|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Previous page | Do you use a pop-up blocker? If so, please read this. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Show Date: 2007.08.26 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||
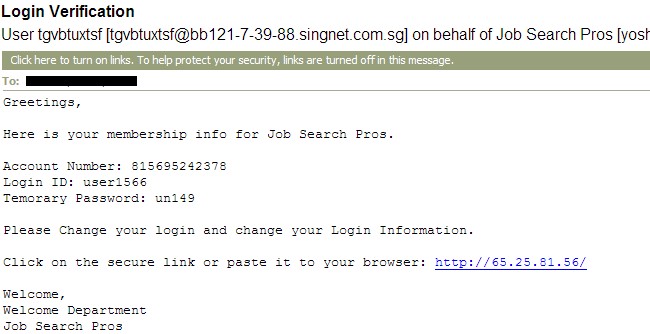
A valiant attempt by a spammerJust last week I started a new feature called Stupid Spam of the Week. This one doesn't fit there. The spammer who created this one deserves a prize: Something like 10 years in prison. The premise is so simple that one has to wonder why nobody did it before. The premise of the spam is that most people have subscribed to an on-line service before and have seen messages from the server with an explanation that they must do something to complete the registration. Like this, for example: It almost looks plausible. Login verification seems reasonable enough and the spam isn't asking for a user ID and password, but providing one. But the message claims to have come from Singapore. Not a good sign. And the URL is an IP address. That's the kiss of death as far as I'm concerned. No legitimate operator will send you to an IP address to confirm login information. Also notice that nowhere does it show your name and the login ID is generic. There isn't a decent system on the planet that assigns user IDs these days; you'll be asked to create your own. Did I sign up for anything like this? No. But if I was looking for a job and if I had signed up for any of the job-search operations, this could have been sufficiently plausible to earn a click. That's what makes it so dangerous. You might be wondering what happens if you go to the website. It appears that the site will do nothing but display a message that says If you do not see the Secure Login Window please install our Secure Login Applet. When you click that, two things will happen:
The huge variable may contain the payload or it may simply contain something to keep you busy while Applet.exe does what it needs to do.
The way to avoid being fooled by these tricks is to treat any message you receive with suspicion. If you didn't request something, don't click on a link. Converting a PDF to editable textAdobe's PDF (portable document format) files are ubiquitous. You'll find them on websites. You'll find them in offices. You'll find them used extensively in the printing industry, both for pre-press work and as files that are used to create plates that are used to print newspapers, magazines, brochures, and more. The primary shortcoming to a PDF document, if you don't have the full version of Adobe Acrobat, is that it's hard to extract the text. Sometimes you need to do that. Why? A company that supplies a product or service to your business may send a PDF that describes the product or service and you may want to use some of the text in one of your publications or on a website. If you could just copy the text or extract it into a word processor. But without the full version of Acrobat, how can you do that?
Short of perfection, but a workable toolIf you look at the innards of a PDF document, which is actually a Postscript file with a wrapper around it, you'll see that it's more than a little challenging to decrypt. In some cases, individual letters are placed according to coordinates, so extracting the text isn't easy. Postscript generally treats a line of text as a discrete unit, too. For example, here is some Postscript: That's the code required to generate this line: In short, Postscript isn't easy to convert to usable text. Neither application does it with 100% reliability, but Docudesk's UN-PDF is a cost-effective way to obtain text you can use in other applications. If you need to extract text from a PDF, consider UN-PDF
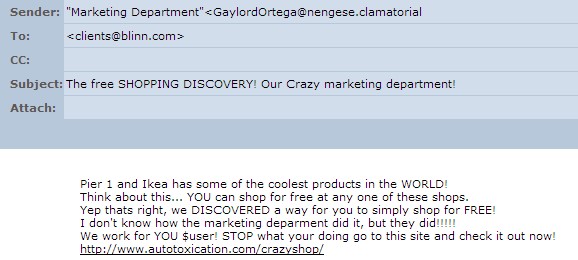
This is a good, solid, reliable application that's easy to use and does what it says it will do. If you extract text from a PDF with UN-PDF, you'll be left with some clean-up work. The needed clean-up work will take far less time than manually typing the text or scanning it and, if your typing is anything like mine, the results will be far more accurate. For more information, visit Docudesk's website. Stupid spam of the weekHere's the next in the series of stupid spams of the week. Despite being creeps, some spammers are relatively clever. "Stupid spam of the week" is designed to highlight the spammers who are a few cans short of a six-pack, a few clowns shy of a circus, a few clues short of an idea.
What's wrong with this one? Let me count the ways.
Nerdly NewsAttacking a monsterPersonal data belonging to hundreds of thousands (millions?) of users has been stolen from Monster.com. According to Symantec, user names, e-mail addresses, home addresses, and phone numbers were uploaded to a remote Web server. Symantec says phishing e-mails to Monster.com users are realistic looking because they contain personal information about the victims. The phishing e-mail encouraged users to download a "Job Seeker Tool". The tool turned out to be a program that encrypted files on the victim's computer and then left a ransom note that told users they would have to pay if they ever wanted to see their files again. Monster.com spokesman Patrick Manzo says it's "not a hack of Monster's security" but the misuse of "legitimate customer credentials". Manzo says it's not a case of identity theft because the information is similar to what can be found in a phone book. Iphone says "bye bye" to AT&TA New Jersey teen with a soldering iron has unlocked his Iphone so that it will work with carriers other than AT&T. By the time you read this, he will probably have heard from Ma Bell's attorneys. So far, neither Apple nor AT&T has any comment. The good news is that there is apparently no US law that prohibits unlocking cell phones. The Library of Congress in 2006 excluded cell-phone unlocking from coverage under the asinine Digital Millennium Copyright Act, which has been used to prosecute (some would say "persecute") people who modify game consoles to play a wider variety of games. George Hotz of Glen Rock, New Jersey posted information about the process on his blog late in the week. The hack isn't easy and requires both hardware and software modifications. A misstep with a soldering iron can destroy the phone. Hotz included a video on his blog that shows an Iphone working on the T-Mobile network. That's because only 2 US mobile networks use the technology built into the Iphone: AT&T and T-Mobile. Hotz says he hopes that someone will find a way to unlock the phone using only software. The Iphone is sold only in the US, but it can be made to work on European networks by copying information from the Subscriber Identity Module, a small card with a chip that identifies a subscriber to the cell-phone network. The Iphone's built-in camera and its ability to access WiFi networks is retained, but the "visual voicemail" feature is lost. Hotz says it took him about 500 hours to perfect his method. He put his hacked $500 Iphone on sale on Ebay and by week's end the high bid was above $3000. Not a bad summer's work. Hotz will be a student this fall at the Rochester Institute of Technology. Is Netflix the Blockbuster buster?Netflix and Blockbuster are engaged in a battle to the death. Both have cut prices and modified offerings recently, but Netflix seems, in my opinion, to have the edge. This week, Netflix founder and CEO Reed Hastings talked with the San Jose Mercury News and suggested that Netflix would win the battle. The full story is on the Mercury News website. Hastings is looking beyond physical delivery of discs. Netflix lost 55,000 subscribers so far this year and is now down to 6.74 million overall. Income and revenue are up. The Netflix Watch Now service that streams movies on demand shows where the company is going according to Hastings. Hastings admits that Blockbuster is better known and is larger (about 5 times larger) than Netflix, but "Our view is that the smart money is that they can't sustain the battle. . . . Last year they were $251 million of positive free cash flow, calendar year. The first six months year to date, they're negative $215 million. Big numbers and a big change." Netflix has been around for a decade and Hasting says that the future is Web-based television that will allow users to "watch all kinds of video content from all kinds of sources." He says Netflix recognized the opportunity early and was able to build a company before others realized what was happening. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Home • Programs • Reference • Subscribe to Technology Corner News • Contact Us • Terms of Use ©2007 by William Blinn Communications. All rights reserved. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||
This is the only ad you'll ever see on this site. It's for my website host, BlueHost in Orem, Utah. Over the past several years, they have proven to be honest, reliable, and progressive. If you need to host a website, please click the banner below to see what BlueHost has to offer. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||

|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||