Listen to the Podcast
15 Sep 2019 - Podcast #660 - (21:20)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
The crooks who run ransomware operations aren't stupid. They've learned that large organizations and large cities generally do a good job of keeping systems updated and often have protections against ransomware. That's not the case for rural counties, small cities, small businesses, and individuals. When huge, lucrative targets make themselves more difficult, the crooks start looking at easier targets.
More than 20 municipal governments in Texas were targeted with ransomware this summer. Two cities in Florida (Lake City and Riviera Beach) together paid more than $1,000,000 to thieves after deciding there was no other way to get their files back. These two cities could probably have put that million dollars worth of taxpayers' money to better use if only they'd had the foresight needed to plan for such attacks.
Barracuda Networks says at least 70 municipalities have been victimized by ransomware attacks this year and the most common vector for planting the malware is (of course) email. The attacks can reach networks, applications, and critical data.
Jackson County, Georgia, paid nearly half a million dollars in March to regain access to its systems. Large cities are vulnerable, too. Last year Baltimore was attacked. The city didn't pay the ransom, but it cost $18 million to recover data and rebuild their systems. And some of the data was lost in the process.
The Jackson county attack took down most of the county's IT systems but didn't affect its website or 911 emergency system. Jackson County officials contacted the FBI, which says victims should not pay ransom. The the county hired a cyber-security consultant who negotiated with the ransomware operators. County administrators decided that paying $400,000 was better than what they believed the alternative to be -- several months worth of recovery operations during which most systems would remain off-line.
The ransomware used is known as "Ryuk", which is currently undecryptable. The source is believed to be Eastern Europe and the crooks' targets are generally local government, healthcare, and large enterprise networks. Operations like this won't go after smaller targets.
Ransomware attacks are distributed via email and file-sharing networks. Some are propagated via on-line ad servers, but the most common vector involves phishing emails. The largest single ransomware attack to date, WannaCry, used a flaw in Microsoft's Server Message Block (SMB) protocol to spread an infection through corporate networks.
The US National Security Agency had discovered the SMB vulnerability but, instead of reporting it, developed code called EternalBlue to exploit the flaw. EternalBlue was stolen by Shadow Brokers who released it in 2017. Microsoft discovered the flaw shortly before the WannaCry attack and had released a patch but many system administrators had failed to install it. Microsoft was highly critical of the US government for its failure to share information about the flaw.
In the early days of ransomware, images were often used to imply that a law enforcement organization had taken over the computer. One common ploy used the FBI logo and stated that illegal file sharing had been detected. The victim was instructed to pay a "fine" or risk criminal prosecution. That technique is no longer used. Instead, the crooks simply state that they have taken over your computer and that you must pay if you want to regain access to your files.
Victims typically pay the ransom using Bitcoin or other virtual currencies but premium SMS messaging and prepaid credit cards are also used.
If you become a ransomware victim, No More Ransom may be able to help. It's a European organization that counts as its members the Europol Cybercrime Center, Amazon Web Services, Barracuda Networks, McAfee, Kaspersky Lab, and the Netherlands national police. The site's goal is to help victims of ransomware retrieve their encrypted data without having to pay the criminals.
The site notes both good news and bad news about ransomware:
The project also aims to educate users about how ransomware works and how infections can be avoided. This is information that applies to any business, government, or organization regardless of size and also to individuals who want to avoid being victimized.
The site lists six key points and two more than apply specifically to WannaCry:
The threat is real and it applies not just to governments, businesses, and organizations. Less skilled crooks go after home users. They won't demand hundreds of thousands of dollars but they might demand $1000 if you ever want to see your tax records, email, and family photos again. That's why having more than one backup is essential and it's why having at least one backup that's disconnected from the computer most of the time is even more important.
Your cloud-based backup system can become corrupted as the system automatically backs up changed files. A second backup, even if it's a week old, can be the safety net that is the difference between a catastrophic and massive data loss and a relatively minor inconvenience. By "relatively minor" I mean that spending several days rebuilding the operating system and reloading files from backup is a lot better than losing all your data.
Electronic devices are always looking for ways to confuse us. This might be a bit more anthropomorphism than you feel is appropriate but these inanimate devices sometimes seem to have animate motivations and sometimes this causes us to look in the wrong place to solve a problem.
On my birthday a couple of weeks ago I wanted to print a coupon that would give me a free sandwich at a local restaurant. I didn't really need the coupon because the offer had been loaded to the restaurant's app on my phone. But I'm an old guy and I don't implicitly trust phone apps.
No big deal. I clicked Ctrl-P to bring up the print dialog, clicked Print, and ... nothing. No activity. No paper. Complete silence. Sometimes the printer goes off-line, so I reached over and pressed the Start button. That woke the printer up, but nothing appeared in the output tray.
No big deal. Sometimes an off-line printer will cause a problem with the print queue. So I opened the print dialog and killed the print job. For good measure I turned the printer off and then turned it back on. Then I clicked Ctrl-P to bring up the print dialog, clicked Print, and ... still nothing. No activity. No paper.
No big deal. Sometimes the computer becomes confused (and there's more anthropomorphism) so I restarted the computer and, after logging in again, I opened the coupon and clicked Ctrl-P to bring up the print dialog, clicked Print, and ... still nothing. No activity. No paper.
All right. Now we have a puzzle and the beginning of an annoyance so I opened Settings and navigated to Printers. I found PDF printers, One Note, and other virtual printers. No physical printers. Then I opened VueScan to see if it could communicate with the scanner that's part of the printer. No luck there either.
So has the printer suddenly died? I selected the option to add a printer and a scan revealed that no printer was available to be added. Will my birthday be ruined? Will I need a new printer? What is going on here? I had a lot of questions but no answers.
And then I glanced at the computer's Notification Area (aka "Tray"). Instead of seeing an icon for an Ethernet connection, I saw an icon for a Wi-Fi connection. "Well that's not right" was my first non-profane thought. The Network section of Settings was no help but clearly one of two things had happened: Either the Ethernet connection on my computer had malfunctioned or there was a problem with the router.
I connected to the router's management console to see what the router thought was connected to it. A firmware update was available for the router but the more important finding was that only Wi-Fi devices were connected. Four Ethernet connections should have been there.
It wasn't the computer that was confused. It wasn't the printer that was confused. Something had gone wacko with the router. I could have just rebooted the router but a firmware update was available so I elected to install the update, which would also reboot the router.
Less than five minutes later the firmware update had been installed, the router had been rebooted, my primary computer had an active Ethernet connection, and the printer was back on-line.
And the moral of the story is .... The moral of the story is that it's a good idea to open your eyes, examine the symptoms, and pursue the solution that will correct the problem. And also computers and other electronic devices really aren't out to frustrate us. It only seems that way.
Despite all their features, Microsoft's Office Suite, WordPerfect's Office Suite, Google's G-Suite, and Zoho's Office Suite may not be the right choice for you. These are all paid applications and perhaps you don't want to pay for an office suite or maybe you can't justify paying for applications that you rarely use or it might be that you just like the idea of open-source applications.
If you're in one of those categories, you might have looked at the open-source office suites: Apache OpenOffice and LibreOffice. If you want the tl;dr version: LibreOffice is the right choice. All open-source office suites trace their origin back to Star Office that was a Sun Microsystems suite until Sun was acquired and destroyed by Oracle. Oracle OpenOffice was discontinued in 2011.
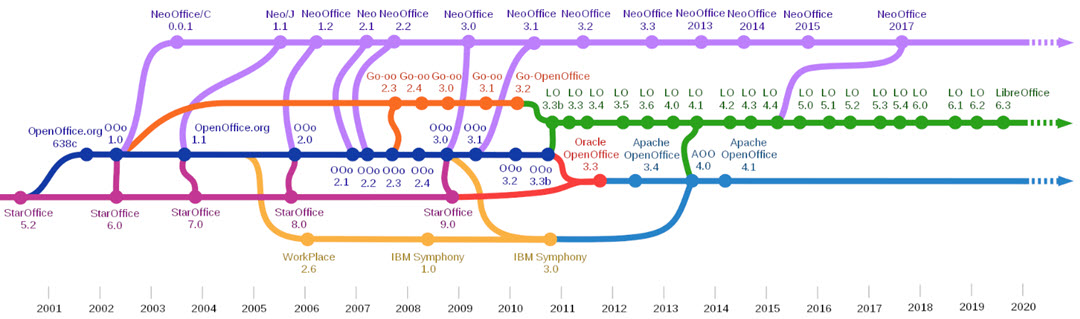
Along the way, OpenOffice was spawned in 2001 and NeoOffice for Mac in 2002. Various forks were spun off and LibreOffice began as a fork of OpenOffice. LibreOffice is the only application that includes frequent updates (about twice a year). By comparison, NeoOffice hasn't been updated since 2017 and Apache OpenOffice's most recent update was in 2014. The open-source suites all have interfaces that are reminiscent of much earlier versions of Microsoft's Office Suite and that makes them attractive to some users.
Even if you use Microsoft applications most of the time, it's a good idea to keep a current copy of LibreOffice on the computer because it's not uncommon for Microsoft Word to corrupt a file in such a way that Word cannot open the file. I'm an on-line acquaintance with hundreds of editors around the world and it's surprising (in a non-surprising way) to hear from someone who has spent weeks editing a manuscript and finds that the file is corrupt. A recent copy of the file can be restored from backup but this might mean losing a day's worth of work.
The recommendations follow a predictable pattern: Reload the file after restarting Word, reload the file after rebooting the computer, and finally install a copy of LibreOffice, open the problem document in the Writer application, save it as a Word document, and then open it again in Word. This almost always resolves the problem.
Even though OpenOffice hasn't been updated since 2014 and LibreOffice has received updates twice this year, there are more similarities than differences. They've both available at no cost. Both run on Windows, MacOS, or Linux. Their interfaces are similar but not identical. Both products are good and the open-source community would be better off if the split hadn't occurred or if it had at least not been so contentious.
Perhaps the most significant difference involves the formats each suite can write. Both can open nearly all current file formats, but OpenOffice can't save files in Microsoft's current formats. If you need to be able to read and write files in Microsoft's formats, you'll need either a Microsoft application or LibreOffice.
OpenOffice and LibreOffice have different licensing methods, too. OpenOffice operates under the Apache License and LibreOffice uses the GNU Lesser General Public License version 3 and Mozilla Public License version 2. There's a lot of technical jargon behind those licenses, but it all comes down to this: LibreOffice can freely incorporate code and features from OpenOffice but OpenOffice can not incorporate anything from LibreOffice. As a result, LibreOffice is able to add features faster.
Both suites have more than sufficient power and flexibility for most people. You can download them and decide for yourself which more closely suits your needs and then uninstall the other. Or keep them both.