Is Thunderbird Right for You?
The open-source Mozilla e-mail program Thunderbird doesn't offer all the flexibility of my favorite e-mail program (The Bat), but it is a full-featured e-mail application that should be a contender if you're thinking about migrating from older applications. Eudora, for example, hasn't released a new version since shortly after the most recent Ice Age and, despite claims to have version 8 "in beta" doesn't appear to be anywhere near launch. That's too bad because Eudora was my favorite e-mail program until shortly before 2000. If you're looking for something a bit more up to date, Thunderbird might be it.
 Although applications can add a variety of extensions and useful functions, the basic operation of any mail user application (MUA) will be the same. Wikipedia says "an MUA is only active when a user runs it. Messages arrive on the Mail Transfer Agent (MTA) server. Unless the MUA has access to the server's disk, messages are stored on a remote server and the MUA has to request them on behalf of the user."
Although applications can add a variety of extensions and useful functions, the basic operation of any mail user application (MUA) will be the same. Wikipedia says "an MUA is only active when a user runs it. Messages arrive on the Mail Transfer Agent (MTA) server. Unless the MUA has access to the server's disk, messages are stored on a remote server and the MUA has to request them on behalf of the user."
Setting up Thunderbird
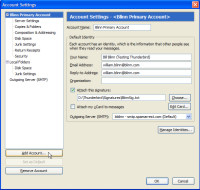 The first step involves setting up a connection between the MUA and the MTA. You need to specify the POP3 (or IMAP) server for inbound mail and the SMTP server for outbound mail. Every e-mail application will have these settings and each will want the same kinds of information.
The first step involves setting up a connection between the MUA and the MTA. You need to specify the POP3 (or IMAP) server for inbound mail and the SMTP server for outbound mail. Every e-mail application will have these settings and each will want the same kinds of information.
You'll be offered the opportunity to set up a default signature (as shown at the left) and to establish other settings and defaults.
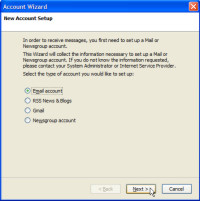 As with most MUAs, Thunderbird handles both e-mail and newsgroup communications, so you'll be asked to set up one or the other, or both.
As with most MUAs, Thunderbird handles both e-mail and newsgroup communications, so you'll be asked to set up one or the other, or both.
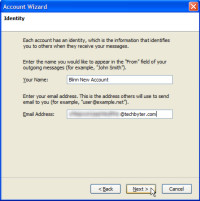 Next, Thunderbird will ask you to name the account. This should be a plain-English name, something that makes sense to you.
Next, Thunderbird will ask you to name the account. This should be a plain-English name, something that makes sense to you.
You'll also need to specify the e-mail address that this account will use.
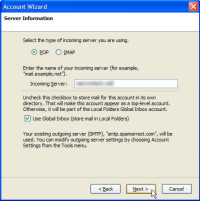 Then you'll need to specify the name of the server that delivers your incoming mail and specify whether it's a POP3 (post office protocol) or IMAP4 (Internet mail application protocol) server. POP is still the most commonly used server type, but IMAP is increasingly popular because it allows users to store messages on the sever.
Then you'll need to specify the name of the server that delivers your incoming mail and specify whether it's a POP3 (post office protocol) or IMAP4 (Internet mail application protocol) server. POP is still the most commonly used server type, but IMAP is increasingly popular because it allows users to store messages on the sever.
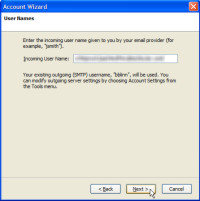 The next step will be to specify the user name. Depending on the server that holds your mail, this could be the first part of your e-mail address (the part before the @) or it might be the entire e-mail address. For some services, it might be another name entirely. Check with your system administrator to be sure.
The next step will be to specify the user name. Depending on the server that holds your mail, this could be the first part of your e-mail address (the part before the @) or it might be the entire e-mail address. For some services, it might be another name entirely. Check with your system administrator to be sure.
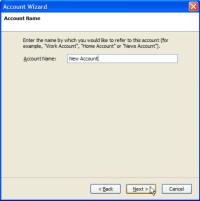 Then you need to give the account a name. This is another plain English name, something that makes sense to you. The computer, the servers, and Thunderbird don't case what you use here.
Then you need to give the account a name. This is another plain English name, something that makes sense to you. The computer, the servers, and Thunderbird don't case what you use here.
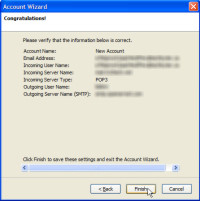 Thunderbird will now show you what you've set up so far. At this point, you'll be able to receive mail, but not send anything. Sending mail requires a simple mail transport protocol (SMTP) server, and that's what you'll be asked to set up next.
Thunderbird will now show you what you've set up so far. At this point, you'll be able to receive mail, but not send anything. Sending mail requires a simple mail transport protocol (SMTP) server, and that's what you'll be asked to set up next.
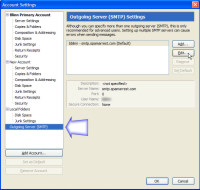 The SMTP server is one that you'll want to keep under close control. That's because you don't want a spammer to discover the server settings and start sending spams from your address.
The SMTP server is one that you'll want to keep under close control. That's because you don't want a spammer to discover the server settings and start sending spams from your address.
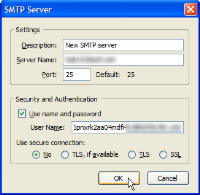 In the next dialog box, you'll want to specify a server name (plain English, for your use) and the name of the server, which will look something like smtp.server.com. The port will typically be 25 or 625 and you should set up authentication for sending mail. Many servers today require authentication and those that don't probably will within the next couple of years. You may note that my user name is rather long and cryptic. This is intentional.
In the next dialog box, you'll want to specify a server name (plain English, for your use) and the name of the server, which will look something like smtp.server.com. The port will typically be 25 or 625 and you should set up authentication for sending mail. Many servers today require authentication and those that don't probably will within the next couple of years. You may note that my user name is rather long and cryptic. This is intentional.
 My password is equally long and cryptic.
My password is equally long and cryptic.
That's all that's required to set up Thunderbird or any other mail user application. A surprising number of people seem to be befuddled by what should be a relatively simple process. E-mail is the oldest protocol on the Internet and the set up process isn't complicated.
Don't let the terminology intimidate you because the process overall is both logical and easy to understand.
75% of Computer Users Spurn Protection
Maybe "spurn" is too strong a word. Most people probably don't reject computer backup with contempt. But most people don't backup their systems or back them up so infrequently that they might as well not be backing them up. The Diffusion Group (TDG), a research organization, says that more than 16% of computer users never back up their computers. About 38% do a backup once or twice per year and just under 21% perform a monthly backup. Would it bother you if you lost all of the files you have created or changed in the past month, six months, or year? Would it bother you to lose everything that's on your computer?
The numbers from TDG are nearly 4 years old, but there's nothing to suggest that people have suddenly changed their attitudes toward backup.
I've described my process: An attached USB drive that keep a daily (or more frequent) copy of every file I'm working on. This is good for quick recovery, but useless as protection against a thief or a fire. I also keep a full backup on external hard drives that I store at the office. I'm supposed to update these once per week, but rarely do (and shame on me). But I also use Carbonite, the on-line backup service that costs less than $50 per year to store all the files on my computer. I really don't like the idea of having to recreate any of my work and some of the files on the computer (photos from the Ohio State Fair, for example) simply cannot be replaced.
TDG says about 11% of users backup their data once per week, a little more than 4% backup files several times per week, and just under 3% backup files once per day. Oddly, almost 7% of the people who replied to the survey said they weren't sure. How can you not be sure if you're backing up your computer?
In 2005, 61% of those who did backup their data said they used CDs, 27% said they used DVDs, and 33% copied content to an external hard drive. At that time, only 6% were backing up to an online storage service, 9% (probably office workers) copied files to a server, and 8% used network-attached storage (NAS). I would expect the number of people backing up to CDs today would be 10% of less. DVD usage is probably up, but it should be down. I hope that more people are using online services or at least external hard drives that they store in another location.
The survey included 1100 broadband Internet users nationally.
What's on Your Computer?
It's not surprising that most of the data on your computer isn't active. By that, I mean that you probably haven't accessed it (looked at it, listened to it, read it, or edited it) for at least 6 months. After all, how often do you open the directory with family pictures from 1999? But would you miss them if they were no longer there? Because many people no longer have prints made, I have to think that most people would be more than mildly annoyed if all of their images disappeared.
That's why backup is important and it's why I consider multi-part backup essential.
The local "hot backup" drive is handy and fast, but it's not secure. A thief, a fire, a tornado, or an earthquake could take out both the computer and the adjacent backup. Yes, earthquake; Ohio is in the expected "major damage" area the next time the New Madrid fault goes.
And as much as I like online storage, I know that recovery will be slow because of the download speed. Some providers limit the data you can store, most are not responsible for lost content, and you're depending on a company that could be acquired or go out of business with little warning. I consider Carbonite to be my safety net.
The fastest and most secure backup is an external hard drive that you store in a building that's at least several miles from your computer. You will need to transport this device to your computer and perform the backup at regular intervals and that's the primary disadvantage: It requires your active participation.
DVDs can play a part, too. Critical current working files could be backed up regularly to DVDs that you store in a secure location.
Be Careful Where You Store Discs and Drives
Some backup programs can encrypt data. If yours does, then you don't need to be too concerned about where you store the media or the device. The location should be secure, of course, because you don't want to find that they're no longer around when you need them. But you won't have to be too concerned if you lose a DVD or even an entire hard drive because nobody will be able to read the drive.
And don't store drives or discs in a "fireproof" safe thinking that they will survive a fire. They won't. Fireproof safes are rated based on their ability to preserve paper. Paper can withstand relatively high temperatures for long periods. CDs, DVDs, and electronic gear cannot. Following a fire, unless you've purchased a very expensive fireproof safe that's rated for electronic media, you're likely to find little more than a solidified blob of plastic that was once a stack of DVDs. Store them in a bank's safe deposit box.
Windows 7 Packages and Prices
Windows 7's release date is approaching and Microsoft has announced the final packaging and pricing schemes. There are still too many choices and the price is still too high, particularly in light of Apple's sub-$50 upcoming new version and the even lower price ($0) of Linux distributions. Microsoft has announced a Windows 7 "Family Pack" that will allow the Home Premium version of the operating system to be installed on 3 home computers for $150. What if you want the Professional or Ultimate version? And that special price will be available only "while supplies last". As if Microsoft is going to make only a limited number of copies of the software.
As for versions, there are still 5: Starter, Home Basic, Home Premium, Professional, and Ultimate. And if you buy one but later realize that you need one of the more complete versions, you can have it. All you have to do is fork over another $80 to $130. Is that per machine or does this apply to the "Family Pack"?
Microsoft is sometimes unjustly accused of stealing ideas from Apple, but here's one I wish they would steal: If you make an operating system, make an operating system. Just one. When somebody wants to buy your operating system, you sell them your operating system, not just a piece of it.
Buy one of those cute little netbook computers with Starter and you can use the "Anytime Upgrade" feature by paying another $80 and Microsoft will send you ... ... don't get ahead of me here and think that Microsoft will send you a DVD with the new operating system on it. No, nothing like that. Microsoft will send you a code that will unlock the Aero and Media Center features that will already be on your computer, but not yet activated.
Thus it appears that OEMs will be able to play the same kinds of silly games that Microsoft let them play with Vista. Put a crippled version of the operating system on a computer, label it "Windows 7", and don't tell anyone that to get the functions they think they're buying they'll have to pay another $80.
A Vista Upgrade
Worse still, there's no easy way to get from Windows XP to Windows 7. If you've been suffering with Vista for the past few years, Windows 7 will install as an upgrade.
But if you have stuck with Windows XP, the only ways to leap from XP to 7 involve either formatting the drive, installing Windows 7, and then reinstalling all of your applications; installing Windows 7 to dual boot with Windows XP; or buying a new computer.
Thanks for thinking of your customers, Microsoft.
Short Circuits
Twitter and Facebook Were Briefly Silenced This Week
Some technology-unaware reporters said that Twitter had been "hacked", but that wasn't even close. Instead, a denial-of-service (DOS) attack made Twitter inaccessible for several hours. The attack appears to have originated in Russia or Georgia. Facebook had problems, also, but it was less clear what caused those.
A DOS attack usually uses hundreds or thousands of zombie computers to send bogus signals to the target, Twitter in this case. The victim's server, not knowing which requests for service are legitimate and which are from botnets, tries to respond to all the requests and grinds to a halt. Network engineers can eventually filter out the bogus requests, but doing so can take hours.
In this case, though, the attack was by means of spam e-mail messages and may have been the result of a political battle between Russia and Georgia, with each side trying to silence the other side's "propaganda".
Also on Thursday, Facebook saw service disruptions that resulted from a DOS attack, but full service was restored in a few hours.
No Apples for Google CEO Eric Schmidt
With competition heating up between Google and Apple, Google CEO Eric Schmidt has resigned from Apple's board of directors. The two companies are each in the mobile phone market. Both are in (or soon will be) in the operating system market. Schmidt and Apple CEO Steve Jobs are friends, but Schmidt said that he found that was increasingly having to recuse himself from votes on corporate issues.
The departure wasn't a surprise. The collision course has been clear for months and the Federal Trade Commission has been investigating the close relationship between Apple and Google with regard to antitrust laws. Earlier this week, the Federal Communications Commission said it was investigating Apple's rejection of the Google Voice application for the Iphone.
Google wanted to allow Iphone users to bypass AT&T's cellular network and communicate via the Internet using voice-over-IP technology. Apple didn't like that idea and took measures to block it.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
