Security: Looking for Vulnerabilities
This week, I have the second part of a 3-part series on security. Software publishers regularly release updates that patch security flaws. The problem is knowing when these patches have been released. Microsoft does a good job of patching its own applications via the Windows Update service and other publishers such as Adobe routinely have their applications check for updates. But what about your other applications? That's where a free application from Secunia can help.
Secunia is a Danish company that was founded in 2002. The company offers fee-based security applications for companies, but also offers a Personal Software Inspector either as a download that you can install or as an online service. Unlike Microsoft's Baseline Security Analyzer, Secunia's Personal Software Inspector examines software from all publishers and offers advice on how to secure your computer.
Installing, Analyzing, and Repairing
I found the Secunia Personal Software Inspector to be easy to use and accurate. As with any such application, it's important to avoid blindly accepting the application's suggestions, but hold that thought for a moment.
After installing the application, I asked it to scan the computer.
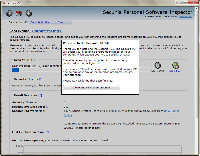 I started the scan using the "simple" interface and I'll show you the "advanced" interface later. If you feel comfortable with the advanced interface, you'll find that PSI gives you more information and more options.
I started the scan using the "simple" interface and I'll show you the "advanced" interface later. If you feel comfortable with the advanced interface, you'll find that PSI gives you more information and more options.
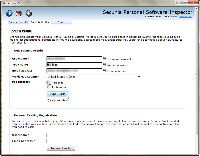 PSI asks you to create a profile. This is optional, but it's useful if you use the application on more than one computer.
PSI asks you to create a profile. This is optional, but it's useful if you use the application on more than one computer.
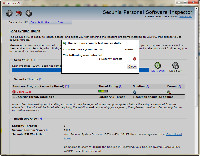 The initial scan completed and found just one security problem. It seems that Opera had issued an update that I hadn't yet downloaded.
The initial scan completed and found just one security problem. It seems that Opera had issued an update that I hadn't yet downloaded.
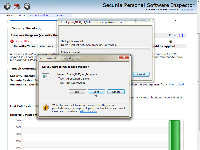 Secunia PSI offered a link directly from the scanner to Opera's website so that I could download and install the patch.
Secunia PSI offered a link directly from the scanner to Opera's website so that I could download and install the patch.
It doesn't get much easier than this.
From this point forward you'll see the advanced interface. It provides far more information, but that additional information requires a certain amount of analysis. If too much information makes you nervous, stick with the basic interface.
Fear and Loathing in Worthington
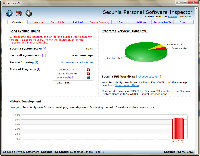 This screen startled me. 18 insecure browsers? I don't have that many installed. 44 insecure applications? 37 end-of-life applications?
This screen startled me. 18 insecure browsers? I don't have that many installed. 44 insecure applications? 37 end-of-life applications?
I had recently upgraded the computer, installed a new operating system, and reinstalled all the applications. Why were there so many end-of-life applications?
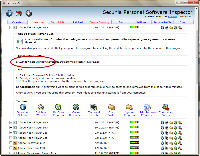 One bit of good news came from examining some of the applications that Secunia PSI called out. Although the scan is surprisingly fast, it's also deep. It had found the windows.old directory on drive E, an artifact of last year's upgrade from Windows XP to Windows 7. Nothing in that directory is used. I had kept it in case I needed some of the files, but I haven't needed anything since September 5, 2009, when the directory was created. Time to get rid of it.
One bit of good news came from examining some of the applications that Secunia PSI called out. Although the scan is surprisingly fast, it's also deep. It had found the windows.old directory on drive E, an artifact of last year's upgrade from Windows XP to Windows 7. Nothing in that directory is used. I had kept it in case I needed some of the files, but I haven't needed anything since September 5, 2009, when the directory was created. Time to get rid of it.
 So I told Windows to delete the directory.
So I told Windows to delete the directory.
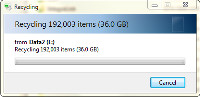 The 192,003 items (36GB) turned out to be too much for the Recycle Bin (d'oh!), so I had to give Windows permission to remove the files without sending them to the Recycle Bin.
The 192,003 items (36GB) turned out to be too much for the Recycle Bin (d'oh!), so I had to give Windows permission to remove the files without sending them to the Recycle Bin.
 And because this is an old Windows directory, it contains a lot of system files. These would have been 32-bit system files that will never be needed on a 64-bit system. It's OK to delete them and that's what I told Windows to do.
And because this is an old Windows directory, it contains a lot of system files. These would have been 32-bit system files that will never be needed on a 64-bit system. It's OK to delete them and that's what I told Windows to do.
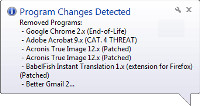 As the deletions continued, Secunia PSI reported that it had detected changes.
As the deletions continued, Secunia PSI reported that it had detected changes.
 Thinking that I had things under control, I asked PSI for another system scan. This took less than 10 minutes despite the fact that this computer has 3.5 TB of attached storage.
Thinking that I had things under control, I asked PSI for another system scan. This took less than 10 minutes despite the fact that this computer has 3.5 TB of attached storage.
Important point: "Only" about 1 TB is actually in use.
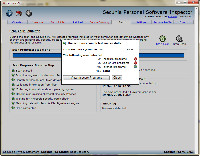 But I still had a lot of reported security problems.
But I still had a lot of reported security problems.
- 24 insecure programs.
- 33 end-of-life programs.
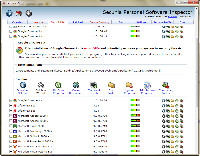 Further investigation revealed that some of the insecure files were on my USB hot backup drive. This drive contains old downloads that have been replaced by updated files.
Further investigation revealed that some of the insecure files were on my USB hot backup drive. This drive contains old downloads that have been replaced by updated files.
This is similar to the problem with windows.old, but I didn't want to delete the files on the hot backup device.
I didn't want bogus errors, either.
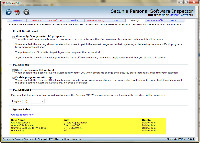 Secunia PSI allows users to specify directories that will not be examined. I have old applications (some go back to DOS days) stored on the computer. There's the hot backup drive and a few other locations exist that contain files that, although technically flawed, pose no danger to the system. I created rules to ignore them.
Secunia PSI allows users to specify directories that will not be examined. I have old applications (some go back to DOS days) stored on the computer. There's the hot backup drive and a few other locations exist that contain files that, although technically flawed, pose no danger to the system. I created rules to ignore them.
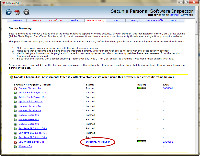 Then I took a break from the insecure programs and examined the browsers panel. All of my browsers were listed and all had some security problems.
Then I took a break from the insecure programs and examined the browsers panel. All of my browsers were listed and all had some security problems.
By "all", I mean Internet Explorer, FireFox, and Opera.
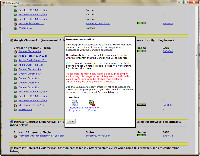 Some of the security problems have no solution. The VLC video player, which is used by all browsers, has a security problem with no current solution.
Some of the security problems have no solution. The VLC video player, which is used by all browsers, has a security problem with no current solution.
Reminder to me: Don't play the porn videos that pop up unannounced.
This is good information and here's the more general rule: When any site offers video, I need to think carefully about whether I trust the source. Eventually VideoLAN will resolve the problem, but for now it's my responsibility to be safe.
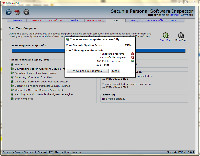 Now I'm down to 7 insecure programs and 1 end-of-life program. That's still too many.
Now I'm down to 7 insecure programs and 1 end-of-life program. That's still too many.
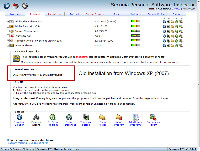 One of the insecure installations isn't really in use. It's a VMWare installation on drive D that was created in 2007 under Windows XP.
One of the insecure installations isn't really in use. It's a VMWare installation on drive D that was created in 2007 under Windows XP.
Solution: Delete the directory.
If I need VMWare, I can install the current version.
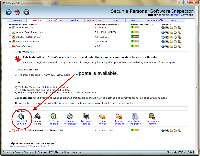 IrfanView had released a new version that corrected a security problem, but I had missed the update.
IrfanView had released a new version that corrected a security problem, but I had missed the update.
The link shown took me to the IrfanView website. I downloaded the update and installed it. Problem solved.
The Microsoft Powerpoint Player was reported as a problem and the link from PSI was to the Windows Update Service, which found that nothing needed to be updated. But the player was dated 2007 and I knew later versions had been released. To correct the failings of Microsoft's Windows Update Service, I tried a different approach:
- Download the PowerPoint Player.
- Install the PowerPoint Player.
- Run the Windows Update Service (which now freaks out and tells me that Very Bad Things will happen if I don't immediately update the PowerPoint Player.
- Allow Windows Update to update the PowerPoint Player.
- Problem solved.
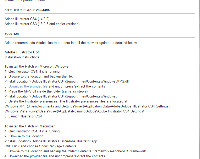 A problem with Adobe Illustrator turned out to be a bit of a challenge, too. Secunia PSI led me to a variety of Adobe updates I had missed, but the AI problem still wasn't resolved.
A problem with Adobe Illustrator turned out to be a bit of a challenge, too. Secunia PSI led me to a variety of Adobe updates I had missed, but the AI problem still wasn't resolved.
Instead, PSI took me to the Adobe website where the corrective process was detailed. I followed the instructions. Problem solved.
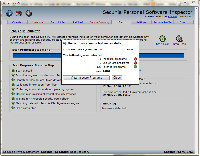 Now there's just 1 insecure program.
Now there's just 1 insecure program.
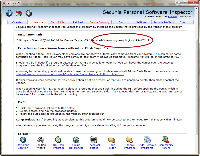 The insecure program is an old version of the Flash Player for Opera.
The insecure program is an old version of the Flash Player for Opera.
I could delete the Flash Player file in the Opera directory.
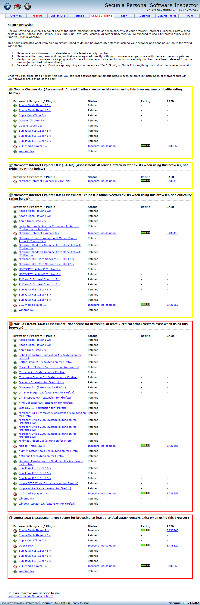 Here's another scary screen that shows the installed Web browsers with security problems.
Here's another scary screen that shows the installed Web browsers with security problems.
They're all present.
- Google Chrome
- Microsoft Internet Explorer
- Mozilla FireFox
- Opera
But the most serious problems have been resolved by patches. In fact, most of the problems go back go the VLC plug in.
Most. Not all. Browsers such as Microsoft Internet Explorer are inherently insecure and currently there is no solution.
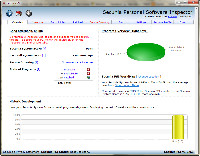 At the end of the day, I had a single problem and it's one that I understand and can live with.
At the end of the day, I had a single problem and it's one that I understand and can live with.
 Bottom Line: Secunia PSI tells you where your computer is vulnerable.
Bottom Line: Secunia PSI tells you where your computer is vulnerable.
Secunia PSI is the best application I've found for analyzing security problems before they bite. It's quick. It's easy to use. For personal use, it's free.
For more information, visit the Secunia website.
Firefox 3.6 Adds Security and Style
A new version of Firefox is out and you may already have been prompted to download it. Version 3.6 is slightly faster than 3.5, which was considerably faster than 3.0. New features have been added to improve security and to allow users to change Firefox's appearance. If you're already a Firefox user, you'll want this version. And if you're still using some other browser, you may want to take a look at Firefox.
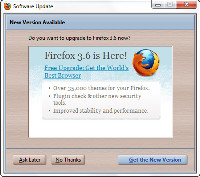 Current users will see a notice about the new version.
Current users will see a notice about the new version.
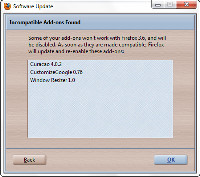 During the download process, you may be warned that some of your add-ons will no longer work under version 3.6. This is to be expected and most add-on developers update their offerings within a few days. Or you can use the Nightly Tester Tool to force compatibility.
During the download process, you may be warned that some of your add-ons will no longer work under version 3.6. This is to be expected and most add-on developers update their offerings within a few days. Or you can use the Nightly Tester Tool to force compatibility.
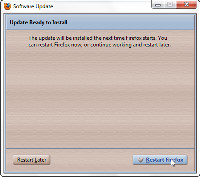 Following the installation, you need only restart Firefox to begin using the new version.
Following the installation, you need only restart Firefox to begin using the new version.
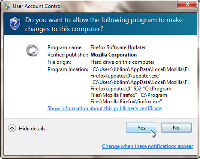 Vista and Windows 7 users may see a User Access Control message.
Vista and Windows 7 users may see a User Access Control message.
What's New? What's "Kewl"?
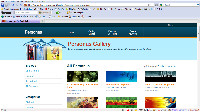 I'll start with one of the features that some people will consider silly: Personas. You can choose one of more than 30,000 appearances for the browser. Why? Because you can!
I'll start with one of the features that some people will consider silly: Personas. You can choose one of more than 30,000 appearances for the browser. Why? Because you can!
Well, also because you may spend a lot of time looking at a browser and you might as well have it look the way you want it to.
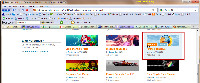 You're supposed to be able to hover your mouse cursor over one of the personas to see what it will look like on your browser, but this works only after you've installed at least one persona. Installation is as easy as selecting Wear It.
You're supposed to be able to hover your mouse cursor over one of the personas to see what it will look like on your browser, but this works only after you've installed at least one persona. Installation is as easy as selecting Wear It.
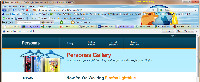 Now the browser has a new look.
Now the browser has a new look.
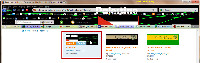 And when I hover the mouse cursor over another persona, the preview works.
And when I hover the mouse cursor over another persona, the preview works.
![]() With more than 30,000 personas to choose from, you're bound to find some that just don't work at all.
With more than 30,000 personas to choose from, you're bound to find some that just don't work at all.
Detecting Out-of-Date Plug-Ins
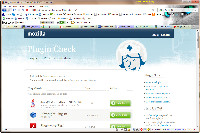 Plug-ins that aren't current can present a security problem and not all plug-ins warn when they're out of date. Old versions of plug-ins can cause crashes and other stability problems, too, so Firefox monitors plug-ins and warns when they're out of date. Mozilla even provides a site where you can obtain additional information.
Plug-ins that aren't current can present a security problem and not all plug-ins warn when they're out of date. Old versions of plug-ins can cause crashes and other stability problems, too, so Firefox monitors plug-ins and warns when they're out of date. Mozilla even provides a site where you can obtain additional information.
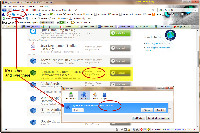 Unfortunately, it's not always accurate. I use LogMeIn and the detector couldn't find it. That's not a problem because LogMeIn checks each time it's launched to be sure that the plug-in is current. If not, you're encouraged to download it.
Unfortunately, it's not always accurate. I use LogMeIn and the detector couldn't find it. That's not a problem because LogMeIn checks each time it's launched to be sure that the plug-in is current. If not, you're encouraged to download it.
This failing makes me wonder what other plug-ins Firefox doesn't detect properly.
Other Features
- Video can now be displayed full screen and supports poster frames.
- JavaScript performance has been improved.
- New cascading style sheet attributes such as gradients, background sizing, and pointer events are now supported.
- Several functions of the new HTML5 document object model are supported.
Some of these functions are being put in place for the future. Until a lot of people have browsers that support the functions, few designers will use them.
The Typeface Race
The previous version of Firefox supported embedding TrueType and OpenType fonts. Version 3.6 includes support for the Web Open Font Format (WOFF) and this is the technology that may eventually allow designers to use more than the handful of typefaces that are reasonably safe across all browsers on all platforms.
WOFF faces are compressed, so they download faster than TT and OT faces. They also contain metadata about the source of the original type outlines, which makes it easier for designers to track down the source of a typeface they like. This is the first step in what will probably be a long process to make embedded typefaces a reality across many browsers on various operating systems.
But at least it's a start.
 Bottom Line: The Best Browser Continues to Improve.
Bottom Line: The Best Browser Continues to Improve.
I can't give Firefox 3.6 a 5-cat rating because of the incomplete plug-in detector. This will continue to be upgraded through the current development cycle. No other browser even comes close to offering the flexibility that Firefox does, though, and that's why it's the browser I use the most.
For more information, visit the Mozilla website.
The First Ten Dot-Coms
A couple of weeks ago the very first dot-com turned 25 years old. These days something like 100,000 domains are registered every day. Back then, it was 9 days until the second and third domains were registered; it was just a few days shy of a year before domain number 10 was registered. Do you remember who was there first?
It wasn't Microsoft or IBM. Some of the original registrants are no longer in business and the domain name redirects elsewhere. Here's a list of the first 10, a bit of history, and what they look like now.
 #1: Symbolics.com registered on 15-Mar-1985
#1: Symbolics.com registered on 15-Mar-1985
Once upon a time there was a computer manufacturer know as Symbolics. When Symbolics went out of business, another company purchased the assets (except for the domain name) and continued selling hardware. The domain name is now owned by XF.com as of 2009. Not much to see here. Move along, folks.
 #2: BBN.com registered on 24-Apr-1985
#2: BBN.com registered on 24-Apr-1985
Raymond Tomlinson is a programmer who implemented an e-mail system in 1971 on ARPANet and used the @ sign to separate the user from the machine. Then in 1967 he joined the technology company of Bolt, Beranek, and Newman, which became BBN Technologies and now appears to be owned by Raytheon.
 #3: Think.com registered on 24-May-1985
#3: Think.com registered on 24-May-1985
ThinkQuest Projects (formerly Think.com) is a project environment where teachers and students engage in collaborative learning.
 #4: MCC.com registered on 11-Jul-1985
#4: MCC.com registered on 11-Jul-1985
Microelectronics and Computer Technology Corporation (MCC) was at one time the largest computer industry research and development consortium. It was located in Austin, Texas. The organization, funded primarily by mainframe computer manufacturers, was disbanded in 2000. The website no longer exists.
 #5: DEC.com registered on 30-Sep-1985
#5: DEC.com registered on 30-Sep-1985
Digital Equipment Corporation was one of the larger manufacturers of minicomputers, devices that were smaller and less expensive than mainframes but larger and more powerful than desktop systems. A failing DEC allowed itself to be acquired by Compaq, which was then acquired by HP.
 #6: Northrop.com registered on 7-Nov-1985
#6: Northrop.com registered on 7-Nov-1985
Prior to 1994, Northrop Corporation was an aircraft manufacturer. The company was founded in 1939 and merged with the Grumman Corporation in 1994 to form Northrop Grumman.
 #7: Xerox.com registered on 9-Jan-1986
#7: Xerox.com registered on 9-Jan-1986
Xerox is, of course, still around. The company's Palo Alto Research Center was instrumental in developing desktop computers, notebook computers, the laser printer (which HP licensed), and much of the technology that runs the Internet.
 #8: SRI.com registered on 17-Jan-1986
#8: SRI.com registered on 17-Jan-1986
Originally the Stanford Research Institute, SRI International is a large contract research institute established by the Stanford University trustees in 1946. It was later spun off from the university and continues to operate as an independent non-profit organization in Menlo Park, California.
 #9: HP.com registered on 3-Mar-1986
#9: HP.com registered on 3-Mar-1986
Look familiar? William Hewlett and David Packard started a little electronics company in a Palo Alto garage not long after graduating with degrees in electrical engineering from Stanford University in 1939. HP built its reputation and its customer base by placing an extreme emphasis on quality.
 #10: Bellcore.com registered on 5-Mar-1986
#10: Bellcore.com registered on 5-Mar-1986
When the telephone company was the telephone company, Bell Communications Research, Inc. (Bellcore) was the research and development division. Now Telcordia Technologies, the company works mainly in network communications and telecommunications.
You might be wondering where Microsoft fits in the first 100. It doesn't. Microsoft thought that the Internet was nothing more than a passing fad.
It wasn't until more that two and a half years after Symbolics registered its domain name, near the end of November 1987, that the 100th dot-com domains had been established. Keep in mind that this was still several years before Tim Berners-Lee invented the technology that would power the Web in 1990. In those days, the Internet was e-mail, gopher, newsgroups, and telnet.
IBM was the 11th domain registered, followed a few days later by Sun; then Intel, Texas Instruments, and AT&T on the same day in March of 1986. Sometimes weeks passed between new registrations.
Short Circuits
It Only Seems Like Forever
In November of 1980, Micro-soft agreed to license a personal-computer operating system that it hadn't written and didn't own to IBM. IBM hadn't announced its personal computer yet; that would come in 1981. And before then Microsoft had to come up with the operating system it had sold. Bill Gates and company worked with a small software company in Seattle, offering them what seemed like a large cash price for a rewrite of an operating system patterned after Digital Research's CP/M operating system. What Microsoft neglected to mention to Seattle Computer was that it intended to license the software to IBM.
That's the operating system that became MS-DOS (when Microsoft sold it) and PC-DOS (when IBM sold it).
In 1985, Microsoft and IBM started work on what they called OS/2 an "advanced operating system", but Microsoft was already working on Windows and later dumped OS/2.
Along the way, the company changed its name to MicroSoft and then to Microsoft. Bill Gates became for a while the richest person in the world. The company spawned many millionaires.
In 1987, Microsoft purchased Forethought, a company that had developed Presenter for the Mac. Presenter became PowerPoint, one of the most important and most misused components of the Microsoft Office suite.
In another 35 years, the year will be 2045. My younger daughter will have paid off her house by then. Microsoft will be 70. Or will it? Given the challenges Microsoft faces, I wonder if it will still be around 35 years from now.
97 Percent Spam?
Some anti-spam organizations say that 97% of Internet e-mail is spam! Really? The answer is both yes and no. Certainly there's a lot of spam, but even if you're one of the people who receive a lot of spam, spam is probably not 97% of what you receive. So it's a lie? Well, no.
A lot of spam is never delivered. Spammers send messages to addresses that no longer exist and to addresses that never existed. I have one address that has never received even 1 spam so far. I use it only for banking communications, so only banks and financial institutions have it. They're pretty good about keeping e-mail addresses private. And it's an address that's not something anyone would guess. For one thing, the address is about 30 characters long and the characters (upper case, lower case, numbers, and symbols) were chosen at random.
That's a special address for a special purpose. For most of my day-to-day communications I use an address that's easy to guess and it receives a lot of spam. But still not 97%. It's all those messages to undeliverable addresses that push the overall percentages up. Those addresses never receive any legitimate messages, only spam. So that's where the huge number comes from.
But spam still costs a lot. It must be transported and stored. And this is 6 years after Bill Gates famously pronounced the end of spam by 2006. It could have happened. Maybe someday everyone who needs to cooperate to kill spam will cooperate. But I'm not holding my breath.
In the meantime, the creeps have been developing a new technique called "scareware". You receive a message that says your computer is infected and you must download something or visit a website to fix the problem. If you follow the instructions, you're rewarded by having an application that you don't want.
The application may be spyware that steals your information. Or it might cause programs to stop running and hold your computer hostage until you pay a ransom. No matter how legitimate a message appears to be, it's important to check it out before you do anything suggested.
If everyone ignored spam, the spammers wouldn't make money from it and the flood would stop. But I'm not holding my breath there, either.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
