Listen to the Podcast
1 July 2022 - Podcast #799 - (18:34)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
A relatively small number of applications are essential for computers I use. Adobe's Creative Cloud suite, Microsoft's Office suite, UEStudio, GoodSync, my current preferred web browser, and Thunderbird for example. These are the applications I install immediately on a new computer so that it will be usable. Then I can install other applications as I need them, a process that can extend over several weeks.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Let's talk about GoodSync today. It's one of three backup applications that I use. Three? Isn't that weird?
Let's talk about GoodSync today. It's one of three backup applications that I use. Three? Isn't that weird?
Perhaps is is, but my goal is never, ever to lose a file even when I do something stupid. Consider the applications I use and why:
GoodSync's automated backups start around four each afternoon and transfer recently created or updated files to the local Y drive. CrashPlan's backups are better for several reasons: They're more likely to be up to date and I can recover older versions of files, but drive Y is attached to the computer and immediately restoring a file is easy. The primary advantage for me, though, is that I can install GoodSync on my wife's computer and have it copy her email, digital camera, and documents directories to my computer for CrashPlan backup.
Phyllis used to bring me her camera's memory card so that I could copy the files to one of the drives that gets backed up. The problem with that is that sometimes it was several weeks between download times and any changes she made to files on her computer wouldn't be backed up. GoodSync resolves that problem.
On my computer, GoodSync runs as a server. There's another licensed copy on her computer and it runs as a client. Once a day, GoodSync checks to see if there are any new photographs or any changed photographs and, if so, copies them to a data drive on my computer. From there the files are backed up to an on-line server, to a network attached storage device, and weekly to separate USB backup drives. Much of that work is handled by GoodSync.
GoodSync can back up data files locally, to a network drive, to another computer, to a GoodSync server, or to any of several other online services.
Users who choose to backup to network shares or folders on external drives may have encountered problems with other backup systems. The drive letters assigned to these devices by the operating system can change and that would cause a backup application that expects a specific drive letter to fail. GoodSync looks for a name that is much less likely to change. For USB drives, GoodSync suggests using the disk drive's volume name. For network drives, GoodSync recommends the universal naming convention (UNC) path. So instead of drive G, GoodSync looks for "Media-Downloads" and instead of network drive Z, it selects "\\readyshare\EXTERNAL_WD1".
The three jobs on my wife's computer run automatically at a time that the computer is almost always in use. That's only one option for backup tasks, though. GoodSync can watch a directory and back up files when they change, periodically, when GoodSync starts, or when a specific folder becomes available.
 There are six jobs that I run manually each week on Wednesday and 18 jobs that run automatically every day, one at 11am and the others starting at 4pm.
There are six jobs that I run manually each week on Wednesday and 18 jobs that run automatically every day, one at 11am and the others starting at 4pm.
The scheduling is accomplished with a system that will be immediately familiar to anyone who has set up a cron job on a Unix or Linux system, but possibly confusing to others. It's really quite simple one you understand that there are settings for minute, hour, day of week, day of month, and month; that no entry means no restriction; and that time entries are based on a 24-hour clock. So setting up a job with an entry of 11 minutes, 16 hours, and blanks for the other components will create a job that will run at 4:11pm every day.
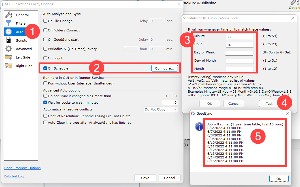 Scheduling uses (1) the Auto tab on the Job Options menu. Selecting (2) On Schedule and clicking the Configure button opens the scheduler. Fill in the (3) schedule parameters and, to confirm the settings, click the (4) Test button and review the schedule (5) for the first ten times the job will run.
Scheduling uses (1) the Auto tab on the Job Options menu. Selecting (2) On Schedule and clicking the Configure button opens the scheduler. Fill in the (3) schedule parameters and, to confirm the settings, click the (4) Test button and review the schedule (5) for the first ten times the job will run.
To run a job to run at 5:20pm each day, you'd enter 20 in the minutes cell and 17 (5pm) in the hours cell. To narrow the run times further, you could specify a day of the week value or a day of the month value. Entering 3 for the day would limit the job to running only on Wednesday, or entering 25 in the day of month cell would limit the job to running only on the 25th of each month.
Unlike most backup applications, GoodSync doesn't have a restore process. That's actually one of its advantages because files and directories are simply mirrored to the backup device. Files are not compressed or encrypted by default, but they can be. Restoring files simply involves copying them from the backup device to whatever location you prefer.
 I can't imagine running a computer without GoodSync
I can't imagine running a computer without GoodSyncAlthough it doesn't do disk image backups, GoodSync is a comprehensive file and folder backup application for Windows and Mac computers. The ability to copy files from nearly any location to any other location is a plus and the ability to fully automate jobs makes it even better. A free version for home use is available, but it can run only three jobs and is limited to 100 files. A license costs $30 for the first computer and there are significant discounts for additional computers.
Additional details are available on the GoodSync website.
The cat rating scale ranges from 0 cats (worst) to
5 cats (best).
Scammers are nothing, if not inventive. Some of them could probably make an honest living as authors, but that would be too much work.
Scammers who want to seal your Instagram account have started using a technique that seems harmless on its face. You may receive a private message asking you to vote for their product or pet or art work in some contest. The backstories vary, but what doesn't vary is that the scammer will send you a link. You're not supposed to click on the link, so that makes it feel safe. Instead, the scammer wants you to take a screen shot of the link "for confirmation" and send it to them.
But here's the trick: The link you'll take a screen shot of and send back to the scammer, who is masquerading as someone you know, is actually the Instagram "forgot password" link. When you send that link back to the scammer, you'll give that person everything needed to change the password on your account and lock you out of it.
Another technique a scammer will use involves an explanation that the user wants to get their other Instagram page on a new phone and they can't figure out how to do it. If you could just take a screenshot of the link they send you and send it to them, they'll succeed.
These are nothing more than variants of the verify-your-account scam. The messages often appear to be from a contact you trust, but the account has been compromised by the scammer. Sometimes they may ask you to add their email or phone number to your account, but the more common process is to ask you to do a screen shot of a link they send you or to copy the link and send it back to them.
What happens next is that you'll be locked out of your account and the scammer will start using it to scam others.
If you receive a message like this, don't reply. Just ignore it and then report the account as hacked.
Overall, Facebook's security has improved in recent years, but Facebook can't protect against user error. That's what the crooks depend on. Facebook said in 2020 that more than 100 million accounts were fake. Although brute-force attacks and spyware can be used to capture a Facebook account, the most common method is social engineering. Naive users are presented with information that they fail to recognize as phony. As a result, they simply hand over their credentials to scammers.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 It's worth noting that there's a difference between an account that has been stolen, which many people refer to as "hacked", and an account that has been cloned. Any account can be cloned, but users can make their accounts less attractive to scammers by simply eliminating the ability for anyone except you to see your friends list. A cloned account is usually used to contact your friends in an attempt to defraud them. Fixing a cloned account is easy: Locate the cloned account and report it to Facebook.
It's worth noting that there's a difference between an account that has been stolen, which many people refer to as "hacked", and an account that has been cloned. Any account can be cloned, but users can make their accounts less attractive to scammers by simply eliminating the ability for anyone except you to see your friends list. A cloned account is usually used to contact your friends in an attempt to defraud them. Fixing a cloned account is easy: Locate the cloned account and report it to Facebook.
Stolen accounts are more difficult. Once a scammer has your user name and password, it will be only moments until the crook changes the password and you'll be locked out. The process of recovering the account isn't easy or fast, so it's better to avoid the problem.
Phishing is one social engineering method. The victim receives a message that may appear to be from Facebook. One common ploy is to tell the user there has been unauthorized activity on the account and that they must follow an enclosed link to verify their account. The link takes you to what appears to be a login page, but its sole purpose is to steal the user name and password. Scammers also use SMS messages and phone calls, so beware. If you think there's a problem with your Facebook account, don't follow the link. Just go to Facebook and log in normally.
And if the worst happens, you'll need to act fast. The Make Use Of website explains what you can do if the scammer hasn't yet changed your password and a companion article has more helpful information.
Computers and mouses (or mice) proliferate, but you might not need a mouse for every computer.
Let's set the Wayback machine (thanks to Mr Peabody and his boy, Sherman) to nearly prehistoric times, at least as far as computers are concerned. Computers were big. They took up entire rooms. People brought work to them, handed information over to the people who ran the computers, and waited for output. These were multi-user computers.
Then desktop computers came along and we had single-user computers.
Eventually, computers became ubiquitous and we had multi-computer users. I thought I coined that term sometime in the 1980s and was quite proud of myself, but probably the term was not one I invented. These days, a lot of people are multi-computer users. Take a look around your house. How many computers do you have?
My desktop always has a Windows computer and a Macbook computer. An Iogear switch allows me to use the mouse and keyboard on either of those computers. The monitors have their own switches that switch from one computer to the other.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 I also have a Windows tablet computer that I need to use on the desk occasionally. I had a mouse for that computer. It has its own keyboard that connects via Bluetooth, but it needed a separate mouse. The mouse was installed on a dock, so only the touchpad on the keyboard was available if I didn't connect the dock. I am not a fan of touchpads.
I also have a Windows tablet computer that I need to use on the desk occasionally. I had a mouse for that computer. It has its own keyboard that connects via Bluetooth, but it needed a separate mouse. The mouse was installed on a dock, so only the touchpad on the keyboard was available if I didn't connect the dock. I am not a fan of touchpads.
The Logitech MX Master is a relatively expensive mouse, but it can connect to any of the computers, and it offers a variety of other controls, including one that allows me to control the audio playback level with a wheel on the side of the mouse. It has a good ergonomic shape that keeps my fingers from cramping.
The mouse connects to the primary Windows computer and the MacOS computer via a Logitech USB unifying device, but the mouse is also capable of connecting via Bluetooth and it can be linked to three separate devices.
The primary advantage is that I need only one mouse and it can be set up so that it works the same way on each of the three computers. The Windows desktop computer and Macbook computer are on one connection, the Windows tablet computer is on another, and I could add a third device, such as an IPad, if that ever seemed like it would be helpful.