Listen to the Podcast
19 August 2022 - Podcast #806 - (20:11)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
One of the best things about digital photography is that individual images cost nothing, but that's also a huge problem. Even amateur photographers routinely amass digital photo archives with tens of thousands of images and sometimes hundreds of thousands. Finding one particular image can be nearly impossible.
Professional photographers, especially those who are old enough to remember film, have organizational methods that include dates and names. Possibly locations. Perhaps even other indicators. Adobe's Lightroom Classic is a fine organizer, but two applications from Excire makes the process of categorizing images easier so that they can be found quickly.
Excire Search is a plug-in for Lightroom Classic and Excire Foto is a standalone application. I wrote about an Excire Search update in September of 2020. The plug-in's operation and characteristics are about the same today as they were in 2020, but Excire Foto has received a significant upgrade.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
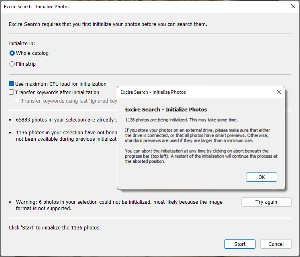 But let's take a quick look at Excire Search, first. When the application has been installed, it runs when Lightroom Classic starts. When you add photos, it's important to run the Excire initialization process. It had been several weeks when I ran the initialization process and more than 11 hundred images were new. The initialization process took only a few minutes. Excire Search does not catalog files in certain uncommon formats, gigantic files that are usually edited versions of existing photos, and any photos for which you've had Lightroom create virtual copies. Excire Search adds its own key words to any key words that you have already assigned to photos.
But let's take a quick look at Excire Search, first. When the application has been installed, it runs when Lightroom Classic starts. When you add photos, it's important to run the Excire initialization process. It had been several weeks when I ran the initialization process and more than 11 hundred images were new. The initialization process took only a few minutes. Excire Search does not catalog files in certain uncommon formats, gigantic files that are usually edited versions of existing photos, and any photos for which you've had Lightroom create virtual copies. Excire Search adds its own key words to any key words that you have already assigned to photos.
 When it's time to use Excire Search, you can provide one of your photos or an external photo for comparison, or search for people, faces, or keywords. If I want to look for pictures of pies, I could (1) select a photo of a pumpkin pie, (2) open Plug-in Extras from Lightroom's Library menu and select Search by Example Photo, and then (3) choose whether to give preference to the photo's content or color, set how restrictive the search should be, choose whether to search the entire catalog or just photos in the film strip, and set the maximum number of files to view.
When it's time to use Excire Search, you can provide one of your photos or an external photo for comparison, or search for people, faces, or keywords. If I want to look for pictures of pies, I could (1) select a photo of a pumpkin pie, (2) open Plug-in Extras from Lightroom's Library menu and select Search by Example Photo, and then (3) choose whether to give preference to the photo's content or color, set how restrictive the search should be, choose whether to search the entire catalog or just photos in the film strip, and set the maximum number of files to view.
The resulting search (4) returned 250 photos including a lot of pies and quite a few pumpkin pies, but there were also other photos that included round objects including a hamburger and even at cat. Excire's artificial intelligence is excellent, but it's not perfect. This should not be a surprise. Perfect or not, the process will usually find the photo you're seeking faster than you could find it manually.
At its most basic, the application is photo management software that categorizes photos and assigns keywords to them. The objective is to help photographers find photos faster. Excire Foto analyzes photos quickly and uses very little disk space.
I uninstalled a previous version of Excire Foto so that the new version would have to examine every photo on the disk. Adobe Lightroom Classic can create sidecar files for any proprietary file formats such as those from Canon, Nikon, and Sony cameras. The sidecar files duplicate information that Lightroom stores in its own catalog file, but I consider these files to be a necessary backup for edits made to raw files. So Excire Foto encountered 113,000 files in 1558 folders. Tens of thousands of these files were XMP sidecar files from Lightroom and some were other sidecar files from Exposure X7. In total, Excire Foto processed 78,202 images in 5 minutes 45 seconds.
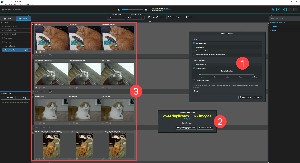 I also had the application (1) locate duplicate images. Most of the duplicates were in folders from my early days of using Lightroom when I sometimes stored output files in the same location as the original photos. This is an exceedingly bad practice. In less than 5 minutes, it found 2544 duplicates and (3) displayed them. At that point, I could use Lightroom to delete or move the duplicates.
I also had the application (1) locate duplicate images. Most of the duplicates were in folders from my early days of using Lightroom when I sometimes stored output files in the same location as the original photos. This is an exceedingly bad practice. In less than 5 minutes, it found 2544 duplicates and (3) displayed them. At that point, I could use Lightroom to delete or move the duplicates.
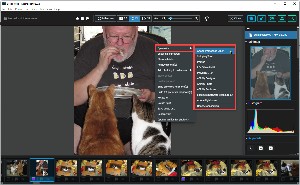 Excire Foto offers excellent organizational tools, including the ability to create photo collections and groups without moving the original images. One oddity is that there's no easy way to edit a photo in Lightroom Classic once you've located it using Excire Foto. The Edit In options are limited to Photoshop, Lightroom (but not Lightroom Classic), the Windows photo tool and snipping tool, and other installed applications such as IrfanView, Affinity Photo, Affinity Designer, and Affinity Publisher.
Excire Foto offers excellent organizational tools, including the ability to create photo collections and groups without moving the original images. One oddity is that there's no easy way to edit a photo in Lightroom Classic once you've located it using Excire Foto. The Edit In options are limited to Photoshop, Lightroom (but not Lightroom Classic), the Windows photo tool and snipping tool, and other installed applications such as IrfanView, Affinity Photo, Affinity Designer, and Affinity Publisher.
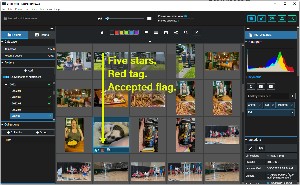 Images can be given rating numbers (1 to 5 stars), any of 5 color tags can be assigned, and any image can be flagged as accepted or rejected. These are the same as used by Lightroom Classic, but the ratings, tags, and flags are not forwarded to Lightroom Classic. That's unfortunate and those who depend on Lightroom Classic would probably be better served with the Lightroom plug-in even though Excire Foto has some additional features. So even though this is a review of Excire Foto, Lightroom Classic users will probably find Excire Search 2 the better option.
Images can be given rating numbers (1 to 5 stars), any of 5 color tags can be assigned, and any image can be flagged as accepted or rejected. These are the same as used by Lightroom Classic, but the ratings, tags, and flags are not forwarded to Lightroom Classic. That's unfortunate and those who depend on Lightroom Classic would probably be better served with the Lightroom plug-in even though Excire Foto has some additional features. So even though this is a review of Excire Foto, Lightroom Classic users will probably find Excire Search 2 the better option.
An extension for Excire Foto called Excire Analytics costs $40. That's in addition to Excire Foto's $100 price tag, but the two can be purchased together for $130. If you're thinking of buying Excire Foto, you won't regret adding the Analytics option. Excire Search 2, the plug-in for Adobe Lightroom Classic is $70.
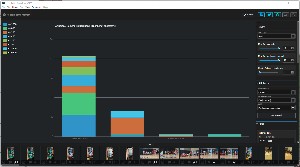 The extension provides insight into how you use your photographic equipment. For example, which cameras or lenses you use most frequently and the settings or camera-lens combination you used to take your top-rated pictures. I might wonder which cameras I've used the most this year. Because the Canon DSLR is currently in use exclusively for capturing images from old family photo negatives that are stored in a separate file structure, the Canon has been used infrequently this year for what I'll call normal photos.
The extension provides insight into how you use your photographic equipment. For example, which cameras or lenses you use most frequently and the settings or camera-lens combination you used to take your top-rated pictures. I might wonder which cameras I've used the most this year. Because the Canon DSLR is currently in use exclusively for capturing images from old family photo negatives that are stored in a separate file structure, the Canon has been used infrequently this year for what I'll call normal photos.
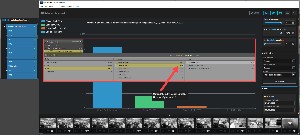 What I discovered is that I used the camera in my smartphone most frequently, the Sony point-and-shoot camera second most frequently, the Canon DSLR hardly at all -- just seven photos, and the camera in the IPad even less. Despite minimal use for normal photos, the Canon was used extensively for photographing roll-film negatives. But there's a problem here: For 2022, Excire reports 423 images made with the Canon, but I knew there were more. Lightroom Classic's Library Filter shows that I've made 923 images this year with the Canon, not 412.
What I discovered is that I used the camera in my smartphone most frequently, the Sony point-and-shoot camera second most frequently, the Canon DSLR hardly at all -- just seven photos, and the camera in the IPad even less. Despite minimal use for normal photos, the Canon was used extensively for photographing roll-film negatives. But there's a problem here: For 2022, Excire reports 423 images made with the Canon, but I knew there were more. Lightroom Classic's Library Filter shows that I've made 923 images this year with the Canon, not 412.
There are also differences between totals for the OpticFilm 35mm scanner (Excire Foto reports 2075 but the correct number is 2671); numbers for the Epson Perfection Scanner are correct (both sources say 89) as are the values for the smartphone camera (both say 5). Note that the Excire Foto filter is set to find all photos present in the Film & Print Scans directory made by all cameras during 2022, the same criteria used for the Lightroom Classic filter.
Although the overall numerical relationships are close, the incorrect counts are troubling. My guess is that the developers will find the problem and correct it in a later version.
 Excire Foto Is A Worthwhile Addition To Photographers' Tool Kits
Excire Foto Is A Worthwhile Addition To Photographers' Tool KitsThe artificial intelligence that powers Excire Foto and Excire Search 2 does a remarkable job of adding meaningful keywords to images. The standalone Excire Foto has limited abilities to interface with Lightroom Classic, but the Lightroom Classic plug-in can make it possible to find photos faster even if you don't add any personalized keywords.
Additional details are available on the Excire website.
The cat rating scale ranges from 0 cats (worst) to
5 cats (best).
Manufacturers of hardware reviewed on TechByter Worldwide typically loan the hardware and it must be returned at the end of the review period. Developers of software reviewed on TechByter Worldwide generally provide a free not-for-resale (NFR) license so that all features of the application will be unlocked.
When my wife followed a link to a recipe on her computer, the screen was immediately filled with dire warning that was accompanied by technobabble from the speaker. She brought the computer to my office and said "I don't know what this is."
The text-to-speech announcement that was playing cautioned that the computer should not be restarted because that would do something terrible. Several items on the screen offered links to "repair" the problem or phone numbers to call for "help". She had not clicked any of the links or called the phone number, and those non actions were exactly right.
The Microsoft logo was present on some of the displayed graphics and the presentation might have been somewhat credible except that:
So I rebooted the computer, ran a diagnostic scan that found nothing, and returned the computer to Phyllis. That left just two questions:
Once I had confirmed that the computer was running properly and that no malware had been installed, I could have used the browser's history function to identify the malicious site. I didn't do that, primarily because I didn't have time for it that day, but there is a lesson here: As the Hitchhiker's Guide to the Galaxy says, DON'T PANIC. Until you're certain that you know what's happening, no action is usually best. Turning off the Wi-Fi connection would have been a good thing to do just in case malware was active. I didn't think it was, but I have to admit that I simply didn't think of killing the network connection. And finally, be sure not to do whatever the message on the screen tells you to do. Click no links. Call no phone numbers.
I've had a love-hate relationship with antivirus applications from when these applications first became available and probably that's not an uncommon point of view.
Possibly in an attempt to justify their existence, third-party protective applications seem to be overly chatty, informing users every time they perform any action, no matter how mundane, and frequently warning about threats that really don't exist. All of this activity distracts the user and slows the computer.
Microsoft includes antivirus, threat protection, and a firewall in Windows Security. The various components remain silent most of the time unless an action realistically needs to be approved or acknowledged by the user. The built-in security functions interrupt users less and have only a minimal effect on system resources.
The history of third-party protective applications usually starts with the development of a decent anti-virus application, but then the developers add more and more functions until it becomes so large and resource hungry that users grumble about the system's performance. I used Norton Antivirus in the early days. When it slowed the system too much, I moved on to AVG and then Avast. Avast now owns AVG. One of the more unfortunate stories is MalwareBytes, which was an excellent application for diagnosing and removing malware. Then a raft of new features caused serious performance problems.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
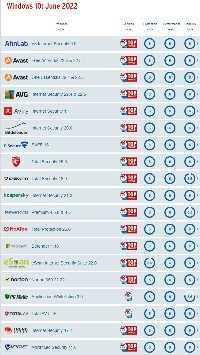 So today my computers run just Windows Security. It's always made sense to me that the operating system's developer would be in the best position to provide protective applications. The frequently updated AV-TEST Institute score for Windows Security is usually 6 for protection, performance, and usability. That's the highest score possible. Many of the third-party apps also score 6-6-6, but if the built-in app earns top marks, why pay more for an app that might be more intrusive and that might slow the computer's operation?
So today my computers run just Windows Security. It's always made sense to me that the operating system's developer would be in the best position to provide protective applications. The frequently updated AV-TEST Institute score for Windows Security is usually 6 for protection, performance, and usability. That's the highest score possible. Many of the third-party apps also score 6-6-6, but if the built-in app earns top marks, why pay more for an app that might be more intrusive and that might slow the computer's operation?
No matter which antivirus system you use, those with G-Mail and Outlook accounts will have the benefit of malware detection on the email servers. Most web browsers also have built-in functions that may detect malicious websites, phishing sites, and other dodgy techniques. Windows has a built-in Smartscreen filter that can issue a warning if there's a problem with a specific piece of software or if you attempt to run an application that isn't known to Smartscreen.
Unless you need some of the extra features that third-party applications provide, Windows Security is probably good enough. What are some of these special features?
Some antivirus applications monitor your webcam to keep scammers from turning the camera on remotely. But today, most webcams have an opaque slide that can be left in place until you need to use the camera. If not, a well placed piece of tape can do the same thing. A few protective applications monitor security breach websites and will let you know if your email address has been exposed. Given the number of breaches that have occurred, it's better to simply assume that your email address is public knowledge and to concentrate on safe computing. Some security bundles include password managers or offer a virtual private network (VPN). Others may have options to securely delete files or offer secure on-line storage. Some applications watch for patterns of malicious activity even if no malware has been detected and a few can watch for attempts to encrypt your files. So a third-party application may have features that you find attractive.
Just bear in mind that every additional feature will have an adverse effect on the computer's performance. How much performance degradation is acceptable in the name of more robust security?