If you have a Windows 8 or Windows 10 computer that you use frequently on battery power, this article is for you. If not, you might want to just scroll down to the next article because there's nothing to see here, folks.
As you know, batteries don't last forever. That's why it's a good idea to check the health of the battery from time to time. It's like occasionally walking around your car to confirm that the tires still have tread so that you won't have a blow-out on the freeway and total the vehicle.
A utility that's available starting with Windows 8 makes the process simple.
Start by opening a command window, type "powercfg /batteryreport", and press Enter. The utility will compile information about any batteries in the computer and save a report to your User directory.
Note that an editing error resulted in the command being called "batterycfg" in the podcast.
Open the report in a browser and prepare to see a lot of information about your battery. The report is in one long screen, but I've created individual screen shots of some of the various areas.
The first section provides information about the computer (it's a Surface 4) and the operating system (Windows 10 Build 10586.17). The second section will list one or more batteries if the computer has them. The Surface has just a single batter using Lithium Ion technology. Full charge capacity is 38,812 milli-Watt hours. You'll also see a value for cycle count. This shows the number of times the battery has been completely drained. In my case, this has occurred 12 times. Batteries can be cycled a finite number of times. The number varies from battery to battery.
The next section shows power usage over the previous 72 hours. There's not a great deal of battery activity because most of the tablet's use is at a desk. The systems logs information periodically showing the computer's current state, power source, and battery capacity remaining as a percent of power remaining and the milli-Watt hours remaining.
Scrolling further down, you'll see a usage chart. Mine doesn't show a lot because the computer hasn't been on battery power much in the past 3 days.
The values used to create the chart appear below it in a table and you'll see the amount of power used, again as a percentage and in milli-Watt hours.
Two charts that I haven't illustrated show the usage history for the life of the battery and its capacity history. These are the two charts that will be of most interest to you as the battery ages. The capacity history report displays the full charge and design charge capacity histories of the battery and it's a good way to monitor the battery's health.
The final chart shows battery life estimates from the time that the operating system was installed. This section is a table that shows the anticipated run-time for the battery based on information the application has collected over time. This will decline over time and it's generally a good way to determine when it's time to have the battery replaced.
The powercfg utility has lots of other functions that can help with (as you might suspect) power management. Some of the functions need to be run from a command prompt with elevated permissions.
To see what else is there use this command:
powercfg /?
Antivirus applications are supposed to protect your computer, but sometimes they have flaws that can be exploited. Kelly Jackson Higgins, writing in Information Week's Dark Reading, described a vulnerability in AVG software that's also now been found in Intel McAfee and Kaspersky Lab antivirus products.
In March, researchers at EnSilo reported that AVG's Internet Security 2015 build 5736 and virus database 8919 exhibited the problem, which involves how the applications allocate memory for read, write, and execute purposes.
The root problem, says Higgins, is that the AV products use "predictable" addresses that could allow malware to exploit applications that are outdated. In other words, it's an edge condition -- but edge conditions do sometimes occur. The flaw would let malware bypass the antivirus system and researchers at EnSilo also found the flaw in Kaspersky Lab's Total Security 2015 and McAfee's Virus Scan Enterprise. Check the article for information about which specific versions are affected.
The Dark Reading article says that all three antivirus providers have patched their applications in current versions, but notes that the same vulnerability could exist in other applications. The flaw cannot be exploited in Windows 10 and is unlikely to be exploited in Windows 8. Those who are still running Windows XP, Vista, and Windows 7 would be at risk.
The article quotes a researcher at EnSilo, who says the flaw turns an antivirus application into a tool for an attacker. EnSilo has released a free tool for companies and vendors to test whether their security products contain the bug.
The good news, according to the article, is that none of the companies -- EnSilo or any of the antivirus providers -- have seen signs of the bug being exploited in the wild.
Read the full article on the Dark Reading website.
Europeans seem to be more serious about privacy than Americans and that was reflected again this week when the EU approved data protection regulations that give citizens more control over how on-line information is collected and managed. The changes won't be fully in effect until early 2017, though.
The rules have been approved by the European Union, the European Parliament, and the EU's member states. Negotiations have been underway for about 6 months to reach a compromise between the rights of individuals for privacy and the rights of companies to collect data.
The changes will make life somewhat more difficult for companies such as Google and Facebook. Some of the primary changes approved this week:
Negotiators weren't able to agree on all aspects of the new data privacy rules, though. One of the remaining points of contention is in regard to which regulators will have the last word in determining when a violation has occurred. Most European Union member nations have their own national privacy agencies and they don't always agree on what constitutes a problem.
No matter what, this will be good news for law firms that represent the social media firms.
Sometimes a product or service catches my attention based solely on its name and that's the case with "Privacy Eraser Free", which claims to be the all-in-one tool to ensure total privacy for PC users. You see, at first I thought it was offering to erase my privacy and that seemed not to be such a good thing. The application is from China and perhaps was named by someone who is not a native speaker of English.
Cybertron Software in Shenzhen, China, says that version 4.7 of Privacy Eraser Free is designed to keep private information on a computer protected and secure. The features, include the ability to wipe files, clean browsing history, remove "traces left by software", and manage Windows privacy. In other words, the same thing that most commercial protective suites already do.
Cybertron Software positions itself as "a leading security systems provider" and says that Privacy Eraser Free "ensures deleted files remain deleted and no one can access private information of any kind, be that browser history, third-party application data, personal documents or anything else."
Deleted files can be restored, even if they've been removed from the Recycle Bin, and temporary Internet files can reveal recently visited websites and downloaded data even if the browsing history has been deleted. Temporary files can reveal personal information.
Privacy Eraser Free's file shredder function permanently deletes files using security wiping standards such as the US Department of Defense standard 5220.22-M (3 passes), US Department of Defense standard 5220.22-M (ECE) (7 passes), and a system developed by New Zealand computer scientist Peter Gutmann (35 passes). A news release from the company says that the drive wiper "helps to completely eliminate the free space of a whole disk drive without any possibility of recovery." I'm sure that's not true. You don't don't want to eliminate free space, but you might want to securely wipe any data that's found there. This is another hazard of having a news release written in a language the writer is not familiar with.
Cybertron says that Privacy Eraser Free keeps track of traces left by third-party applications and removes unnecessary remnants by using more than 250 pre-configured plug-ins, "not to mention user-configured plug-ins." So I won't mention those. The program also manages start-up programs, a feature that's available from numerous other applications and, to some extent, within Windows natively.
Privacy Eraser Free is available for Windows Vista and above. The program supports both 32-bit and 64-bit systems. As you might expect, in addition to Privacy Eraser Free, the company offers a more advanced Privacy Eraser Pro that is not free. Privacy Eraser Pro sells for $20 (1 year license) or $60 (lifetime license). The published (but probably never charged) prices are $40 and $80, respectively.
Cybertron is a certified partner of Microsoft and Intel. The company has been developing applications for home and business computer users since 2002. For more information about Privacy Eraser, visit the Cybertron website.
IBM says that it wants to expand its Green Horizons initiative to reduce pollution and other problems in Beijing, New Delhi, Johannesburg, and other cities. Given the news from China in recent weeks about the extremely heavy pollution, it's clear that the problem is real.
The Green Horizons project will be expanded to enable city governments, utility companies, and factories to better understand and improve their relationships with the environment and to help tackle pressing issues related to air pollution and climate change.
Dr. Jin Yan Shao (right) showcases a prototype of a mobile and compact environmental monitoring unit, at the IBM Research lab in China. IBM is announcing that it will expand its Green Horizons initiative globally to enable city governments, utility companies and factories to better understand and improve their relationships with the environment and to help tackle pressing issues related to air pollution and climate change.
Image provided by IBM.
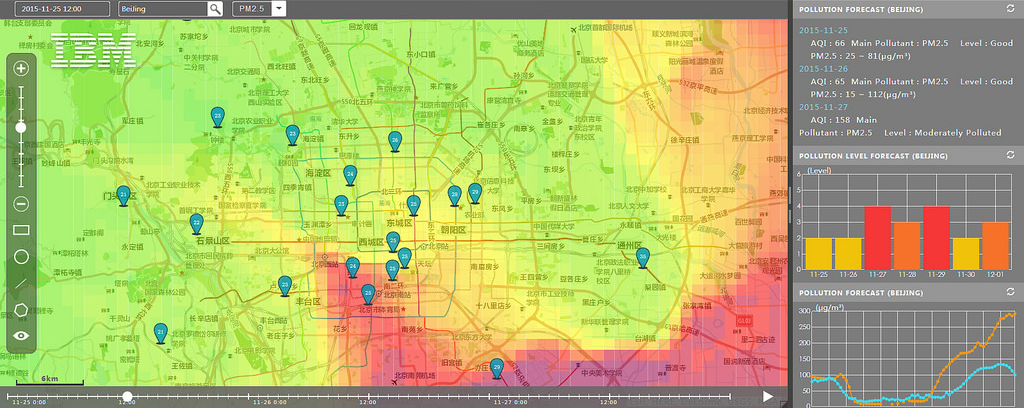
The expansion follows a year-long collaboration with the Beijing Environmental Protection Bureau to include over a dozen commercial deals and research engagements on four continents. IBM's China Research lab is working with the Beijing EPB to provide advanced air quality forecasting and decision support systems that can generate high-resolution pollution forecasts on a square kilometer basis 72 hours in advance and pollution trend as well as being able to provide predictions up to 10 days in advance.
The technology models and predicts the effects of weather on the flow and dispersal of pollutants as well as the airborne chemical reactions between weather and pollutant particles. In the first 9 months of 2015, the Beijing government was able to achieve a 20% reduction in ultra-fine particulate matter. The goal is to reduce the figure by 25% by 2017.
Despite the efforts, pollution in Beijing has been so severe for the past week that a company has been selling bottled air. According to The Independent (London), "[S]ales of Vitality Air - bottles fresh mountain air from Banff and Lake Louise, Canada – have soared in China. A single bottle of the company's 'premium oxygen' costs $28 while a bottle of its Banff air costs $24."
IBM says its Green Horizons engagements apply the company's advanced machine learning and Internet of Things (IoT) technologies to ingest and learn from vast amounts of data, constantly self-configuring and improving in accuracy to create some of the world's most accurate energy and environmental forecasting systems.
An agreement with the Delhi Dialogue Commission will employ the technology to understand the correlation between traffic patterns and air pollution in India's capital. A pilot program with the Johannesburg and South Africa's Council of Scientific and Industrial Research will model air pollution trends and quantify the effectiveness of the city's intervention programs.
Additional clean air projects in China include one with the Environmental Protection Bureau in Baoding, one of China's most polluted cities, and another with the city of Zhangjiakou, host to the 2022 Winter Olympics.
British energy giant SSE is piloting the use of this technology to help plan power generation at its wind farms. The system is able to forecast energy for individual turbines and includes visualization tools to show expected performance several days ahead.
In Japan, the IBM technology is being used with a program that creates power from solar energy using 890,000 solar panels.
And in the United States, home of climate change denial, the technology is being used with the US Department of Energy's SunShot initiative to support supply and demand planning on the nation's power grid. For more information about the technology visit the IBM website.