PaintShop Pro's X7 Release Offers Useful Features
Remember PaintShop Pro? Maybe you thought it no longer exists, but that's wrong. Corel has released PaintShop Pro X7 and PaintShop Pro X7 Ultimate with extensive changes to the user interface. Corel also says brush performance is 30% better and support for 64-bit architecture allows fast performance with large images.
PaintShop Pro has been around for a long time. It was originally published by Jasc Software and Corel purchased the company in 2004. Jasc was located in Eden Prairie, Minnesota, and Corel maintained that office until 2007 when development was moved to California and China. Corel's offices are in Ottawa. The original version was was released in 1992 for Windows 3.1.
There's a new Shape and Text Cutter tool that I'll describe in more detail. This tool allows the user to clip a background image so that it fits within a shape. A new Smart Edge brush option controls the placement of pixels when you're painting around objects. PaintShop Pro X7 has also added support for what's called "sidecar" files that hold XMP data for raw images so that changes made in PaintShop Pro will be recognized in other programs such as Adobe Lightroom.
The X7 Ultimate version includes software from other vendors: Reallusion FaceFilter3, Perfectly Clear by Athentech Imaging, and a variety of of brushes, textures, and royalty-free backgrounds.
The X7 interface offers 3 primary panels: Manage, Adjust, and Edit.
The Manage panel is where you'll start. This is where you'll import images, store them, tag them, and rate them. The thumbnail images can be resized at any time from relatively small to very large.
There's also a wealth of information about each image in a panel on the right. This includes information about the camera and lens used to create the picture, the various settings (ISO speed, shutter speed, f-stop, focal length, white balance, file type, and exposure overrides).
The EXIF and IPTC values are displayed and you can add information about people and places.
When you select the Adjust tab, information in the left and right panels change.
The right panel offers a variety of "instant effects" that can be applied immediately. The effects can be stacked so multiple effects can be added to a single image. When you save the resulting file, it will be given a new name so that the original remains unchanged.
The panel on the left has 9 types of adjustments that can be applied to images.
Crop, rotate, and red-eye adjustments.
- Overall brightness and saturation, as well as highlight and shadow adjustments.
- White balance and tint.
- Brightness and contrast.
- Fill light (gamma modification) and clarity.
- Vibrancy (affects the strengths of colors).
- Local tone mapping (used to adjust the image sharpness).
- High-pass sharpen (radius and strength) and the blending mode.
- Digital noise removal and sharpening.
Here I've added just a bit of local tone mapping to boost the sharpness slightly.
Although a lot can be done with just these controls, the still more powerful tab is called Edit, where all of these adjustments are possible and more.
If the image you're working with is a camera raw file, you'll be given the opportunity to examine the histogram and make some basic adjustments to brightness, saturation, shadows, and white balance.
Here's a cheetah from the Columbus Zoo.
I increased color saturation slightly to make the colors more vibrant and then decided to use a feature that's not included in most competing products. I wanted to create text with letters that contained the cheetah's pattern and colors.
After selecting a typeface with thick letters, I sized the text so that it fit over the cheetah's fur.
The next step, with the text tool selected and the text cursor anywhere in the word, is clicking the Text Cutter icon in the tool presets.
And the result ...
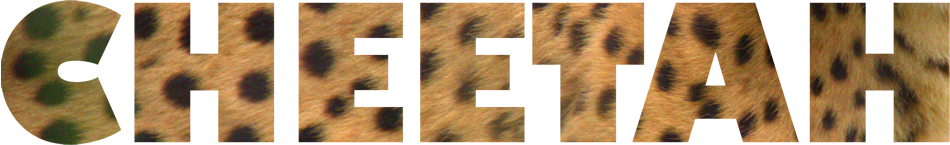

 Cool new features make PaintShop Pro X7 well worth looking at.
Cool new features make PaintShop Pro X7 well worth looking at.
PaintShop Pro X7 costs $80 and the Ultimate version is $100 (upgrades are priced at $60 and $80). An enhanced user interface, support for 64-bit processors, new features, and faster operation overall make PaintShop Pro X7 a contender for digital photography fans. New support for sidecar files and complete camera raw handling make things even better.
Additional details are available on the Corel PaintShop Pro website.
Should You Be Using Two-Factor Authentication?
Is it more secure or just a bothersome extra step? With the increasing number of user names and passwords that have been stolen in the past year, you may be thinking about enabling 2-factor authentication for accounts that offer it. Or maybe you've just heard the term and wonder what it is.
If your accounts have a user name and a password, you're using single-factor authentication. The 2-factor process adds a second level of authentication to an account log-in. In addition to your user name and password, 2-factor authentication schemes will typically require something you know (a PIN or a second password, for example), something you have (a security fob, ATM card, or mobile phone), or something unique to your body (finger print, eye scan, or voice print).
There's no question that 2-factor authentication makes the log-in process more cumbersome because you need to provide what amounts to 2 forms of identification and one of those should be "out of band", which simply means that the method you use to provide the extra information isn't linked to the method you used to provide your user name and password: Entering a code that the service sends to your cell phone, for example, or a series of numbers that change every 60 seconds from a security fob.
And despite the extra effort required, 2-factor authentication doesn't ensure absolute security. In the security business, "absolute" is a nonsense term. That said, adding the complexity of 2-factor authentication automatically takes the bottom-feeder crooks out of the game and limits the pool of potential attackers.
Persistent crooks could steal a physical device. Numerous books and movies involve thieves stealing a person's fingerprints (or fingers) to hack a biometric system. Sufficiently talented thieves could insert themselves at a location between you and the protected resource so that then can grab the authentication token that's intended for your computer.
And sometimes techniques that have been put into place to help users can also help crooks. Although many of the largest holes have been patched in various companies' password recovery processes, it's still possible for someone who knows enough about you to "recover" your password.
The biometric option is the most secure option now. Even though costs are dropping, biometric authentication is still too expensive for most systems, though. Besides making systems more secure, biometrics could make recovery easier in the event that the user misplaces a portable device or loses the device to a thief.
The second most secure option uses a device that plugs into a USB port on the device or displays a code that changes frequently. In the case of a device such as an RSA fob, the number that the user must enter is made up of parts: A prefix that the user must change every 30 to 45 days and the 6-digit code that changes every 60 seconds from the fob's display.
At right, an RSA key that I use to gain access to certain assets.
Devices such as this usually contain an accurate time source so that the authentication server can "synchronize" with the fob even though no connection exists. To account for minor time shifts over the life of the device, the authentication server will typically accept as correct either the current or immediately previous code, or the next code in the sequence. Display fobs need to include some amount of internal encryption to reduce the ability of a thief to dis-assemble the unit.
Magnetic-striped cards are still used in some cases, but the vulnerability of these cards has been illustrated clearly. As a result these cards have been discontinued by banks in most of Europe and will be eliminated in US banks over the next several years. They may still be used in other settings and new card readers can make existing cards more secure by analyzing and recording each use of the card on the card itself.
Smart cards may serve multiple purposes -- credit card, ID card, access card, and network authentication. In a corporate environment, these cards could be used to provide access to specific locations within an office and then be used with a card reader to give the user access to a computer.
The primary drawbacks to multi-factor authentication involve users' inability to keep track hardware tokens or USB plugs. Multi-factor authentication increases support costs and, if a hardware device is used, it also increases equipment costs. Whether the increased security is worth the extra costs will depend to some extent on what is being protected.
Except for banking and some government operations, multi-factor authentication isn't yet common. Increasingly, though services for consumers are providing at least two-factor authentication. These include services operated by Apple, Dropbox, Google, LastPass, LinkedIn, Microsoft, PayPal, Tumblr, Twitter, Yahoo, and many others. Typically, setting up two-step authentication is relatively easy and it involves visiting a settings panel, finding a security link, and modifying a selector.
Short Circuits
What's Cooler than an Apple Phone or Watch?
Apple introduced a new watch and an updated Iphone this week. They got most of the attention, but the real bombshell from Apple is a new payment method that has the potential to virtually eliminate credit cards. Credit cards are inherently lacking in security and Apple's new "Apple Pay" (not IPay) could change a lot of things.
At first glance it would seem not to be so secure. The user waves an Apple device at a payment device, enters a validation code of some sort, and the payment is made. What happens if the Apple device is lost or stolen?
The answer is easy: Because the finder (or thief) won't have the appropriate validation code, the device can't be used for payments. The user turns off the service for that device and that's it. There's no need to replace credit cards or do anything other than replace the phone. That's because the credit card information isn't stored in the phone.
When you make a payment, the Apple device will contact your bank and obtain a token. The token will then be passed to the store's payment device. That token is then presented to the bank for payment. Tokens may be used only once and nobody but you and the bank need to know your credit card number. That alone removes a large part of the risk.
Even if a thief gains access to the payment processing system at a store, the only information passing through the system is the single-use token. Once that token has been processed by the store, it would no longer have any value to a thief. Stores would be expected to process the tokens immediately, just as they do with other payment methods.
Amazon Fire Phones: 99 Cents
To say that the Amazon Fire hasn't sold very well is rather like saying the Titanic's initial voyage experienced minor problems with an iceberg. In an effort to sell the things, Amazon has dropped the price from $199 to 99¢. You still have to take a 2-year contract with AT&T, so even at 99¢ it might not be a great deal. Europeans don't get the full discount, though; they have to pay €1 and take a 2-year contract with a service provider.
But wait, there's more. You also get a year's worth of Amazon Prime (regularly $99). OK. Now you're talking. That might make the deal workable. And consider this, you would be the owner of a unique phone. After all, it's believed that only about 35 thousand Fire phones have been sold. Comments online, though, have not been kind with no small number of people saying that the Fire would be worth 99¢ only if it came with a year's worth of Amazon Prime and no service contract requirements.
The Fire fiasco should be a big embarrassment for Amazon. The phone was released in late July after thousands of employees worked on it over a 4-year period. The phone was expected to sell 1 or 2 million units in the first year, not 35 thousand. Amazon customer reviews of the phone are about uniformly divided between 4- or 5-star ratings and 1- or 2-star ratings. The most savage of the reviews come from people who say that they generally like Amazon products or had great expectations that weren't realized. More than 25% of those who rated the phone gave it just one star.
The Great Internet Slowdown Day
If you visited any websites on Wednesday, you may have seen the "loading" symbol a lot. Sites hadn't actually been slowed, but many of the larger players in providing Internet content were trying to raise awareness of what would happen if the Federal Communications Commission approves the creation of "fast lanes". FCC Chairman Tom Wheeler has adamantly said that the agency will never allow "slow lanes" without seeming to realize that establishment of "fast lanes" means that the rest of the Internet would be in de facto slow lanes.
The result: The event resulted in more than 2 million e-mail messages and more than 300,000 calls to Congress. Another 723 thousand pro-Net Neutrality comments were filed on the FCC's website and the site failed yet again. To say that the #NetNeutrality tag on Twitter was busy might easily be considered an understatement.
Overall, nearly 5 million comments have been filed with the FCC.
One of the event organizers, Free Press Action Fund President and CEO Craig Aaron, says “Internet users spoke out loud and clear on Wednesday. They’re united against FCC Chairman Tom Wheeler’s plan to allow fast and slow lanes on the Internet.”
Netflix has been a proponent of net neutrality because it doesn't want to pay "tolls" to broadband providers so that its video streams will be delivered smoothly. After sitting on the sidelines for a long time, Google has finally expressed support for the net neutrality concept this week and, in my opinion, it's about time.
