When you consider that I'm surrounded by three Windows 10 computers (one running a slow-ring version on the Insiders program), a Mac, and one that runs Linux Mint, you might expect that one system or another will pester me about updating something frequently. You would be right. These updates may seem bothersome, but skipping them would be a mistake.
The Windows computers also run NiNite, a utility that keeps track of updates needed by applications such as Filezilla, Notepad++, Skype, ImgBurn, MusicBee, IrfanView, 7-Zip, LibreOffice, PDF Creator, Java, Shockwave, and Google Earth. When any of these applications has an update, NiNite tells me about it and offers to install it.
There's also Adobe Creative Cloud and its nearly 2 dozen individual components. The Creative Cloud application displays an alert when updates are available.
So it's a rare day that passes without installing at least one update and I'm sometimes puzzled by the reluctance some people express when it comes to updating operating systems and applications. Regardless of the operating system on your computer, it's wise to install updates promptly.
Let's consider Windows first. Often the updates for the operating system include security updates. These are flaws that malware and crooks can exploit. It's important to understand that applications and operating systems are written by people and that people sometimes miss flaws. It's also a good idea to realize that crooks spend a lot of time looking for anything they can use to break into your computer.
Windows has flaws. So do components that are used by various applications -- ActiveX, Dot-Net Framework, and Java, for example. Browsers are also updated frequently and nearly every browser update contains fixes for security flaws. Other updates are pushed out to fix bugs that cause either the operating system or an application to malfunction. Updates also sometimes contain new features, as is the case for annual Windows updates and updates for applications on the computer.
It's true that any update can create a problem for users. This is something I've seen on Windows, MacOS, and Linux computers -- but errors that are introduced as part of an update are usually addressed quickly by the developers. Microsoft's track record with updates is far better than it used to be and despite the potential for problems, Windows users are almost always better off installing updates sooner rather than later.
Users can specify "active hours", the times during which they don't want to be bothered by updates. By default, this is set to 8am to 5pm. The operating system generally won't be restarted during these hours. There is an exception: If you turn the computer on at 8am and turn it off at 5pm, there is never a time when it can be restarted to install updates. In this case, Windows will eventually insist on restarting the computer.
Once an update has been downloaded and installed, you can specify the time that the computer will restart.
Those capabilities existed previously, but Creators Edition Fall Update has made some significant changes in how future updates will be installed. You'll find these changes under Advanced Options near the bottom of the Update and Security panel of Settings.
Although the MacOS is generally perceived to be more secure than Windows, the MacOS is just as insistent as Windows is when it comes to updates. Apple says that users who receive a notification that software updates are available can choose when to install the updates or ask to be reminded the next day.
Mac users can adjust some security and software update settings. Users have the option of setting the Mac to install updates automatically for the operating system as well as for applications acquired through the App Store. It's also possible to visit the App Store to check for updates manually.
Apple installs required security updates automatically unless you turn that feature off. My recommendation: Don't turn it off. There are six options and I enable five of them.
Some other applications (Microsoft Office, for example) will have their own procedures for acquiring updates. Because Office updates often have security implications, you'll want to set the Microsoft Update app to install updates automatically. The setting is available from within any Office app and there are three choices:
The various operating systems use different interfaces and procedures to install updates, but the underlying intent is the same for all of them: Correct programming errors and eliminate security threats. The numerous Linux distros have different faces and there are several package managers -- the component that installs applications and updates, but the underlying component, the kernel, is the same regardless.
Each Linux distro might present update information in a slightly different way, but the reasons for updating both the kernel and the installed applications are the same for Linux as they were for Windows and MacOS. The big three reasons:
When Linux has an update, you'll generally see a list of the packages that will be updated. Mint displays a level number for each proposed update.
Users should always install updates with levels 1 through 3. The cautions (levels 4 and 5) apply mainly to Linux systems that are being used as servers. Individual users should probably still take any kernel updates even if they are shown as level 4 or 5, as I did in a recent update that listed two kernel updates with level 4.
During the update process, the user can display a screen that shows what's going on in the background.
If you're easily amused and have nothing better to do during the update process, you may want to watch the text scroll by. Read fast, though!
If you're easily alarmed, avoiding the verbose display would be wise because you'll occasionally see the words "warning" or "error". For example, you may see "Warning: No support for locale: en_US.utf8". This message refers to local language support and it is the result of changes that have been made to how localizations are stored. It's a cosmetic problem that will cause no problems.
The operating system on your computer really doesn't matter. What does matter is keeping it up to date. Updates can occasionally cause problems, but all have been tested before being released. Hardware-related problems are less common on MacOS computers because that operating system will run (legally) only on Apple hardware. Linux and Windows systems both permit a larger variety of hardware -- Windows even more than Linux -- so waiting a week or two is safe for all updates except those that are shown as critical security fixes.
It's been a long time since Firefox began its quest to take over the browser market from Microsoft's Internet Explorer. It was November 2004 when Mozilla released Firefox 1.0 after more than 2 years of development and pre-1.0 releases. Computer geeks like me were excited because the browser was faster and considerably more secure than Internet Explorer 6.
Those who didn't understand Firefox's advantages, or didn't care, stuck with Internet Explorer. Still, by 2008, Firefox had about a quarter of the browser market share. Internet Explorer had about 70%. The rest was split between Safari (available for both Mac and PC at the time) and Opera.
Then, in September 2008, Google released the first version of Chrome. Within a year, Chrome had around 3% of the market and Firefox continued to gain strength, reaching about 30% of the market and IE was down to 60%. In 2010, Firefox hit 31% and never went higher. Chrome offered several advantages over Firefox and it didn't have the memory leak that had plagued Firefox from the beginning.
Today Chrome has nearly 65% of the market, Internet Explorer and Microsoft Edge combined have around 13%, and Firefox has about 14%. Firefox, however, has a new version and for the first time in several years, I'm running it as my primary browser.
The newly released Firefox Quantum has real promise, but it might be too late. Will anyone notice?
Chrome has been my primary browser for several years. When Chrome starts, it loads 13 websites, so I set up Firefox to load the same 13 websites and then started watching system resources, particularly CPU usage and memory. I expected Firefox to use more resources than Chrome and for that old memory leak to cause available RAM to shrink over time and -- guess what: It didn't happen.
Firefox's consumption of both CPU and RAM was lower than Chrome's.
I opened 3 more tabs in Firefox (total 16) and closed 2 in Chrome (total 11). At that point, each browser was using about 2.2GB of RAM and 1 to 4% of the CPU. This was both unexpected and welcome.
Even with so many tabs open, Firefox seems faster than Chrome. Mozilla claims huge speed differences that were doubtless achieved in a highly controlled environment. I didn't see these huge differences, but Firefox was perceptibly faster. Then I opened more tabs. With 30 tabs open in Firefox, it finally started using slightly more memory than Chrome with 11 tabs and CPU usage stayed in the 3% to 5% range.
You could say that I was impressed. Even with 30 tabs open, navigation within any of the tabs still felt faster than in Chrome.
Firefox has always been more customizable than Chrome, although Chrome has made significant advances. Firefox Quantum adds more interface customization and a new feature allows the user to specify which app opens in response to clicking various kinds of links -- from email and video files to images and zip archives. And if there's a Chrome extension that isn't available yet for Firefox, you can use a Firefox extension that allows running Chrome extensions in Firefox.
If you haven't used Firefox for a while, now might be a really good time to update it and give it a try. Prepare to be impressed.
If you've ever driven for Uber or used Uber to take you somewhere, a great deal of information about you is on computers operated by crooks. Uber made the breach public just before Thanksgiving, but they had know about it for more than a year.
Uber says that your information is safe. Why? Because they paid the thieves $100,000 to delete the files. And apparently somebody at Uber thought that crooks would actually take the $100,000 and then delete the data. These are crooks. They lie, cheat, and steal for a living. That's what they do. And Uber thinks they'll just quietly delete the data?
The breach affected information for about 57 million customers and drives. That was enough to get the attention of the Federal Trade Commission and also attorneys general in Connecticut, Illinois, Massachusetts, Missouri, and New York -- so far. Most states have laws that require companies to notify regulators within a few weeks when they discover a data breach. Uber had known about the breach for more than a year. This happened while Uber was under investigation by the Federal Trade Commission for failing to secure private customer data.
If you've driven for Uber, the crooks have your license number. If you've used the service, the crooks probably have your phone number, address, and name. Possibly more.
Consumers Union has become increasingly vocal about internet security and the lax attitude of far too many companies when it comes to protecting information about their customers. Tim Marvin, a campaign manager for the non-profit publisher says "Uber is just the latest in a string of prominent corporations to expose sensitive customer information. Our data security laws remain wholly inadequate to protect consumers from identity theft and other misuses of their data. In the case of Uber, the breach is even more troubling because the company has had multiple incidents and withheld this information from the public."
Consumer Reports has set up an on-line petition that urges Congress to investigate and Marvin says that the petition is important because "until companies are compelled to institute strong security measures, these breaches are going to keep on happening." If you sign the petition, you'll be offered email updates from Consumers Union. If you don't want to receive them, un-check the opt-in box.
Email scams continue to improve. Although they're still fairly easy to spot, the crooks are getting better at disguising them. I recently received a message from my “webmail administrator”, so I knew the message was a fraud. I am my own email administrator and I didn’t send myself the message. Let’s deconstruct this.
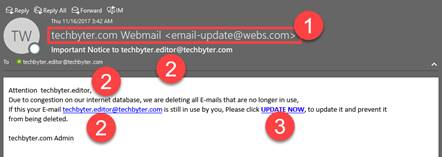
Here’s the link address:
![]()
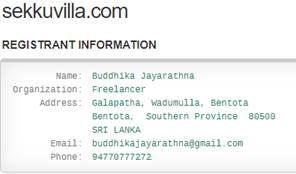
The link would take me to a web page at sekkuvilla.com and pass my email address to that page. What is sekkuvilla.com? It’s a domain that’s registered to someone in Sri Lanka.
Not knowing whether this was an attempt to plant malware or to steal credentials, I used a Windows PowerShell function to load the contents of the website into a text editor so that I could safely examine it. Here’s what I found.
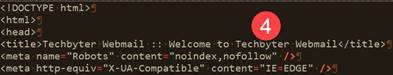
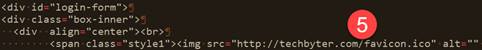
![]()
Overall, I have to give this scam an A+ for effort and attention to detail. Including the Techbyter name in the comments is clever because it could fool someone who knows enough to be able to examine the code, but not enough to recognize the scam for what it is. There was nothing in the code that looked like an attempt to plant malware, so the goal was to steal credentials.
And then what? Well, if the crook had the ability to send messages as me, social engineering attacks would be likely to follow.
The general rule applies here: Don’t click links in messages that ask you to confirm something. Instead, log in to the site as you normally would.