Listen to the Podcast
28 Jul 2019 - Podcast #653 - (18:43)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Threats abound when it comes data on your computer and money in your bank account. Home-grown and foreign threats endanger elections, too. Protection is essential and software can go only so far, so it's up to us to develop increasingly sophisticated ways to repel them. Or is it? Basic security practices eliminate most threats.
Comedian Jack Benny occasionally repeated a skit in which he was approached by a rough-looking character. “Your money or your life?” the guy bellowed. After a moment, the crook repeated the threat: “Come on, buddy, your money or your life?” And Benny replied, “I’m thinking! I’m thinking!”
Hackers supported by governments in Russia, China, Israel, England, and most other countries are constantly poking and prodding. So are criminals. Hospitals and municipal governments are favorite targets for the crooks who encrypt the data on computers’ hard drives and then offer to sell the hospitals and governments access to their own data.
Some organizations have paid but there is no guarantee that they’ll get their data back. Other organizations have been able to recover on their own. In either case lives are literally at risk when medical systems are compromised and when police or fire departments lose access to emergency communications systems.
Malware that encrypts data is easy to obtain. Even small-time crooks can find ransomware offered as a service on the dark web. If one of these people manages to place malware on your computer, it doesn’t matter much if he’s a bored teenager, a high-school drop-out, or an unemployed person who’s desperate to come up with next month’s rent.
According to McAfee Labs, technologically inept crooks can rent what they need. The developers take a cut of the profits. Collecting $20,000 to unlock a hospital’s computers or $100,000 to restore a city’s systems are big payoffs, but crooks also collect a few hundred dollars each from people who find that they are locked out of access to their photographs and financial records.
Crooks know that companies can afford to pay higher ransoms than consumers. A survey by IBM found that about half of the respondents had experienced a ransomware attack and 70% of them paid to get their data back even though the FBI strongly recommends against paying ransom.
The FBI asks that anyone who is hit with ransomware, whether or not they pay the ransom, to report the incident at the Internet Crime Complaint Center at www.IC3.gov.
If your computer is infected with ransomware and you don’t have a full, complete, and verified backup, your only option might be to pay the ransom and hope that the crooks are “honest”. A better option is to keep ransomware off your computer.
The first and last line of defense is what I usually refer to as “wetware” — the stuff between your ears. Software solutions have a place, but no protective application will catch every threat and that’s why it’s important for us computer users to be vigilant and cautious.
Many people become victims of ransomware when they open an email attachment that contains malware or when they click a link that takes them to a corrupt website that installs malware.
These malicious email messages are usually easy to spot. Does that message that appears to be from UPS, FedEx, the USPS, or your bank actually come from Albania, Ukraine, Brazil, or Hungary? Every decent email application allows users to view routing information that will quickly answer the question.
Examining the contents of the message is another critical step. A legitimate message from UPS, the Post Office, or FedEx will have a tracking number, not an attachment. Messages from banks, other financial institutions, or companies will clearly identify you as the recipient. For example, the message won’t have been sent to “undisclosed recipients” and you should see your full name and other identification in the message.
If a message asks you to follow a link to “confirm” your account, ignore the link. Instead, go directly to the organization’s website and log in normally. Clicking a link in a poisoned email may appear to take you to the organization’s website, but it can also be a link to a man-in-the-middle site that collects your user name and password before passing you on to the real website.
Observation and caution alone eliminate most problems.
Even the most cautious person can make a mistake, so it’s wise to have an application that watches for threats even though those applications are far from perfect.
Anti-virus and anti-malware applications aren’t able to keep up with every possible threat, but they do provide some protection. For Windows users, the Windows Defender Antivirus is a good choice. It’s included with Windows and updated regularly. It’s important not to use more than one anti-virus application; doing so will render your computer less secure.
The sole exception is Malwarebytes. Regardless of which anti-virus application you’re using, Malwarebytes is a good addition because it includes website, malware, exploit, and ransomware protection.
Regardless of how many protective measures you put in place, they won’t catch everything and that brings me back to the importance of using your “wetware”.
Microsoft has several simple suggestions that can be combined into a single overarching rule. “Often fake emails and web pages have bad spelling or just look unusual. Look out for strange spellings of company names (like ‘PayePal’ instead of ‘PayPal’) or unusual spaces, symbols, or punctuation (like ‘iTunesCustomer Service’ instead of ‘iTunes Customer Service’). Don’t click on a link on a web page, in an email, or in a chat message unless you absolutely trust the page or sender.”
Microsoft’s most basic advice says it all: “If you’re ever unsure — don’t click it!”
It's been 40 years since people began to use computers at home. To be "current" used to mean replacing the computer every couple of years. Many corporations still stick to that timetable, but home computer users have found that they can get five years of use or more from current computers. Still, the time comes when new hardware is needed and that often leaves a still functional machine that needs a home.
Organizations exist that will accept working computer so that they can be reconditioned and given to users in developing countries and to schools or individuals in low-income areas of the United States. Some of these older computers are converted to run Linux or are given to younger family members. Others are sold on EBay, Facebook, or other on-line services. Some are donated to Volunteers of America or Goodwill Industries. But what if the computer doesn't work?
We replaced my wife's computer nearly two years ago and the old computer has been sitting on a shelf since then. Donating it wasn't an option because the hard drive was faulty. I didn't want the computer carcass to end up in a landfill, but who wants a computer that doesn't work?
As it turns out, SellBroke wants computers that don't work.
SellBroke will also buy computers and other electronics that are still working, but you'll get more money by selling working devices on-line. The dead computer we had was a Lenovo G500. Everything worked but the hard drive. Given enough time and patience, I could get the computer to boot, but it was far from functional.
I found that SellBroke would pay $44 for this computer even knowing that the hard drive was bad.
Well, that was an easy decision: $0 and send the dead computer to a landfill or $44 and keep it out of a landfill.
I filled out the order form and SellBroke sent me a UPS shipping label. They pay for shipping, so that didn't come out of what they offered for the computer. There was no downside. If I sent the computer in and they failed to pay me, I was out nothing. The computer didn't work and all I could do with it was recycle it.
So I managed to get the computer to boot one final time, removed all of the files from my wife's account, and then shut the computer down. It would have been better to wipe the disk, but that simply wasn't going to happen.
Then I packed the computer, attached the UPS label, and dropped it off at a UPS store.
Less than a week later, the computer arrived at SellBroke in Reno, Nevada.
A few days later, I received a couple of email messages, one from PayPal and one from SellBroke. I now had $44 for a computer that I considered to be entirely useless. Now I can say that if you have any computer or other electronic device that doesn't work, you should take a look at the SellBroke website.
For devices that are still fully functional, you'll probably get more from EBay or one of the other on-line sales sites. Don't forget, though, that sites such as EBay charge a commission and you'll be responsible for paying to ship the item to the new buyer. If you're looking for a quick, easy, no-fuss way to convert old hardware to new cash, SellBroke might be the best choice even if what you have is still functional.
I have a love-hate relationship with electric providers. I'm the son of a man who was an electrical contractor, so I understand some of the problems that electric utilities face. But I'm also someone who sees the unequal position electric utilities have because of the monopoly position they enjoy. Companies such as American Electric Power are guaranteed to be profitable.
I've complained frequently about power outages in my neighborhood. These outages are generally caused by squirrels who meet their demise when they become part of a short circuit. The only solution to that problem is burying power lines and most consumers aren't willing to pay for the cost of doing that. So we deal with a certain number of power outages and consider ourselves fortunate to be dealing only with first-world problems such as occasional periods when the power is off for a few hours.
In the past two years, American Electric Power has installed "smart meters" at homes in my area. The advantage for AEP was that the meters could be "read" without sending someone to look at them, but now there are some advantages for homeowners.
AEP offers to send homeowners a device that lets them see what the smart meter sees, to pay their monthly bill, to see a map of where power is out, and more.
I signed up for the service and AEP sent me a little device that can communicate with the smart meter and also provide usage information that I can view on a smart phone.
Because the device connects to my home Wi-Fi system, I can see how much power is being consumed even if I'm not anywhere near the house.
Some users have complained about the display, but it seems logical to me. Each day is represented using a 24-hour circular graph that shows power consumption on an hour-by-hour basis.
For example, on 30 June (left) the power consumption was relatively low except when the air conditioning unit was on. At night there are long periods between the usage spikes, but the spikes are much closer as the temperature rises during the day and as people are awake and working.
An alternate view (right) combines usage with anticipated temperatures during the day.
So if your electric utility has installed smart meters and offers free access to the data from the meter, it would be a good idea to take advantage of the offer.
Adobe's photographic, video, and publishing applications often capture the spotlight from some of the other more specialized applications but Adobe keeps adding features and making improvements. So lets take a look at Audition this week. An update was issued about a week ago.
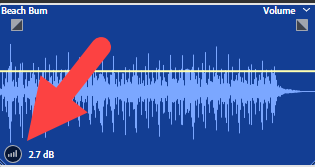 The coolest new feature for me is on-clip audio scaling. Sometimes (often) it's necessary to change the overall volume of an audio clip. It's easy enough to drag the volume envelope marker, but it's also easy to accidentally set a key frame. Then you have to delete the key frame and try again. Now a small icon in the lower left corner of each clip makes changing the level easy.
The coolest new feature for me is on-clip audio scaling. Sometimes (often) it's necessary to change the overall volume of an audio clip. It's easy enough to drag the volume envelope marker, but it's also easy to accidentally set a key frame. Then you have to delete the key frame and try again. Now a small icon in the lower left corner of each clip makes changing the level easy.
Auto ducking has been added.  No. Not that kind of duck.
No. Not that kind of duck.  No ducks in the studio! Ducking refers to the process of dropping the level of music or background sounds when someone is speaking. In the past, this has been a manual process. It's not difficult but automating the process saves time. Audition can now generate a volume envelope to duck ambiance sound behind dialogue, sound effects, or any other audio clip using the Ducking parameter in the Essential Sound panel.
No ducks in the studio! Ducking refers to the process of dropping the level of music or background sounds when someone is speaking. In the past, this has been a manual process. It's not difficult but automating the process saves time. Audition can now generate a volume envelope to duck ambiance sound behind dialogue, sound effects, or any other audio clip using the Ducking parameter in the Essential Sound panel. 
A feature called Punch and Roll Recording has been added so that users can insert corrected audio during a recording session. Given Audition's massive number of precision editing controls that can be used in a post-recording environment, this feature seems unnecessary. Still, post-recording edits take time and when time is a critical factor, punch-in recording can save critical minutes.
Are these big improvements that will make audio production professionals stop and say "WOW!"? Aside from on-clip audio scaling, no, they're not. They are incremental improvements that will delight some users and be ignored by others. These are the kinds of enhancements that long-time users of Adobe's various products have come to expect.