Google's Chrome is 31
Mozilla's Firefox is still my primary browser, but there's a lot to like about version 31 of Chrome. Because it's built by Google, it puts many Google features at your fingertips. Currently, it's not quite enough to drag me away from Firefox, but maybe someday.
I would rate Firefox and Chrome nearly as equals, followed by Internet Explorer and Opera. Fortunately, Apple's Safari browser is no longer available for Windows machines so it's no longer at the bottom of the heap.
When you start Chrome with no sites open, you'll have a large Google search entry box along with direct links to Google Plus, G-mail, Images, and (with 2 clicks) to most other Google services. And no, this isn't the default background. Chrome can be skinned and this is the skin I selected.
If you have a microphone, you can tell Google what you're looking for by simply saying it. This works well on tablets such as the Nexus. Privacy note: Google is listening. If you say it, Google will store it.
Chrome will try to convince you that if you're one of the thirty-seven people in the world who currently don't have an account with Google that you should create one. Should you? Probably, but you'll have to decide for yourself whether the convenience is worth the intrusiveness.
Once you've installed Chrome, it will always be up to date because the updates are delivered more or less silently. Unlike Firefox, though, extensions aren't automatically updated. This offers better security than Firefox does, but it also means that you'll need to do more work.
Flash and PDF Support Are Included
Adobe Flash is included with Chrome so you don't need to install a separate plug-in. That's also true for Adobe PDF support. Since Adobe fixes security problems with the Flash player about every 12 minutes, having those updates taken care of automatically is a plus. And because Chrome runs Flash in a "sandbox" (a protected area of memory), security is improved, too.
If a website offers you a PDF document, Chrome's built-in PDF reader takes over. Although you can copy and paste text from PDFs, the same isn't true for images.
Sync or Swim
In addition to being able to synchronize bookmarks across multiple devices, Chrome now allows users to sync tabs, passwords, preferences, themes, apps, auto-fill entries, extensions, and more. This can be handy (if you want Chrome to be the same on all computers) or it can present a problem (if you want to have different settings on various machines). After trying this, I turned it off.
Privacy Finally Comes to Chrome (More or Less)
Chrome has the "distinction" of being the last big browser to support the Do Not Track privacy option, and the developers have turned the option off by default and they've hidden it so well that it's likely most people will never find it. This is Google, after all, a company with a vested interest in being able to track users.
If you want to turn it on, you'll need to open the Advanced Settings section and disregard the somewhat disingenuous pop-up that says your privacy won't actually be protected
Because Google's motto is "Don't be evil," it's worth noting that Internet Explorer 10 (from the "evil empire") enables Do Not Track protection by default.
Actually, if you want the strongest Do Not Track protection, you should be using Internet Explorer 10. (And you don't know how strange it is to type that!)
Apps Can be Launched Inside or Outside Chrome
Beware, though, if you decide to use this feature, Chrome will insist that you log in, it will add a new icon to your task bar, and it seems also to want to make itself the default browser. After a few minutes of being asked to sign in every few seconds (and signing in) I finally gave up on the apps function of Chrome. If you set Chrome as your default browser, maybe you'll find a useful app to load. From my perspective, there wasn't much. Google Maps? I can use that from Chrome, Firefox, or Internet Explorer already. Why do I need an app?
And "Writer"?
Well, this is pretty 1985, isn't it? Although this looks a lot like a character-based application, it's really a Windows GUI. If you use an application like this, you'll quickly see that no formatting is possible. No bold. No italic. No underline. No indents. No left, right, or center justification. But if you misspell a word, you'll get a red squiggle.
The advantage of an application such as this is that all of your attention is focused on the words. Formatting comes later. In other words, it's a lot like any standard text editor and I already have one of those.
This application displays "News" in the upper right corner. Annoyingly, it bounces from time to time. If I click the link to follow it, the developer tries to sell me a $60/year upgrade. In two words: No thanks.

 Browsers are "free", so should you pick just one?
Browsers are "free", so should you pick just one?
As a browser, it's fine, but watch out for the "extra features" that you might find in Chrome. If you're somebody who doesn't trust Google with information about your life, then you should probably avoid this browser.
Additional details are available on the Google website.
New York Times Update Appears, Vanishes, and Reappears
Even people who work at the New York Times don't much care for the newspaper of record label that has been applied to the paper. It's not like an event, if it's not reported there, ceases to exist. But the New York Times continues to be, with the occasional mis-step, a dependable source of balanced information. For many years, I received the print version of the paper at home, but the national print version, if it still exists, closes in the late afternoon. The Web-based version is more timely and I read it daily. A new version of the website appeared and then disappeared. It's back now and I like it.
When I logged on recently, a pop-up message offered a preview of the new site. I clicked and immediately decided that it was a significant improvement over the original site even though the original site was probably the best example of newspaper journalism on the Web. But when I tried to find it the next day, it was gone.
After a few more days, I contacted the newspaper's customer service department and asked. It seems that what I saw was, indeed, a preview and that the update would be rolled out the following week, on my older daughter's birthday. Not that they knew it was her birthday.
On the appointed day, I received a message that told me the new version was available.
Instead of taking the Apple approach and simply claiming that everything is "discoverable", the NY Times management went to considerable lengths to explain how the new site works.
A "welcome" page showed that the design would work well with various screen sizes and orientations, portrait or landscape. And it offered a video to show more.
I had already seen the new site, so the video probably wouldn't tell me anything new, but I thought I'd watch it.
The video never started to play. But the other graphics clearly illustrated that the update is designed not only with computer users in mind, but it's also for the large and growing group of people who use tablets of various sizes and phones to read the newspaper.
After navigating to the Science section, I thought I'd read the review of one of my favorite new books, Cat Sense, by John Bradshaw.
At the top of the screen, the website offers other articles that might be of interest to me and I'm offered various ways of sharing the story in the left margin.
In Scandinavian countries, sans serif type is the norm, but in much of the rest of the world, typefaces with serifs are considered easier to read. Computer screens have, until recently, been unable to display serif faces well. (That's why TechByter Worldwide uses a sans serif face.) The NY Times has elected to use a serif face and it's highly readable. The designer has also increased the line spacing slightly to enhance readability.
The New York Times is a large newspaper with many sections and access to these sections is addressed by the drop-down list from the upper left corner. Readers can immediately navigate to any of the major sections.
Each section lists the articles that are appropriate for the part of the newspaper. The New York/Region section shown here shows the primary stories at the top and 3 columns allow additional organization.
I decided to read the story about a diplomat from India who has been charged with abusing her domestic help.
Instead of being broken up over several website pages, the entire account is a single page. This makes it easier to read (just scroll) and also easier to print.
When you're reading one story, other accounts from the same section of the paper are in a scrollable bar at the top.
Nice job, New York Times!
The Nexus Tablet Listens When I Talk
I • remember • when • voice • recognition • software • required • speaking • like • this. That's no longer the case and even small devices such as smart phones and tablets are able to listen and respond to what you say. Remarkable? To an old guy like me, yes. To somebody who has never known a time when there wasn't a computer nearby, not so much.
My little Nexus 7 tablet listens when I talk. Earlier versions of the tablet required only that the user say "Google" but now the trigger is "OK, Google." Adding the "OK" probably eliminates false activations. What can I find out? A few examples:
- Go to techbyter dot com.
- Send an email to president at whitehouse dot gov.
- What time is it in Barcelona?
- What is the weather today in London?
- Tell me about cats.
- And lots more.
I asked about the weather (OK Google, Tell me about the weather) and the tablet opened my favorite weather application, Weather Underground. Here we see it's 8 degrees below zero currently and the chart at the bottom shows predicted conditions and temperatures for the next few days.
You can listen to some of the commands and responses on the weekly podcast.
A quick tap shows me temperatures in the area.
Or maybe I'm hungry for pizza. OK Google, Find pizza gives me a lits of pizza shops within 20 miles of my current location.
If I suddenly decide that I need another cat and I don't know where to find them because I'm in Hilliard instead of in Worthington, OK Google, Find cats does the trick. Unfortunately, if I'm looking for a cat who has hidden somewhere in the house, this command isn't at all useful.
E-mail Trouble? Maybe You Need Another Option!
A participant in a discussion list I read was having an e-mail problem. "A couple of years ago a university started rejecting messages from my domain. The tech people at the university tried to help, but found that the overrides they put in place didn’t last. This week, a message that I sent to one of my clients at the university didn’t go through. Should I use another email address such as Hotmail?"
This is something that mainly affects people who operate their own domains, but sometimes large providers such as aol.com and hotmail.com also become blacklisted. This information could be used by anyone who has more than one account with services that allow the use of standard e-mail clients.
I started by explaining that this happens occasionally with any shared host. BlueHost is good about TOSing the offending party (deleting the account under the provider’s terms of service), but it can take a while for the e-mail block to be removed. I suggested setting up the e-mail client to use the ISP's SMTP server instead of BlueHost's. This kind of split operation is easy to set up and I keep both settings handy.
So even if you don’t have your own domain, this could be a handy trick to permit sending messages through an alternate service. For example, you could set up your ISP’s server as one option and G-Mail’s as the other. If you decide to do this with G-Mail, you’ll find Mozilla’s explanation useful even if you don’t use Thunderbird.
Why Your Domain’s Mail Might be Blocked
The most common reason is a result of your domain being on a “shared host” (BlueHost, DreamHost, etc.) If you have a domain name and it’s not hosted on your own private server (or “virtual private server”), you’re on a shared host. Also, if you’re not paying at least $100 per month for hosting, you’re on a shared host.
A shared system may host 100 or more (often a lot more) domain names. When somebody signs up for hosting, the hosting company assigns the domain name to a specific server. At BlueHost, my domains happen to live on box445.bluehost.com. TechByter Worldwide has a static IP address (67.222.41.89), but that doesn’t affect mail I send via BlueHost. All outbound mail from all domains on box445 come from 74.220.220.182.
So if SammyTheSpammer.com sets up business on BlueHost and is assigned to box445, he’ll run afoul of one of several Internet vigilantes that run e-mail blacklists. These blacklists are used by many universities, corporations, and ISPs and messages coming from blacklisted IP addresses are assumed to be spam.
BlueHost will discover the problem and with delete SammyTheSpammer.com’s account under their terms of service (TOS), but that’s not the end of the problem. Sammy will have been TOSed, but the blacklist will be in force for another 48 or 72 hours and your messages will be refused by those who use the blacklist.
This situation can occur with any shared-host operation, so changing from DreamHost to BlueHost or from BlueHost to GoDaddy or from GoDaddy to UncleHarry’s Cheap Hosting won’t eliminate the problem.
A Permanent Solution
The solution is to have a standby server that you can send mail through and just about everyone who has a domain name has that backup server thanks to their Internet service provider (Comcast, RoadRunner, WideOpenWest, etc.)
Before discussing that, it’s important for you to know that two servers are involved in e-mail: The POP3 (Post Office Protocol) server handles mail that has been sent to you and the SMTP (Simple Mail Transfer Protocol) handles mail that you send.
I’m going to illustrate this with images from Thunderbird because it’s one of the more popular e-mail programs. Other programs have similar settings and usually call them the by the same, or very similar, names. You’ll want to view the Outbound (or SMTP) server settings.
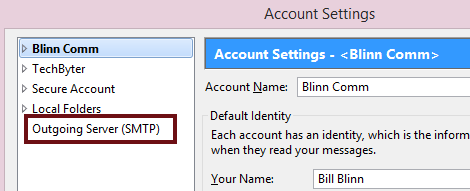
Two crucial settings are the server name and the port.
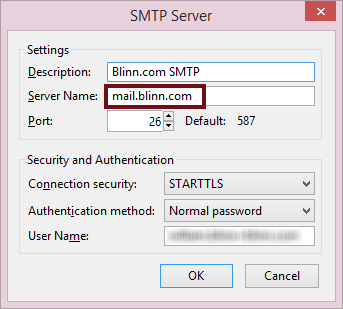
The default port for unencrypted SMTP is 25 and 587 for encrypted SMTP. BlueHost specifies port 26. If you’re using your hosting provider to send mail, you have already worked out all of this. Now you need to add a second server, the one operated by your ISP (or maybe by G-Mail).
So visit your ISP’s help page and search for instructions to set up an e-mail client. The instructions will probably list several popular applications. Any of these will have the information you need, which is the name of the SMTP (outgoing mail) server. Ignore any authentication instructions; that comes later and it will differ from what the ISP says.
Take the server name back to your e-mail program. Because you are using one company’s server to receive mail and another company’s server to send mail, you cannot use the same credentials for both. You will need to set up explicit credentials (user name and password) to send mail.
Find the location in your program where you can add a new server. This is usually labeled clearly.
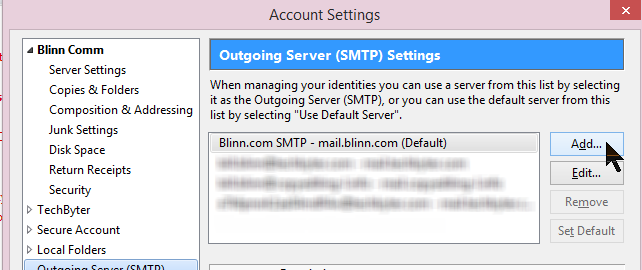
That will open a dialog box such as this:
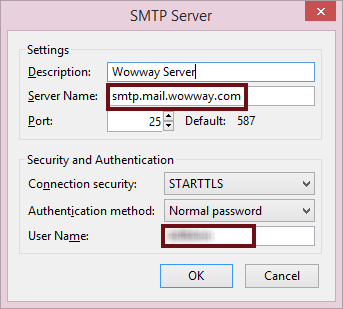
You will provide at least the server name and your user name (the one the ISP assigned to you) here. Depending on the e-mail program, you may also be asked for the password. Thunderbird asks for the password the first time this account is used to send mail and then remembers it. You’ll want to have both your user name and password handy.
When you have completed the setup and tested to be sure that you can send messages using this server, you’re prepared for those instances in which your messages are blocked because a spammer is operating on your server.
To use the alternate server, visit the account settings section of your application and change the outbound server for your account from your hosted domain’s server to your ISP’s server.
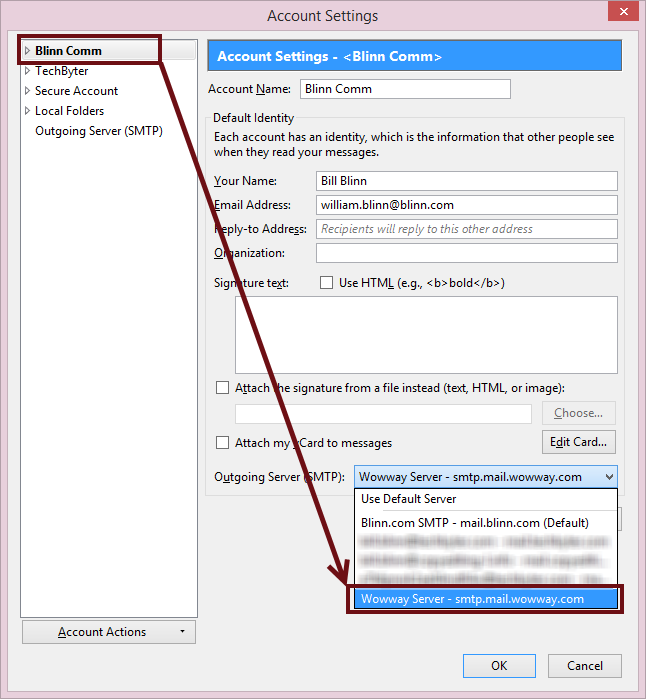
That seems like a lot, but once you get it set up, switching from one to the other takes just a few seconds, so it’s a good insurance policy.
Short Circuits
Webroot Secure Anywhere: No Longer Recommended
It’s unusual for me to miss something so obviously problematic with an application that I shouldn’t have recommended it in the first place. Most applications have a certain number of “surprising features” (aka “bugs”) but if the application is generally usable, we learn to live with them.
That’s what I thought initially about Webroot Secure Anywhere. This is a cloud-based protective service that seemed ideal because it accepted automatic input from systems where the application had been installed. Unfortunately, I found that it causes a lot of problems and Webroot’s support team – although always prompt, polite, and concerned – was never able to solve them.
By the time I decided the best solution would be to remove the application from my computers and to request a refund, the period during which a refund would be granted had passed.
The first problem I encountered was with Secure Anywhere’s privacy protection feature. It made programs that I depend on unusable by default. These included LastPass, the password manager, and a macro application called MacroExpress. Eventually, I figured out what the problem was and found that I could exempt individual programs. Secure Anywhere receives frequent updates, though, and every time the program was updated, I had to fix the problem again.
Eventually Webroot found a way to permanently exempt the programs, or so they said. I still had to fix the problem occasionally. Webroot also installed a Password Manager in Firefox and activated it by default. That was the primary point of conflict with LastPass. Although I disabled the add-on and uninstalled it, it returned whenever an update ran.
Secure Anywhere also warned about numerous websites that were safe. I want to be protected from rogue sites, but there were far too many false alarms.
Every time I reported a problem, Webroot’s first suggestion was to download their log grabber, run it, uninstall Webroot, and then re-install it. At some point this begins to feel a lot like being told that for the spell to work, the chicken must be waved clockwise around the head instead of counter-clockwise.
And once their logging tool reported that Secure Anywhere wasn’t installed; not only was it installed, but also it was running. This wasn’t exactly a confidence builder.
The most recent time that Webroot support asked me to uninstall Secure Anywhere and then reinstall it, I decided to leave it uninstalled for a few days to see if another problem would persist when Secure Anywhere wasn’t running. Occasionally and in various programs, some keystroke simply disappeared. For example, I might type "some keystrokes disappear" and what would appear on screen was "some keysappear". After removing Secure Anywhere, that behavior stopped.
This is unfortunate because the idea behind Secure Anywhere is excellent, but sadly the implementation seems not to be.
Net Neutrality: Dead or Just Badly Wounded?
If it was up to me, companies such as Comcast and TimeWarner would have to treat all Internet traffic the same, but a federal judge has given the companies what is, constructively, permission to do whatever they want with data on their networks. Unless the Federal Communications Commission acts. So will it?
Good question! FCC Chairman Tom Wheeler hasn't been exactly a powerhouse in the battle for consumers' rights. Wheeler, writing on the FCC website, said that the agency will vigorously exercise its authority to ensure broadband providers operate their networks in the public interest. But -- get this -- "cautiously".
Service providers want to be able to give preference to content provided by their own companies at the expense of all others. So the people who have Internet access via Comcast, for example, might find that their attempts to watch Netflix streaming media is hampered by a slow connection while video provided by Comcast properties would play at full speed. The same could be said for all of the other large providers who also own media operations.
Wheeler seems to be attempting to remain, well, neutral in the matter, perhaps trying to find a middle way between what the providers want (being allowed to do what they want) and what advocacy groups want (prohibiting network providers from treating data differently because of its source).
He wrote that network operators are unlikely to do anything that will diminish the value of the Internet and that the FCC will not needlessly hinder the ability of the providers to do what they need to do.
To some extent, network management already requires that some types of data be treated differently. Streaming video and audio, for example, generally get higher priority than e-mail messages or file transfers because this allows media to play without halting and slight delays in e-mail or file transfers will go unnoticed.
