2009 Change: “We Leave Out the Jingles”?
I've been saying for several years that we're able to provide an hour's worth of technology news in about 20 minutes because we leave out the sports, the jingles, the weather, the news, and the commercials.
So you may be wondering what's with the jingles in the show now?
Well, they're not really jingles. The music is limited to the open, the close, and the "bridges" or "bumpers". For the open and close, the music adds about 20 seconds to the length of the program and the bridges are there simply to indicate a new article. Together, they add another 30 or 40 seconds to the entire show, but they clearly designate the point at which one segment has ended and another about to begin.
I consider the slight addition to the length to be worth the extra clarity, but I still leave out the sports (particularly the sports), the weather, the news, and the commercials. And I'll have more details for you about the changes on the February 1 program.
Don't Lose that Syncing Feeling
No, it's not a blues song from the '60s. Yes, it could be spelled "synching", too; each is acceptable. Now that we have the important topics out of the way, let's take a look at a free application that can keep a safety copy of your most important files in a different directory or on another hard drive. This doesn't take the place of backup, but it's helpful when something unfortunate happens to an important file. Instead of having to restore from a backup drive that may be stored elsewhere, you may be able to retrieve the last known good version of the file from your sync directory.
AllwaySync is free for personal use, but if you use it as much as I do, it will soon begin bugging you to license the "pro" version, which has no additional features, but it will then stop nagging you. Given the application's low cost ($20), it was easy enough to fork over the money. Click any of the images here for a full-size view.
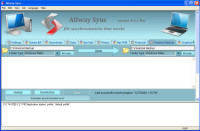 AllwaySync has an easy interface that allows you to define "left" and "right" folders. The folder on the left is the source folder and the folder on the right is the destination. In setting up the relationship, you tell AllwaySync what to do when files on either side are changed or deleted. Because I set up the application to be a safety net, I want changed files to be copied from left to right and deletions not to be mirrored on the right.
AllwaySync has an easy interface that allows you to define "left" and "right" folders. The folder on the left is the source folder and the folder on the right is the destination. In setting up the relationship, you tell AllwaySync what to do when files on either side are changed or deleted. Because I set up the application to be a safety net, I want changed files to be copied from left to right and deletions not to be mirrored on the right.
This means I can delete a file on the left, but it will still be available on the right.
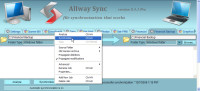 Each job becomes a tab on the interface and, in manual mode, right-clicking the tab offers the opportunity to analyze or synchronize the folders.
Each job becomes a tab on the interface and, in manual mode, right-clicking the tab offers the opportunity to analyze or synchronize the folders.
![]() As the synchronization process runs, AllwaySync logs every action it takes: Creating new directories on the right, copying files, and such. In the case shown above, AllwaySync found 24 new or changed files on the left and copied them to the right.
As the synchronization process runs, AllwaySync logs every action it takes: Creating new directories on the right, copying files, and such. In the case shown above, AllwaySync found 24 new or changed files on the left and copied them to the right.
You're not limited to just the drives that are attached to your computer. AllwaySync can back up files to a network folder, an FTP site, Amazon's Simple Storage Service, OffsiteBox.com, or a WebDAV folder. I don't recommend using AllwaySync instead of a full backup application, but if you don't have a true backup strategy in place, this would be a good start.
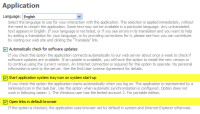 The real power comes from the ability to start AllwaySync when the computer starts (menu on the left) so that it can watch the directories you have defined.
The real power comes from the ability to start AllwaySync when the computer starts (menu on the left) so that it can watch the directories you have defined.
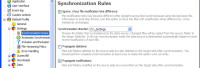 For each defined job, you set up specific rules for file synchronization. In nearly all cases, I simply copy new and changed files from left to right without mirroring deletions (right).
For each defined job, you set up specific rules for file synchronization. In nearly all cases, I simply copy new and changed files from left to right without mirroring deletions (right).
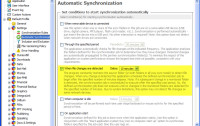
 The next setting determines whether AllwaySync monitors the directory and how long it will wait before starting to copy new and changed files to the right. To avoid constant disk activity, it's a good idea to set this to 10 minutes or more. 10 minutes is the default.
The next setting determines whether AllwaySync monitors the directory and how long it will wait before starting to copy new and changed files to the right. To avoid constant disk activity, it's a good idea to set this to 10 minutes or more. 10 minutes is the default.
You can also specify (above, right) which files and folders to include or exclude when performing the synchronization.
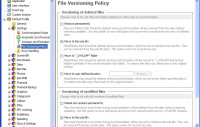
 You can also determine what should happen to files that will be deleted when new versions are copied. Currently, I have AllwaySync send the old versions to the Recycle Bin, but I might later choose one of the other options.
You can also determine what should happen to files that will be deleted when new versions are copied. Currently, I have AllwaySync send the old versions to the Recycle Bin, but I might later choose one of the other options.
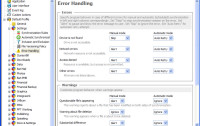
And finally, you're allowed to specify what the program should do if it encounters an error.
 Bottom Line: AllwaySync doesn't replace a real backup application, but it can speed recovery from the occasional "oops" moment.
Bottom Line: AllwaySync doesn't replace a real backup application, but it can speed recovery from the occasional "oops" moment.
Tell the application which files and directories you want to synchronize, where you want to store the copies, which files to include or exclude and you're ready. This fits my definition of easy.
For more information, visit the AllwaySync website.
What's Talking and to Whom?
You might be surprised to find out how much chattering your computer does, both internally and with Internet services. According to the utility CurrPorts, AVG Antivirus was maintaining 14 connections on various ports when I checked, Firefox had 6 connections, and Pidgin had 15. And then you might wonder what's happening on all those connections.
Here's a chart that shows all of the chattering processes, but not all of the information provided is present here because the actual chart is actually about 3 times as wide as this tiny-text version. If you'd like to see what's chattering on your machine, download a copy of the free CurrPorts application and run it. No installation is required, but you will need to unzip the file.
| Process Name | Process ID | Protocol | Local Port | Local Address | Remote Port | Remote Address | Remote Host Name | State | Product Name | Process Attributes |
|---|---|---|---|---|---|---|---|---|---|---|
| alg.exe | 3512 | TCP | 1035 | 127.0.0.1 | 0.0.0.0 | Listening | Microsoft® Windows® Operating System | A | ||
| AppleMobileDevice Service.exe | 516 | TCP | 27015 | 127.0.0.1 | 0.0.0.0 | Listening | Apple Mobile Device Service | A | ||
| avgemc.exe | 2872 | TCP | 10110 | 127.0.0.1 | 0.0.0.0 | Listening | AVG Internet Security | A | ||
| avgnsx.exe | 312 | TCP | 1959 | 127.0.0.1 | 0.0.0.0 | Listening | AVG Internet Security | A | ||
| avgnsx.exe | 312 | TCP | 1960 | 127.0.0.1 | 0.0.0.0 | Listening | AVG Internet Security | A | ||
| avgnsx.exe | 312 | TCP | 1961 | 127.0.0.1 | 0.0.0.0 | Listening | AVG Internet Security | A | ||
| avgnsx.exe | 312 | TCP | 1962 | 127.0.0.1 | 2558 | 127.0.0.1 | localhost | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 1962 | 127.0.0.1 | 2576 | 127.0.0.1 | localhost | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 1962 | 127.0.0.1 | 2957 | 127.0.0.1 | localhost | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 1962 | 127.0.0.1 | 2977 | 127.0.0.1 | localhost | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 1962 | 127.0.0.1 | 3623 | 127.0.0.1 | localhost | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 2559 | 192.168.1.2 | 5190 | 64.12.28.94 | Established | AVG Internet Security | A | |
| avgnsx.exe | 312 | TCP | 2578 | 192.168.1.2 | 5190 | 64.12.165.65 | oam-m01a.blue.aol.com | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 2959 | 192.168.1.2 | 5190 | 205.188.8.188 | Established | AVG Internet Security | A | |
| avgnsx.exe | 312 | TCP | 2978 | 192.168.1.2 | 5190 | 64.12.165.95 | oam-m01c.blue.aol.com | Established | AVG Internet Security | A |
| avgnsx.exe | 312 | TCP | 3624 | 192.168.1.2 | 5190 | 64.12.30.92 | Established | AVG Internet Security | A | |
| carboniteservice.exe | 1128 | TCP | 668 | 127.0.0.1 | 0.0.0.0 | Listening | Carbonite Secure Backup Engine | AR | ||
| carboniteservice.exe | 1128 | TCP | 668 | 127.0.0.1 | 2528 | 127.0.0.1 | localhost | Established | Carbonite Secure Backup Engine | AR |
| carboniteservice.exe | 1128 | TCP | 668 | 127.0.0.1 | 2930 | 127.0.0.1 | localhost | Established | Carbonite Secure Backup Engine | AR |
| carboniteservice.exe | 1128 | TCP | 2870 | 192.168.1.2 | 443 | 38.97.103.141 | Established | Carbonite Secure Backup Engine | AR | |
| CarboniteUI.exe | 5788 | TCP | 2528 | 127.0.0.1 | 668 | 127.0.0.1 | localhost | Established | Carbonite InfoCenter | AR |
| CarboniteUI.exe | 5788 | TCP | 2529 | 127.0.0.1 | 1959 | 127.0.0.1 | localhost | Close Wait | Carbonite InfoCenter | AR |
| CarboniteUI.exe | 5360 | TCP | 2930 | 127.0.0.1 | 668 | 127.0.0.1 | localhost | Established | Carbonite InfoCenter | AR |
| CarboniteUI.exe | 5360 | TCP | 2935 | 127.0.0.1 | 1959 | 127.0.0.1 | localhost | Close Wait | Carbonite InfoCenter | AR |
| firefox.exe | 2380 | TCP | 3395 | 127.0.0.1 | 3396 | 127.0.0.1 | localhost | Established | Firefox | A |
| firefox.exe | 2380 | TCP | 3396 | 127.0.0.1 | 3395 | 127.0.0.1 | localhost | Established | Firefox | A |
| firefox.exe | 2380 | TCP | 3397 | 127.0.0.1 | 3398 | 127.0.0.1 | localhost | Established | Firefox | A |
| firefox.exe | 2380 | TCP | 3398 | 127.0.0.1 | 3397 | 127.0.0.1 | localhost | Established | Firefox | A |
| firefox.exe | 2380 | TCP | 3809 | 192.168.1.2 | 443 | 74.125.95.18 | iw-in-f18.google.com | Established | Firefox | A |
| firefox.exe | 2380 | TCP | 3810 | 192.168.1.2 | 443 | 74.125.95.18 | iw-in-f18.google.com | Established | Firefox | A |
| LogMeIn.exe | 4608 | TCP | 2002 | 0.0.0.0 | 0.0.0.0 | Listening | LogMeIn | A | ||
| LogMeIn.exe | 4608 | TCP | 2002 | 127.0.0.1 | 2790 | 127.0.0.1 | localhost | Established | LogMeIn | A |
| LogMeIn.exe | 4608 | TCP | 2002 | 127.0.0.1 | 2933 | 127.0.0.1 | localhost | Established | LogMeIn | A |
| LogMeIn.exe | 4608 | TCP | 2787 | 192.168.1.2 | 443 | 64.94.18.193 | Established | LogMeIn | A | |
| LogMeInSystray.exe | 4632 | TCP | 2790 | 127.0.0.1 | 2002 | 127.0.0.1 | localhost | Established | LogMeIn | A |
| LogMeInSystray.exe | 4496 | TCP | 2933 | 127.0.0.1 | 2002 | 127.0.0.1 | localhost | Established | LogMeIn | A |
| lsass.exe | 1216 | UDP | 500 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| lsass.exe | 1216 | UDP | 4500 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| mDNSResponder.exe | 596 | TCP | 5354 | 127.0.0.1 | 0.0.0.0 | Listening | Bonjour | A | ||
| mDNSResponder.exe | 596 | UDP | 1025 | 0.0.0.0 | Bonjour | A | ||||
| mDNSResponder.exe | 596 | UDP | 57906 | 0.0.0.0 | Bonjour | A | ||||
| mDNSResponder.exe | 596 | UDP | 5353 | 192.168.1.2 | Bonjour | A | ||||
| pidgin.exe | 5484 | TCP | 2558 | 127.0.0.1 | 1962 | 127.0.0.1 | localhost | Established | Pidgin | A |
| pidgin.exe | 5484 | TCP | 2576 | 127.0.0.1 | 1962 | 127.0.0.1 | localhost | Established | Pidgin | A |
| pidgin.exe | 2200 | TCP | 2957 | 127.0.0.1 | 1962 | 127.0.0.1 | localhost | Established | Pidgin | A |
| pidgin.exe | 2200 | TCP | 2977 | 127.0.0.1 | 1962 | 127.0.0.1 | localhost | Established | Pidgin | A |
| pidgin.exe | 5484 | TCP | 3623 | 127.0.0.1 | 1962 | 127.0.0.1 | localhost | Established | Pidgin | A |
| pidgin.exe | 5484 | UDP | 2562 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 5484 | UDP | 2563 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 5484 | UDP | 2585 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 5484 | UDP | 2587 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 2200 | UDP | 2961 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 2200 | UDP | 2962 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 2200 | UDP | 2985 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 2200 | UDP | 2986 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 5484 | UDP | 3627 | 127.0.0.1 | Pidgin | A | ||||
| pidgin.exe | 5484 | UDP | 3628 | 127.0.0.1 | Pidgin | A | ||||
| svchost.exe | 1508 | TCP | 135 | 0.0.0.0 | 0.0.0.0 | Listening | Microsoft® Windows® Operating System | A | ||
| svchost.exe | 1828 | TCP | 2869 | 0.0.0.0 | 0.0.0.0 | Listening | Microsoft® Windows® Operating System | A | ||
| svchost.exe | 1716 | UDP | 1027 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 1159 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 1160 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 1161 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 1162 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 1163 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1716 | UDP | 2235 | 0.0.0.0 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1624 | UDP | 123 | 127.0.0.1 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1624 | UDP | 1050 | 127.0.0.1 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1828 | UDP | 1900 | 127.0.0.1 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1624 | UDP | 123 | 192.168.1.2 | Microsoft® Windows® Operating System | A | ||||
| svchost.exe | 1828 | UDP | 1900 | 192.168.1.2 | Microsoft® Windows® Operating System | A | ||||
| System | 4 | TCP | 445 | 0.0.0.0 | 0.0.0.0 | Listening | ||||
| System | 4 | TCP | 139 | 192.168.1.2 | 0.0.0.0 | Listening | ||||
| System | 4 | UDP | 445 | 0.0.0.0 | ||||||
| System | 4 | UDP | 137 | 192.168.1.2 | ||||||
| System | 4 | UDP | 138 | 192.168.1.2 | ||||||
| Unknown | 0 | TCP | 3747 | 192.168.1.2 | 443 | 74.125.95.18 | iw-in-f18.google.com | Time Wait |
What Does This Tell Us?
CurrPorts displays the list of all currently opened TCP/IP and UDP ports on your computer along with information about the process that opened the port: The process name, full path to the file, version information about the process, the time that the process was created, and the user that created it. This can be useful information if you suspect an intrusion from a program that's trying to contact its creator without your knowledge.
Click any of the images here for a full-size view.
 At the right is the full report provided by CurrPorts. Even if you view the full-size image (just click the image here to do that), you probably won't be able to read it because I've compressed the table horizontally to fit on a single screen.
At the right is the full report provided by CurrPorts. Even if you view the full-size image (just click the image here to do that), you probably won't be able to read it because I've compressed the table horizontally to fit on a single screen.
CurrPorts also allows you to close unwanted TCP connections, kill the process that opened the ports, and save the TCP/UDP ports information to HTML file, XML file, or to tab-delimited text file. If there are any suspicious applications, CurrPorts will color them pink.
The CurrPorts utility is uncommon among Windows applications in that it doesn't require any installation; just unzip the file, copy it to any folder you wish, add a shortcut to the start menu if you want one, and run it.
If that's just too much information and you don't want to view all available columns, or you want to change the order of the columns on the screen and in the files you save, select 'Choose Column' from the View menu, and select the desired columns and their order. In order to sort the list by specific column, click on the header of the desired column.
 Bottom Line: CurrPorts is a quick, easy, free way to find out what's chattering on your computer.
Bottom Line: CurrPorts is a quick, easy, free way to find out what's chattering on your computer.
CurrPorts is just one of several useful network utilities written by Nil Sofer. It's easy to install, easy to use, and free. Besides that, it does what it's supposed to do.
For more information, visit the NirSoft website.
Another Year, Another New Format
Every year starting in November, I put on my designer's cap and my graphic-design-professional daughter starts laughing. I doubt that I'll ever design anything as creative and compelling as she would, but I've managed to avoid creating too many designs that are unbearably ugly. So now that it's January, it's time to tell you about the new features and the new look.
This year, I had three goals in mind: Soften the appearance a bit, reduce clutter, and make the site more accessible to those who might need larger type or smaller type on the screen. These are the main changes:
- Fuzzy ("grunge") type for the banner. The faces used are called Malapropism, which visually seemed to represent the kind of sound that comes out of a megaphone, and Calamity Joe, which just seemed to fit the theme. The megaphone is a stock image from IStockPhoto that I cropped and rotated.
- The top-level menu is now on one line and the program date shares a line with information about the program's podcast to conserve vertical spacing.
- The headlines are lighter and smaller this year and level-one heads are on a light contrasting field to make the beginning of each article easier to find.
- If you have a browser that is capable of resizing a Web page (current versions of Microsoft Internet Explorer, Mozilla Firefox, Google Chrome, Opera, and probably others I haven't tested yet can do this), enlarging or reducing the page will scale both the text and the images.
- Last year, I removed tables (except when needed for tabular data, as you'll see in the account below) and I have continued that this year. Current browsers all handle cascading style sheets well enough to make this possible so that the site can now separate design from structure.
Scaling the Page
This is the primary change I've made this year and it's something that will help those who have uncommonly low resolution screens. Previously the site would not fit properly on any screen less than 1024 pixels wide. Granted, most people have screens at least that size now, but not everyone runs the browser full screen. And visitors who arrived with extremely high resolution screens would find a lot of white space around the page. Now you can scale the contents larger or smaller to meet your needs.
- Internet Explorer (Windows): To make the text larger, press Ctrl and the plus key. To make text smaller, press Ctrl and the minus key. To return to standard resolution, press Ctrl and the zero key. Text and graphics will both be resized.
- Mozilla Firefox (Windows, Mac, Linux): Same as Internet Explorer. Text and graphics will both be resized. (Cmd key instead of Ctrl on the Mac.)
- Google Chrome (Windows): Same as Internet Explorer. Text will be resized; graphics remain their default size.
- Opera (Windows, Mac, Linux): To make text larger, press the plus key. To make text smaller, press the minus key. To return to standard resolution, press Ctrl and the zero key. Text and graphics will both be resized. (Cmd key instead of Ctrl on the Mac.)
- Safari (Mac): To make the text larger, press Cmd and the plus key. To make text smaller, press Cmd and the minus key. To return to standard resolution, press Cmd and the zero key. Text only will be resized and resizing tabular data doesn't work properly.
TechByter's Graphical History
Click any of the images here for a full-size view.

 Although the program goes back to the early 1980s, the Web wasn't available then. The Web was invented in the early 1990s and the earliest files currently on the website are from 1998 (left).
Although the program goes back to the early 1980s, the Web wasn't available then. The Web was invented in the early 1990s and the earliest files currently on the website are from 1998 (left).
The design changed slightly in 1999 (right).
 Apparently I was afflicted by a severe lack of creativity between 2000 and the end of 2004 because the overall design remained nearly the same for the entire period (left).
Apparently I was afflicted by a severe lack of creativity between 2000 and the end of 2004 because the overall design remained nearly the same for the entire period (left).
With the advent of 2005, I created a new design that began to employ cascading style sheet technology. Still, the design was largely table based and the banner took up a lot of space for anyone who had a low-resolution screen.
 In 2006, after WTVN dumped Technology Corner, I changed the name, but kept the style that I'd developed at the beginning of the year. In 2006, I added the podcast feature (left).
In 2006, after WTVN dumped Technology Corner, I changed the name, but kept the style that I'd developed at the beginning of the year. In 2006, I added the podcast feature (left).
For 2007, I created what I came to think of as the TechByter hamburger (right).

 In 2008, I finally did away with tables as a design element. This makes the site much more accessible to anyone who uses a screen reader. And in 2009 I updated the cascading style sheet to make it more standards compliant.
In 2008, I finally did away with tables as a design element. This makes the site much more accessible to anyone who uses a screen reader. And in 2009 I updated the cascading style sheet to make it more standards compliant.
Over the years the screen width has grown from less than 800 pixels to 1000 pixels to keep pace with larger high-resolution screens. Giving users the ability to modify the size on their own makes the situation better for everyone.
Nerdly News
Surprise! Spam Levels Continue to be Depressed
In mid November last year, the upstream providers to a hosting operation called McColo shut off service and immediately cut Internet spam by about half. I had expected levels to bounce back within a week or two. It didn't and it still hasn't. This is definitely not a complaint.
McColo, thought to be run by a Russian gang of thieves, had negotiated a backup connection with Swedish ISP TeliaSonera. But the thieves were lazy. After getting the service back on-line within a couple of days, the dawdled in re-establishing their botnet operation. The TeliaSonera connection was shut down before McColo could fully recover. As a result, nearly two months later spam levels are still far lower than they've been for years.
Prior to mid November, I could expect to receive 4000 to 5000 spams per month. The rate fell below 1000 briefly and is now around 2000. Because of the way I've organized anti-spam measures, all but about 25 messages per month are discarded without little intervention by me.
Intel's Speedy New Processors are also Greener
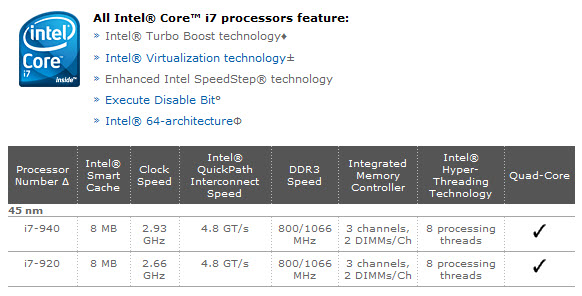 If you have $600 to $1000 to drop on a new CPU (just the CPU; you'll still need a main board, memory, a power supply, one or more hard drives, and a box to put everything in) you'll want to know about Intel's new line of processors. The I7 (or as Intel likes to style it, the "i7") processors bring new speed, even though most people don't need more speed, and other features that people do really need.
If you have $600 to $1000 to drop on a new CPU (just the CPU; you'll still need a main board, memory, a power supply, one or more hard drives, and a box to put everything in) you'll want to know about Intel's new line of processors. The I7 (or as Intel likes to style it, the "i7") processors bring new speed, even though most people don't need more speed, and other features that people do really need.
You don't need more speed? Right. You probably don't. Those who need more speed are "professional" gamers, video editors, photographers, and the like. These are people who use powerful applications that need enormous amounts of processing power, memory, and disk speed. If you're just surfing the Internet, writing books no larger than the average encyclopedia volume, and tinkering with the occasional photo, a fast new processor won't do much for you.
At first glance, you might think that these processors aren't a lot faster than some of the current processors. Speeds are "just" 2.93 and 2.66 GHz, but they handle 8 processing threads, come with 8 MB of cache, and have 3 Channels for DDR3 1066 MHz memory. That's FAST. Or as Intel says, "brilliantly fast".
The integrated memory controller, for example, yields a maximum of 25.6 GB/sec of memory bandwidth. This is exactly where memory-intensive applications such as photo manipulation applications need all the bandwidth they can get.
Faster usually means more power and hotter, but the I7 family is smart enough to use only what it needs. Instead of running everything full out all the time, it can turning on only what it needs at the moment. The result, particularly if you're running a room full of computers, is lower energy consumption and lower cooling costs.
So even the people who don't need all the speed will probably start paying attention to this new processor.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
