Scareware: Yet Another Plague to Endure
You're sitting at the computer and working on something. Suddenly a pop-up warns you that the computer is infected and that you must do something immediately to remove the threat. You're offered a link. You click it. And from there, it's downhill all the way. This problem is real and it's serious. For network administrators, it could be a disaster.
No matter where you see something like this, the first thing to keep in mind is this: You don't have to do something immediately. Take the time needed to think things through. As first responders are taught: Assess the situation so that you're part of the solution and not part of the problem.
Fake virus warnings are common and they use social engineering to lure users to malicious sites and scare them into paying for fake threat removal tools that only make things worse. Antivirus company Sophos has prepared a report called "How to Keep Scareware off Your Network" but parts of this report can help home and small-office users avoid the threat, too.
I'm talking about fake security software which pretends to find dangerous security threats—such as viruses—on your computer. The initial "scan" is free but if you want to clean up the fraudulent reported "threats", you'll need to pay. I have observed "scanners" as they locate threats in the C:\WINDOWS directory of a computer. In one case, the computer was a Mac. Macs don't have a WINDOWS directory. They also don't refer to disk drives by a letter designation.
Sophos explains why the fake antivirus scam is so popular among cybercriminals: "It is a huge revenue source. Compared to other classes of malware such as bots, backdoor Trojans, downloaders, and password stealers, fake antivirus draws the victim into handing money over directly to the malware author. Victims typically pay around $120 via credit card to pay for the junk software that will supposedly fix the problem."
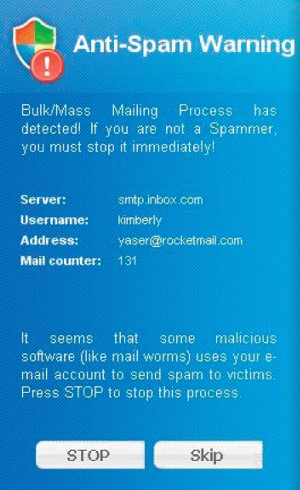 Here's the kind of warning you might see. This attack is designed to look like the AVG Antivirus program. The warning says that a mass mailing process has been detected and "If you are not a Spammer, you must stop it immediately!" The absurdity of that statement should be obvious to even the most casual user of computers. But if you press STOP (and possibly even if you press SKIP) the malware will be activated.
Here's the kind of warning you might see. This attack is designed to look like the AVG Antivirus program. The warning says that a mass mailing process has been detected and "If you are not a Spammer, you must stop it immediately!" The absurdity of that statement should be obvious to even the most casual user of computers. But if you press STOP (and possibly even if you press SKIP) the malware will be activated.
Given the recent security problems with Apple's operating systems, this note from Sophos is particularly compelling: "Macs are now a major target, including Mac-targeted social engineering being used as bait to the malware. We have been carefully tracking the developments in the Mac OS X malware community, and have concluded that fake antivirus for Macs is advancing fast and taking many cues from the Windows malware scene." So it's less likely that the bad guys will continue to display "scans" of "C:\WINDOWS\" on Mac computers.
The infection vectors are many and varied but most share a common thread: social engineering. The Sophos report says that the user is tricked into running the fake antivirus installer executable in a way similar to many other types of Trojans. Fake antivirus authors have used a huge range of different social engineering tricks and are continuing to come up with new ones all the time.
 Search results are among the most common vectors. The malware distributors create pages that respond to common search terms and deliver victims to infected sites. The rogue page performs a fake "scan" and reports infections.
Search results are among the most common vectors. The malware distributors create pages that respond to common search terms and deliver victims to infected sites. The rogue page performs a fake "scan" and reports infections.
But e-mail is also a common vector for infections.
Sophos says that a fake antivirus is often sent directly to the victim as an attachment or as a link in a spam message. The message is predominantly sent through e-mail, but other forms of spam have also been observed to deliver fake antivirus, such as instant messaging applications including Google Talk. The spam message itself usually uses social engineering techniques to trick users into running the attached file or clicking on the link.
- Account suspension scams: Victims receive an e-mail message suggesting access to a specific account has been terminated and they need to run the attached file to fix the issue.
- Ecard scams: An e-mail is received purporting to be from a legitimate ecard company. In fact, a fake antivirus installer is attached.
- Password reset scams: Victims receive a message supposedly from a popular website, informing them that their password has been reset and the new one is in the attached file.
- Package delivery scams: Details of a (fictitious) recent postal delivery are included in an attached file. In reality, the attachment will install fake antivirus.
You've probably seen all of these from time to time.
One of the more insidious threats comes from legitimate websites that have been compromised by having malicious code injected into a page. Fraudsters do this by breaking in to the target website’s hosting server and appending code (usually Javascript) to HTML pages. The code can be used to send the browser to any type of malware hosting page including exploit kits and fake antivirus. The code is almost always heavily obfuscated.
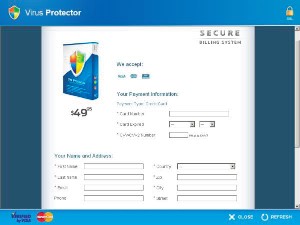 All of these threats have a common outcome. Users are told they must register or activate the (fake) product in order to clean up the threats. They are taken to a registration website where they are asked to enter their credit card number and other registration details. These pages are convincing and occasionally include logos and trademarks from industry-recognized organizations.
All of these threats have a common outcome. Users are told they must register or activate the (fake) product in order to clean up the threats. They are taken to a registration website where they are asked to enter their credit card number and other registration details. These pages are convincing and occasionally include logos and trademarks from industry-recognized organizations.
How Can You Protect Yourself and Your Computers?
Although the Sophos report is directed primarily at corporate IT managers, it also offers suggestions that can be used by individuals, families, and small offices. There are 5 primary steps: Reduce the attack surface, protect everywhere, stop the attack, keep people working, and educate users. For home and small office users, that last step is probably the most important.
Users should know not to click on anything suspicious and they should be reminded that the IT department (or, for home and small office users, the installed antimalware application) takes care of antivirus protection for their computers. If they are concerned about antivirus, or have strange messages popping up, they should contact IT (or, for home users, the most knowledgeable user—the one who installed the antimalware applications) and not try to sort it out for themselves. This goes back to one of the opening points: Be part of the solution and not parts of the problem. Users should at least know to refuse any anti-malware software that offers a free scan but requires a payment for cleanup. No reputable brand does this.
Breaking Adobe Acrobat File Restrictions
Adobe Acrobat files can be protected in a way that makes it impossible to print them, edit them, or extract text from them or so Adobe claims. In fact, the password protection is weak and can easily be circumvented. Why would you want to do this? Well, it's possible that the file you have contains text that you would like to use, with appropriate attribution, in a report or on a website. You can display the file on screen and manually copy the text, of course, but what if you have a legitimate need to obtain all of the text in a single locked file or snippets of text from dozens of locked files?
The solution is A-PDF Restrictions Remover. It's not password recovery utility because you don't need to recover the password. All you really want to do is remove the document restrictions so that the text inside the file is accessible.
A-PDF offers several applications that work with PDF files. Some are free. Others are reasonably priced. Restrictions Remover, for example, costs just $10.
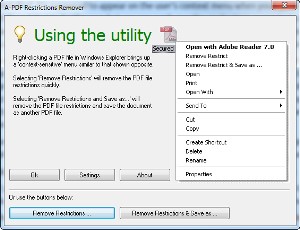 Once installed, it's supposed to appear on the computer's context menu when you right click a PDF document in the Windows Explorer. I haven't found that to be the case but you can easily run the application, navigate to the PDF document you need to extract next from, and then have Restrictions Remover remove the restrictions. The process takes just a few seconds and the result will be a PDF that offers accessible text and a backup version of the file with the restrictions still in place.
Once installed, it's supposed to appear on the computer's context menu when you right click a PDF document in the Windows Explorer. I haven't found that to be the case but you can easily run the application, navigate to the PDF document you need to extract next from, and then have Restrictions Remover remove the restrictions. The process takes just a few seconds and the result will be a PDF that offers accessible text and a backup version of the file with the restrictions still in place.
The built-in encryption method provided by Adobe gives a PDF the potential to have 2 passwords, master and user. The master password is required to make changes to any of the functions controlled by the user password. The user password controls whether anyone but the owner can copy, modify, print, or annotate the document.
A document is encrypted whenever a user or owner password or restrictions are supplied for the document. However, a user is prompted for a password on opening a document only if the document has a user password. None of this should be confused with the option to activate Reader rights, which make it possible for users of Adobe Reader to fill in form fields and perform certain other functions.
The application comes with a 15-day free trial during which it operates as nag-ware.
A-PDF publishes something like 80 utility applications that convert PDF documents to other formats or convert files created in various programs to PDF. The applications range in price from less than $10 to around $80.
If you have a locked PDF document that you need to unlock, take a look at the A-PDF Restrictions Remover.
Short Circuits
Microsoft Is Frightening Apple! (Really?)
Mercury News reporter Richard Saintvilus wrote about the tech triangle of Microsoft, Apple, and Google this week. Spurred, no doubt, by the announcement this week that Microsoft will invest $300 million in Barnes and Noble, the article is a worthwhile read.
The $300 million Microsoft investment gives Barnes and Noble some breathing room just as a similar Microsoft investment allowed Apple to remain afloat in the late 1990s. And just as with the Apple deal, Microsoft gets something out of this generosity, too. Later this year Microsoft will ship the new Windows 8 operating system which runs on devices ranging from servers to phones. And tablets. Microsoft would like to have content for those tablet devices and that's where Barnes and Noble figures into the deal.
But the Barnes and Noble reader, the Nook, runs on Google's Android operating system now. It seems reasonable to expect that Microsoft will apply a certain amount of pressure to wean the Nook away from Android and toward Windows 8.
So how does Microsoft frighten Apple at a time which Microsoft's share of the marketplace is dwindling and Apple's is rising?
Saintvilus suggests that Apple's quick response to the announcement of Windows 8 by pushing quickly to release OS X Mountain Lion is a sign of Apple's concern. "To me," he writes, "it was a swift jab to the chin of Microsoft to remind investors and analysts to whom the mobile power truly belongs -- regardless of how revolutionary Windows 8 is expected to be."
And now Saintvilus says he wonders if Apple sees Windows 8 as a potential game changer, something that "Microsoft has been searching for since Windows 95."
Regardless of how successful (or not) Windows tablets and phones are, "Microsoft is certain to leverage its existing enterprise footprint by virtue of its lead in the software and server markets for both consumers as well as corporate environments." A new version of Office is also in development.
The full report is well worth the few minutes required to read it.
Google Under Siege?
Google's managers could be forgiven for thinking that they're under siege. It's beginning to appear much more likely that the Federal Trade Commission will take Google to court, much as the same agency filed suit against Microsoft some 15 years ago and the company's "don't be evil" motto probably won't serve as a get-out-of-jail card. A case can be made for saying that Microsoft became a better company as a result of the suit. Might Google become a better company if it's forced to play by other people's rules?
The core question is whether Google has abused its power to gain market share and other advantages.
This week the Department of Justice hired Beth A. Wilkinson, a former Justice Department prosecutor, to work on the case. The DOJ rarely hires outsiders, having done so only twice in the past 10 years and Wilkinson is a very high profile prosecutor. Earlier she had a key part in the trial that convicted Timothy McVeigh, the domestic terrorist who bombed the federal building in Oklahoma City.
This comes at a particularly bad time for Google. The European Commission has been investigating the company for the past 2 years and will soon make a decision on whether to file suit. Defending itself against two antitrust suits on two continents could stretch even Google's substantial legal resources thin.
The scope of the investigations by the European Commission and the FTC are similar. Even so, the tougher fight might be in Europe because the courts take a much stronger position against antitrust violations that US courts do. Additionally, the EU can impose some sanctions without a trial.
Although Google commands about 70% of the search market in the United States, its dominance exceeds 90% in some parts of Europe. Antitrust investigators say that Google gives its own services unfair advantages when users conduct searches. Specifically, if any Google entity offers the product or service being sought, links to those Google services typically appear at the top of the results list.
The DOJ case against Microsoft curbed the company's power and allowed startups to compete in the marketplace. One of those startups was a little company that decided to call itself "Google".
How Many Phone Numbers Do You Have?
I've used Skype for several years to record interviews but recently I got a little more serious about using the service. Sometimes it's helpful for a technology journalist to have a New York City number. There's little chance that you'll be able to con anyone into giving you a 212 phone number but I was able to snag a 718 area code number. This area code is primarily for phones in Brooklyn, Queens, Staten Island, the Bronx, and the Marble Hill section of Manhattan. Many Manhattan cell phones also use the 718 area code so the number I have registered with Skype places me squarely in the New York City area.
Marble Hill is the furthest north section of Manhattan, further north even than Washington Heights. Ah, well, actually it's part of Manhattan politically but physically it's not part of Manhattan Island. So technically it's part of the Bronx because of the rerouting of the Harlem River in 1895. Well, close enough.
How many phone numbers do you have? I have an office number. There's the home number. I also have two Google Voice numbers, one in central Ohio that forwards to my cell phone and a second in Houston because I could use it to spell TechByter.
I can use one of the Google Voice numbers to make free outbound calls to any number in the US or Canada. The Skype number costs $60 per year and inbound calls are free. Outbound calls to cell phones and landlines in the US and Canada cost less than 3 cents per minute (plus a "connection fee" that's around 5 cents.) International calls range from a few cents per minute to several dollars per minute. The advantage to using the Skype number for interviews is that I can create a recording that places me on one stereo channel and the person I'm interviewing on the other stereo channel and when I mix that down for the podcast I can closely match the channels.
In the late 1950s I spent quite a bit of time trying to see how far I could call for free. The directory provided by the telephone company showed codes needed to call nearby towns for free so I called one of those towns, obtained a new dial tone, and then used the codes provided to residents of that town to obtain a dial tone in another town. I think that I made it half way from Bellefontaine to Columbus before something went wrong or the system got wise to what I was trying to do.
In some ways I pre-dated Cap'n Crunch (John Thomas Draper) who discovered that the whistles included in a box of Captain Crunch cereal could be used to fool the phone company into providing free long-distance access.
Today—who cares! If I don't need to record the conversation, Google Voice provides free long-distance calls and, if I do need to record the call, I can use Skype for less than $2 per hour. Google Voice does allow recording but Skypes functionality and quality are better.
Note This: Noteworthy Notes of Notable Note
 ADOBE CAMERA RAW: Adobe released Camera Raw 6.7 this week. Camera Raw is a plug-in for various Adobe products. It offers fast and easy access to raw image formats produced by digital cameras. The new version adds support for 9 new cameras including Pentax K-01 and Olympus OM-D E-M5. It also adds more than 30 lens profiles to help photographers automatically correct unwanted distortion and chromatic aberration.
ADOBE CAMERA RAW: Adobe released Camera Raw 6.7 this week. Camera Raw is a plug-in for various Adobe products. It offers fast and easy access to raw image formats produced by digital cameras. The new version adds support for 9 new cameras including Pentax K-01 and Olympus OM-D E-M5. It also adds more than 30 lens profiles to help photographers automatically correct unwanted distortion and chromatic aberration.
You might be wondering whether you need the new version (it's free) because the previous version already supported your camera's raw format. The answer to that question is Yes! Each new version of Camera Raw adds support for cameras you probably don't own but each new version also includes improvements over the version you have and Camera Raw can be used even with JPG images to recover detail.
The Camera Raw 6.7 plug-in is available as a free download. For more information and to download the updates, visit the Adobe updates site. Camera Raw is available for both Mac and Windows.
At the time I wrote this article, Camera Raw 6.7 wasn't yet available at the address shown above. If you follow that link and still can't find it, try one of these:
Windows: http://www.adobe.com/support/downloads/detail.jsp?ftpID=5371
Mac: http://www.adobe.com/support/downloads/detail.jsp?ftpID=5374
WI-FI UNDERGROUND: New York City's subway stations will have Wi-Fi access points operated by Boingo within the next 5 years.
The subway serves 4.3 million riders every day and many of those people undoubtedly have Wi-Fi-capable devices that are currently useless once they enter an underground station and most of the stations in Manhattan, Brooklyn, Queens, and the Bronx are underground. Note, though, that I said the stations will have Wi-Fi. So once passengers are aboard trains and the trains leave the station, service will be unavailable. The system has 277 stations and Wf-Fi is currently operational in 5 stations along 14th Street.
WHY MAC MALWARE WILL EXPAND: If you're a Mac user and you're still running a naked computer, you may want to rethink that decision. Apple is far behind Microsoft when it comes to fighting malware, primarily because Macs haven't needed much protection until now. Until now.
That Flashback attack last month reportedly handed the creators of the malware something like $10,000 per day. Here's the word from Symantec: "Ad-clicking Trojans are nothing new and in an analysis of W32.Xpaj.B last August a botnet measuring in the region of 25,000 infections could generate the author up to $450 per day. Considering the Flashback Trojan measures in the hundreds of thousands, this figure could sharply rise to the order of $10,000 per day."
If you're still in denial about the security of your Mac, it's time to get over it.
The consensus among security experts is that when Apple's market share hits 15% or thereabouts the Mac will be a viable candidate for various attacks. Apple now has about 12% of the market and few Macs have antimalware applications installed. Although Windows still has most of the desktop market, about 95% of Windows computers have antimalware software installed.
Where's the coming threat? Do the math.
HOW DO ANGRY BIRDS SURVIVE IN SPACE? Very well, apparently. The latest iteration of the Angry Birds franchise, which I've found to be distressingly addictive, hit 50 million downloads in a little over a month. Thirty-five days, specifically, so I guess I'm not the only one addicted to this nonsensical game.
I like to tell myself that I'm learning something about trajectories and gravity and science when I'm sling-shotting birds from planet to planet. Angry Birds in Space features "zero-gravity" scenarios. The game has levels that include floating rocks, planets, birds with new powers, and gravity fields that can change.
If you have an Iphone, an Android tablet or phone, or an Ipad, there's an Angry Birds version for it. A Windows phone version is in development.
AMAZON.COM: ABOVE AND BEYOND. I was listening to the Blues Brothers in early May and in one of the tracks Dan Ackroyd (as Elwood J. Blues) talks about the demise of the Blues, particularly the Chicago Blues. I've heard this track many times but this time it caused me to go off in search of some Chicago Blues tracks to add to my collection. The purchase reminded me of why I continue to buy from Amazon.com.
I found Chicago Blues, an MP3 download, for $16.98. My Amazon Visa card had about $50 worth of credits so I decided to use those for the purchase. There was, however, no option to apply the credits at checkout. So I made the purchase anyway and wrote to Amazon support asking why I couldn't use the credits.
The next morning I received an apology that started with the explanation I had requested: "At this time, we don't accept rewards points as a payment method for MP3 downloads."
If that's all I had received, I would have been satisfied but the writer went on: "To remedy the situation, I've requested a refund of $16.98 for the purchase." The message continued with what appears to be boilerplate text such as "I realize that no refund can really make amends for the disappointment caused" and "I am truly sorry that we were not able to fulfill your expectations for this level of service. I hope that you will honor us with another opportunity to prove the quality of our service to you."
But Amazon is a large company and I am a small (although fairly regular) buyer. Amazon didn't have to do more than just answer my question but by providing both an explanation and a refund they further cemented the relationship.
I think there's a lesson in there somewhere for marketers.



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
