Partly Cloudy with a Chance of Locust Swarms
Everybody seems to be excited about "cloud computing". Everybody but Microsoft, that is. By way of hedging its bets, Microsoft offers its Live service to compete with Google Docs and Zoho. The online (in the cloud) services continue to improve, but they're still faint copies of applications that run locally on a computer. This week we'll take a look at Zoho.
When Zoho went live several years ago, there was little interoperability between the various applications. In fact, they bore little resemblance to each other. That has changed.
 Zoho offers the most features of any similar application: A documents tab shows documents of all types and specific tabs exist for the calendar function, tasks, notes, contacts, text documents, spreadsheets, presentations, and online meetings. You'll also find a document viewer and a free-form notebook function.
Zoho offers the most features of any similar application: A documents tab shows documents of all types and specific tabs exist for the calendar function, tasks, notes, contacts, text documents, spreadsheets, presentations, and online meetings. You'll also find a document viewer and a free-form notebook function.
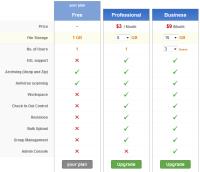 Zoho allows users to collaborate on documents and share them and the basic (limited) service is free. For $3 per month, you can increase storage from 1GB to 3 and add several features that increase usability: Revision tracking, secure connections, the ability to upload documents in bulk, and check-in control for documents. For $9 per month, you can have 15GB of storage, 3 users, and an admin console. For 10 users and 100GB of online storage, you would pay $40 per month.
Zoho allows users to collaborate on documents and share them and the basic (limited) service is free. For $3 per month, you can increase storage from 1GB to 3 and add several features that increase usability: Revision tracking, secure connections, the ability to upload documents in bulk, and check-in control for documents. For $9 per month, you can have 15GB of storage, 3 users, and an admin console. For 10 users and 100GB of online storage, you would pay $40 per month.
The problem is that features I count on in Microsoft Office aren't present when I view the documents in Zoho.
 Here's an example. I keep track of upcoming programs in Excel. The current and following weeks are highlighted in orange. Past weeks are in green. Future weeks are in light orange. Completed program segments are shown in dark green, while segments I've started are in light blue. Anything not yet started is in a tan color.
Here's an example. I keep track of upcoming programs in Excel. The current and following weeks are highlighted in orange. Past weeks are in green. Future weeks are in light orange. Completed program segments are shown in dark green, while segments I've started are in light blue. Anything not yet started is in a tan color.
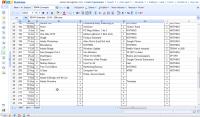 When I import this sheet to Zoho, none of the highlighting is present. I can still find the current and upcoming weeks by examining the dates. I can tell the status of a program segment by decoding the status column (N=not started, S=started, C=completed) but the color coding makes a quick review so much faster and easier.
When I import this sheet to Zoho, none of the highlighting is present. I can still find the current and upcoming weeks by examining the dates. I can tell the status of a program segment by decoding the status column (N=not started, S=started, C=completed) but the color coding makes a quick review so much faster and easier.
 And so it goes with the other applications: The basic functionality is present, but I depend on more than just the basics. Zoho does offer a host of other features, some of which have a minimal charge.
And so it goes with the other applications: The basic functionality is present, but I depend on more than just the basics. Zoho does offer a host of other features, some of which have a minimal charge.
But Microsoft clearly hopes to continue to own your desktop by providing an operating system and applications that do everything you want and probably more than you need. By providing a huge range of features Microsoft attempts to ensure that you'll find at least one relatively obscure function that you cannot live without and that this obscure function is not present in Open Office, IBM Lotus Symphony, WordPerfect Office, Google Documents, or Zoho.
So far, that strategy is working.
 Bottom Line: Zoho's suite is broad, but somewhat shallow.
Bottom Line: Zoho's suite is broad, but somewhat shallow.
I give the Zoho suite 3 cats, which means that it's a solid, functional application. Because of the price (free for individuals), I considered giving it a 4-cat rating. The suite also includes far more than the basic (word, number, and presentation) applications. Although the feature set is probably adequate for most people most of the time, the limitations rule it out for some users. Regardless, Zoho should be making some folks in Redmond, Washington, more than a little nervous.
For more information, visit the Zoho website.
That File You Erased Isn't Really Gone
Most people know that deleting a file doesn't really remove it from the computer. The file is simply "moved" to the Recycle Bin. And that's not quite entirely true, either. The file stays where it was and its location is noted as the Recycle Bin. Many people think that when you empty the Recycle Bin, the file is actually removed from the computer, but that's not the case. Everything is still there. The file is marked as deleted, but recovering it is a relatively trivial exercise. That's why the military specification for securely eliminating data calls for the physical destruction of the disk drive. But you probably don't need measures quite that extreme.
Allow me to introduce you to Eraser, a security tool for Windows that obliterates sensitive data when you delete it, not by moving the file to the Recycle Bin but by writing selected patterns to the areas of the disk where the file resided. It works with any version of Windows from XP (with service pack 3) through Windows 7, both 32-bit and 64-bit versions.
And it's free. The open-source code is released under GNU General Public License.
You probably have some files on your computer that you would prefer not to share with others. If you bring files home from the office to work on, would the remnants on your computer's hard drive be a problem? Have you ever written passwords to a plain-text file? Are you planning to sell your old computer or donate it to someone? There are people who buy old hardware from anyone who's selling it just to see what they can find.
So even if you don't need a secure-erase tool on a daily basis, you should use one before you sell or give away a computer or any kind of disk drive. Deleting files doesn't remove them. Formatting the drive doesn't overwrite the data. Only a program designed specifically to obliterate data will remove files that you don't want someone else to see.
Eraser makes this security problem much less of a problem and it does so with ease.
![]() After you install Eraser, you'll notice two changes: First, a new icon will appear in the Tray. That's because Eraser is always running so that it's available whenever you need it.
After you install Eraser, you'll notice two changes: First, a new icon will appear in the Tray. That's because Eraser is always running so that it's available whenever you need it.
 Second, you'll have an Eraser option from the context menu when you right-click any drive, file, or directory.
Second, you'll have an Eraser option from the context menu when you right-click any drive, file, or directory.
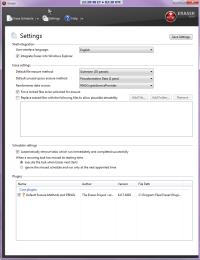 By default, Eraser uses what's called the Gutmann method to securely erase drives, directories and files. This is an algorithm devised by Peter Gutmann and Colin Plumb that writes a series of 35 patterns over the region to be erased. Most of the patterns in the Gutmann method were designed for older MFM/RLL encoded disks and because modern drives no longer use those technologies, some of the patterns are not needed.
By default, Eraser uses what's called the Gutmann method to securely erase drives, directories and files. This is an algorithm devised by Peter Gutmann and Colin Plumb that writes a series of 35 patterns over the region to be erased. Most of the patterns in the Gutmann method were designed for older MFM/RLL encoded disks and because modern drives no longer use those technologies, some of the patterns are not needed.
 Bottom Line: Before you sell or donate a disk drive, use Eraser.
Bottom Line: Before you sell or donate a disk drive, use Eraser.
This is a free, open-source application that simplifies the process of sanitizing a disk drive before disposing of it. Although the process is not as certain as physical destruction of the drive, it's more than adequate unless you're involved in some sort of international intrigue that involves well financed government security agencies.
For more information, visit the Eraser website.
Securely Deleting CD/DVD Data
If you store backup copies of some files on CDs or DVDs, you might be wondering how to render those files inaccessible when it's time to discard the media. The answer is quick and, depending on the tools available to you, it might even be fun.
 The fun method: If you have a paper shredder that can handle CDs and DVDs, your problem is solved. Mine isn't powerful enough to shred a DVD, but the result is clearly an unusable disc.
The fun method: If you have a paper shredder that can handle CDs and DVDs, your problem is solved. Mine isn't powerful enough to shred a DVD, but the result is clearly an unusable disc.
The not-as-much-fun-but-just-as-reliable method: Use scissors to cut the disc into 2 pieces or (depending on how paranoid you are) more than 2 pieces.
All that's really required is a deep scratch, one that breaks through the recording surface from the back of the CD or DVD. By "back", I mean the side that you write or, print on (if it's a printable disc), or place a label on. Two or three deep scratches on this side of the disk will be nearly as effective as the mangling illustrated above.
If you're a member of the mafia, a terrorist, or some other such unsavory person who might reasonably be expected to attract the attention of the FBI, the CIA, or the NSA, you'll probably also want to burn the remains. For most of us, though, what I've described is more than adequate.
Looks Like Everybody Died! Or Joined LinkedIn.
Have you noticed that spams come in waves of similar design. Although I plan to discontinue SpamArrest at the end of the year and use Postini instead, I've left the SpamArrest account enabled as I continue testing and becoming familiar with Postini. I no longer have SpamArrest collect any of my messages, so only messages sent to my SpamArrest user name show up there. Even so, the mailbox receives hundreds of spams per week.
 Many of the spams that SpamArrest picked up one day told me that someone had died. Gwen Stefani, Brad Pitt (several times, apparently), Angela Keys, Tiger Woods, Tom Cruise, Miley Cyrus, Angela Jolie, Johnny Depp, and Jennifer Aniston.
Many of the spams that SpamArrest picked up one day told me that someone had died. Gwen Stefani, Brad Pitt (several times, apparently), Angela Keys, Tiger Woods, Tom Cruise, Miley Cyrus, Angela Jolie, Johnny Depp, and Jennifer Aniston.
It must have been quite a day!
You won't be surprised to learn that I didn't open any of those messages.
 Postini is smarter about what it shows me and that's one of the reasons I'm midway through converting from one system to another.
Postini is smarter about what it shows me and that's one of the reasons I'm midway through converting from one system to another.
Most legitimate messages sail right through the Postini device and land in my inbox (after a week's worth of training). A large number of messages that can be clearly and definitively identified as spam are simply deleted. What Postini shows me are the messages that seem suspicious but haven't triggered enough warnings to be deleted without review.
On the same day, the Postini box suggested several people I don't know wanted me to join LinkedIn. I'm already a LinkedIn member and (here's something else that won't surprise you) none of these people had made the request via the LinkedIn site.
I continue to be concerned about spam: Not so much that people send it because criminals will always do anything that's profitable. What concerns me is that enough people open messages that are obviously worthless (at best) and possibly dangerous without giving the action any thought at all.
Short Circuits
New G-Mail Feature: Phone Calls
Google Voice lets you forward a phone number to your home phone or cell phone. You can even (within reason) name your own phone number. I came up with this number for TechByter: TECHBYTER1 (832-429-8371). But now Google allows users in the United States to make free phone calls to any other phone in the US or Canada through G-Mail. You don't even need a Google Voice phone number.
I'll have a full review of the service soon, but I have to say that all you need is a computer with headphones or speakers and a microphone. The quality is better than I expected it to be and it's easy to use.
You will, of course, surrender even more information to Google and that must be factored in to the "free" price.
Google says that calls to the US and Canada will be free for at least the rest of the year and calls to other countries will be billed at Google's usual (low) rates. For many countries, the cost is just 2 cents per minute.
If you have a Google Voice phone number, calls made from G-Mail will display that number as the outbound caller ID. You can also receive calls made to your Google Voice number inside G-Mail.
Google started rolling this feature out earlier this week and the company reports that it is now available to all G-Mail users in the US.
Analysts say Google's new service is more likely to hurt Skype than traditional phone companies because the telcos started cutting their prices several years ago in response to stiff competition.
Users made more than 1,000,000 free calls during the first 24 hours that the service was available.
Welcoming a Worm to Your Computer
Plug in a USB device and you may be opening the door to a worm. This week a spider dropped down from the ceiling and crawled across my hand as I sat at the computer. Harmless. Later in the week, it was crickets. A co-worker squished one of them, but I caught the other one and took it outside. Harmless. But worms? Not so harmless and Panda Security says many business computers are infected every year by worms that arrive on USB devices.
This is probably why some companies forbid the use of any USB storage devices.
Panda Labs says that about a quarter of this year's worms have been designed to spread through USB storage devices connected to computers. When the USB device is attached, the malware copies itself to any device that can store data. That includes cell phones, external hard drives, DVDs, flash memory cards, and MP3 players.
Panda Labs Technical Director Luis Corrons says that the replication is designed to be automatic and that most of the infections are invisible to the average user. "This has been the case with many infections we have seen this year, such as the distribution of the Mariposa and Vodafone botnets."
E-mail is still the most common vector for malware, but USB-based transmission is increasingly a threat. "There are now so many devices on the market that can be connected via USB to a computer," Corrons said. And any digital camera, cell phone, audio player, or video player could be "carrying a virus without your knowledge."


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
