Nigeria? Why Don't Scammers Claim to be from New Jersey?
A research paper by Microsoft's Cormac Herley asks the question Why do Nigerian Scammers Say They are from Nigeria? You may have wondered about this, as have I, and Herley has an economically plausible explanation. The 14-page report includes a lot of sophisticated formulas that I'll not try to parse but the conclusion is definitely worth sharing.
 Every time I receive a Nigerian scam message it occurs to me that only a gullible fool would fall for such an obvious ploy but it seems that this is the point. But let's start at the beginning.
Every time I receive a Nigerian scam message it occurs to me that only a gullible fool would fall for such an obvious ploy but it seems that this is the point. But let's start at the beginning.
The problem scammers face is one of differentiating what are called "true positives" (people who can be victimized) from "false positives" (people who appear to be good targets but who will cost the scammer a great deal of effort for zero return.)
Much of the paper explores the various mathematical models that are in play and, in the midst of all the formulas, points out that those who have fallen for a Nigerian scam, may be more likely to fall for the related “fraud funds recovery” scam. Apparently P. T. Barnum was right and a fool is born every minute.
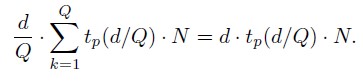
An example of the math behind the theory.
The attacker risks two types of errors: He may attack a non-viable user, spend time cultivating the victim, and gain nothing or he may decide not to attack a viable user and thereby forgo any gain. This is a "binary classification problem". Although the cost of sending spams is near zero, the cost of following up by e-mail and phone with potential victims is not. This part is actually quite labor intensive.
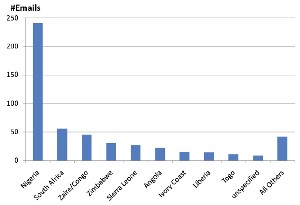
For example, a population of 200 million users might contain 2000 viable candidates, of which 80 will be attacked if the scammer uses what Herley calls "optimal strategy". His paper explains how this may be accomplished but this summary won't go into that. But 96% of the viable users who would succumb if attacked and yield a payback to the scammer will escape harm because there is no strategy to attack them without also attacking so many non-viable users as to destroy the profit.
 And that's where Nigeria comes in.
And that's where Nigeria comes in.
Nigeria is by far the country that is most commonly cited in scam spams. Herley says that if the goal is to maximize response to the e-mail campaign, it would seem that mentioning “Nigeria” (a country that to many has become synonymous with scams) is counter-productive. One could hardly choose a worse place to claim to be from if the goal is to lure the unwary into email communication.
But what seems like common sense here doesn't work. The scammers need to identify the most gullible recipients. "Since gullibility is unobservable, the best strategy," Herley writes, "is to get those who possess this quality to self-identify. An e-mail with tales of fabulous amounts of money and West African corruption will strike all but the most gullible as bizarre. It will be recognized and ignored by anyone who has been using the Internet long enough to have seen it several times. It will be figured out by anyone savvy enough to use a search engine.... It won’t be pursued by anyone who consults sensible family or friends or who reads any of the advice that banks and money transfer agencies make available. Those who remain are the scammers ideal targets. They represent a tiny subset of the overall population."
How Can This Be Used to Our Advantage?
Herley suggests that injecting false positives into the scammers' operation could eventually make the endeavor financially impractical. The portion of the population successfully attacked falls much faster than victim density and at low densities the attacker is far more sensitive to false positives.
Herley's conclusion: Binary classification reveals the fundamental trade-off that an attacker must make. To maximize profit, an attacker will not pursue all viable users but must balance the gain from true positives against the cost of false positives. This difficulty allows many viable victims to escape harm and, for attacks with low victim densities, the situation is extremely challenging for the scammer. Unless viable users can be distinguished with great accuracy, most viable users must be left un-attacked. However, building an accurate classifier requires many viable samples. This suggests that at low densities certain attacks pose no economic threat to anyone, even though there may be many viable targets. Most work on researching vulnerabilities, Herley points out, ignores this fundamental question.
"Thinking like an attacker is a skill rightly valued among defenders. It helps expose vulnerabilities and brings poor assumptions to light. We suggest that thinking like an attacker does not end when a hole is found, but must continue (as an attacker would continue) in determining how the hole can be monetized. Attacking as a business model must identify targets, and this is easy only if we believe that attackers have solved a problem that has vexed multiple communities for decades."
If you'd like to read the full 14-page abstract by Cormac Herley, you'll find it on the Microsoft Research website. (This link downloads the PDF directly.)
How to Speed Up a Slow Computer (2)
That computer that seemed so fast when you bought now seems to crawl. It's not all your fault but there are some things you can do to remedy the situation. This is part 2 of a series and although the examples here are for a Windows 7 system, most of processes will work on Vista or Windows 8, and even on XP. The names may differ slightly but most of what you need to make the improvements will be there.
If you have a spare thumb drive lying around, you might be able to use it to improve the computer's speed. This trick won't work on XP or Vista and it's a bit of a long shot regardless but we'll take a look at it as the first of this week's suggestions and if it works, it's the fastest and easiest way to speed up a computer.
Click a small image for a larger view. Click the larger view to close it.
Add a ReadyBoost Drive
ReadyBoost is a technique that permits the computer to borrow memory from flash drives. It can handle up to eight drives with a maximum 256 GB of additional memory.
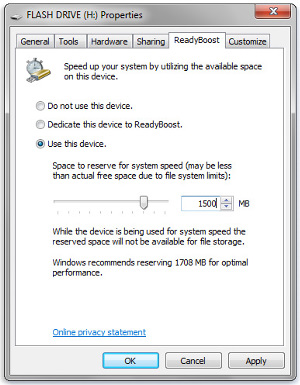 For ReadyBoost to work, the flash drive or memory card (yes, if you have a second flash drive for your digital camera, you can use it when the camera doesn't need it) needs to have at least 1 GB of available space. ReadyBoost will tell you if it doesn't and, if enough space is available and the device meets the minimum requirements, Windows will show you how much space it recommends for optimal performance.
For ReadyBoost to work, the flash drive or memory card (yes, if you have a second flash drive for your digital camera, you can use it when the camera doesn't need it) needs to have at least 1 GB of available space. ReadyBoost will tell you if it doesn't and, if enough space is available and the device meets the minimum requirements, Windows will show you how much space it recommends for optimal performance.
Make sure that any device you want to use for ReadyBoost can handle data transfer at 2.5 MB/sec or faster for reading and at least 1.75 MB/sec for writing. Faster is better. If you have a USB drive or memory card that meets these specifications, it's easy to set up ReadyBoost.
Plug in the flash drive or flash memory card into your computer and, if nothing happens, you've disabled AutoPlay. Visit the Control Panel to re-enable AutoPlay.
When the AutoPlay dialog open, select the General options tab and click Speed up my system. Then in the Properties dialog box, click the ReadyBoost tab, and select Dedicate this device to ReadyBoost (to use the maximum available space on the flash drive or memory card for ReadyBoost) or Use this device (to use less than the maximum available space on the device for ReadyBoost). In either case, any existing files on the device will be preserved. Click OK to complete the process.
Defragment Your Hard Drive
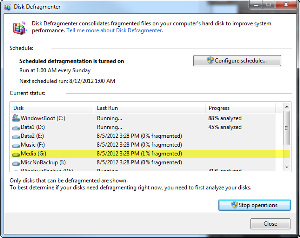 Windows 7 does a good job with this all by itself and the process is scheduled to occur once per week. You may want to consider changing the schedule, though, but don't do this if you have installed a solid-state disk (SSD) drive. SSDs don't like being defragmented and the process can actually reduce their service life. If you have standard disk drives, though, the ones that spin, you may gain a bit of additional performance by running the defragmentation process.
Windows 7 does a good job with this all by itself and the process is scheduled to occur once per week. You may want to consider changing the schedule, though, but don't do this if you have installed a solid-state disk (SSD) drive. SSDs don't like being defragmented and the process can actually reduce their service life. If you have standard disk drives, though, the ones that spin, you may gain a bit of additional performance by running the defragmentation process.
Press the Windows Key and type defrag. This will open the Disk Defragmenter.
If you don't see Scheduled defragmentation is turned on, click Configure Schedule and set up regular defragmentation. Unless you've previously turned it off, though, this will be turned on.
Select all of the drives listed and click Analyze. The process will take a few minutes (or possibly a lot of minutes.) In my case, it was complete in about 10 minutes and showed that the worst fragmentation (1%) was on drives C and G. If you see no drives with fragmentation higher than 15%, close the dialog box and get back to work.
If you see one or more drives with excessive fragmentation, select them and click Defragment Disk.
Disk fragmentation is a result of the way that Microsoft writes files to the drive. When files need to be read into memory, the process is always faster if the files are in a single contiguous chunk instead of scattered all over the drive. the defragmentation process identifies files that are split into many pieces and recombines them.
Defragmentation is likely to create a noticeable improvement only if you had turned off defragmentation and your disk(s) are badly fragmented.
There are two more ideas for improving your computer's performance. I'll continue this topic next week.
Short Circuits
Identifying the Source of Viruses, Both Computer and Human
A Swiss research facility has developed software the scientists say can be used to quickly identify the source of a computer virus, a human virus, or a rumor. And they say their application can be used to identify terror suspects.
Doctor Pedro Pinto, a postdoctoral associate at Lausanne's Federal Polytechnic, AFP, says that this method can find the source of all kinds of things circulating in a network just by listening to a limited number of members of that network. For example, "By reconstructing the message exchange inside the 9/11 terrorist network extracted from publicly released news, our system spit out the names of three potential suspects – one of whom was found to be the mastermind of the attacks, according to the official enquiry."
The algorithm examines the data and identifies the route taken by the information and thereby identifies the source. The investigation uses the time at which the data is passed from sender to recipient to identify the path and eliminate false trails.
Pinto's research was published in Physical Review Letters. The techniques can be used to identify the source of false rumors. Pinto says that the source of a rumor sent to 500 contacts can be identified by examining posts received by no more than 20 people.
Pinto says that the same process can also identify the origin of spam or computer viruses and to help epidemiologists identify the source of viruses. Pinto traced the source of a cholera outbreak in South Africa by using his software to examine water and transport networks.
Windows 8—Now Available for Some of Us
Members of Microsoft TechNet can now download the release-to-manufacturing disc image of Windows 8 and I've done that. Thursday evening I booted to a Windows 8 installation disc and, after filling in some of the details, I was told that I had booted from a DVD (actaully, I knew that already) and that I should start Windows normally and then load the DVD if I wanted to upgrade the system. This was on a computer that has both Windows 7 and Windows 8 (preview) installed.
The installer then told me that it was making sure the computer was ready to have Windows 8 installed and that the process would take a few minutes. It took many minutes. Then it displayed several applications installed on the notebook computer that either needed to be reinstalled under Windows 8 or that weren't compatible with Windows 8. I could leave them or uninstall them. I uninstalled all 3 questionable applications, including the Intel Wi-Fi application (and that made me nervous).
Then a restart was required. Hmmm. Do I need to boot from the DVD or allow the normal boot process to continue? No clues provided. So I allowed the normal boot process to continue and selected Windows 7. Then I started the Windows 8 installer again. This is what I should have done the first time and I should have remembered that.
After rebooting, I had the option of continuing from where I left off (that's what I selected) or starting over. Then, nothing. So I started the installer (again) from the DVD, once again wondering if anyone on the development team had actually tried this process. Then I noticed that the "Making sure you're ready to install" function was already running in the background. D'oh! Eventually, and after telling the Java updater (several times) that I wasn't interested in a Java update right now, I was "Ready to Install". ("Your PC will restart several times. This might take a while.")
Reboot.
Reboot.
Reboot.
(Wow. This is fun.) Well, the installer did warn me that this would happen several times.
I was then asked to provide information to identify myself and the installer then said that it's "getting your PC ready". (This will take a few minutes.) During the process, the screen cycled through various colors. Then it began "installing apps". (This will take a few minutes.) And then the installer was "taking care of a few things". ("Please don't turn off your PC.") "Almost ready. Please don't turn off your PC."
And voiala! It's the Windows 8 Start Screen!
I selected "restart" and the boot manager offered Windows 8 (on volume 2) and Windows 8 (on volume 3). Hmm. Windows 8 on volume 2 was the previous Windows 7 partiton, so that's what I selected. And we're off to the races.
For those who aren't members of TechNet but who would like an advance explanation of what you'll find in Windows 8 and Office 2013, I encourage you to visit Lynda.com. David Rivers offers a 92-minute summary of what you'll find in the new operating system. Only a few of the videos in the series are available for free but for the cost of a 1-month subscription you'll be able to view this series and various other programs that you'll find useful.
Rivers has another 76-minute series on Office 2013 and it touches on all of the major applications: Word, Excel, PowerPoint, OneNote, and Outlook. Windows 8 is the operating system that will be on your next computer and Office 2013 is your next version of the office suite. Now is a good time to learn what's in the pipeline.
As it turns out, the notebook computer upgrade from Windows 7 to Windows 8 wasn’t quite as successful as I had hoped. The Windows 8 Preview on a separate partition was fast and everything worked. The Windows 8 RTM (release to manufacturing) image that I used to update the old Windows 7 partition was painfully slow and my DVD no longer worked.
Details are here.
For Android, No Flash (In or Out of the Pan)
Adobe has removed its Flash Player plug-in for Android from the Google Play Store. This isn't a surprise because the decision had been announced earlier as part of Adobe's decision to halt development of the software for mobile devices.
The decision was made now because of the release of Android 4.1 (Jelly Bean). Adobe says the new version of the Android operating system would result in what the company called "unpredictable behavior" that would be unacceptable.
So if you have the Flash player installed on an Android device and you have upgraded the device to Jelly Bean, or you're planning to, Adobe says you should uninstall the Flash player.
Adobe notes that the decision does not affect the Flash player for desktop and notebook computers. It also does not affect Adobe Air, an application that allows developers to convert Web-based applications into mobile apps using Flash.
Crack Google's Chrome Browser and Win Big Money
Google is placing as much as $2 million on the table for those who can find and exploit a security flaw with Chrome. And this is the second time around for Google. According to a company blog, "the first Pwnium competition held earlier this year exceeded our expectations. We received two submissions of such complexity and quality that both of them won Pwnie Awards at this year’s Black Hat industry event. Most importantly, we were able to make Chromium significantly stronger based on what we learned."
Google is looking for people who can perform various types and levels of exploits, from a full exploit that uses only bugs in Chrome itself to full exploits using flaws in plug-ins or the computer's operating system and even incomplete exploits that might, for example, run in a sand box but not be able to escape.
A "sandbox" is a security mechanism that separates running programs. It is often used to execute untested code, or untrusted programs from unverified third-parties, suppliers, untrusted users and untrusted websites. The point of using a sandbox is to protect other applications on the computer and the computer's operating system. A sandbox usually provides a tightly-controlled set of resources for guest programs to run in and disallows network access and the ability to inspect the host system or read from input devices.
Prizes range from $40,000 to $60,000 for full exploits. Amounts awarded for incomplete exploits will be determined by committee.
Google Software Engineer Chris Evans says that exploits must be demonstrated against the latest stable version of Chrome. Chrome and the underlying operating system and drivers will be fully patched and running on an Acer Aspire V5-571-6869 laptop. The person who writes the best exploit gets to take the computer home, too.
Participants must document the exploit, which is clearly why Google is interested, and the bugs must be something that Google programmers haven't seen previously.
Mystery Computer Virus has Kaspersky Asking for Help
Why would a computer virus watch for computers with no Internet connection and install itself only when no Internet connection is found? That's one of the primary questions software engineers at Russian antivirus maker Kaspersky are trying to solve. A computer virus called Gauss, discovered in June, is active in Lebanon.
Making the situation even worse is the fact that the payload the virus carries is encrypted so Kaspersky is now asking others for help. In a blog post this week, the company said that it has thus far been unable to break the encryption. "We are presenting all the available information about the payload," Kaspersky's blog says, so that someone can find a solution and unlock its secrets. "We are asking anyone interested in cryptology, numerology and mathematics to join us in solving the mystery and extracting the hidden payload."
The Gauss virus has been found on more than 2500 computers. Although most are in Lebanon, it has surfaced elsewhere. The amount of encryption involved and the locations where the virus has been found—various Lebanese banks, Citibank, and PayPal—suggest that this is a large and potentially dangerous attack.
The fact that Gauss specifically seeks out computers that are not connected to the Internet suggests that it is looking for computers that are generally considered safe by virtue of being off the public Internet. So far it seems primarily to be collecting user names and passwords.
Kaspersky's blog speculates that Gauss is a state-sponsored attack but the question then would be which state? Israel and the United States have been implicated in development of the Stuxnet virus that was used to delay Iran's nuclear program. So who created Gauss?



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
