Using a virtual private network (VPN) is essential if you ever connect to the internet via a public Wi-Fi hotspot or even if you connect to the internet via somebody else's private Wi-Fi hotspot. Cost is no longer a factor.
For infrequent users, services such as Private Internet Access may seem too expensive at $40 per year. There's an alternative that has a very attractive price: FREE. Yes, there's a "catch". Let's take a look at Private Tunnel.
If you're a geek, you can set up your own VPN server at no cost. This is not something that most people will want to do because you'll need a server that's running a firewall application or you'll need to configure your ISP's firewall to pass traffic to the VPN server. Once you've done that, you'll need to select a VPN technology that's available on your firewall, on VPN server, and your personal computing devices. Forget that!
So you're looking for a service that you can use. Commercial services exist and previously I've described Private Internet Access. It costs $40 per year and is an excellent value for people who travel frequently or use coffee-shop Wi-Fi hotspots on a regular basis. If you're not in that group, $40 might seem like too much.
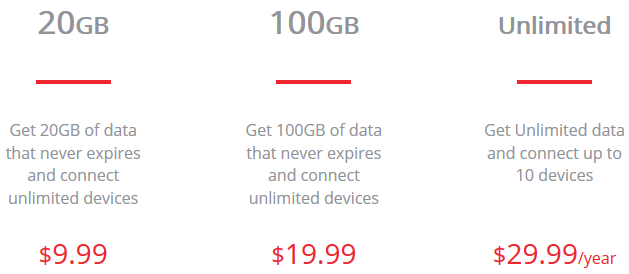
Private Tunnel is what you're looking for. Create an account and download the app for your device. The first 2GB of data will cost $0. The limitation is that you can choose only the PT server in Chicago. And you're already wondering what happens when you hit the 2GB limit. When that happens, you can buy additional data: $10 for 20GB or $20 for 100GB. Not per month. Whatever you buy is good forever and you can use the service on any Windows or Mac computer or any Android, IOS, or Windows mobile device.
If you do travel a lot, consider the $30 annual plan. In that case the amount of data is unlimited, but you can't connect more than 10 devices. Do you have more than 10 devices? For many people, the $20 will probably last several years if used judiciously. If you're a paying client, you can choose from VPN servers. This means that you can appear on the internet to be at any of several locations in the United States or at several locations outside the US. While that feature is useful, the more essential feature is encryption. When you're sending or receiving email, or connecting to websites, all traffic is encrypted.
When I wrote this article, I was in the waiting room of an auto repair shop while my car was having its oil changed, its tires rotated, and several other routine maintenance actions performed. The Wi-Fi in the waiting room was totally open. Nobody in the room looked suspicious, but you never know. I started Private Tunnel because I knew that I would be connecting to my email server and also to other services that should not have credentials sent in plain text.
Private Tunnel looks about the same on a Windows PC as it does on a Mac.
On an Android device, you'll have a full-screen page to connect (left). When the connection has been made, the Android operating system will display a lock icon at the top of the screen (right).
The ease of connecting and disconnecting is a plus for the service because users can easily turn the service off when they're on a corporate network or their own home network and turn it on with just a couple of clicks when they need to connect via a public Wi-Fi hotspot.
Private Tunnel is operated by OpenVPN Technologies, a privately held company in California. Currently more than 4 million people use the service and OpenVPN Technologies says that about 100 thousand new users sign up every month.
 You Need a VPN and Private Tunnel Is a Good Choice
You Need a VPN and Private Tunnel Is a Good ChoicePrivate Tunnel's $10 and $20 plans are perfect for people who use public Wi-Fi hotspots infrequently because the data limits never expire. For those who travel frequently or use
public Wi-Fi hotspots every day, the $30 annual plan would be a good choice. Earlier this week, the free plan ran dry, so I signed up for the $30 annual plan. Anyone who uses public Wi-Fi hotspots should use VPN technology. Not doing do is both negligent and dangerous.
Additional details are available on the Private Tunnel website.
Not so long ago, the most serious threats we encountered from scammers involved people pretending to be Nigerian princes or crooked bankers who wanted your help to get millions of dollars out of the country. Those threats were ineffective if the targeted victim had any common sense, but the threats are a lot more dangerous now and much harder to avoid.
Ransomware is one of the most dangerous threats and even that threat is evolving. Until recently, the crooks were at least honest crooks. Those who paid the ransom received a code that allowed them to decrypt their files. Now a growing number of crooks take the money and run.
The crooks are finding better ways to get their malware onto computers and increasingly they are targeting big businesses.
The FBI handled nearly 2500 complaints about ransomware last year. That's up from about 1500 in 2014. Losses were estimated to be more than $1.6 million and it's likely that the number of incidents and the losses were actually much larger.
Scammers typically asked for just a few hundred dollars when they locked the files on a small company's or individual's computer. Now they're going after hospitals and school systems.
Hollywood Presbyterian Medical Center paid $17,000 to regain access to systems after an attack that shut down their communications systems for 10 days.
The Horry County School District in South Carolina paid $8500 to recover the use of hundreds of computers. The initial intrusion was spotted quickly, but it put some 60% of the school district's computers out of operation in minutes.
The first thing you should do is shut down the network. Then determine which machines have been infected and take them off the network. Once you're sure that you've identified and removed all infected machines, it's probably safe to enable the network again.
ZD Net recently wrote about a free ransomware response kit that includes a suite of tools that may be able to help.
Decide whether you will pay the ransom or not. Some experts recommend paying and some say that this only encourages the thieves. Given that some of the crooks won't unlock your data even if you pay, refusing to pay is becoming a more rational option.
If you have a good backup system, check to see if critical files can be restored.

Swiss security company High-Tech Bridge offers several free security tools that can be used to test your network: SSL/TLS Server Test checks your servers for security and compliance with certain standards, Web Server Security Test examines your web server for compliance with Open Web Application Security Project (OWASP) guidelines, and Domain Security Radar help identify typo-squatted, cyber-squatted, and phishing websites that are designed to look like yours. Some other recommendations:
The danger is real and the consequences can be fatal to a company.
Chinese browser publisher Maxthon has released a beta version of its new MX5 browser and some users are raising concerns about privacy and security. The browser offers more features than Firefox, Chrome, Edge, and Internet Explorer, but some of those features make users nervous. Maybe even paranoid.
Maxthon chief executive, Jeff Chen, writes the company's blog. He says that the primary goal is to be an "information assistant" for users and he cites 3 features designed to do just that: An "infobox" allows users to save web pages in the cloud, a password manager is built in, and the browser offers a way to create email aliases that can help insulate the user from spam.
If you think that these features sound like you'll need an account to use them, you're right. You can't use the Maxthon browser until you set up an account. Security firm Exatel published a report almost immediately after the original beta version was released. Exatel reported that Maxthon collects sensitive user information and sends URLs Maxthon's server. That is, in fact, part of the company's user experience improvement program (UEIP). But you can turn it off -- or you're supposed to be able to turn it off.
Most applications have similar options these days, limited to sending usage and crash reports for analysis so that developers can improve them. Exatel reported that turning the UEIP function off had no effect.
Chen says that the Exatel report revealed a bug in the code. "Users are supposed to have full control when it comes to opting in or out of the UEIP. If a user opts out, the UEIP is not supposed to collect information. However, upon investigating the situation based on the Exatel report, we located a bug in our 2007 code library. We have immediately fixed this bug. We thank the Exatel team for helping us identify the problem."
The UEIP concept isn't unusual. Adobe does it. Microsoft does it. Most on-line applications do it. Maxthon describes its UEIP policy in its terms and condition. Chen and Exatel both note that the information Maxthon collects is designed to improve the user experience by better configuring the software users run in the system.
But does Maxthon send URLs to the Maxthon server? Yes, but Maxthon doesn't store them unless you're storing a page in the infobox. As with other browsers and security applications, the URL is evaluated to determine whether the website is safe. Some other browsers have similar functions and Chen says that the security checks "have prevented users from visiting millions of fake and malicious websites since 2005." Even so, an option will be added to allow users to turn off the scanner.
I have used the Maxthon browser in the past and have generally found it to be well designed. I'm looking at the new MX5 so a full review will be coming. Maxthon's goals are impressive:
Unlike most browsers that pick one rendering engine or the other, Maxthon uses both Trident and Webkit so that it's able to render just about any page, old or new, properly.
You'll find the occasional spelling in menus and configurations, but that's to be expected from a browser whose developers do not speak English as their primary language. Give me a couple of weeks as Maxthon rolls out additional updates and I'll let you know what I think.
Microsoft released the promised anniversary edition of Windows 10 on the second of August. It installed without a problem on the notebook that's been running the insider preview. Likewise on the Surface tablet. Not so on the production desktop system, though.
The desktop just sat there looking at me, so I told it to go check for updates and it told me there were none.
Then I drilled down through the menus and found a "Get the Anniversary Update" link. Clicking that opened a browser and allowed me to download a small installer. CPU OK, it told me. Memory OK. Disk space OK. But then "!Display: The display is not compatible with Windows 10. Check with the manufacturer for support."
So the monitor (although not brand new, not very old) that's been running just fine with Windows 10 for a year isn't compatible.
Thinking the message might have been a fluke, I repeated the process with the same result.
The message specifically pointed to the monitors, but maybe it's actually seeing a problem with the video subsystem's drivers. An update existed for the Nvidia graphics card. After downloading and installing that, I learned that Windows 10 still didn't like my monitors.
A quick detour to the device manager showed that the monitors were "Generic PnP" and not Asus monitors. Asus had no updated software and Windows shouldn't need any help identifying the monitors because the color management system I use, Colormunki, correctly identified them.
An hour on the phone with a Microsoft support technician didn't resolve the problem. We're both pursuing some additional possibilities, some of which will be very time consuming.
So around here we're 2 for 3 and I expect that to increase to 3 for 4 when I run the update process for my wife's computer. When the process works, it works very well. Admittedly my desktop computer is a special snowflake because of everything that's installed on it -- both hardware and software -- so I expect that the update will go well for most users.
A couple of items this week about video. Let's start with Kodak's hardware that lets you keep an eye on Fido or Fluffy and then move on to a Russian internet service provider's application for tiny video shorts.
The Kodak Connected Family Home system makes it possible to keep an eye on your home when you're not there. Now it's been expanded with the addition of the Pet Highlight Reel to allow the CFH-V15 camera to turn video clips into a montage that you can save or share. Fido and Fluffy will no longer have any privacy.
Tend Insights developed Kodak's connected home system and the update allows that system to recognize animals and compile recorded clips into video montages. Not only can you watch your pets, but you can talk to them using two-way talk-back audio via the Isecurity+ app accessible from any smart phone, tablet, or computer. Watch streaming HD video and control the pan and tilt functions.
The system connects to any Wi-Fi network and a battery-power option makes it portable. Automated editing allows users to create and share polished videos of their pets without prior editing expertise or practice.
The Kodak Video Monitor CFH-V15 with Pet Highlight Reel is available for about $100. For more information, visit PetHighlightReel.com.
Halfway around the globe, the Mail.Ru Group wants you to try its neural network-powered app to process videos. It's called Artisto and it uses neural networks for editing short videos and processing them in the style of famous artworks or any other source image. The app is available on App Store and Google Play globally.
Artisto now processes 5-second videos and offers 14 filters to choose from. New filters will be added later. Mail.ru is, as you doubtless suspect, is headquartered in Moscow and is one of Europe's largest internet service providers.
In machine learning and cognitive science, artificial neural networks (ANNs) are inspired by biological neural networks -- in other words, the central nervous systems of animals and in particular, the brain. A neural network attempts to approximate functions that can depend on a large number of inputs that are generally unknown.
Anna Artamonova, a Mail.Ru Group vice president says that neural networks are attracting a lot of attention now and that they were eager to test out stylization capabilities such networks provide. "There are a few very neat solutions for redrawing photos," she says, "so it was only logical to try our hand at video."
The app is now available for both Android and IOS devices.