Sending email from a hand-held device, while possible, is not likely anyone's first choice. Most of the email applications I've tried for my Android tablet and smart phone have ranged from OK to horrible. K-9 Mail seemed to offer the most features and then I encountered Aqua Mail.
Setting up e-mail accounts was surprisingly easy. Many apps do a good job if you're connecting them to Hotmail (now Outlook), G-mail, or one of the more common providers. I send and receive mail via my internet presence provider, so I need to set up accounts on blinn.com and techbyter.com. My preference is to use the IMAP protocol for portable devices and POP3 for my desktop system.
IMAP leaves messages on the server and POP3 downloads them to the computer. The app supports SMTP for sending messages and encrypted connections can be set up for both sending and receiving. Users who want to receive mail via their own domain but send messages using G-mail or their internet presence provider can do so. Aqua Mail is also supposed to be able to support Microsoft’s Exchange Web Services protocol, but I haven't been able to test that.
The free version supports up to 2 email accounts and adds a promotional notice at the bottom of each sent message. Upgrading to the Pro version costs $5 (a one-time fee) and makes it possible for Aqua Mail to be set up with more than 2 accounts. The promotional message is also omitted from sent messages and users can establish account aliases.
Users can view messages from each account individually or use a Smart Folder that shows messages from all accounts. The Smart Folder shows messages that have been sent, have been read, and that have arrived but have not yet been read. Messages can be marked with a star and Aqua Mail can be set to include or exclude these messages in the Smart Folder.
For an Android application, Aqua Mail has an astonishing number of features.
There are UI settings for the overall color scheme (light or dark), how many lines of a message will appear in previews, how the sender and subject are displayed, the size of type, and quite a bit more.
When I send a message from a mobile device, I almost always want to send a blind copy of that message to myself so that I'll have a record of it on the main computer. But I also frequently forget to do it. Aqua Mail makes this easy. Each account has an option to send a blind copy: Just select "BCC to self" and specify the address you want to use.
If you use G-mail, your email application will need to support OAUTH2, Google's preferred method for apps to log into your account. This keeps an app from needing to know, store, or transmit your password. Instead, at setup time, you select a G-mail account that's already present in the device's system settings and Aqua Mail will request permission to access the account's email messages. There's no need to enter your password into the program. This is also supported for Hotmail (now called Outlook).
 The Best Email Client I've Seen for Android Devices
The Best Email Client I've Seen for Android DevicesEven if I didn't want to be able to enable more than 2 accounts or use account aliases
and even if I didn't mind having the advertising message at the bottom of every sent message, I would pay the tiny registration fee. The price should be at least double what's being asked and probably even double that. Aqua Mail is an incredible bargain.
Additional details are available on the Aqua Mail website (or via the Google Play Store from your Android device).
The folks who brought us the Nigerian Prince scams are back with a new way to separate people from their money and Dark Reading executive editor Kelly Jackson Higgins says it's been successful in making millions of dollars for the scammers.
 The article quotes James Bettke, a researcher at SecureWorks, describing the crooks as "respected family men and leaders [who] are devoutly religious. They have Bible quotes on their desktops." And the scam itself is characterized as an evolved Nigerian scam.
The article quotes James Bettke, a researcher at SecureWorks, describing the crooks as "respected family men and leaders [who] are devoutly religious. They have Bible quotes on their desktops." And the scam itself is characterized as an evolved Nigerian scam.
Researchers got a look inside the operation when the man in charge of one group apparently infected his machine with his own malware. That left enough of a trail for sleuths to figure out what the group does and how.
The article says that scammers steal email credentials from legitimate business people so that they can intercept business transactions and send the money to their own accounts. "Unlike the traditional Nigerian 419 scams," Higgins writes, "this new generation of Nigerian scams is employed not by college-age scammers but by men in their late 20s to 40s, many of whom are considered pillars of society, active in their churches and communities."
Nigerian authorities reportedly are investigating the operation that's believed to make $3 million per year for the 40 or so people who are involved.
Bettke at SecureWorks says his people "stumbled across a web server with a wide-open web directory that contained screen shots and keystroke logs from the group's operation." Among those screen shots, Bettke says, were the scammer's instant messaging, Facebook, and bank accounts. "We saw their day-to-day operations."
Another scammer who was recently arrested appears to have made $60 million from business email compromise attacks and the FBI says that nearly 18 thousand known victims have reported losses of more than $2 million.
The full article is on the Dark Reading website.
Short answer: No. Slightly longer answer: Hell, no. Even longer answer: What kind of idiot would ask a question like that? Linux, which has generally been considered to be "safer" than Microsoft's Windows or Apple's OSX has some serious security shortcomings.
 I don't write about Linux a lot because it has such a tiny market share of desktop systems. Linux, however, is the de facto operating system of the internet. It also runs millions of Android devices.
I don't write about Linux a lot because it has such a tiny market share of desktop systems. Linux, however, is the de facto operating system of the internet. It also runs millions of Android devices.
Some 80% of Android devices are vulnerable and the flaw allows attackers to identify hosts that use the Transmission Control Protocol (TCP) and then either end the connections or stage an attack. Is this a new bug? If you consider a bug that was introduced in 2012 to be new, yes.
In a presentation at last week's USENIX Security Symposium in Austin, researchers from the University of California at Riverside described a flaw that exposes thousands of websites to attack.
The researchers injected code into a live USA Today page. The Linux bug is only part of the problem: USA Today doesn't use encryption.
Linux is the most common operating system for websites and this flaw means that thousands of websites (and probably millions of users) are at risk. Here's a long article about Linux security.
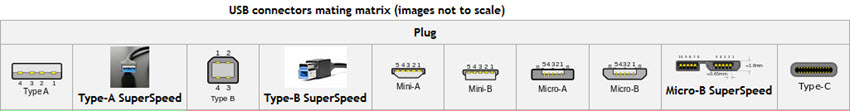
Many users think that a rule exists for USB plugs: No matter which way you try it the first time, you will be wrong. Sometimes a single rotation fixes the problem, but in other cases the plug needs to be reversed as second time. Fortunately some plugs have ridges or bumps on one side so the user can remember whether the bump should be up or down. But that's all about to change.
USB-C is a new standard that has been developed by the USB Implementers Forum. Some 700 companies are members of the group. USB-C is like Micro USB, but not quite. It's slightly thicker, so it won't fit in a Micro USB slot. It's faster because it supports USB 3.1, which is twice as fast as USB 3.0. The connections will be on some Apple devices even though Apple has Thunderbolt (for data) and MagSafe (for power).
In addition to the speed, USB-C doesn't have an up side or a down side. It will fit either way. It took only 20 years for the USB folks to figure this out.
The USB-C port can be used for DisplayPort, HDMI, power, USB, and VGA connections, but not Thunderbolt. Expect to see some Ethernet adapters that plug into USB-C slots, too.
One of the first docking stations available with the USB-C interface comes from StarTech. The dock works with any USB-C enabled laptop, such as the new MacBook Pro, Dell XPS, or Chromebook Pixel to connect with peripherals so that it can be a full desktop workstation. The dock supports power delivery to the laptop and the devices connected to it, so only the dock's power adapter is needed to power the laptop and devices, eliminating the need to have a power adapter for each device. With MST technology enabled, the laptop screen can be expanded to two DisplayPort monitors.
For more information, see StarTech's website.
The Shadow Brokers, a group of hackers, wants the National Security Agency to pay then 1 million Bitcoin (that's more than half a billion dollars) to recover some "cyber-warfare" technology.
The group claimed to have hacked its way into the "Equation Group", which is thought to be a front for the NSA.
Their message, which not particularly grammatical, was clear enough: "Attention government sponsors of cyber warfare and those who profit from it !!!! How much you pay for enemies cyber weapons? We find cyber weapons made by creators of stuxnet, duqu, flame. We follow Equation Group traffic. We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons."
Cyber weapons are considered to be "good" if we use them. For example, the US and Israel are implicated in the Stuxnet attack against Iran. Cyber weapons are considered to be "bad" if somebody else uses them against us. The illogic of that would have been apparent to George Orwell, the author of Nineteen Eight-Four.
Computer firm Kaspersky has provided evidence that links Equation to the NSA and to Stuxnet.
The Shadow Brokers posted some of the data they stole, including installation scripts and configuration files for command and control services. They included names of some tools that match those revealed by Edward Snowden in 2013. But that raises a question about whether they have the information or they're just mimicking information that's already public.
So far, the NSA isn't paying and it's unclear whether this represents an actual breach or is just an audacious fraud.
The Social Security Administration announced plans last month to strengthen security on its website. Account holders were told that they needed to provide a cell phone number that the SSA could use to send an 8-digit code that the user would need to provide at log-in time. The announcement was not met with enthusiasm.
Just about any cell phone, even one that's 10 years old or even older, would be able to accept the text message. Probably some people didn't know that and the SSA didn't explain it well. Now the phone requirement has been removed.
The agency has posted a message on the site noting that it has removed the requirement to use a cell phone to access accounts, but that it's still recommended. "We encourage those of you who have a text capable cell phone to take advantage of this optional extra security. We continue to pursue more options beyond cell phone texting."
The SSA neglected a low-tech solution: Sending a one-time code by using the US Postal Service. That, in fact, would be more secure because the recipient of the message would have to be physically at the location on the envelope. The SSA could simply add the security component to messages that are already being sent out when people sign up on line.
The problem with the phone security option is that anyone can sign up and provide any phone number. That's really not secure. Thieves can still create an account for anyone who doesn't have an account.
So if you have a Social Security account and you have a cell phone that can accept text messages, adding the security option is a good idea.
During the sign-up process, the SSA uses several knowledge-based questions to authenticate a person's identity. These include questions about previous addresses, loan amounts, and other information that most people believe would be known only to the person signing up for an account. But Equifax knows the answers. That's the service the SSA uses to check your answers. Crooks can gain access to that information and can use Facebook and other social media to investigate a person's history.
Safety is not assured.
Even if you're nowhere near the age when you'll need to sign up for Social Security, there's nothing to keep you from signing up right now. The SSA allows only one account to be created for any Social Security number so once you've created an account for your number, no crook can create an account for your number.