Windows 7: Right Operating System, Wrong Price
I'm one of those kooks who think that anyone who bought any version of Vista and lived with it for the past couple of years should get an automatic and free upgrade to Windows 7 Ultimate. I also think that Microsoft should offer only one version for workstations (Ultimate) and one version for servers. Instead, Windows 7 will be available in 6 editions, although only Home Premium, Professional, and Ultimate will be available for retail sale in most countries. But regardless of the price, Windows 7 is the right operating system if you're a Windows user. The code has been released to OEMs and boxes will be on store shelves in a little less than 2 months.
After the boondoggle that was Vista development and the problems Vista causes for users, Windows 7 shows that Microsoft can deliver a good product on time.
Actually, you can buy Windows 7 right now, but you won't receive it until after October 22nd. If you're willing to settle for the Home Premium version, you can buy a license for $150 and install it on 3 machines. Apparently there's some excitement in the marketplace, or possibly just extreme frustration with Vista. According to the UK branch of Amazon.com, pre-sales of Windows 7 exceeded, in just 8 hours, the sales of Vista in its first 17 weeks.
You probably know that I've been running the Windows 7 Release Candidate for the past several months on a notebook computer. I haven't installed it on the desktop system because upgrading from XP to Windows 7 requires formatting the disk drive and reinstalling everything. The upgrade from the Release Candidate version to the final full version will also require formatting the drive. For the desktop system, I prefer to do that just once.
There's lots of eye candy: Windows 7's user interface is quite attractive. But there's ear candy, too, with 13 additional sound schemes from Afternoon and Calligraphy to Cityscape and Festival, Quirky to Raga, and Savanna to Sonata.
A beta version of Virtual PC is available for Windows 7 Professional and above. This allows the user to run more than one Windows environment, including Windows XP Mode, on a single machine. XP Mode runs Windows XP and may help with applications that cannot be run in Vista today.
As important as what's in the new operating system is what you can turn off if you don't want it. If you don't want to use Internet Explorer, Windows Media Player, Windows Media Center, Windows Search, or the Windows Gadget Platform, you can turn them off.
One of the biggest changes, and one that took a little getting used to, is the absence of the Quick Start section of the Task Bar. Instead, you can pin applications to the Task Bar. If you’ve used Office 2007, you’ll recognize this as similar to pinning a document to the File menu. Pin an application to the Task Bar and its icon will be there permanently. Mac users will recognize this behavior from the Dock. At first, I thought I wouldn’t like this, but I find that I miss it when I’m using the desktop computer, which is still running XP.
At the right edge of the Task Bar, you'll find a rectangle. Hover the mouse there and all applications turn transparent so you can see the desktop. Click it, and all programs minimize. A second click restores everything.
During the 2 years or so that I tried to learn how to live with Vista, the shutdown process would sometimes take 10 to 15 minutes. The Windows 7 shutdown process is even faster than XP's. It's still not as fast as a Linux shutdown (10 seconds or less), but it's far better than with Vista.
The Windows 7 Release Candidate is no longer available for download, but you can still obtain a license key until the day before Windows 7 ships. The Release Candidate will expire on June 1, 2010. If you haven't installed a licensed version of Windows 7 by then, your computer will stop working.
How About Another Media Player for Your Computer?
"Timing," a friend likes to remind me, "is everything." For the past 6 months or more, I've been working on a report about the VLC Media Player. The product kept changing though. Finally, it reached version 0.9.9 and I concluded that version 1.0 would be along soon. It's here. VLC joins a bunch of other media players and they all want to be your best friend. Should you invite VLC inside to play?
It seems that everyone has a media player: There's Real Media's player (free and paid versions), Winamp (now owned by AOL, with free and paid versions), Apple's Itunes (free), VideoLAN's VLC player (free), and the DIVx player (free and paid versions). Some are primarily for audio, some are primarily for video, but most try to do everything. And they sometimes like to stab each other in the back.
 I like VideoLan's VLC media player. Not because it's free, although that's a welcome feature. Not because it plays nearly any CD, DVD, or media file I throw at it, although that's extraordinarily helpful. One of the primary reasons I like VLC is because it runs on my Windows machines, on my Macs (both universal and Intel versions are available), and on my Linux machines (available for the most popular distributions). You can even download the source code if you want to compile your own version.
I like VideoLan's VLC media player. Not because it's free, although that's a welcome feature. Not because it plays nearly any CD, DVD, or media file I throw at it, although that's extraordinarily helpful. One of the primary reasons I like VLC is because it runs on my Windows machines, on my Macs (both universal and Intel versions are available), and on my Linux machines (available for the most popular distributions). You can even download the source code if you want to compile your own version.
I've been using VLC for several years as it has progressed through its beta cycle.
Version 1.0.0 was released recently and followed almost immediately by 1.0.1. If you've ever struggled to play a file you downloaded from the hinterlands of the Web, you clearly didn't try opening it with VideoLan's VLC media player. That's another reason you should consider giving it a try.
VideoLAN is a volunteer project that releases its applications under the GNU General Public License. Its primary application is the cross-platform VLC media player. In addition to being a small, portable player for most audio and video formats from files, physical media, TV capture cards, and many network streaming protocols, VLC can also be used to convert media files, transcode, and act as a streaming server over unicast or multicast and IPv4 or IPv6. It doesn't need any external codecs to work.
That's saying a lot for any program, much less one that asks only for a donation if you like it.
Reasons for Liking VLC
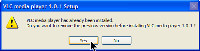 The reasons start the instant the installation process begins. If VLC notices that a previous version was present, it offers to remove it.
The reasons start the instant the installation process begins. If VLC notices that a previous version was present, it offers to remove it.
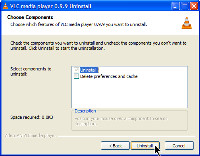 Because a previous version had been installed on my computer, VLC asked if I wanted to keep the existing preferences information. That way I wouldn't have to set up all the preferences from scratch.
Because a previous version had been installed on my computer, VLC asked if I wanted to keep the existing preferences information. That way I wouldn't have to set up all the preferences from scratch.
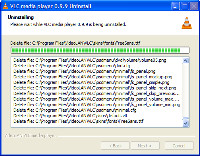 The removal process is quick, easy, and complete.
The removal process is quick, easy, and complete.
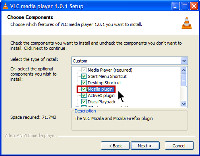 During the installation process, I noticed that VLC doesn't install the Firefox plug-in by default. This is uncommonly polite operation. I selected the option because I want the plug-in.
During the installation process, I noticed that VLC doesn't install the Firefox plug-in by default. This is uncommonly polite operation. I selected the option because I want the plug-in.
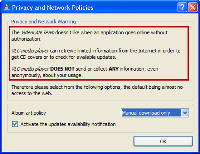 When VLC plays a file, it can check various Internet sources to see if artwork is available. By default, this is set to manual and the explanation says that the developers don't like it when an application goes on line without saying anything about it. This is yet another good example of proper programming technique: Ask the user.
When VLC plays a file, it can check various Internet sources to see if artwork is available. By default, this is set to manual and the explanation says that the developers don't like it when an application goes on line without saying anything about it. This is yet another good example of proper programming technique: Ask the user.
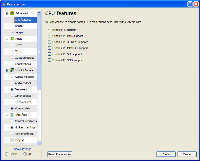 By default, the preferences panels ask only for the most essential settings and don't bother the user with a lot of questions that can be answered by audio engineers, video engineers, and networks engineers. However, if you do want to see all the settings (left) VLC shows them to you.
By default, the preferences panels ask only for the most essential settings and don't bother the user with a lot of questions that can be answered by audio engineers, video engineers, and networks engineers. However, if you do want to see all the settings (left) VLC shows them to you.
The entire set-up process (including downloading both Windows and Mac versions of the file, uninstalling the old version, and installing the new version) took less than 10 minutes.
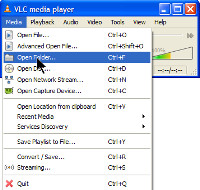 Now I was ready to listen to music, so I opened a folder and the music started playing.
Now I was ready to listen to music, so I opened a folder and the music started playing.
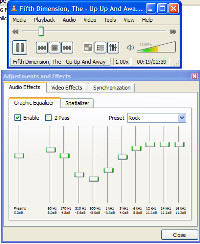 If you want to control the sound of the music, there's a 10-band graphic equalizer that you can set to suit your tastes and your audio system, or you can use one of the many presets.
If you want to control the sound of the music, there's a 10-band graphic equalizer that you can set to suit your tastes and your audio system, or you can use one of the many presets.
The audio controls are clear and easy to use, but what about video?
 I opened a disc with season 5 of the BBC's MI-5 spy series and the disc started to play. VLC includes controls for changing the color balance, gamma, and other video settings, but I've rarely needed to use them.
I opened a disc with season 5 of the BBC's MI-5 spy series and the disc started to play. VLC includes controls for changing the color balance, gamma, and other video settings, but I've rarely needed to use them.
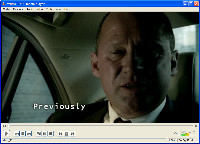 At the left is the opening scene from MI-5 season 5, episode 1. Because of the way video is handled by most video cards, creating an image such as the one at the left is impossible. I needed to combine the screen shot of the player, which had only a black screen, with a screen shot that VLC created.
At the left is the opening scene from MI-5 season 5, episode 1. Because of the way video is handled by most video cards, creating an image such as the one at the left is impossible. I needed to combine the screen shot of the player, which had only a black screen, with a screen shot that VLC created.
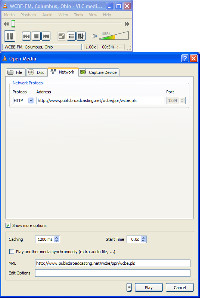 Streaming audio? Easy. I filled in the information provided by WCBE on its website and the audio immediately started to play.
Streaming audio? Easy. I filled in the information provided by WCBE on its website and the audio immediately started to play.
If you have a mixture of Windows machines, Macs, and Linux computers, you'll probably enjoy VLC because it's one of the few applications available that works the same on any of the 3 platforms.
I probably won't stop using Itunes and Winamp to listen to audio because both programs are better when it comes to organizing the audio files on my computer, but VLC is certainly the easiest way to watch just about any kind of video file.
And I haven't even talked about the additional abilities VLC has to transcode video files so that you can view a program on a portable device. Yes, there are still some legal questions about transcoding material from a DVD to view on a portable device, but one has to think that Congress and the courts will eventually determine that someone who buys a DVD and wants to watch the program while on a business trip really isn't violating the law by copying the program to a portable player.
 Bottom Line: VLC is one essential program if you watch videos on your computer.
Bottom Line: VLC is one essential program if you watch videos on your computer.
Open source, multi-platform, and multi-talented. VLC from VideoLan is an ideal option for video on the desktop.
For more information, visit the VideoLan website.
Say Goodbye to Spam from Web Forms
A Perl script called formmail is responsible for sending the output from a lot of Web-based forms to website owners. Unfortunately, though, the original formmail.pl is still in use on many websites. Having been written more than a decade ago by a high school student who was learning Perl, the original formmail omitted even the most basic security measures. NMS, a British group reworked the scripts early this decade, but stopped work on the project by about 2004. If configured properly, the new version cannot be used to send spam through your website to hundreds or thousands of victims. But the form can be compromised by spambots that fill out the form and submit it. I countered that weakness by installing a CAPTCHA (completely automated public Turing test to tell computers and humans apart) device, but spambot operators have found a way to get around that, too. Now I've shut them down.
The Perl script that parses the information from the form and sends me an e-mail is supposed to check the "referrer" (location of the form) and run its process only if the the referer is in my extremely short list of valid domains. It then has permission to send a message to one of three addresses. So spammers can't use the process to send spam to any address other than the 3 addresses known only to the script. And, although the script checks for the referrer, this is apparently not difficult to spoof.
As a result, I was receiving 50 to 100 spams per day, consisting of messages like this:
ContactProblem: gBB4Ay <a href="http://soxyqchduett.com/">soxyqchduett</a>, [url=http://wigmwrmqecny.com/]wigmwrmqecny[/url], [link=http://nuhqvujrinqv.com/]nuhqvujrinqv[/link], http://zlzvqvfcwrkj.com/ ContactEmail: nsfmos@dhdiev.com ContactName: tdziqs Validator: NesVGsOQnQPQ
What's with all the nonsense? The goal seems to be for the gullible to wonder what's with all the nonsense and click one of the links. Do that and bad things will undoubtedly happen to your computer.
The Easy Solution or the Right Solution?
I could have my e-mail program check for the presence of one of my validator words and, if the word isn't present, delete the message unread. But still this was 50 or more messages per day and, given the way spam works, I could foresee a day when the count would hit 1000 or 10,000 or 100,000. The time had come to stop it.
The CAPTCHA is processed by JavaScript, which has one very large shortcoming: It's visible to anyone who wants to look at it. The Perl script, on the other hand, wasn't. So that's where I had to solve the problem. Scripts, whether Perl or some other language, when used in this way are referred to as CGI (common gateway interface) scripts.
I knew that the zombie computers were filling in the form and submitting it, probably from a location on an infected computer. Submitting the form via the website would have failed because the JavaScript wouldn't allow a form with a validator of "NesVGsOQnQPQ" to pass, so the process was going around the Web form and directly accessing the CGI script. There were no validator tests in the CGI script, so it seemed that simply adding one there should do it.
There is a finite and easily changed list of valid words for the validator, so initially I started by defining all of the current possible words in the CGI script.
When the CGI script processes the form, it receives all of the information from the form in a series of "name-value" pairs. So the validator from the fake form above will arrive as a name ("Validator") and a value ("NesVGsOQnQPQ"). I'm certainly not a power programmer when it comes to Perl, but I know enough to be able to extract the validator value into a variable.
From there, all I have to do is compare the passed value of the validator to my list of valid words and, if the word isn't present in my list, the submission process just quietly ends. The Perl syntax for doing this is easy (and, no, I'm not going to show you my list of magic words or even tell you how long that list is):
my $spamcheck = $q->param('Validator') || '';
($spamcheck ne 'XXXXX'
&& $spamcheck ne 'XXXXX'
... (extra validator words be here)
&& $spamcheck ne 'XXXXX') {die};
Instead of 50 to 100 form-based spams each day, I now receive zero.
You might think that's the end of the story. I'd like to think so, but I suspect that spammers will eventually find a way around this. When they do, I'm already prepared with some possible modifications.
Instead of storing the validation terms in the CGI script, store them in a separate file that the CGI script can read. This would make them even more secure.
Encrypt the validation terms and decrypt them on the fly using a public/private key scheme to make it impossible for spammers to read them and get around the CGI validation.
If you want to know more about how this works, drop me a line (or use the contact form from the website).
Short Circuits
Reports from Our Correspondents
I've received message from readers who let me know about some questionable business practices.
The Never Ending Antivirus Program
Garth Edwards told me about a practice that I thought had all but disappeared. Referring to what he called a "somewhat underhanded approach by Symantec Norton Antivirus," Edwards notes that Symantec will automatically renew antivirus registrations year after year unless the customer specifically cancels it. This occurs "whether one has been using Norton antivirus or not." In other words, it's the old negative option that is still in use by some book clubs, although many have changed to a model by which they don't send anything or bill for anything unless the customer requests it.
I'm sure that Symantec covers this practice in the fine print of its licensing agreement and I'm sure that it's completely legal. Still, it would be more fair to the customer to ask the customer for a renewal and not just assume that the renewal is wanted.
My Internet service provider (BlueHost) has my credit card number on file. The renewal is automatic, but BlueHost starts warning me about the charge several weeks in advance.
The key here, it seems to me, is making sure that your customers know what to expect.
The Return of the Microsoft Firefox Plug-in
Rick Babgy reminded me of my report concerning Microsoft's unwanted and unneeded Net Framework plug-in for Firefox. Microsoft installed the plug-in automatically, without asking for permission and did so in such a way that removing it required a trip to the Registry editor.
Rick was surprised to find that the plug-in was back. "Recently, it happened again. Even though I have my machine set so that I have to check for the updates and then select the ones that I want, I found that my machine was updating anyway. So, I checked Firefox, and the rogue add-on was there again."
I checked my computer, too. Sure enough, there it was.
This time Microsoft at least got the installation process right. Instead of installing for all users this time, Microsoft installs for just the current user. So if you want to remove the Net Framework component from Firefox, you can do it in the normal way.
Some people cannot bring themselves to trust Microsoft and Microsoft seems to wonder why.
A Free Copy of Apple's Snow Leopard? Not Too Likely.
Unlike Microsoft, Apple is pricing the latest version of its operating system competitively, but that doesn't stop people from responding to offers of a free stolen version of the operating system. What do you get instead? You get a Trojan that changes your DNS server to something that will send your computer to Very Bad Places. Intelligent? Not exactly.
Trend Micro says several rogue sites are offering free copies of Snow Leopard, but if you're stupid enough to bite, you'll find that your machine is infected with OSX_JAHLAV.K, and that's just the beginning. The Trojan starts by changing your computer's DNS configuration to include new servers that will take your browser to phishing sites.
Supposedly pirated versions of Microsoft's still unreleased Windows 7 operating system have also been used to trick thieves into installing malware on their computers. Yes, I referred to the "victims" as "thieves". If you're honest, you won't get caught in this trap. But nearly 30,000 people downloaded the infected version of Windows 7.
The Snow Leopard Trojan is part of an OS X mountable disk image (DMG). Load it and the script will create a cron job that runs the malware every 5 minutes.
If you want Snow Leopard on your Mac, obtain it from Apple's website.
Free Computers for Governors
When several state governors received shipments of unordered laptops, the assumption was that they weren't being sent by anonymous benefactors hoping to improve governance. The FBI is investigating the mystery shipments. West Virginia, Wyoming, and Vermont officials acknowledge the shipments. Clearly the orders are fraudulent, but what's behind them?
The source of the machines is being investigated on the suspicion that they could be used to introduce malware into state networks.
It's not uncommon for thieves to "lose" CDs or USB drives outside business and government offices. Employees find the "lost" devices, take them back inside, and put them in their computers. Instant malware infection. With "netbook" computers costing only a few hundred dollars. So for just a few thousand dollars, crooks could stage a major break in.
How many other state or federal officials have received the computers? How many reported them? Are any currently in use somewhere? And are the machines being used as vectors for malware or are they just somebody's idea of a practical joke?


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
