Crimeware: Understanding New Attacks and Defenses
Viruses, worms, denial-of-service attacks, keyloggers, screen scrapers, rootkits, spam, phishing, pharming, identity theft, domain squatting, spyware — the list goes on and on. Nearly every week some new exploit, or a new twist on an old exploit seems to crop up. Keeping your information safe is a never ending task as new offenses are developed to keep up with each new defensive move. Crimeware: Understanding New Attacks and Defenses, a book by Markus Jakobsson and Zulfikar Ramzan, may frighten you, but it will also educate you.
The book starts by reminding us that computer attacks are no longer perpetrated by people who want to be able to boast about infecting millions of computers. Now the attacks are staged by criminals who are intent on extracting money or information without the victim being aware of the problem until too late.
I'll get my petty quibble out of the way at the outset: Although Jakobsson and Ramzan are the primary authors, sections of various chapters were contributed by more than 20 other writers. Making a cohesive whole when so many contributors are involved is difficult, but Symantec Press would have been well advised to employ a stern editor who would reign in some of excesses. (One writer apparently learned the word "taxonomy" recently and decided that it was necessary to use the word at least 16 times in 6 pages, including 3 times in one short paragraph. Yes, I did go back and perform a quick scan to count them!)
Despite the books minor shortcomings, it's a valuable addition to the bookshelf of anyone who's interested in a broad view of security challenges and examples of countermeasures that can be taken. For the more general reader, each chapter provides a high-level overview of a specific problem; the balance of the chapter deals with the problem in more detail for those who want the additional information.
Threats to Consider
Router Magic
If you connect to the Internet via a router, have you changed the default settings? By the author's estimation, half of all users don't bother to change the default channel, default SSID, or default encryption state (which is usually the weaker WEP that can be broken in 20 to 30 minutes of concerted effort.) Additionally, the author claims that 60-70% of users don't even bother to change the default password.
Failing to take basic protective steps such as these create large security holes that open your network to threats that can allow data thieves access to your files.
Router manufacturers ship routers with common IP addresses (192.168.1.1 is nearly universal, but a few are set at 192.168.2.1). The SSID will usually be the name of the router manufacturer. The router will, by default, broadcast the SSID. And the administrator's user name and password for the router will almost always be "admin".
Simply knowing enough to change those settings can improve your security.
Tricking Victims with the Hosts File
The hosts file stores information about where to find a node on a computer network by mapping host names to IP addresses. When you type a URL into the address bar of your browser, the browser first checks to see if an entry exists in the local file. If an entry exists, that IP address is used; otherwise, the browser send a request to the domain name service server to ask for the IP address.
- Most versions of Windows (WinNT, Win2K, WinXP, Win2003Server, Vista, and the upcoming Win7) use %SystemRoot%\system32\drivers\etc\ as the default location, but this may be changed by editing a Registry key (\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DataBasePath). Win9x and WinMe store the file in the Windows system directory.
- Linux and Unix systems (except the Mac) use the /etc directory.
- Although the Mac's OS X is based on BSD Unix, hosts is store in /private/etc/hosts; Mac System 9 and earlier operating systems use the System Folder: Preferences folder or the System folder. It's in /private/etc/hosts on the Iphone and Ipods.
 Click any of the images here for a full-size view.
Click any of the images here for a full-size view.
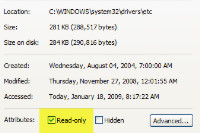
Depending on the operating system, the file may be marked as "read only", meaning that editing is not permitted. At least on Windows, changing this is trivial.
A man-in-the-middle attack could be established easily by corrupting a user's machine so that a domain such as "www.MyBank.com" (where "MyBank" is the victim's bank) would point to the attacker's IP address. When the victim types "www.MyBank.com" into the address bar, the hosts file directs the browser to the attacker's IP address. The attacker will have set up a site that looks a lot like the real bank's site. It will accept input from the victim, pass that information to the bank, and pass the bank's responses back to the victim. During the session, the attacker will capture all of the information sent by either the victim or the bank.
Here's a trivial example without the man-in-the-middle. This is designed only to show how the hosts file can be used to misdirect traffic.
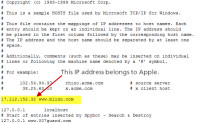
 I've located Apple's IP address (17.112.152.32), turned off the host file's read-only attribute on my computer, and opened the file in a plain text editor. The change is simple (left): "17.112.152.32 www.blinn.com" will cause any requests for blinn.com to be redirected silently to 17.112.152.32. (right, above)
I've located Apple's IP address (17.112.152.32), turned off the host file's read-only attribute on my computer, and opened the file in a plain text editor. The change is simple (left): "17.112.152.32 www.blinn.com" will cause any requests for blinn.com to be redirected silently to 17.112.152.32. (right, above)
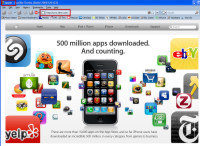 Note that even the URL doesn't change. As far as the browser knows, it's happily connected to blinn.com. The clear giveaways are that the title bar says "Apple" and the page content is obviously Apple's and not mine. But no browser-based warning popped up. The victim would have no clue that the site requested is not the one on the screen.
Note that even the URL doesn't change. As far as the browser knows, it's happily connected to blinn.com. The clear giveaways are that the title bar says "Apple" and the page content is obviously Apple's and not mine. But no browser-based warning popped up. The victim would have no clue that the site requested is not the one on the screen.
The Dangers of USB Devices
Security professionals don't like USB drives. I've mentioned that previously, but mainly in connection with data thefts perpetrated by insiders. A disgruntled employee with access to a company list of customers can easily load the list to a USB drive that can easily be hidden or that might not need to be hidden because it looks like a pen, and walk out with it.
But outsiders can use USB devices to attack a company. The book describes a situation in which data thieves dropped several USB drives in and around a corporation. Employees found them, took them back to their computers, and plugged them in. The USB drives had been loaded with auto-run malware that installed itself, collected data, and e-mailed that information to the thieves.
This threat could be mediated by turning off the Windows' auto-run function for all devices. This is a step I typically take when setting up a new computer because I rarely want a CD, DVD, or USB drive to run automatically. For those few times when I do want to run the device's default application, I can navigate to it in two or three clicks. Microsoft should have this feature turned off by default.
Crimeware covers a huge range of topics in its 550 pages. If you've ever wondered how the bad guys accomplish their deeds, this is an excellent starting point.
Listen to the Source
I had an opportunity to speak with authors Markus Jakobsson and Zulfikar Ramzan to duscuss their book that is, if not terrifying, at least sobering. The two authors are well positioned to know the subject. Jakobsson is principal scientist at the Xerox Palo Alto Research Center. His specialties include cryptographic protocols and human factors involved in security. Ramzan is a senior principal researcher at Symantec who specializes in understanding online fraud, phishing, and Web security. The audio segments in the podcast are the full versions of the interviews, which you can also listen to individually here:
- Zulfikar Ramzan of Symantec: LISTEN (12 minutes 46 seconds)
- Markus Jakobsson of the Xerox Palo Alto Research Center: LISTEN (12 minutes 35 seconds)
 Bottom Line: If you're unconcerned about Internet security now, you'll change your mind after reading Crimeware.
Bottom Line: If you're unconcerned about Internet security now, you'll change your mind after reading Crimeware.
This isn't exactly light or inexpensive reading. At $55 ($50 from InformIT Press), it's a significant investment, but the book is comprehensive in scope, current enough to allow readers to understand today's threats, and sufficiently general to provide a good basis for anticipating threats that haven't yet been developed.
For more information, visit the InformIT website.
I Think There's Something Sleeping ...
... in my refrigerator. I know that I should take a look, but I think I'll wait 'till later. Those words are, to the best of my memory, from a song by the Talon Brothers in the late 1960s. And so it is with computers. You might think there's something in there that shouldn't be, but you don't really want to look. Delay might only make things worse and some built-in Windows functions could help you determine if there's something inside the computer that needs your attention.
First rule: Never ever accept a pop-up offer to scan your computer. You may find these offers while you're browsing the Web. Just ignore the offer and leave the website. Quickly! If something like this pops up when you're not using a Web browser, and if it's not a warning from an antivirus program that you've installed, your computer is already infected with malware.
Here are some of the actions you can try track down the bad guys.
Windows Management Instrumentation Command-line
Most people don't even know the Windows Management Instrumentation Command-line exists, even if they're computer technicians. That's too bad because it's a most useful utility. To use it, make sure your user has admin access, then open a command window and type: "wmic". You'll see a message about the process being installed, then a wmic:root/cli> prompt. At the prompt, type: "process". Examine the list for processes that are running from odd locations, particularly if they have strange names.
If you use Windows XP Home, wmic is not available. This is one of many reasons that I recommended against saving a little money by selecting Windows XP Home instead of Windows XP Professional.
Also use: "process list brief" to see HandleCount, Name, Priority, ProcessId, ThreadCount, and WorkingSetSize, or "process list full" to see a much more complete summary for each process. Example:
CommandLine=C:\WINDOWS\system32\wbem\wmiprvse.exe
CSName=***REDACTED***
Description=wmiprvse.exe
ExecutablePath=C:\WINDOWS\system32\wbem\wmiprvse.exe
ExecutionState=
Handle=4584
HandleCount=142
InstallDate=
KernelModeTime=625000
MaximumWorkingSetSize=1413120
MinimumWorkingSetSize=204800
Name=wmiprvse.exe
OSName=Microsoft Windows XP Professional|C:\WINDOWS|\Device\Harddisk0\Partition1
OtherOperationCount=2184
OtherTransferCount=136992
PageFaults=1596
PageFileUsage=3264512
ParentProcessId=1384
PeakPageFileUsage=3268608
PeakVirtualSize=40677376
PeakWorkingSetSize=6340608
Priority=8
PrivatePageCount=3264512
ProcessId=4584
QuotaNonPagedPoolUsage=5136
QuotaPagedPoolUsage=74132
QuotaPeakNonPagedPoolUsage=5136
QuotaPeakPagedPoolUsage=74316
ReadOperationCount=14
ReadTransferCount=62298
SessionId=0
Status=
TerminationDate=
ThreadCount=6
UserModeTime=156250
VirtualSize=40677376
WindowsVersion=5.1.2600
WorkingSetSize=6340608
WriteOperationCount=12
WriteTransferCount=888
What you're seeing here is the full path of the executable associated with the process and its command-line invocation. Examine each process to determine whether it has a legitimate use. If you don't recognize a command (wmiprvse.exe, for example) ask Google: Windows Management Instrumentation (WMI) is a component of the operating system that provides management information and control in an enterprise environment....
Note: wmiprvsW.exe is the Sasser worm!
Next you might try "startup list full" to obtain a list of all applications and services that start when the machine starts. This will probably take a long time to run (minutes). Be patient. Every process will have an entry that looks like this, which tells you what the application calls itself, the command line that started it, how it was started (in this case, via the Registry), "SettingID" (I've never seen an entry here), and the user name (typically All Users or .DEFAULT):
Caption=COMODO Internet Security
Command="C:\Program Files\COMODO\COMODO Internet Security\cfp.exe" -h
Description=COMODO Internet Security
Location=HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SettingID=
User=All Users
When you're finished, type "exit" to return to the command prompt or just close the command window.
Current Ports
You may also want to download a copy of Current Ports from www.nirsoft.net and run it. Current Ports does not need to be installed. Just extract the executable file from the zip you download and run it. This will provide a huge amount of information about processes on your computer that are communicating either internally or externally. I wrote about it here if you want a more detailed explanation or to know what to expect from the display.
Netstat
Another helpful tool is netstat, a built-in command from Microsoft. Open a command window and type "netstat /?" for a list of switches you can use. As you'll see, it's essentially a command-line view of the information Current Ports provides. I offer this only if you don't want to download Current Ports, which I think is easier to use.
Open Files
To see what files are open, you'll need to activate an openfiles function. Open a command line window, type "openfiles /local on", and press Enter. You should see:
SUCCESS: The system global flag 'maintain objects list' is enabled.
This will take effect after the system is restarted.
Reboot the computer.
After restarting the computer, wait long enough for any malware to activate and phone home (15 minutes or more), then open a command window and type "openfiles /query /v". If you're on a network, you've enabled file sharing, and someone on the network has a file open, you'll see it reported here. Otherwise, this should be the display:
C:\Documents and Settings\Bill>openfiles /query /v
INFO: No shared open files found.
Files Opened Remotely via local share points:
INFO: No shared open files found.
If you see unusual or unexpected files, and particularly if the files are associated with local users who aren't logged on, there's a problem. You can leave this accounting function turned on, but if you want to turn it off, open a command window, type "openfiles /local off", and restart the computer.
The Windows Ultimate Boot Disc
I also recommend having a copy of the Windows Ultimate Boot Disc. You need to make this yourself, but you'll find instructions here. The UBCD can be quite helpful in the event of a problem because you can boot from the CD and use utilities on the CD to perform various security scan. This is helpful because it keeps malware from starting with the computer as it would do during a normal start-up. Think of it as a fire extinguisher.
Nerdly News
Marketing Brilliance or an Absurd Waste of Money?
My bet would be on the latter as Microsoft is once again copying Apple. Microsoft will soon open a chain of Microsoft Stores (compare, "Apple Stores"). There's one huge difference: Microsoft doesn't manufacture computers (Apple does) and Microsoft depends on 3rd-party manufacturers who buy the operating system to install on their computers (and who might decide that if Microsoft wants to compete at the retail level, Linux would be a better choice.)
Microsoft has hired David Porter to set up the chain of stores. This is somebody who should understand the challenges involved. He worked 25 years for Walmart, then became the head of worldwide product distribution at DreamWorks Animation. If anybody can make it work, this guy will.
Microsoft is looking for a "better sales experience" for their customers, which would seem to mean that they're not happy with the sales experience offered to customers by the existing retail stores. Microsoft's chief operating officer Kevin Turner said the company wants to improve "the articulation and demonstration of the Microsoft innovation and value proposition so that it's clear, simple and straightforward for consumers everywhere." Perhaps you've noticed that people who might otherwise say "we want to give our customers a better buying experience" will (when translated by the company's public relations folks) end up using words like "articulation" in a sentence that's twice as long as it needs to be to say what needs to be said. And it won't even be particularly clear, simple, or straightforward.
A year or two from now we'll know whether this was brilliant or somewhat less than brilliant.
For Mac Users, A New Version of Entourage
Microsoft has released the public beta of a modified version of Entourage. The release version is expected later this year. The changes are all below the surface and, unless you're using an Exchange Server to get your mail, non-existent. For this reason alone, most Microsoft Office 2008 users should not download the beta.
Users of the other two e-mail protocols, POP and IMAP, won't see any differences between the beta and the out-of-the-box Entourage 2008. Or at least they shouldn't. Microsoft hasn't made any changes there. All of the changes deal with converting from WebDAV to Exchange. In fact, Microsoft is cautioning that if you find any "issues" (that's Microsoft for "bugs") that relate to POP or IMAP, you might as well keep them to yourself. In the words of one Microsoft blogger, "This beta is all about Exchange, so anything else is going to go on our list of stuff to consider in the future...."
The other reason you shouldn't consider this for use on a production system is that it will change the structure of the database that holds messages, calendars, notes, and tasks. If you do install the beta, at least back up the database file first.
And if you're looking for one more reason not to install the public beta, it's because it's a beta. Betas are released so that the application can be used in a work environment that will reveal hidden bugs. If you like finding hidden bugs, beta applications are for you.
If not, just wait for the final version, which will be released later this year.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
