Free Wi-Fi is available just about everywhere. Public libraries, restaurants, hotels, and even some stores offer it. It's a big draw and its an inexpensive feature to set up and offer. All that's needed is an Internet connection and a wireless router. But if you use a public Wi-Fi system without protection, the cost of that free service could be exceedingly high.
A thief sitting nearby can monitor the network traffic of an entire store with a device that's no larger than a pack of cards. The simple fact that many people don't understand the threat makes public Wi-Fi networks very attractive targets.
One of the most common tricks thieves use is setting up their own Wi-Fi service that can be used to trick people into connecting to it instead of the store's system. The crook passes information through to the store's network, so users think they're connected. If you're using a Web browser to connect through Wi-Fi, start by making sure you see a lock indicator in the address bar. That means the browser is using the secure protocol (https) instead of the open protocol (http).
But that works only with browsers. If you're using an e-mail client or some other kind of application, everything will be sent in plain text unless the application offers some sort of internal encryption. Even applications that do still may send the user name and password in the clear before switching to an encrypted connection. Needless to say, this isn't really secure.
A virtual private network (VPN) can be used to encrypt everything. The VPN protects all data even if a website doesn't offer https and even for applications that have no encryption functions.
A VPN service adds an encryption layer between your computer and the Internet by routing your encrypted communications through a server operated by the VPN company. For this reason, you won't find very many free VPN services and you'll find that cheap VPN services are almost unusably slow.
One of the best descriptions I've seen to explain VPN compares it to how you might fool somebody who's trying to follow you. Instead of driving from home to your destination, you drive to a closed parking garage, switch cars, and drive out the back entrance. Then the person following you won't know where you went.
Click any of the smaller images for a full-size view.
Press Esc to dismiss the larger image.
Although several VPN services exist, one of the best seems to be Private Internet Access. For $7 per month (or an annual fee of $40, $60 for 2 years), you have access to more than 3000 servers in 35 regions of 24 countries. The company also offers simultaneous connection for up to 5 devices.
A user can install the application on any number of devices as long as no more than 5 are on-line and active at any given time. I confirmed this interpretation of the operating rules with the company's Jonathan Roudier and I'm surprised that the license is this open.
It's not unreasonable to wonder if there is a real threat or if this is little more than a marketing ploy. If you want to see how easy it is to intercept data, search for applications such as FaceNiff, Firesheep, Ethereal, or Wireshark. Download one of them and you can start snooping. Of course this is illegal in some areas, but criminals don't pay much attention to laws. And because they're all but invisible, it's unlikely that they'll ever be caught.
But how likely is it to happen? If you're using Wi-Fi at a small, suburban library, the chances are probably small. If you're in an airport or other location where a lot of people who are in a hurry and are probably not thinking about security gather, the odds are no longer in your favor. Given the modest cost of a VPN application, should you ever use a portable device on a public Wi-Fi system without one? My advice would be not to take the risk.
You might also want to consider installing a VPN on your desktop computer even though it never goes near a Wi-Fi hotspot. That's because of other advantages provided by a VPN connection.
Some websites block access based on the user's IP address. If you travel abroad, you may be in a country that uses censorship filters. Streaming media websites often block users based on their geographic location. VPN software allows user to bypass these restrictions.
On a more mundane basis, a VPN eliminates many of the techniques used by marketers to monitor your on-line activities.
During the process of writing this report, I decided to sign up for Private Internet Access. That $40 fee covers the desktop computer, a notebook computer, a tablet, and two Android devices.
The list at the left shows the servers that are available. I use the automatic connection option, so Private Internet Access picks one for me. If I need my connection to appear to be originating from a specific country, I can select it from the list.
After purchasing a license (there's a 7-day money-back guarantee), you can download a special installer that's good for 48 hours. Using that installer eliminates the need to fill in the user name and password. Installing later will require the generic installer and you'll have to fill in your user name and password. That's also true if you install the application on an Apple or Android phone or tablet. Download the app from the appropriate store, install it, and then fill in your credentials. Either way the installation is easy.
In fact, within 30 minutes of when I downloaded the Windows installer, I had the application running on a desktop system, a notebook, the Surface tablet, an Android phone, and an Android tablet. Installing on the Android devices required that I manually enter the user name and password before running it the first time, but it remembers the login credentials for future use.
By default, the application will not start when the device boots. On Windows devices, there are 2 settings to modify: Start application at logon and auto-connect when app is started. You can specify a location to use when connecting or allow the application to choose the fastest current location.
On Android devices, you'll change just a single setting to enable connection at boot time.
Running the Windows tracert (trace route) command from the command line illustrates some of the information that would be visible. The key point here is that we see the address that my Internet service provider had given me. That number can be used to identify numerous other bits of information.
With Private Internet Access running, we don't see the IP address my ISP assigned.
Here's the kind of difference that makes. Using a service that identifies IP addresses (What Is My IP Address), I retrieved some of the information that could be discerned from my IP address. My location is shown as Columbus and my ISP is Wide Open West.
Private Internet Access selected a server in Matawan, New Jersey.
From here, it's possible to drill down a bit.
In this image, information about my non-VPN connection is on the left and the connection through the VPN tunnel is on the right. You might be wondering how close the reported latitude and longitude are to my exact location. So was I. It's off by about 2.4 kilometers or about 1.5 miles. The postal code is close, but not quite correct.
With the VPN tunnel, my reported location is about 745 kilometers (about 460 miles) east of where I'm actually located and the postal zone is, of course, completely wrong.
I had set up my e-mail client to send mail using an encrypted connection on port 465, but with Private Internet Access enabled, the connection failed. That seems reasonable because the e-mail client was attempting to encrypt an already encrypted connection. Or maybe it was the other way around with PIA trying to encrypt an already encrypted connection. Because the connection is encrypted, it's no longer essential for the e-mail client to establish its own secure TLS connection. When I set the connection to an unencrypted protocol, everything worked normally.
Does using the service cause the connection to be slower? I've run speed tests with Private Internet Access enabled and with it disabled. The differences are within the range of normal speed fluctuation.
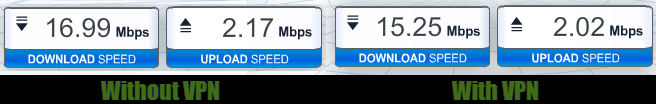
In this case, the connection without the VPN is slightly faster than the connection with the VPN. However, I have run tests where the opposite was true: the connection through the VPN tunnel was better than the straight connection. Overall, given the security that a VPN provides, being without one -- at least when you're connecting to a public Wi-Fi hotspot -- seems illogical.
 No portable device should be without a VPN application.
No portable device should be without a VPN application.Although I started writing this account to describe actions that could be taken to make using a public Wi-Fi system less risky, I repeatedly encountered excellent reviews of Private Internet
Access. Knowing that VPN technology eliminates the need for halfway measures, I started looking at the application, installed it, and tested it. I now understand why the reviews are so good. If you ever use a public Wi-Fi hotspot, or even if you just value privacy on the Internet, this is a worthwhile application to have.
Additional details are available on the Private Internet Access website.
The US power grid is generally acknowledged to be vulnerable to certain types of attacks by hackers. According to CyberX Labs, this kind of attack has already been used in Europe. CyberX is less than 2 years old and was founded by Omer Schneider and Nir Giller after they served in the Israeli military.
The company says that it believes "weaponized" malware called BlackEnergy was used in an attack against Ukraine Power Company. The attack was launched during Ukraine's elections late in 2015. It is also suspected to be the cause of a power cut in Crimea on the 23rd of December.
Another security company, ESET, says that the power outages were not isolated incidents and that other Ukrainian energy companies have also been attacked. ESET claims to have been observing instances of BlackEnergy for some time.
CyberX Labs says BlackEnergy was planted "months before the Ukrainian elections" and that an article by CyberX in the May 2015 issue of DarkReading warned that there might be more undiscovered BlackEnergy components. The report described the theft of data from ICS networks and notes that another attack on the Ukraine media industry is considered an example of this type of large scale operation.
This isn't a new threat. BlackEnergy has been around since 2008, 5 years before CyberX was formed. The Computer Emergency Response Team, part of Homeland Security, warned about it in 2014. The malware can be highly destructive.
Research by CyberX on the Ukrainian attack has produced additional information describing how the malware can format hard drives. CyberX says it believes that it has derived information about how the malware works, but it is "not yet authorized for publication" because the company is in the process of disclosing the information to utilities. Additional research involves security firms such as ESET and Kaspersky.
Damage estimates from attacks to date exceed hundreds of millions of dollars. The source of the attacks is generally believed to be Russia.
There's a very old joke about 3 engineers in a car that's having mechanical problems. One of them works for Microsoft. Two of the engineers suggest typical common-sense engineering solutions to the problem. The Microsoft engineer, of course, suggests shutting the car off and starting it again. Everybody laughs. That could be one intro to this account. Another might be for people old enough to remember Knight Rider on television 3 decades ago. In the show, David Hasselhoff talked to his car, KITT.
Sometimes I talk to my car. Maybe you do, too. The car doesn't do anything, though, unless it's a recent model that includes some speech recognition software. Now Microsoft is getting into the game with Volvo.
Wear a Microsoft Band 2 and you'll be able to talk to your car from a distance. But that's not all. The watch-like device tracks your heart rate, exercise, calories burned, and sleep quality. It includes 11 sensors that record personal information and delivers it to other devices, Microsoft, Apple, and Android.
Users will be able to tell the car to set up navigation, start the heater, lock the doors, flash the lights, or sound the horn. That might be helpful in a large parking lot when you've forgotten exactly where you parked. "Hey, car!" I might say, "Where are you?"
Volvo and Microsoft have announced plans to incorporate HoloLens technology into the project. HoloLens is a wireless holographic computer that Microsoft says could be used to "redefine how customers first encounter, explore, and even buy cars."
Volvo Vice President Thomas Müller says that Volvo wants to make the car experience easy and convenient by using technology in relevant and inspiring ways. "With voice control we are only just beginning to scratch the surface of what is possible with digital assistant functionalities," he said.
Launched in 2001, Volvo on Call became one of first car-based telematics systems intended to provide safety, security, and tracking services in case of accident, breakdown, or theft. The latest version of Volvo on Call still provides the original safety functions as well as a broad range of car and service related functionality. The new options will be available in spring 2016.
 Oculus Rift
Oculus RiftUnquestionably, Microsoft's HoloLens is the technology to beat when it comes to virtual reality, the the HoloLens is currently available only for developers and organizations such as the National Areonautics and Space Agency. The Oculus Rift is now available for pre-order, but it won't be available until March. Does this mean that it's beaten Microsoft to the marketplace? Maybe.
HoloLens will cost more than $600, which is what the Oculus Rift sells for. Oculus Rift will be available in 20 countries near the end of March and will include a headset, sensor, and an Xbox One controller.
If you buy one, be sure that you have hardware that meets these minimal specifications: A graphics card such as the NVIDIA GTX 970 or AMD R9 290, an Intel i5-4590 CPU, no less than 8GB of RAM, HDMI 1.3 video output, 3 USB 3.0 ports and at least 1 USB 2.0 port, and a 64-bit version of Windows 7 with SP1.
You can bet that pornographers will be ready to capitalize on this.