Although most of the big computer shows such as PC Expo no longer exist, the Consumer Electronics Show continues to run each January in Las Vegas and shows no signs of fading away. As always, there was lots of hyperbole, so let's see if we can slice through some of it.
Wearing the Kodak brand, a new Android smart phone manufactured by the Bullitt Group was on display at the CES. You knew that the "preview" picture I showed last week was fake, right? So the actual Kodak Android smart phone looks like -- surprise -- an Android smart phone.
 In addition to the Android operating system, there's a custom-built user interface, remote-management software, and a special app store. The hardware is an octa-core 1.7 GHz processor in a box with a 5" HD screen, 13 Mpxl rear camera, 5 Mpxl front camera, 8 GB ROM, and a paltry 1GB RAM that the user can expand to 32GB with a Micro SD card.
In addition to the Android operating system, there's a custom-built user interface, remote-management software, and a special app store. The hardware is an octa-core 1.7 GHz processor in a box with a 5" HD screen, 13 Mpxl rear camera, 5 Mpxl front camera, 8 GB ROM, and a paltry 1GB RAM that the user can expand to 32GB with a Micro SD card.
The Samsung Galaxy Note 4, for example has 3GB of RAM and 32GB of built-in memory and it supports Micro SD cards up to 128GB, so Bullitt has some opportunities for improvements.
One interesting feature is the remote management software that allows trusted friends and family to provide help via a PC or tablet. Bullitt also notes that the Kodak heritage means that taking, storing, sharing, and printing photos is easier than on competing devices.
Kodak's vice president for brand licensing, Eileen Murphy, says that photos often are "stuck on mobile phones" because the process of moving photos to other devices confuses users.
The Kodak IM5 will be available for sale around the end of the first quarter.
Microsoft Devices Group unveiled the Nokia 215 at the CES. Instead of "cheap", the term Microsoft uses is "most affordable Internet-ready phone". How affordable/cheap is it? $30, which is being stated as "$29 before taxes and subsidies."
 The Nokia 215 is aimed at first-time mobile phone buyers or those who have wanted to add Internet access to their phones. The irony here is that the person who buys a $30 phone could then pay double that every month for a data plan.
The Nokia 215 is aimed at first-time mobile phone buyers or those who have wanted to add Internet access to their phones. The irony here is that the person who buys a $30 phone could then pay double that every month for a data plan.
Available in both Single SIM and Dual SIM models, the Nokia 215 will expand the reach of Microsoft services at more affordable prices.
The Nokia 215 has a built-in flashlight and offers "up to 20 hours of talk time" and "outstanding battery life" (manufacturers always overstate battery life). Instead of streaming audio, the phone comes with a built-in FM radio and the ability to play MP3 files. There's a camera with VGA resolution. VGA, by the way, is the standard that Sony used with it's original digital camera, the one with a built-in disk drive -- 640 x 480 pixels.
The screen has a 2.4-inch form factor with 320x240-pixel resolution and the phone supports up to 32GB of memory via a Micro SD card.
In other words, the board rooms at Apple and Samsung are probably not crowded with executives who are trying to figure out how their companies will survive in light of this new entry.
Router manufacturer D-Link says its new PowerLine AV2 devices will enable gigabit communications speeds over standard power lines. If it works, this will be a welcome development for people who live in buildings that aren't Wi-Fi friendly.
 The primary problem with powerline networking to date has been the limited data transfer rates. After all, powerlines are designed to carry 120-Volt, 60-Hz electricity instead of low-voltage, high frequency data.
The primary problem with powerline networking to date has been the limited data transfer rates. After all, powerlines are designed to carry 120-Volt, 60-Hz electricity instead of low-voltage, high frequency data.
There are 2 models DHP-701AV and DHP-601AV. Both will be available for purchase before the end of the first quarter.
Turtle Beach makes a lot of audio gear for computer users and is a big name in the gaming market, so one would expect the company to announce new devices at CES. One would not be disappointed.
 This year the company brought out new gaming headsets, including the Elite 800X, XO Seven Pro, and XO Four Stealth. The new "HyperSound virtual reality audio solution" was highlighted, too. Moving beyond audio applications, Turtle Beach also announced a new line of PC gaming accessories, including keyboards, mice and mouse pads.
This year the company brought out new gaming headsets, including the Elite 800X, XO Seven Pro, and XO Four Stealth. The new "HyperSound virtual reality audio solution" was highlighted, too. Moving beyond audio applications, Turtle Beach also announced a new line of PC gaming accessories, including keyboards, mice and mouse pads.
The Stealth 500X headset is what the company calls the first 100% wireless headset for the Xbox One. With these on your head, you'll have 7.1-channel surround sound. At $200, they're not cheap. They're also not new for CES. Turtle Beach introduced them late last year.
The Elite 800X headphones are new and include active noise cancellation and a microphone that doesn't require a boom. The XO Seven Pro is licensed by Major League Gaming and features "Superhuman Hearing". That's some of the hyperbole I mentioned earlier. Superhuman Hearing is simply a sound-leveling process that reduces the dynamic range of the sound and thus makes quiet sounds that are hard to hear louder. The XO Four Stealth is a lightweight gaming headset for Xbox One and mobile devices.
The new gaming accessories carry the Turtle Beach name, but are manufactured by Nordic Game Supply. They won't be available until spring. In addition to mechanical keyboards (Impact 700 and Impact 500), there's a programmable laser mouse (Grip 500), and optical mouse (Grip 300), and 2 mouse pads (Drift and Traction).
With about three quarters of a year to go, Microsoft developers continue to work on the next version of the operating system. I installed the public beta on an older 32-bit notebook computer and make a point of using the system for at least a few hours every month.
I tried to make the case for "lifetime" licensing for Windows on the 2 Nov 2014 program. It would make sense for Microsoft to license Windows on a per-computer basis and then allow automatic free updates for as long as that computer remains in service.
That's probably too revolutionary a concept for Microsoft's finance managers, but it appears that users of Windows 8 and 8.1 will be allowed to upgrade their systems to Windows 10 without cost. Microsoft says that users of Windows version 7 and later will be able to perform an in-place upgrade. That was expected. Those who want to upgrade an older computer from Vista or XP will need to perform a clean installation, meaning that the disk will be formatted during the process.
Various reports have indicated that Microsoft is planning the no-cost upgrade for Windows 8 users and will charge a "nominal" fee for those who own Windows 7 computers. Vista and XP users would be required to pay the full cost of the new operating system, whatever that cost turns out to be.
Windows 10 is expected to include a new Web browser code-named Spartan. The new browser hasn't yet been included in the public beta, but there are hints that Microsoft will demo the new browser at an event on the 21st of January. Spartan won't replace Internet Explorer, but will be offered as a supplement. It's being positioned as a fast, lightweight browser. In effect, Microsoft is celebrating Internet Explorer's 20th birthday by giving it a younger sibling that will continue to use the Trident rendering engine, but will look and feel more like Firefox or Chrome.
Microsoft will continue along the path of creating a single operating system with variants for servers, desktops, notebooks, tablets, and phones. The variations may be slightly more pronounced with increased emphasis on the desktop for "traditional" computers. On desktop systems, booting to the Desktop will be the default operation. Taking a page from the responsive website operation book, Microsoft says that Windows 10 will modify itself to fit the device it's been installed on.
E-mail is often used to send proprietary information (business development plans, for example) even though most people probably know that e-mail is even less secure than a postcard. Encryption will protect your data, but encryption is puzzling, or frightening, or both. A vice president of development at CDK Global, Phil Turner, who I’ve known for more than 30 years, recently explained encryption in an uncommonly clear article that simplifies this complex subject. He gave me permission to use it here.
There are two fundamental tools in modern cryptography: hashes and ciphers. Hashes are used to create a “fingerprint” for a document and only work in one direction. A document is run through a hash algorithm which produces a fingerprint for the document. Every time the document is run through the hash algorithm it produces the same fingerprint, but if anything in the document changes, the fingerprint will change as well.
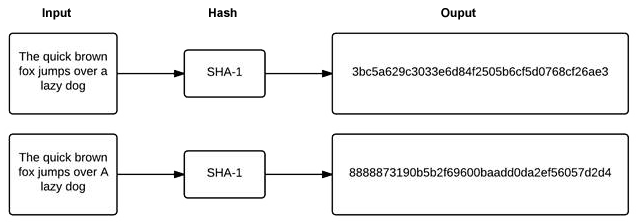
Note the small difference above ("a lazy dog" in the top example and "A lazy dog" in the bottom example.)
Ciphers are the workhorse of data encryption and function in two directions: encryption and decryption. A document is run through a cipher’s encryption mode and the result is an encrypted document that renders the information in the original document unusable to anyone except the recipient. The encrypted document can then be run through the cipher in decryption mode which then reconstitutes the information in the original document. For the cipher to do its magic, it requires a “key” which is simply a little chunk of data used to uniquely encode the document. How the ciphers use a key separates them into two broad classes: symmetric ciphers and asymmetric ciphers.
What makes a cipher symmetric is if the same key is used to both encrypt and decrypt the document.
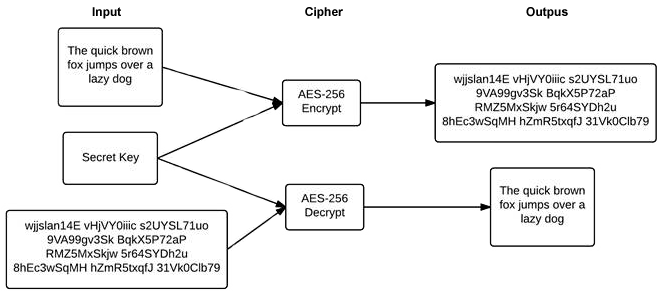
This key is typically referred to as a “secret key” because anyone with this key can decrypt the encrypted document. One needs to keep the key secret and known only by the originator and intended recipient of the document.
The advantages of a symmetric cipher are that it is very fast and there are no restrictions as to the size of the document which can be encrypted with cipher algorithm. The disadvantages of a symmetric cipher are around keeping the secret key known only by the intended recipient. One must choose a “strong” secret key then distribute the key to the recipient in a manner where only the recipient knows the key. The strength of the key is determined by how easy it is to guess the key so creating a long key by randomly selecting numbers, upper, and lower case letters provides a strong key. Selecting short keys or using a single word from the dictionary would create a weak secret key.
A cipher is asymmetric if instead of a single secret key, the cipher uses a pair of keys and whichever key is used to encrypt the data, only the other key in the pair can be used to decrypt the data.
Instead of calling the key a secret key, usually one of the two keys is designated the “private” key and is kept secret, while the other key is designated the “public” key and can be widely distributed without concern about who has access.
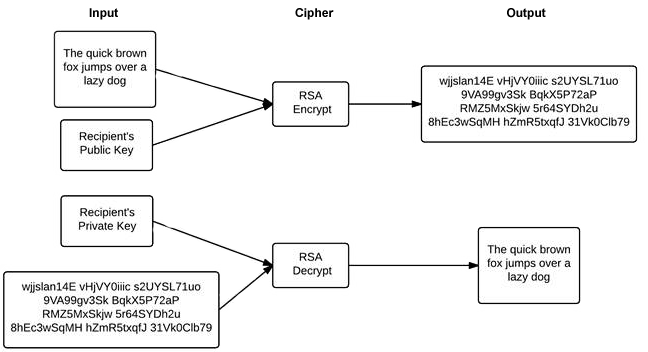
This allows the recipient to distribute their public key to the originator of a document, and then the originator can encrypt the document with the recipient’s public key. The resulting encrypted document can only be decrypted by the recipient with the recipient’s private key. This solves the secret key distribution problem, but there are two problems with asymmetric ciphers. The first is that they involve very complex computations, so they are slow. The second is that there is a size limitation for the document that can be encrypted by any given key. For example, an asymmetric cipher such as RSA with a 2048-bit key (which is considered to be a long key), can only encrypt around 250 characters of data
PGP encryption leverages both symmetric and asymmetric ciphers to give us the best of both worlds.
When PGP encrypts a document, it generates a long, random, strong one-time-use secret key which is called the session key. This session key is used with a symmetric cipher such as AES-256 to encrypt the document. The session key is then encrypted with an asymmetric cipher such as RSA using the recipient’s public key. The encrypted document and the encrypted session key are combined to create the PGP-encrypted message which is sent to the recipient. To decrypt a PGP-encrypted message, the recipient’s RSA private key is used to decrypt the session key, then the session key and the AES-256 symmetric cipher is used to decrypt the document.
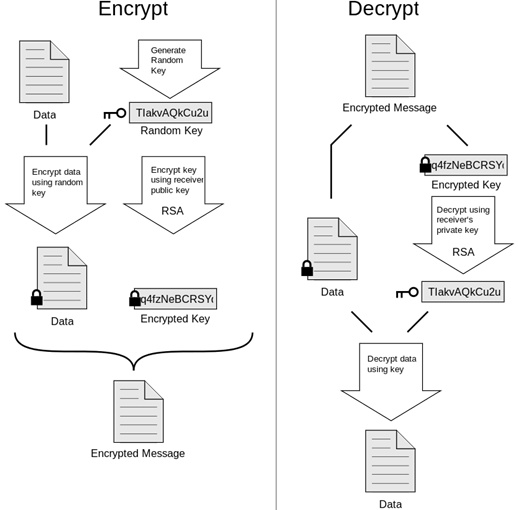
This allows PGP to solve the key distribution problem using the strengths of an asymmetric cipher and to solve the document length and speed problem using a symmetric cipher. You can find more information for PGP by looking up Pretty Good Privacy (that’s what PGP stands for) on Wikipedia.
Digital Signatures – The Extra Credit Problem: A digital signature allows the recipient of a document to verify that the document was originated from a given party and was not modified in transit. To accomplish this task, we need an asymmetric cipher and the other tool in our cryptography toolbox – the hash.
First, the originator of the document needs to have an asymmetric cipher key pair and distribute the public key to the intended recipients.
The originator then creates a cryptographic hash of the document, and encrypts that hash using their private key to create the digital signature. The originator can then transmit both the document and the digital signature to the recipient.
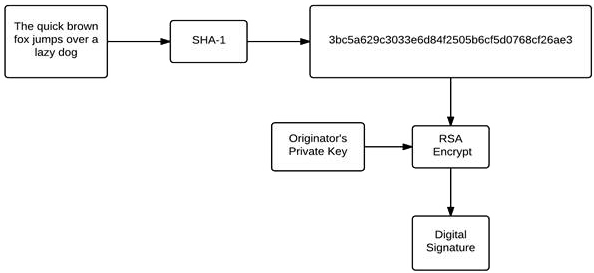
The recipient, to verify the document, decrypts the hash using the originator’s public key and also creates another hash by processing the received document through the hash algorithm. If the two hashes are the same, the document was not altered in transit and was indeed created by the originator.
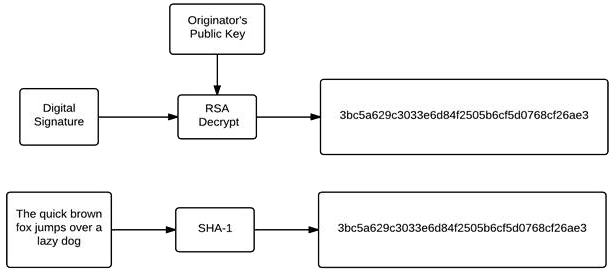
How do we know this? If the document were modified in transit, the hashes would not match. If the document was forged (created by someone other than the purported originator), then decrypting the encrypted hash with the originator’s public key would yield “garbage data” and again, the hashes would not match.
Complicated? Sure, but digital signatures, digital certificates, and SSL are just combinations of these hashes, symmetric, and asymmetric ciphers.
It could be that crooks have already stolen everything that they can steal. The IBM report notes that although the number of attacks was down, crooks still snagged more than 61 million customer records last year.
IBM says attacks were down by half in 2014, but yields were way up. Most of the crooks scaled back their hacking efforts around Black Friday and Cyber Monday. The report was created by IBM's Managed Security Services team of analysts.
The report notes that attackers are becoming more sophisticated and they're using complex techniques that give them access to confidential records with increased efficiency. So although the number of incidents is down, the threat has actually increased.
The primary threats come from organized cyber crime rings according to Kris Lovejoy, the general manager of IBM Security Services, who says that it's more important than ever for those who deal with customers' data to "have the right people, processes, and technology in place to take on these growing threats."
Key points from the report
IBM notes that there has been a rise in the number of point-of-sale (POS) malware attacks, but most incidents that target the retail sector involved command injection or SQL injection. Both of these attack vectors are well known to security experts and should be high on the system developers' lists of techniques to protect against.
An Israeli company, Nice Systems, has announced an application aimed at preventing online fraud. Nice Systems creates applications designed to improve customer experience and simultaneously protect the business.
The Real-Time Fraud Prevention solution attempts to detect and prevent fraud in real time. Among the techniques used are voice biometrics and other analytics. Nice says the system identifies 90% percent of fraudulent callers in the first few seconds of a call. The company didn't provide any information about false positives, which could adversely affect customer service.
The system screens all interactions to detect suspicious activity so that company employees can handle high-risk interactions properly. The intent is to accurately flag fraudulent activities without needlessly delaying or disrupting legitimate callers.
Nine to Five Mac is predicting that the much anticipated Apple Watch will be available soon, perhaps before the Ides of March.
The site reports that the date has been moved up to March, which is slightly more detailed than the previous "early 2015" expected ship date. "Senior Vice President of Retail Angela Ahrendts got a bit more specific by telling employees that the launch will occur in the 'spring', after the Chinese New Year," the site noted.
Training programs in Cupertino and Austin are reported to be scheduled for mid February and most Apple stores around the country will send at least one employee to be trained on how the Apple watch works. Those employees are expected to return to their stores and share the knowledge.
Unlike most watches, this one will have to be recharged every night and the charging will be done wirelessly.
The $350 watch will be Apple's basic model, but some users will want the mid-range model, rumored to be priced at $500 or so. And then there will be the gold-standard Apple watch, featuring real gold, and a price tag "in the thousands of dollars".
Did you buy in to the silliness of the pundits a year or so ago when they said the personal computer was dead? We would all be doing everything on our smart phones and tablets? Probably not, but a lot of people did.
This week's Consumer Electronics Show may have shown the pundits what anyone with any common sense already knew: smart phones and tablets can't do everything that most people want to do. The PC, whether desktop or notebook, will be around for a while.
A smart phone is perfect for checking messages, keeping up with Facebook, or grabbing photos and videos. Tablets are making some inroads into digital image processing, but only as adjuncts to desktop systems.
It's clear that the market for personal computers is changing, but that market is not disappearing.
Smart phones and tablets are still new. People who have purchased them in the past 2 or 3 years instead of replacing a desktop system are now beginning to think about replacing those systems. What they're finding is desktop systems that take up less of the desk and notebooks that aren't so heavy that you get a sore shoulder from carrying them through an airport. By using smaller frames (such as those used in portable devices), manufacturers are placing larger screens in smaller boxes.
Of course, you can go only so far with that. The box has to be at least as large as the screen -- but not by much. And the manufacturers are adding features that can't be added to a smart phone or a tablet.
The bottom line is, as it always has been, that the intelligent user will fit the tool to the task at hand.