The Many Faces of Fraudulent Spam
My e-mail inbox leads a sheltered life. Because I use a challenge-response system that sits on a server in Seattle, it never receives any spam. None. But because I like to see what the fraudsters are up to, I use a couple of mechanisms that sequester all spam in a kind of litter box. Occasionally I'll take a look to see what's in the litter box and pull out some of the larger clumps to examine them. They range from sublime to absurd. Sometimes the spams suffer from thesaurusitis, the same thing that gets high school sophomores in trouble when they seek out elegant variations to common words, make the wrong choice, and write a sentence without sense.
Click any of the images here for a full-size view.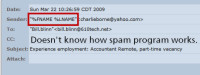
Whenever I see a spam that lists a return address such as this, I have to take a look because I know it will be a garden full of cluelessness: %FNAME %LNAME <charlieborne@yahoo.com>. Clearly the spammer doesn't know how to use his own spam program. The variables should have been replaced with an actual name, not printed as is in the message.
Here's the full text of the message that was titled "Venerable Insurance". I have market the particularly clueless sections this way and [my comments look like this]:
A venerable insurance company within the underlying market of operation, is proud to announce yet another feasible entry for uprising accounting adepts. [This sentence has so many problems that it's hard to tell where to begin. I have no idea what an "underlying market of operation" is and I probably wouldn't want to meet any "uprising accounting adepts" in a dark alley.]
Comfort working environment will most definitely justify the necessity to excel in the vast sphere of professional goals, and thereof lay a firm foundation for your career advancement. ["Thereof" should be "thereby", but the rest of the sentence is pure gibberish.]
Salient associates, with profound work knowledge, will assist you in unwrapping avocation related techniques, which will best integrate with the development and popularization of high-caliber insurance solutions. [The writer seems to pick random words from a thesaurus and sprinkle commas with equal randomness.]
Feel free to consider the prerequisites table right below, to amass the important information.
-- This is part time work at home position and can easily combine this vacancy with other work. [Missing something here is, believe I.]
-- Your education and status don't matter. [Sure they don't. If you had any question about the legitimacy of this "offer", you should by now be completely disabused of them.]
-- You will receive payments (Direct Bank Deposits and wire transfers) from client within United States and send it by instant payment sistem such as Western Union. You will receive 5% of processed amount. [The message is now shouting "fraud" and even spelling "system" right wouldn't help much.]
-- To start work with us you must only have basic checking account at any bank. Your financial information will never be disclosed to third parties. [At last, two complete and more or less correct sentences!]
-- You can work 2-3 hours per day.
-- This is not insurance sales position and you don't need to sell insurance, this is Money Transfer Assistant vacancy. [Why would any "venerable" insurance agency need a "Money Transfer Assistant"? Don't they have accounting departments for this kind of thing?]
-- You do not spend your own money and there are no startup fees. All charges for withdrawal or transferring the money will be deducted from the payment.
-- We do not ask any personal information and we run business according to laws of the United States of America. [I should hope so because your telephone area code claims that you are in Arizona.]
-- Your fixed salary is 2000 USD a month + 5% from each payment processed by you. [$2000 per month for 2-3 hours per day? Dream on.]
-- The main responsibilities will be to fill forms, receive and transfer money from our clients at the United States to our couriers.
-- WE ARE HIRING ONLY AT THE UNITED STATES, PLEASE DO NOT REPLY FROM OTHER COUNTRIES. [What's the deal with this "at the United States" phrase?]
If you want to apply please send all your questions and contact information at HRManagerPIC209@gmail.com . We're looking forward to our further communication. [And here's another misplaced "at" instead of "to". I see that the "venerable insurance company" uses a Gmail address, too.]
Phone: (520) 762-7351
Fax (520) 844-0888
Julie Mathews. HR department.
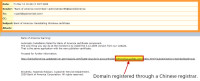 The Bank of America tells me that the security certificate installation failed.
The Bank of America tells me that the security certificate installation failed.
The only thing I can do to remedy this situation is visit the Bank of America site and download the appropriate file. This might be slightly more convincing if I actually had any banking relationship with the Bank of America.
The URL tries its best to look convincing by starting with "http://bankofamerica", but there's more. A lot more: "updateserver.permissions.certificate-dcy1ibnjx.accountholde". What most people won't see is the rest of the URL.
The next part is "technologyupdtas.com/index.html/?subject/action=5oerd2dksetmx4o", so the domain you'll actually connect to is not "bankofamerca.com", but "technologyupdtas.com".
Would it surprise you to learn that technologyupdtas.com is registered in China?
The "Avant-guard" Advertising Agency wants to offer me a "job position". First rule for spamming: If you're going to use a term such as "avant-garde", at least spell it right. The message is at least written in passable English.
My name is Erick Krusini, I'm HR manager of Avant-guard Advertising Agency. I would like to offer you a job position in your area according with your skills and experience level.
Our system found you as a potential candidate for the following job vacancy:
Junior Service Manager
If you are ambitious and would like to work in an interesting business, open up something new to yourself, to climb up the professional ladder and gain a new experience, come to work in our company! Our specialists will always support and give professional help during your first steps. [You're on your own later, though, buster!]
Tasks:
Processing orders(sales) from clients and their partners;
Following security procedures;
Drawing up reports (Ms Word; Ms Excel). [Who are Ms Word and Ms Excel? Will I be working with them?]
Requirements:
High School diploma or equivalent required.
Proficient in computer window-based programs with excellent navigational skills. [Microsoft, Apple, Linux, and Unix all have "window-based" programs. I wonder why I'll need excellent navigational skills. Will they be moving the office frequently and expect me to find them?]
Ability to multi-task.
Good documentation abilities.
Effective dealing with deadlines
Strong organizational and problem solving skills.
Compensation:
Base Pay: $40,000–$60,000 /Year - monthly paid salary $3,000/month. [Make up your mind. Is it $40-60K per year or $36K per year?]
Other Pay: Generous commission program - extra income per each completed task.
Telecommuting is ok.
Principals only. Recruiters, please don't contact.
If you are ready to apply, please fill in the following form:
http://guard.co.cr/careers.html [CR is the domain for Croatia.]
(Sorry we do not answer on email reply, please fill form)
You will get all necessary information regarding this position.
For your privacy and protection, when applying to a job online:
Never give your social security number to a prospective employer.
Yours Sincerely,
Erick Krusini
Human Resources Manager
Avant-guard Advertising Agency [Consistently wrong.]
It seems that I've bought an airline ticket from Delta.
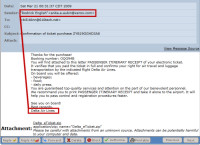 Thanks for the purchase! [Besides knowing that I hadn't purchased a ticket from Delta, I thought it was interesting that messages from Delta are processed by Xerox. Has there been a merger I'm unaware of?]
Thanks for the purchase! [Besides knowing that I hadn't purchased a ticket from Delta, I thought it was interesting that messages from Delta are processed by Xerox. Has there been a merger I'm unaware of?]
Booking number: OQG94B
You will find attached to this letter PASSENGER ITINERARY RECEIPT of your electronic ticket. [The attached zip file undoubtedly contains malware of some sort. I did not open it.]
It verifies that you paid the ticket in full and confirms your right for air travel and luggage transportation by the indicated flight Delta Air Lines. [This is a 2-pronged hook: If you're honest, you might open the file to see if you could reunite the ticket with its rightful owner. If you're not honest, you might open it to see if you could use the ticket or cash it in.]
On board you will be offered:
- beverages;
- food;
- daily press. [How long is this flight!? Do they mean "newspaper"?]
You are guaranteed top-quality services and attention on the part of our benevolent personnel. [Can you imagine any airline calling its employees "benevolent"?]
We recommend you to print PASSENGER ITINERARY RECEIPT and take it alone to the airport. It will help you to pass control and registration procedures faster. [The writer clearly knows English as a far-distant second language. Mistaking "alone" for "along" is particularly amusing.]
See you on board!
Best regards,
Delta Air Lines
Libraries: High Tech and High Touch
I’ve always liked libraries. From whenever it was that I discovered the boxy little library in Bellefontaine to today, when I’m surrounded by libraries that provide access to books, CDs, DVDs, electronic books, online databases, and more. It’s hard to imagine a world without libraries and I know that I wouldn’t want to live in such a world. This is mainly about central Ohio libraries, but what's true here is true for many libraries in most parts of the country.
The largest library system in central Ohio is, of course, the Columbus Public Library, the mainstay of the Discovery Place system that unites several libraries. But other libraries are available, too: Bexley, Upper Arlington, Grandview Heights, and Westerville, to name just four.
Worthington’s library was named Library of the Year in 2007. It’s a busy library, but so are many of the libraries in this area.
No Longer Marian the Librarian
In The Music Man, Marian the librarian is a quiet, mousy person. Maybe librarians were once like that, but no more. Librarians are likely to know more about technology than you do. I know that because several librarians attended a conference I attended 10 years or more ago. If I had any preconceived notions of librarians, this conference blew them away.
The conference topic was website design and the presenter mentioned that not everyone had up-to-date equipment. Librarians, he cited as an example. One of the librarians in the room set him straight: The library had a faster connection than most of us in the room and the librarians knew how to use it.
So there.
And, as for mousy, some of the librarians I deal with have tattoos and piercings. It’s no longer Marian. When I was looking for a Perl reference late in 2008, I wasn’t sure which terminals had access to the catalog, so I asked a librarian to direct me. She said that she could look it up for me. “Perl,” I said. “Bailey, knitting, or the computer language?” she asked. No, definitely not prim little Marian. Actually, I have a feeling that most librarians never really quite fit that stereotype, anyway.
The fact is that librarians have always been underrated. A very long time ago, WCOL Radio had a program segment that answered questions. I was one of the people who researched the answers, but I cheated most of the time. When a question came in, I picked up the phone and called a research librarian at the Columbus Public Library. In many cases, the librarian knew the answer. If not, she (and in the 1960s it was almost always “she”) could find it.
That was before the Internet was in every home. Well before Google. Finding answers meant looking in books. Research librarians are still some of the coolest people on the planet.
An outgrowth of the research department is the “homework help” section. Librarians won’t do children’s homework for them, but they can provide suggestions about how to perform the appropriate research and find the right answers.
Libraries Offer More than Ever
Google can’t answer every question. Your local library has access to many online databases. You can use these resources at the library and, in some cases, you can even use them at home if you have a library card for the library. Some databases are restricted and are available only on terminals at the library.
You may also find electronic books that you can download or read online. Audio books can be checked out from your library or you may be able to download them and listen to them at home. In a few cases, you’re even permitted to create your own CDs from audio book downloads. Some libraries offer video downloads, too, in addition to DVDs that can be borrowed.
Franklin County Choices
Although many people think that they are limited to using just the library where they live, this isn’t true. I may live in Worthington, but I also borrow materials from the Grandview Heights and Upper Arlington libraries because I can easily visit them on the way home from work. You do need to obtain a library card from the other library systems, but this is not a problem.
Click any of the images here for a full-size view.
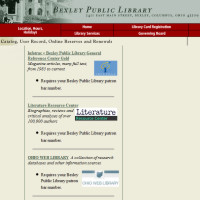 Bexley: “[A]nyone who resides, attends school, or is employed within Franklin County, Ohio may obtain a Bexley Public Library borrower’s card. For more information, see http://www.bexlib.org/.
Bexley: “[A]nyone who resides, attends school, or is employed within Franklin County, Ohio may obtain a Bexley Public Library borrower’s card. For more information, see http://www.bexlib.org/. Columbus: “You must be an Ohio resident to register for a library card.” For more information, see http://www.columbuslibrary.org/. Columbus, Worthington, and the Southwest Public libraries all share the same catalog and any book available at any library can be sent to a library near your home or office for pickup. The Columbus system has 23 branch locations.
Columbus: “You must be an Ohio resident to register for a library card.” For more information, see http://www.columbuslibrary.org/. Columbus, Worthington, and the Southwest Public libraries all share the same catalog and any book available at any library can be sent to a library near your home or office for pickup. The Columbus system has 23 branch locations. Grandview Heights: “Any resident of the State of Ohio may register for a Library card in order to borrow Library books, DVDs, and other materials and to use our online resources.” For more information, see http://www.ghpl.org/. Grandview Heights is part of a library consortium that includes libraries in Fairfield County, Marysville, Pickaway County, Pickerington, Plain City, Wagnalls, and Alexandria.
Grandview Heights: “Any resident of the State of Ohio may register for a Library card in order to borrow Library books, DVDs, and other materials and to use our online resources.” For more information, see http://www.ghpl.org/. Grandview Heights is part of a library consortium that includes libraries in Fairfield County, Marysville, Pickaway County, Pickerington, Plain City, Wagnalls, and Alexandria. Upper Arlington: “Verification of current address is required. (You must be an Ohio resident.)” For more information, see http://www.ualibrary.org/.
Upper Arlington: “Verification of current address is required. (You must be an Ohio resident.)” For more information, see http://www.ualibrary.org/. Westerville: Not specified. For more information, see http://www.westervillelibrary.org/.
Westerville: Not specified. For more information, see http://www.westervillelibrary.org/. Worthington: “Personal cards are issued free of charge to individuals who are Ohio residents.” For more information, see http://www.worthingtonlibraries.org/.
Worthington: “Personal cards are issued free of charge to individuals who are Ohio residents.” For more information, see http://www.worthingtonlibraries.org/.
As a library card holder, you have access to every online database that the library subscribes to (illustrated above). A few of these require you to be in the library to use them, but most are available from home, 24 hours per day, 7 days per week. As the Upper Arlington Public Library’s website says, “Our online databases & reference Ebooks provide access to thousands of respected magazines, newspapers, and professional journals—plus business and investment, science, history, literature, and genealogy sources. They provide information you can’t find by simply doing a Google search.”
 Bottom Line: Libraries are probably the best value you'll find anywhere on the planet, if not in the entire solar system.
Bottom Line: Libraries are probably the best value you'll find anywhere on the planet, if not in the entire solar system.
Libraries have kept up with technology. No longer just repositories of books, magazines, the occasional fine-art print, and a few albums or films, your public library provides CDs, DVDs, online database access, and more.
For more information, visit one or more of the library websites shown above or a library in your part of the world and see what resources are available to you.
A Protocol Languishes and Nobody Seems to Care
On Wednesday of this coming week, it will have been 19 years since RFC 1149 was proposed to ease network traffic and shamefully slow implementation has resulted in virtually no action being taken on what was viewed as an exciting new development in 1990. "RFC" is an initialism for "request for comments". RFCs are what provide guidance for the Internet. For example, RFC 821 describes SMTP, the simple mail transport protocol (67 pages that describe how e-mail should be transported) and RFC 2161, the hyper-text transfer protocol (176 pages that describe the basics of how the Web operates). By contrast, RFC 1149 is just 2 pages long and still it languishes. Why?
Nine years later, in 1999, RFC 1149 was updated by RFC 2549, which added new features to make the proposed protocol even more robust. Astonishingly, no action was taken then. And now, 10 years after the second proposal, there is no indication that the protocol will be developed anytime soon.
RFC 1149's language was simple and straightforward. What was being proposed was "A Standard for the Transmission of IP Datagrams on Avian Carriers," described as an experimental method for the encapsulation of IP datagrams in avian carriers, which would be "primarily useful in Metropolitan Area Networks." RFC 2549 updated the proposal to include the ability to indicate service level "on a per-carrier basis by bar-code markings."
The 2-page original RFC was simple and direct: "Avian carriers can provide high delay, low throughput, and low altitude service. The connection topology is limited to a single point-to-point path for each carrier, used with standard carriers, but many carriers can be used without significant interference with each other, outside of early spring. This is because of the 3D ether space available to the carriers, in contrast to the 1D ether used by IEEE802.3."
Security of the new protocol was given careful consideration, "Security is not generally a problem in normal operation, but special measures must be taken (such as data encryption) when avian carriers are used in a tactical environment."
The time has come to implement RFCs 1149 and 2549! Write your congressman or senator. Demand that the United States government move forward immediately on these important protocols!
Before writing, please check the references:
RFC 1149
RFC 2549
Calendar (In particular, note next Wednesday's date.)
Nerdly News
Finding Security by Looking for Vulnerabilities
Find a browser bug and collect $5000. That's the basis of a contest held recently by CanSecWest in Vancouver. CanSecWest is a security conference in, well, the western part of Canada. This was the 10th annual conference and it's billed as "the world's most advanced conference focusing on applied digital security." The conference included a "Pwn2Own" contest. That would be leet-speak for "own to own": If you write an exploit that "owns" the machine, you earn $5000 and you own the laptop computer used for the contest.
The winner was a German guy known only as "Nils". He presented 3 new exploits, 1 each for Firefox, Safari, and Internet Explorer.
Ease of use is paramount for a browser and, because of that, security sometimes must sit in the back seat. But even if security was paramount, there would still be flaws because programmers write imperfect programs and because browsers are exposed on the Internet for every crook in the world to play with.
You might think a conference such as CanSecWest, which brings hackers together to compare notes, is a bad thing. It's not. The truly bad folks find security problems and share them. Conferences such as CanSecWest help to uncover security flaws and then report those flaws to the vendor. In Microsoft's case, the flaw that Nils revealed was patched the next day when Microsoft released the first non-beta version of the browser.
Nils took home the Sony Vaio notebook used at the conference, along with $5000 each for the flaws he demonstrated in Safari, IE, and Firefox.
The hacker, a student at a German university, didn't release his last name because he wanted to avoid being sought out by criminals who would want to buy information about his exploits. He did explain, though, that he found it a lot easier to write the exploit for Firefox or Safari on the Mac's OS X than on Windows Vista.
Yes, you did read that correctly: Vista was significantly more secure than OS X. Nils says that he expects more exploits to be written specifically for the Mac as Windows users migrate to Vista or (more likely) to Windows 7 when that version of the operating system is released.
A word to the Mac wise: You have been warned.
Router Botnet: End of the World or No Big Deal?
Based on what's been written on some blogs and in the "old media", too, a botnet that takes over some routers spells the end of the Internet as we know it. Drone Blacklist has been on the receiving end of distributed denial-of-service attacks from these corrupted routers and it's the company that announced the presence of the router-borne botnet. Drone isn't particularly concerned about the threat, though, and says that the botnet seems to have been taken out of service.
When every possible exploit becomes "the end of the Internet as we know it", the noise level increases. When the noise level increases, legitimate messages are lost in the clutter. It's the Chicken-Little syndrome. Every time you hear that the sky is falling and then the sky doesn't fall, you become a bit less likely to pay attention to the next warning.
I sincerely wish that those who write about technology (and that includes SlashDot) would be a bit more careful about what they write.
"Little-endian" is an arcane concept that refers to the way numbers are stored in computing devices. Given a 32-bit hex number such as 1A2B3C4D, a little-endian system would store the least-significant digits (4D) in the lowest memory location and the most-significant digits (1A) in the highest memory location. In a linear representation, the number would be stored as 4D3C2B1A. There is no inherent advantage to little-endian or big-endian, but the same system must be used by all processes accessing the memory.
As Drone Blacklist describes the problem on its website, your router would be vulnerable only if it's a mipsel device (MIPS running in little-endian mode), if it presents an SSH or Web-based interface to the WAN, and if you have a weak user name and password or the firmware is exploitable.
In short, "90% of the routers and modems participating in this botnet are participating due to user-error (the user themselves or otherwise). Unfortunately, it seems that some of the people covering this botnet do not understand this point, and it is making us look like a bunch of idiots."
Those devices that have been compromised can be easily disinfected: "[S]imply power cycle your device and take appropriate action to lock it down, including the latest firmware updates, and using a secure password."
There, now. That wasn't so bad, was it?
Podcast Audio Modifications
If you listen to the podcast, you may notice some changes this week. Earlier this year, I added some reverb to the signal. Subtlety has never been a strength for me and I've been told that the settings were too high. I have to agree with that assessment. Starting this week, I've dialed the reverb back considerably so that it will do what it's intended to do: Give some presence to the sound without making it appear that I've fallen down a well.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
