Protecting Yourself from Identity Theft
Did you know that about 4% of all Americans will lose their identity to thieves in any given year? Or that the identity theft racket worldwide steals about $40 billion annually? And if your identity is stolen, even if your bank makes good on all of the fraudulent purchases, you'll spend more than $600 and 40 hours on the phone to recover your identity? These are the scary but realistic figures that describe the problem. As with most problems, avoidance is better than recovery.
I attended a program by ADP Chief Security Officer (CSO) Roland Cloutier and learned the distressing story about the rapid growth of this "industry". With a $40 billion annual haul, collectively the thieves are larger than many major corporations and even some countries. As the CSO of ADP, Cloutier has functional and operational responsibility for ADP’s cyber, information protection, risk, workforce protection, crisis management, and investigative security operations worldwide. In other words, he knows what he's talking about.
ADP is a gigantic company. As a provider of business outsourcing and human capital management solutions, it serves more than 620 thousand clients in more than 125 countries. Needless to say, security is a very big deal with ADP because of the kinds of data the company handles.

Cloutier calls on people to be "human firewalls" because no technology can protect us from everything. If you depend on an antimalware application to shield you from identity theft, you're well on the way to becoming a victim. Being a human firewall involves taking a bit of time to learn something about security. Think of it as a defensive driving class for computers. It also means being aware of your surroundings, much as you would be on an unfamiliar street. And it's important to maintain a certain amount of healthy paranoia and skepticism.
It's a Growth Area
Cybercrime is a fast-growing area of crime according to Cloutier. More and more criminals are exploiting the speed, convenience and anonymity of the Internet to commit a diverse range of criminal activities that know no borders, either physical or virtual. The crimes can be divided into 3 broad areas: Attacks against computer hardware and software using botnets, malware and network intrusion; financial crimes such as online fraud, penetration of online financial services, and phishing; and abuse, often involving young people, in the form of grooming or 'sexploitation'.
You can greatly improve your own safety and security, Cloutier says, by consistently taking just 4 essential actions:
- Be Aware of Your Situation: If you're applying for a loan and you're in a bank, expect to be asked for a lot of identification. But if you receive an e-mail or phone call that claims to be from your bank and the message or caller asks you to "verify" your account number, user name, password, or PIN — beware! "Never give out personal information over the phone, through the mail, or over the Internet unless you know exactly who you’re dealing with ," Cloutier says.
- Shred It: Any sensitive papers should be shredded before being disposed of. Some people make a good living sifting through trash looking for papers with account numbers and other identification. A $40 shredder is a good investment, Cloutier says.
- Cyber Hygiene: Keep your computer clean by not opening attachments or clicking links in e-mail messages from people you don't know. And even if the message appears to be from someone you do know, ask yourself if the message is in character for the sender. On websites, Cloutier says, "Look for 'https' or a picture of a lock in the address line before purchasing from a website or giving out information on that website."
- Review, Dispute, and Report: When bank and credit card statements arrive, review them promptly and carefully. If there's a charge that you don't recognize, check it out immediately. The sooner you notice and report a problem, the less damage a criminal can inflict.

A fifth important point involves passwords: Important passwords should be "long and strong" and it's important to change them regularly.
A password for a newspaper site need not be particularly secure, but one for your credit union should be. Some financial institutions are building more security in to their websites, but a strong password is always the first line of defense.
If Your Identity Is Stolen
Act fast! This is important because you want to stop the thief before too much damage is done. Cloutier says these are the steps that need to be taken:
- File a report with local law enforcement.
- Change your passwords for all online accounts.
- Inform your bank of the situation and replace your credit and charge cards. Close any unauthorized or compromised credit cards and inform those companies of the situation.
- Contact one of the three credit bureaus to report the crime or suspicion: Equifax, Experian, TransUnion.
- Identify what other information may be at risk. You may need to reach out to other agencies.
Reporting the incident to police is not done with the expectation that police will be able to solve the crime. Few police departments have detectives who are trained in fighting cyber crime and, even if they did, the criminal is often in some distant jurisdiction or in another country. You will, however, need to reference the police report when dealing with financial institutions.

Public Wi-Fi and Hotel Business Center Threats
The National Cybersecurity and Communications Integration Center recently warned about "keylogger" applications found in hotel business centers. Many people already know about the dangers of using public Wi-Fi hotspots, but generally don't consider any dangers in hotel business centers because computers provided there are hard-wired to the hotel's network. When a keylogger is installed, anything the user types (URLs, user names, and passwords) will be captured.
The warning said that the attacks were not sophisticated, requiring little technical skill, and did not involve the exploit of vulnerabilities in browsers, operating systems or other software. The malicious actors were able to utilize a low-cost, high impact strategy to access a physical system, stealing sensitive data from hotels and subsequently their guest’s information.
The incident noted here affected mainly hotels in the Dallas/Fort Worth areas, but could be replicated anywhere. In some cases, the suspects who planted the malware used stolen credit cards to register as guests of the hotels. Once in the hotel's business center, the thieves would use the public computers, log in to a G-Mail account, and run malicious key logging software.
The keylogger malware captured the information other hotel guests entered when they used the computers and then sent information via e-mail to the thieves' e-mail accounts.
According to the report, "the suspects were able to obtain large amounts of information including other guests' personally identifiable information (PII); log-in credentials to bank, retirement and personal webmail accounts; as well as other sensitive data flowing through the business center's computers."
Fraudulent E-Mails Seem to be on the Upswing
I receive a lot of fraudulent e-mail messages and most of them come to my TechByter address. There's a good reason for that: The address is on literally hundreds of website pages. The address isn't one that I use for business, though, so I know that any message from Bank of America (not my bank) or Bed Bath and Beyond (don't shop there) or Sam's Club (not a member) sent to that address is a fraud. But what about a message from companies I do buy from?
I like Petco. I buy cat food there, but they don't know me as Mr. TechByter. They have my personal e-mail address and the account is linked to a phone number that isn't public. So when I receive a message telling me that I must retrieve my customer loyalty points right away or lose them, I know better than to click the link.
Not everybody has the luxury of having multiple e-mail addresses, though; so what if you receive a legitimate-looking message from a company that you do business with?
Examine the message. In my case, it's being sent to an address I don't use for businesses, so I don't have to look any further. The clues are both present and abundant, though. The sender isn't Petco. Neither are either of the two links provided. And the deadline was 1 day in the future. Businesses simply don't do things like that. A limited-time-offer might be good for a month or a week, but not just a single day or a few hours.
Click any of the smaller images for a full-size view. Press Esc to dismiss the large image.
I've seen messages for new cars at 80% off. That's patently absurd and no rational person should click the link. What about this one, though. There are no truly absurd claims, but there's a pointless notice number. Car dealers don't "liquidate" stock in the summer, though. This fits into the "if it's sounds too good to be true, it probably is" category.
"After doing this, you'll have twenty-twenty vision by Friday." Really? Disregarding for a moment that "doing" something won't magically improve your vision, even if such a technique existed, it would certainly take more than a week. Place this one in the same category as the ones that promise you'll lose 30 pounds in 6 days, that you can reverse diabetes by eating one weird food, or that a doctor somewhere has been imprisoned because he can cure cancer.
Costco isn't in the business of handing out shopping sprees to people who aren't members. Or, for that matter, to people who are members. This one has another phony number and sounds like it was written by someone with a limited grasp of English. Oh, and of course I must use them TODAY!
Mixed in with these are the almost daily offers for free oil changes. "Just print the coupon you'll find at this (poisoned) link." Not all of these links want to send malware your way, though. Some will simply force you to fill in a form that asks for an outrageous amount of personal information. Then, to cover the fraudster's tracks, it may actually display a "coupon" that you can print. It'll print just fine, but if you try to use it, the coupon won't be accepted because it's fake.
The fake-coupon scam is also pretty common with fast-food restaurants. And there's the perennial "Somebody has ordered a background scan on you. See it here." These are almost always thinly veiled attempts to install malware.
At first glance, one might think that this fraudster was addressing me by name (Bill.blinn), but clearly that's the first part of my e-mail address. I'm a bit surprised that most fraudsters haven't yet figured out that they could make these ploys look more realistic by splitting the first part of the e-mail address on any punctuation and then capitalizing each word. Any middle school kid who has gone online to learn any programming language would be able to do that in the first week.
This message also has a really long certificate number (the longer the number, the more believable it is). And I need to use it within one day.
If Warren Buffet knows how to turn $1000 into $20,000, don't you think he'd be using it himself and not spamming the entire world with a "tip" that must be used on the same day it was received?
The bottom line for almost all of these is that nobody would ever fall for one of these simple scams if they'd just take a moment to examine the message, consider a skeptical question or two, and apply common sense.
Don't let the scammers get you!
InDesign Pushes into the Future of Publishing
The future of publishing would seem to be electronic. Paper-based books are in not danger of disappearing anytime in the foreseeable future because they have numerous advantages for some kinds of works (reference books in particular). But electronic books offer some gigantic cost advantages to publishers by eliminating paper, printing, shipping, warehousing, and (pardon the reminder) remainders. Remainders are books that didn't sell and are offered by operations that sell them for as much as 90% less than the published price.
The Creative Cloud 2014 update of InDesign places a heavy emphasis on epub-formatted output. In fact, InDesign has been able to create epub files for a while now, but the process was successful only for books that didn't depend on any given illustration's being located in any position relative to any particular text. Some say that epub files are like Web pages. That's correct, but it doesn't go quite far enough. Epub files are Web pages and the text is intended to reformat based on a variety of factors.
Users are able to modify the size of the text, the width of the margins, line spacing, and (depending on the reader) several other factors. All of these have an effect on how the text flows and the publisher can't guarantee what effect the changing text flow will have on graphics within the text. For a basic non-fiction book or novel, that's not a problem; it is a problem, though for electronic versions of poetry, picture books, and such. The new ability to create a fixed-format epub makes it possible to create an electronic book that exactly mimics the design of the print version.
Right, Wrong, or It Depends?
Some designers may think that this is a wonderful development and plan to use it for all their books. That would be a bad choice.
Some designers may think that this is a terrible development and plan to ignore it entirely. That would be a bad choice.
The right response should be to evaluate the publication at hand and determine whether fixed-layout or text re-flow is the better option. There is no "good" or "bad" here in a general sense, but a decision making process is needed to evaluate the design of each book and decide which output format is more appropriate.
For now, the best solution might still be to use a PDF output if you need a fixed-layout file. That's not because of anything that Adobe did wrong, but it reflects the current state of reader technology. To display books in the new format properly, the reader must support the EPUB 3.0 standard and most readers are still on version 2.
Let's take a look.
Here's the sample publication that Adobe provided. It's a multi-page concert souvenir booklet that contains text and images juxtaposed so that they make sense in context. It's important that the words and pictures remain associated.
So for this publication, I selected the fixed layout option. Note that there are also choices for reflowable (standard) epub files, PDFs intended either for interactive use or print, HTML, and several other formats.
This is an example of what happens if you export a highly-designed publication in reflowable format.
To be fair, InDesign includes numerous options that improve the layout for a viewer that supports only reflowable files, but the process involves a lot of manual work. That's why the fixed format option is so welcome.
The fixed-layout dialog includes a reminder that the file will be in EPUB 3.0 format.
Here's the result in Calibre, a free viewer that has some support for EPUB 3.0. Apple's reader currently has the best 3.0 support but other readers will eventually catch up and it's good to know that InDesign will be ready when that day arrives.
Currently, though, the better option for a fixed-layout publication might be the interactive PDF format. PDF readers are available for every computer and tablet I know of and the display will always be correct.
Making Tables Easy to Modify
If you've ever created a table in InDesign and then realized that a row or column is in the wrong location, you're probably familiar with the process of adding a new row or column, copying the information from the original location to the new location, and then deleting the unneeded column or row. It's not too bad if just one row or column needs to be moved, but rearranging several rows or columns used to be painful.
InDesign makes the process much easier now, employing a website-like drag-and-drop feature.
You can use the Table menu to select a row or column, but power users will quickly learn the keyboard shortcuts (column: Ctrl-Alt-3; row: Ctrl-3).
After selecting the row or column (row in this case) drag until the blue line appears where you want the selection to be moved to.
The Vimes row now appears below Wild Leaves.
Easy!
Some Shortcomings Remain
For all of its power, InDesign is surprising for some of the features it doesn't have. Come back with me to June of 2004 when I wrote about InDesign. Here's a section of Technology Corner (what TechByter Worldwide was called in those days) from a decade ago:
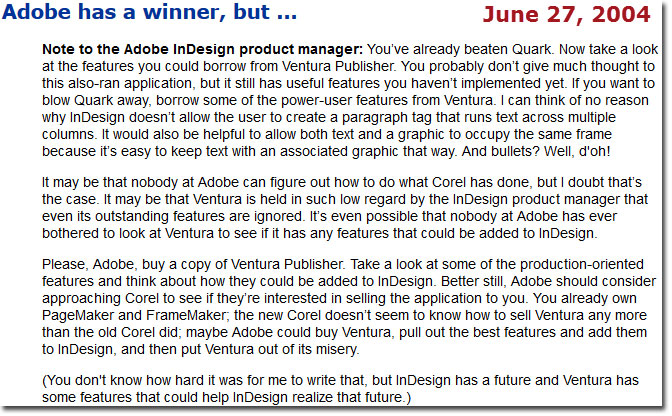
A few months after that column ran, I was in Seattle and was invited to talk with some of the InDesign developers so that I could describe and illustrate some of the areas that needed improvement. Probably many of the improvements I wanted to see were already on Adobe's road map, but it still took at least 5 years for InDesign to gain the ability to define a paragraph style that would allow a headline to span multiple text columns. Many, if not most, of the things we talked about back then are now included in InDesign, and features that never occurred to me, such as the ability to create e-books and now the ability to create epub files with fixed layouts.
A new capability to inherit program settings from one version of the program to another is welcome, but long overdue, and InDesign is still incapable of performing one task that is so basic that even word processors have done it for years: That missing feature is an inter-column rule.
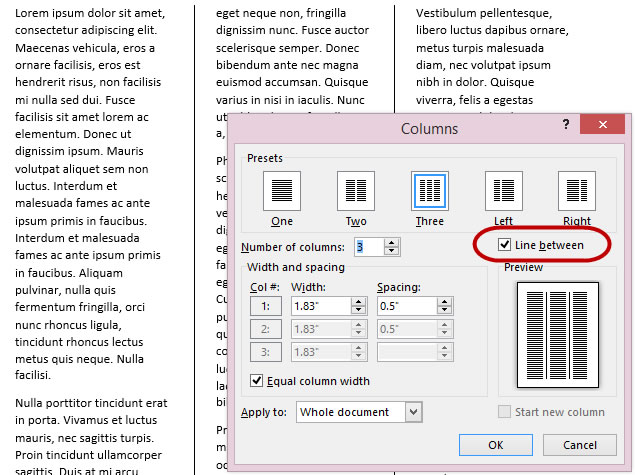
Inter-column rules in Word.
This is such a basic feature that I'm surprised every time a new version is released without it. If you perform a Google search with the terms "inter-column rules" and "InDesign", you'll see that InDesign users who simply assumed that such a basic feature would be present are surprised when they need to do something that they expected to be simple only to find that the only way to create the column rules involves the time-consuming and error-prone process of manually drawing the rules.

 InDesign's new features are winners and that makes the absence of some basic functions all the more puzzling.
InDesign's new features are winners and that makes the absence of some basic functions all the more puzzling.
Despite the minor issues I've noted here, and they are minor when considered in the overall context of what InDesign can do, there's simply no other game in town. Corel has withdrawn Ventura, Quark Express has all but disappeared, and lesser publishing tools such as Microsoft Publisher or the open-source Scribus just don't have the features that pros need. InDesign is part of Creative Cloud. I'd like to see Adobe add pizza-style pricing for the Creative Cloud so that those who find that the need 3 or 4 of the primary applications, but not the entire supreme pizza with all the toppings, could get the ones they need for a lower monthly cost. Adobe is nothing if not adaptable, though, and the company's marketers are probably doing the math on other possibilities.
Additional details about InDesign are available on the Adobe website.
Short Circuits
What People Take When They Leave
Dealing with security when employees quit or were fired used to be easy in the old days. They couldn't easily carry off a filing cabinet full of information. Then came copiers. And computers instead of dumb terminals. Now e-mail and Internet connections and thumb drives. A former employee can easily walk off with tens of thousands of pages of confidential information. And sometimes companies make it even easier.
Osterman Research surveyed nearly 400 people and found that 89% of them still had access to various accounts that belonged to former employers. These included sales databases, PayPal, e-mail accounts, internal wiki or SharePoint accounts, and social media accounts.
Having worked with one company that has clear-cut and stringent policies for dealing with employees who quit or who are let go, I was shocked by these numbers. In the case I'm familiar with, when an employee leaves the company, on good terms or bad, several things happen immediately:
- Whether or not the former employee's access control credentials have been returned, the credentials are immediately rescinded to eliminate physical access.
- Access to all internal computer resources (login credentials for servers and services) are deactivated.
- Phone and e-mail credentials are deactivated.
- And on and on and on. The policy that describes the process is detailed and complete.
The study found that nearly half of the former employees they spoke with retained access to confidential data and that most of them had logged on to corporate computer resources after leaving the company. This is dangerous and it could have legal implications for the company.
Osterman provides market research, cost data, and benchmarking information to technology-based companies.
Owners and managers of smaller companies often think that the problem is one faced only by large corporations, but it's not. The report cites a lack of "IT offboarding" procedures as the main problem.
You can read the full report online.
Just Write on the Bellhop's Forehead
Be sure to check out "‘Beep,’ Says the Bellhop" by John Markoff in the New York Times this week. (Link at the bottom of this account.) It describes the bellhop in a hotel that's adjacent to Apple's corporate headquarters. The bellhop makes the hotel distinctive because it's a robot.
In fact, the robot ("Botlr") hasn't yet been rolled out (literally). That will happen on the 20th of this month. But he has been seen operating in test mode. Botlr is about 3 feet tall and can deliver items to guests' rooms.
Botlr arrives, calls the room's phone to announce its arrival, senses when the door has been opened, and then opens its top-loading bin to deliver whatever the guest requested. You don't tip this bellhop, but you can rate its service. Give Botlr a high rating and, according to the article, it performs a little happy dance before departing.
Markoff says Botlr looks a bit like R2-D2, "or perhaps like a miniaturized nuclear power plant’s cooling tower." It rolls at about 4 miles per hour. When it needs to travel to another floor, Botlr calls the elevator and enters the car, "taking care to stay out of the way of any human passengers."
Botlr can even connect itself to a recharging station so it's always ready to go.
