You've probably seen email described as having the security of a post card. Actually, it's worse than that. After you mail a postcard, it will be handled only by the US Postal Service (and, if you've sent it to another country, by that country's postal service). Plain-text email can be intercepted and read at many locations by many people.
Encryption makes your messages more secure at the added cost of some complexity. Applications such as GPG4Win and Mac GNU Privacy Guard strive to simplify the process, but do you need it?
For routine messages ("meet me for lunch at noon under the clock"), probably not. But if you send messages that contain user names, passwords, financial data, proprietary commercial information, personal identification information about others, or any information that you don't want to see on the front page of a newspaper, encryption is essential.
Encryption is the envelope that protects your message from being read by others. Whether you use it, when, and for which messages is up to you. Software such as GPG4Win simply gives you the right to choose.
Although what happens behind the curtain is immensely complex, the overview that describes what happens is easy to understand and that's my primary point today.
Imagine a key. It can be used to lock or unlock a door. If you want somebody else to be able to see what you have in a locked room, you have to provide a copy of your key to that person. In the real world, that's easy enough: You just hand the other person a copy of your key. But how can you send a copy of your email key securely? You can't. By the way, this kind of encryption is called "symmetric" encryption because the key that encrypts/locks a message is the same key that decrypts/unlocks the message.
The limitations are obvious, so another method is needed.
GPG uses the concept of a "public key" and a "private key" to solve the problem of key exchanges. You create a private key (nobody but you will ever know what it is) and a public key that can be given to anyone. The two keys are inextricably connected with a complex mathematical formula, but you can't use one to figure out what the other is.
A public key is used to encrypt messages while a private key is used to decrypt messages. If I want to send you a private message, I need to encrypt it with your public key. When you want to read the message, you decrypt it with your private key. As I mentioned earlier, what's going on in the background involves some uncommonly complex math, but from the user's perspective, the process is really just as simple as encrypting with the receiver's public key and decrypting with the receiver's private key. This process is called "asymmetric" encryption.
The private key is a file that is stored on your computer. To prevent unauthorized access of this file, it is secured in two ways: First, no other user may read the file or write to it. This is difficult to ensure because the computer's administrators always have access to all files. Also, the computer may be lost or attacked by viruses, worms, or Trojans. A second method is needed to protect the private key, a pass-phrase; just like a password, it should be complex, impossible to guess, and easy to remember.
A pass-phrase can be discovered programmatically by bad guys if it's something you already use for an email account or your mobile phone; if it's a word that can be found in a dictionary; if it uses a birth date, a name, or other public information; if it's a common quote ("to be or not to be"); or if it's no more than 8 characters long.
You've received an encrypted message from me. How do you know I am who I say I am? When you want to send an encrypted message to someone you don't know personally, how can either of you vouch for the other? There are two methods available.
This is my public key.
Secure/Multipurpose Internet Mail Extension (S/MIME) requires that your key must be authenticated by an accredited organization before it can be used. The certificate of this organization is then authenticated by a higher-ranking organization until the process reaches the root certificate. This hierarchical chain of trust usually has three links: the root certificate, the certificate of the issuer of the certificate ("CA" for Certificate Authority), and finally your own user certificate.
Alternatively, the OpenPGP standard builds a web of trust. For example, if User 2 trusts User 1, then User 2 could also trust the public key of User 3 if the key has been authenticated by User 1. I know Joe and you know Joe; he vouches for both of us, so we can trust each other.
Even though OpenPGP and S/MIME are not compatible, PGP4Win allows for the use of both. As we delve just slightly below the surface, we'll stick with OpenPGP.
GPA is the application used to create keys and the GPG4Win key manager is called Kleopatra.
Once you've created a key pair, you need to distribute the public key. Everyone should have your public key, and you should have the public keys of everyone you correspond with. To exchange secure messages, both partners must have and use the public certificate of the other person. Additionally, the recipient of your encrypted messages must have a program such as the GPG4Win with Kleopatra certification administration. An additional option involves publishing your public key on an OpenPGP server.
If you're interested by the idea of being able to send and receive messages securely, GPG4Win is a good choice. It's free and it comes with a 180-page manual that covers installation, use of Kleopatra, instructions for both OpenPGP and S/MIME X.509. And that's why I'm not even going to try a deeper dive on encryption here.
Clearly, for an application this complex, TechByter just can't provide complete documentation, but perhaps I've provided just enough information to get you started.
Backup is important. Perhaps you've noticed that it's one of the things I frequently talk about -- "yammer on endlessly about" might not be putting too fine a point on it. Security, another "yammer on endlessly about" topic and backup work together -- security to avoid problems and backup to recover from problems.
If you back up to an internal or external hard drive that's stored in the same building as the computer, effectively you have no backup. That's the allure of cloud-based backup. But restoring from cloud-based backup is relatively slow. The best solution is probably more than one backup.
I've described my system previously:
Having both local and cloud-based backups seems to be gaining favor among small and medium businesses.
A survey by Clutch, a business-to-business research firm says that 42% of survey respondents feel that local backup is more important than cloud-based backup. After all, if you have just a single cloud-based backup, you're depending on somebody else's business to be able to recover your data in an emergency.
The Clutch survey says that more than 60% of small and medium businesses have adopted cloud-based backups in the past 2 years. Despite this, nearly 90% of them continue to back up their data on-site in addition to on-line. In my opinion, that's smart.
Mark Anderson, the IT strategist at Anderson Technologies, says "it's natural for business owners to take a cautious approach to adopting technology, especially when it comes to securing their critical business data."
SkySync's chief technology officer compares cloud-based backup to a double-edged sword. "Some small business IT teams will be familiar with the workings of the cloud while others may be afraid of the unknown."
SMBs that back up data in the Cloud tend to choose consumer-facing solutions according to the survey. Apple iCloud (47%), Google Drive (36%), and Dropbox (35%) rank as the top three on-line backup services used by SMBs. All three typically meet the more basic backup and data recovery needs of SMBs.
These solutions are popular in the SMB market because employees are often familiar with the options, having used them elsewhere or for personal data management. This often influences an SMB's IT team to apply the service throughout the company, a practice Steve Woodward of SkySync calls, the 'bring your own service' approach.
The full results of the survey are on the Clutch website.
If you haven't given your backup strategy much thought for the past year or two, now would be a good time to review the plan.
Windows 10 brought back the full Start Menu, but with some additions that give you a lot more control than you had in the past.
Windows 10 offers 4 sizes for Start Menu tiles. Microsoft calls them small, medium, wide, and large. Small shows just the icon and large is often useful only with applications that show additional information -- news updates, weather, or your calendar, for example. In between the medium size shows more information than the small icon and the wide size, as you undoubtedly suspect, is wider than it is tall.
Switching among sizes is easy. Right-click if you're using a mouse or press and hold if you're using your finger, then choose Resize from the context menu. You can also remove the icon from the Start Menu by choosing Unpin or add it to the Task Bar from here.
But that's just the beginning. You can also change how much of the screen that the Start Menu will occupy. My preference, even when I'm not using a touch-enabled computer, is to run it full screen. If that's not your preference, you can make small adjustments by selecting the side or top of the Start Menu's outer edge. Once you've done that, you can drag to make the menu larger or smaller.
To make the Start Menu fill the screen, visit the Settings app, select Personalization, and then choose Start and turn on "Use Start full screen." Another option that was added recently is the ability to show 4 small icons across instead of 3 as it was previously. I prefer this because it works better with combinations of icon sizes. To enable this, turn on the "Show More Tiles" option while you're in the Start Menu section of Settings.
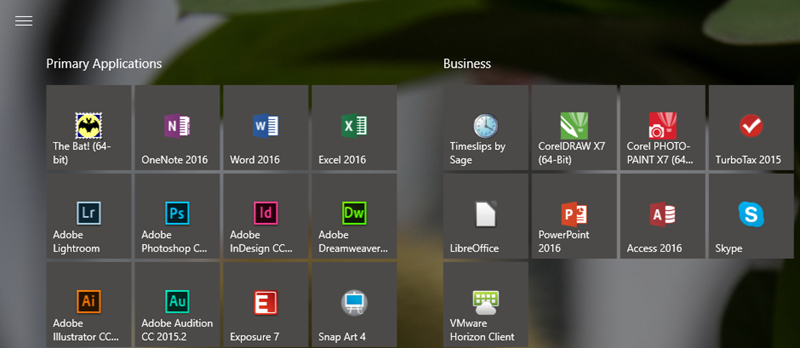
The 4-icon arrangement is more flexible.
Incidentally, Microsoft pushed out what will be one of the last Windows Insider previews before the anniversary update in the fast ring at the end of June. The current fast ring version is 14379.rs1_release.160627-1607 and it consists mainly of bug fixes. Some applications, both Microsoft and third-party, failed to function under an earlier release, but those problems seem to have been remedied. Other changes according to the Windows team:
Hummer (no, not the stupidly large SUV that can't get out of its own way) is malware that could be on your Android phone or tablet. Some research labs call it "hummingbird" instead. At least that sounds less threatening. The good news, at least if you're in the United States, is that it seems not to be a big threat.
Not so, though, in China, where it originated or in India, Mexico, Turkey, and Indonesia. At its peak, Hummer was infecting nearly one and a half million devices per day. The number of new infections is declining now, but more than one million Android devices are thought to be infected according to security researchers at Cheetah Mobile Security Research Lab.
A message on Cheetah Mobile's blog says that the virus developer could be collecting more than half a million dollars per day. The malware roots the phone to gain high-level privileges. Users will see pop-up ads and the background installation of unwanted apps. Uninstall the apps and Hummer will just reinstall them.
Some phones with the infection have downloaded 2 GB of data in a single day. If you have a small data plan that charges extra when you go over the limit, this could be a very expensive problem.
Cheetah says that the Hummer family of malware has 20 or so different root methods, so normal protective applications can't remove it, and even a factory reset won't eliminate the problem.
A Swiss company says its newly developed technology allows your plants communicate with you. PhytlSigns is described as "wearable tech for plants." I checked the calendar and April First was quite some time ago. Developers say the device listens to what the plant is communicating rather than simply measuring the air temperature or the soil around it.
 OK. Actually, we do know that plants can communicate with each other. Perhaps not in a way that humans would think of as communication, but it happens.
OK. Actually, we do know that plants can communicate with each other. Perhaps not in a way that humans would think of as communication, but it happens.
The device is available from the crowd-funding platform Kickstarter for $135.
The device works by amplifying the electrical signals that plants use to communicate internally, allowing people to hear them via an attached speaker and see their communications via an app on a phone or tablet. After watering the plants, you can observe how they are reacting to their environment.
The device's creators say the device is for keen gardeners and plant enthusiasts, techies who are into signal processing, professional growers, and academics who work with plants. But wait, as they say, there's more: Hearing and seeing what plants are telling us is just one part of the PhytlSigns story. Inventor Nigel Wallbridge says that analyzing the signals our plants are emitting allow us to "unlock the messages within them and ultimately decode the language of plants." Is a plant under attack from pests? Does it need water? "Understanding what our plants are saying is exciting for everyone," Wallbridge says.
You'll find more information on the company's website.