Everybody who knows anything about security has been complaining about the Internet of Things (IoT). Now we've had an example of why they're concerned, but nothing much will improve.
When the internet was developed as a private network for schools, the military, and corporations, secure protocols weren't considered to be important. After all, the network connected just a few organizations. When the internet became public, the lack of security was felt profoundly.
Secure protocols were bolted on and, if they're used correctly, can assure a reasonable level of privacy and security. One might have thought that the IoT would handle things differently, that the developers would have learned from the earlier mistakes.
But, no. For the most part, IoT devices have no security and because much of the code that runs the devices is embedded in hardware, it's unlikely that patches will be available anytime soon, if ever.
Last week, huge distributed denial of service (DDoS) attacks were launched. These attacks took down some of the most popular sites on the internet, including Twitter, Amazon, Tumblr, Reddit, Spotify, and Netflix.
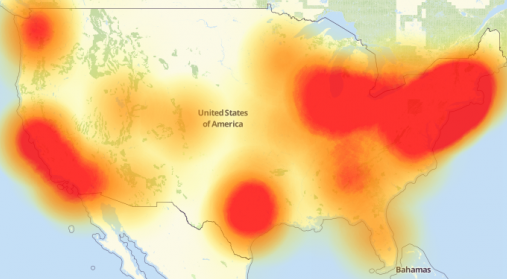
If you live anywhere in the red areas on this map, you had some severe connectivity problems last week.
Source: downdetector.com
The attackers launched their efforts from hundreds of thousands (perhaps millions) of devices such as security cameras, baby monitors, digital video recorders, and routers. This was possible because the idiots who designed these systems often enable default user names and passwords that cannot be changed by the users.
The attacks use software called Mirai and the person who created it has released the code, which means that anyone can use it to attack anyone at any time. Mirai crawls the internet looking for vulnerable devices and then includes them in its harem.
Chinese manufacturer XiongMai Technologies makes components that are used by virtually all other manufacturers, according to security expert Brian Krebbs, quoting security firm Flashpoint's director of research, Allison Nixon.
The attack was directed at Dyn (say it like "dine"). Dyn is a both a DNS provider and a host. As a DNS provider, it correlates the names we type into browser address bars with the IP address of the site we want to view. This site, techbyter.com, is 67.222.41.89, for example. You could type the IP address, but "techbyter.com" is easier to remember than "67.222.41.89".
The attack took down sites such as Amazon, Netflix, Reddit, Twitter, and a host of smaller sites several times. Taking down a company such as Dyn does more than just cripple one or two websites. As we saw this past week, it renders the network virtually ususable.
The first attack occurred about 7am Eastern time and that was followed by a second attack at noon and a third attack later in the day. Dyn needed most of the morning to respond to the first attack, which affected only the east coast. The second attack was intended to affect global operations, but Dyn shut it down within an hour. The third attack simply failed.
DDoS attacks send a continuous stream of requests to the victim. The victim must examine every request and attempt to respond to it. If the number of meaningless requests is sufficiently large, the victim cannot respond to legitimate requests.
In an ideal world, whenever an IoT device was set up and placed on-line for the first time, the device would force the user to create a new administrator user name and password, or at least a new password. Companies are probably reluctant to do that because users would do something wrong and then would need to contact the company for support. The result of that would be that the company would need to hire more people to work in support, which might adversely affect quarterly earnings, and that might endanger the CEO's ability to buy a new boat or summer home.
At one time we had federal agencies that were charged with creating regulations designed to avoid problems like this. So many of these agencies have been co-opted by businesses that they are supposed to regulate that idiotic situations such as this arise.
There is a real and present danger here. It's not going to get better on its own. If you're wondering what can be done, so am I. It seems to me that government agencies could force manufacturers to recall their defective products. There is a clear precedent for this: The National Transportation Safety Board (NTSB) can force automobile manufacturers to fix defective vehicles. The problem, of course, is equally obvious: Most of these devices are probably owned by people that the manufacturers cannot identify and, even if they could identify the owners, convincing people to take devices out of service and send them in for updates is unlikely to succeed.
So, welcome to the future.
If you're using your internet service provider's nameservers, maybe you should switch to another service. Some have suggested that this would reduce the effect of attacks such as the one that occurred last week. I doubt it, but there are some other advantages.
The DNS server is set in your MacOS or Windows settings if you have no router, but anyone who uses a router will want to look at the router's control panel.
While you're looking at your router's configuration, you should also change the default admin password so that Mirai won't take over your router and use it for bad purposes. Once you've done that, it's time to change the DNS settings.
The section of the router control panel you want to look at is probably called "internet" or "wan". You'll find a section for domain name server (DNS) address and that will probably be set to obtain the address automatically from your ISP. Instead, change this to an option that indicates you'll provide your own DMS servers.
There are several options. My preference is OpenDNS.

There are others you may want to try.
A reasonable question might be raised about the defensive capabilities offered by using a separate DNS server. A reasonable answer seems to be that it probably won't help much. After all, there are only so many large nameserver operations and swamping all of them wouldn't be a massive undertaking. Still, using a nameserver other than your ISP's nameserver will probably provide faster response and some of the alternates watch for misspelled domain names and either return an error message or deliver you to the site you really wanted instead of the one you typed. OpenDNS is one of these.
Alien Skin's Snap Art is one of the most effective ways to give photographs a complete makeover that can change the image's overall look. No effect can turn a bad photograph into a work of art, but often an effect can help to communicate the intended meaning of an image. Recently I wanted to modify a photograph in a way that would impart the meaning of childishness, so I applied a crayon effect to the image using SnapArt 4 and the effect was exactly what I was looking for.
No, I'm not going to show you that image for reasons that would become clear if I did show you the image. But I will show you the effect with another image. This time, lets imagine that you have a picture of a cat. After all, I have lots of pictures of cats. And then let's assume that you'd like to create an image that looks like it had been created by a child using crayons.
Here's my starting image in Lightroom. As with other current Alien Skin applications, SnapArt4 can be used in conjunction with Lightroom or Photoshop, or it can be used as a standalone application.
Why would anyone want to use an application that reduces the clarity of a sharp, clear photograph? That's an obvious question and it has an easy answer: Sometimes the extreme clarity produced by today's lenses and sensors doesn't fit the artist's expectation for the image.
Click either of the small images for a larger view.
Sometimes sharp images are exactly what's needed for a subject. In other cases, intentionally moving the camera during the exposure produces the mood and look that the photographer wants. SnapArt4 is used for the same reasons.
Many different treatments are possible, from color pencil and crayon to pointillism and watercolor.
For this image, I selected a crayon effect. My stated goal was to create an image that has the appearance of something created by a child. This would have been an image created by an astonishingly talented child.
And here's the result. Click the image for a larger view.
To make the image look more like a child created it, it would be necessary to first use some Photoshop magic, such as Liquefy, to modify the shape of the cat. Young children rarely get perspective right and preprocessing in Liquefy would add that dimension.
Alien Skin's SnapArt4 has a wealth of controls that can be used to individualize the modifications that are applied to an image -- increasing or decreasing photorealism, brush size, and stroke length, for example. Or modifying color variation, brightness, contrast, or saturation. And that's just the beginning.
Masking allows greater control of the painterly effects, so that you can reduce the effect in areas where you want more detail and increase it in areas where you want the effect to be more pronounced.
The next time you want to excite your inner artist, take a look at Alien Skin's SnapArt4. You'll find more information on the Alien Skin website.
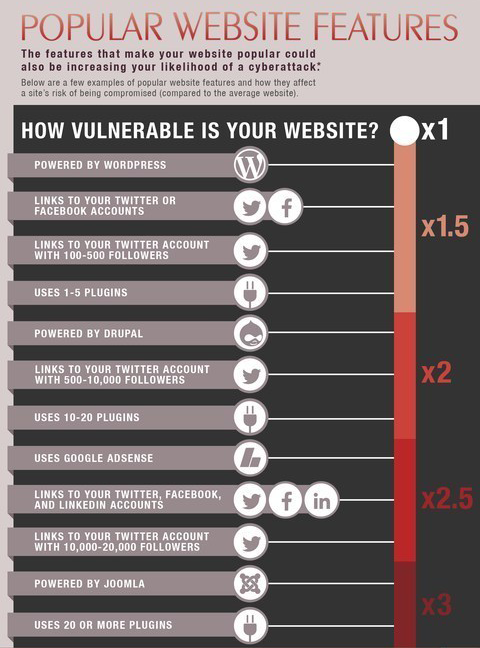 Every year more than three-quarters of a million websites are breached. The result may be the theft of sensitive and private information or it may result in malware being placed on the site. TechByter Worldwide uses SiteLock to monitor the server and the company says that some site characteristics increase the chances of an attack.
Every year more than three-quarters of a million websites are breached. The result may be the theft of sensitive and private information or it may result in malware being placed on the site. TechByter Worldwide uses SiteLock to monitor the server and the company says that some site characteristics increase the chances of an attack.
SiteLock scans more than 6 million websites every day and has found that sites are more likely to be attacked if they use certain technologies or have links to some social media applications.
Many websites offer highly engaging and complex features such as social media, e-commerce, and custom web applications, but these popular features may attract more than fans. They can also significantly amplify site vulnerability.
SiteLock says that a website is 2.5 times more likely to be compromised than the average website if it links to a Twitter account that has 10,000 or more Twitter followers. A website with more than 10 plug-ins is twice as likely to be hacked and a site with 20 or more plug-ins triples its threat risk.
There are clear warning signs that a cyberattack is underway, from slow load speeds to questionable data and obvious spam. For example, back door files account for 40% of all malware infections and give hackers the ability to alter a site's content. I have seen this happen to a site that went from being clean one day to having thousands of malicious files (and being shut down by the website hosting provider) the next day.
SiteLock has a variety of plans, from basic monitoring to automatic removal of malware when it's found. Many hosting providers have teamed up with the company. If you have a website, SiteLock is worth checking out.
Federal police agencies across Europe have joined in a project launched by the Dutch National Police and others to shut down ransomware. So far the agencies have helped more than 2500 victims decrypt their data, saving an estimated $1 million in ransom payments.
No More Ransom was created by the Dutch National Police, Europol, Intel Security, and Kaspersky Lab. Kaspersky Lab provides security applications to more than a quarter of a million business clients worldwide. Intel Security owns McAfee, another provider of protective applications.
The project was launched in July and now several additional federal police agencies have joined: the United Kingdom, Bosnia and Herzegovina, Bulgaria, Colombia, France, Hungary, Ireland, Italy, Latvia, Lithuania, Portugal, Spain and Switzerland. (Yes, Colombia is a Central American country.)
The operation's objective is to provide a helpful resource for victims of ransomware. Users can find information on what ransomware is, how it works and, most importantly, how to protect themselves.
During the first two months, more than 2500 people managed to decrypt their data without having to pay the criminals, using the main decryption tools on the platform (CoinVault, WildFire, and Shade). This has deprived cyber-criminals of an estimated $1+ million in ransoms.
 Since the launch of the portal in July, the WildfireDecryptor has been added and two decryption tools updated: RannohDecryptor (updated with a decryptor for the ransomware MarsJoke aka Polyglot) and RakhniDecryptor (updated with Chimera).
Since the launch of the portal in July, the WildfireDecryptor has been added and two decryption tools updated: RannohDecryptor (updated with a decryptor for the ransomware MarsJoke aka Polyglot) and RakhniDecryptor (updated with Chimera).
Ransomware is a top threat for EU law enforcement: almost two-thirds of EU Member States are conducting investigations into this form of malware attack. While the target is often individual users' devices, corporate and even government networks are affected as well.
Steven Wilson, head of the European Cybercrime Centre, says that Europol is committed to supporting the project within the EU and internationally. Despite the increasing challenges, he says, the project has demonstrated that a coordinated approach by EU law enforcement succeed by focusing on prevention and awareness.
In order to broaden the audience and improve results even further, the portal is currently being adapted to support different language versions. As a second step, the project developers expect to welcome new companies from the private sector.
Learn more at https://www.nomoreransom.org/.