starting at $4 per month, provide additional features such as a single account with up to 10 email addresses; 15 GB of storage; support for one custom email domain; the ability to use pm.me as the domain in your email address, unlimited labels, folders, and filters; contact groups; an option for an auto-reply message; and no limits on the number of messages sent.
The easiest way to use ProtonMail involves sending a message from one ProtonMail user to another. There's nothing more to do. The message is encrypted when you send it and encrypted when the recipient receives it. You don't need to do anything to encrypt the message and the receiver doesn't need to do anything to decrypt it. The obvious shortcoming is that both the sender and receiver must have ProtonMail accounts and that means both will have to use special email addresses and use ProtonMail's online mail system.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
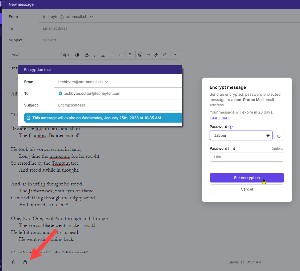 Sending a message to someone who doesn't use ProtonMail involves a bit more work for you, but very little extra work for the receiver. When you send the message, you'll need to mark it as encrypted and specify a password. You'll also need to find a way to communicate the password to the recipient, but that can be done with an SMS message, a phone call, or an email from another account.
Sending a message to someone who doesn't use ProtonMail involves a bit more work for you, but very little extra work for the receiver. When you send the message, you'll need to mark it as encrypted and specify a password. You'll also need to find a way to communicate the password to the recipient, but that can be done with an SMS message, a phone call, or an email from another account.
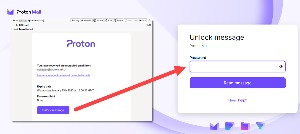 The recipient will receive a message from your ProtonMail account. That message will explain that the receiver needs to click a link and provide a password to view the message. It will also note that the message will be deleted from the server in 28 days or less. The sender can specify the duration. Clicking the link opens a browser and displays a text box where the recipient can type the password. The message can also display a password hint.
The recipient will receive a message from your ProtonMail account. That message will explain that the receiver needs to click a link and provide a password to view the message. It will also note that the message will be deleted from the server in 28 days or less. The sender can specify the duration. Clicking the link opens a browser and displays a text box where the recipient can type the password. The message can also display a password hint.
If both you and the person you're sending encrypted messages to are familiar with public keys and private keys, you can set these up in ProtonMail and the recipient can set them up on any email program that supports encryption. However, if both you and your correspondent understand public and private keys, you'll probably both be using email programs that support encryption.
To learn more about ProtonMail, visit the website.
Those of us who have used Windows since the early days may remember fondly the ability to press the F8 key during the boot process to start the operating system in Safe mode. Microsoft eliminated this capability, but you can restore it.
Let's start with why you might want to do that: Safe mode is intended to allow users to diagnose and fix problems with an operating system. It is also widely used for removing rogue software. In Safe mode, the operating system has reduced functionality and all non-core components are disabled. It usually provides access to utility and diagnostic programs so a user can determine the cause of a problem that prevents the operating system from working normally.
All operating systems have a safe mode: Windows, MacOS, Linux, and even Android phones. For Windows computers, the user can press F8 at boot time to access Safe mode. At least they could until Windows 8 when Microsoft decided that saving a few seconds at boot time was better than providing easy access to Safe mode.
Any time spent waiting for a computer is wasted. I've said that for years, but sometimes it's worth trading a few seconds for improved functionality. This is one of those cases. After all, what do we do as the computer is booting? I don't know about you, but I don't stare at the screen in hopes of speeding the process. I'm more likely to be getting a cup of coffee or taking a look at my schedule on the phone or collecting notes for an article I'm working on. Sometimes the computer can wait several minutes for me to provide a fingerprint to unlock the system. Yes, this means that every morning I give my computer the finger. After all, any time the computer spends waiting for a human means the human is doing something important.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
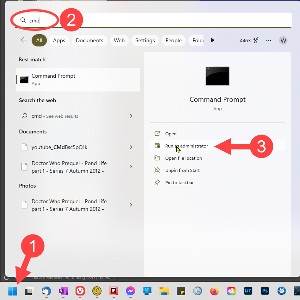 Restoring the functionality is easy and takes less than a minute. Start by opening a Command Prompt as Administrator. There are lots of ways to start the Command Prompt as Administrator. I usually (1) pres the Windows key, (2) type CMD in the search window, and then (3) choose Run as administrator.
Restoring the functionality is easy and takes less than a minute. Start by opening a Command Prompt as Administrator. There are lots of ways to start the Command Prompt as Administrator. I usually (1) pres the Windows key, (2) type CMD in the search window, and then (3) choose Run as administrator.
You should see a User Account Control window asking for your permission to run CMD as Administrator. The Command Prompt window will open. Type (or copy and paste) this one-line command:
bcdedit /set {default} bootmenupolicy legacy
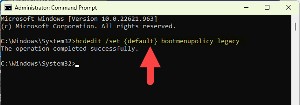 The appropriate response from Windows is The operation completed successfully. If you don't see that, make sure you typed (or copied) the full command accurately.
The appropriate response from Windows is The operation completed successfully. If you don't see that, make sure you typed (or copied) the full command accurately.
Making this change doesn't modify what you see when the computer starts. It just adds a second or two to the process. If you want to start the computer in Safe Mode, press F8 immediately when you power the computer on, and continue tapping (not holding down) the F8 key until you see Advanced Boot Options which will offer Safe Mode and Safe Mode with Networking. Select one and the computer will start in Safe Mode.
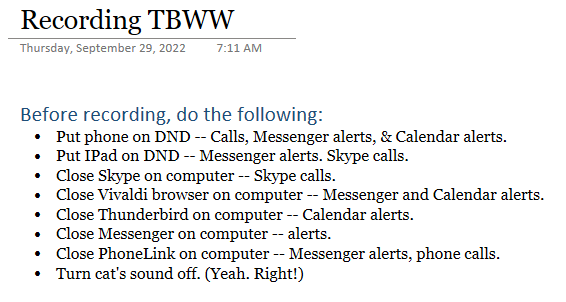 It’s not uncommon to hear a Windows alert sound on NPR, particularly when one of the reporters is on a live remote using Skype or some other communications app. I have a similar problem when recording the TechByter podcast. Sounds generated on the computer are loud and become part of the recording. Sounds from other devices aren’t as loud, but they can usually be heard – and they’re distractions.
It’s not uncommon to hear a Windows alert sound on NPR, particularly when one of the reporters is on a live remote using Skype or some other communications app. I have a similar problem when recording the TechByter podcast. Sounds generated on the computer are loud and become part of the recording. Sounds from other devices aren’t as loud, but they can usually be heard – and they’re distractions.
Now I have a checklist to run through before starting the recording session.
In 2003, an open-source was about to launch. It seemed exciting and I wrote about it:
San Jose Mercury News columnist Dan Gillmor is predicting an "open-source interpersonal information manager" may eventually make it to market. A what???
Gilmore explains, "The software is being designed to securely handle personal e-mail, calendars, contacts and other such data in new ways, and to make it simple to collaborate and share information with others without having to run powerful, expensive server computers."
OK. Got it. Sorta like Act or Outlook, except without the server. But how would that work? Peer-to-peer?
Maybe it's worthwhile to pause here for a moment and consider who the inventor is. Mitch Kapor. Does the name sound familiar? He was once a disk jockey, but that's not why you remember him. No, Kapor was the founder of Lotus Development. The guy who killed VisiCalc by developing Lotus 1-2-3. In other words, a smart guy who's capable of seeing a need, finding a way to fill the need, and then marketing the product.
But how do you make money with "open-source" software? The source code will be posted on the Internet, along with compiled versions of the working program. The calendar part should be available by the end of this year, with the rest of the product coming along by early 2004. So don't toss your copies of Outlook or Act just yet. And how you make money is by providing support, documentation, packaged installers and the like.
The project has been code-named "Chandler" (after novelist Raymond Chandler, the mystery writer). The software will run on Windows, Mac OS X, and Linux.
Twenty years later, Chandler has come and gone. Microsoft launched OneNote in 2003 and Chandler was discontinued in 2009.