In July, Microsoft will release an "anniversary update" that will include a lot of new features. Those who are participating in the Windows Insider program, have seen numerous recent updates with only minimal visible changes. That's because developers have been working on the framework that will hold the new features. This week Microsoft released Preview Build 14316 in the Fast ring.
The Fast ring is not for production machines. In other words, don't install Fast ring builds on any computer that has information you care about. I use a notebook computer that sees a fair amount of use but contains no irreplaceable files as a Fast ring machine. The desktop and Surface tablet stay safely behind with general release code.
The new build includes some excellent clues about the future of Windows.
The bash shell from Canonical's Ubuntu (Linux) is available as a native interface on Windows 10. Huh? Linux is a Windows competitor and Steve Ballmer, the (thankfully) former Microsoft CEO, once famously called Linux "a cancer". The two companies collaborated to build the Windows Subsystem for Linux, but Linux is a competing operating system -- open source where Microsoft is closed, free where Windows isn't. What's going on here?
Developers need to activate "developer mode" first (Settings > Update & Security > For Developers; search for "Windows features", choose "Turn Windows features on or off", and then enable "Windows Subsystem for Linux (Beta)"). Bash can be installed by opening the Command Prompt and typing "bash". This swaps the Linux kernel for the Windows NT kernel.
Bash is a Unix shell that Brian Fox wrote in 1989 for the GNU Project as a free replacement for the Bourne shell. It's present on most Linux computers and you'll find it on Apple computers. Now it's about to become a part of Windows.
This isn't a new concept. Windows users have been able to download and install Cygwin and MinGW, so you might wonder why Microsoft decided to make it available to Windows users (and currently only to users on the Fast ring of the Insiders program).
Peter Bright, writing on Ars Technica, has some thoughts. On the Surface, Bright notes that developers like bash and keeping developers happy is good for Microsoft. But that's not the whole reason.
Fifteen years ago, Windows was the only serious development platform. OSX has just arrived, but Apple's computers ran on underpowered Motorola processors. That has changed.
Apple computers are more price competitive with Windows computers and Macs run on top of the operating system that runs the Internet. Website development in particular needs access to Unix/Linux tools and bash is part of the package. Installing these tools on a Windows machine has been possible, but not always easy.
Perhaps Microsoft is trying to get ahead of the future.
Read Bright's full article on the Ars Technica site.
Bash is one of several Unix/Linux shells. It's a command line interpreter that dates back to 1989 and is the most common shell used on Linux machines and Apple's OSX computers.
As a command processor, bash usually runs in a text window. Users can type commands, but bash can also read instructions from a script. Bash's keywords, syntax, and other basic features come from sh, the original Unix shell and some advanced features came from csh and ksh.
Unix developers are lovers of puns and acronyms; bash is both. It's pronounceable, so it's an acronym. The expanded acronym is "Bourne again shell", which is a religious pun, but the pun is descriptive because bash is a free version of the Bourne shell. Adding one more layer, "bash" describes how the shell was created: By bashing together sh, csh, and ksh.
Microsoft's Edge browser finally gets some extensions. Two extensions come with the preview build, Pin It and OneNote Clipper. Users need to install the extensions by clicking the elipsis (…) icon in the top right corner of the browser, selecting "Extensions", and then choosing "Get extensions".
Build 14316 breaks any extensions already installed, but you should be able to download new installation files and re-install existing extensions.
The next general release version of Windows will do a better job of conserving battery power. Under the "Battery" option of the Control Panel, you can now manager overall battery settings and then drill down to the "Detailed Battery Use" panel to manage background settings for each application. The "Managed by Windows" option prohibits programs from running in the background when Battery Saver mode is enabled and also temporarily suspends applications that haven't been used recently. Windows will suggest turning Battery Saver mode on when the batter has only 20% capacity remaining.
Speaking of the Control Panel, Windows 10 continues to have 2 Control Panels: A limited Control Panel that's available via the Modern interface but doesn't include all settings and the older Control Panel that contains all of the settings. Battery settings are in the old Control Panel.
Microsoft has finally admitted that the Action Center can be annoying. The new build allows users to select the alerts appear. When you select an application in Settings > System > Notifications & Actions, you'll be able to set notifications to one of three options: Normal, High, and Priority.
Personalization gets an improvement in Build 14316, too. Dark and light modes are available from Settings > Personalization > Colors. Making changes here will modify apps that use the Universal Windows Platform, but some third-party apps won't change even if they're UWP enabled. You can also select a color theme for the Start menu, Action Center, and Task Bar.
Google is eliminating what some considered to be "free" Internet service in Kansas city. It wasn't really free, but it did involve a one-time fee and was then supposedly without charge after that.
That plan is going away. Google Fiber will still offer 100Mbps service for $50 per month. Compare this to what you're paying for service that's probably a fraction of that speed. The other options are $70 per month for 1000Mbps. That's almost enough to get me to move to Kansas City. And if you want to pay $130 per month, you get 150 TV channels with the ability to record up to 8 programs at once in addition to 1000Mbps Internet service and 1 terabyte of cloud storage.
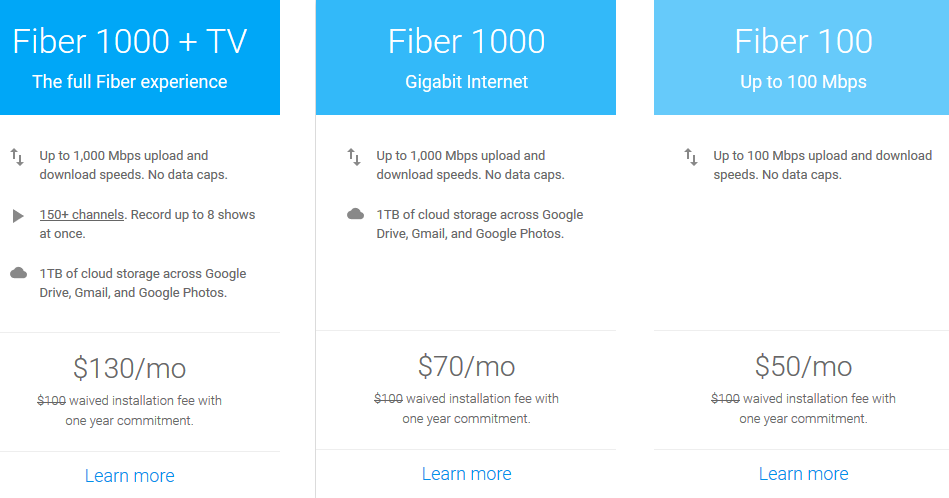
It annoys me to pay more than the highest price in Kansas City and get service that's only 1/50th of the speed in Kansas City. Even the "slow" Kansas City speed is 5 times faster than what I have.
The free service that's being discontinued topped out at 5Mbps, which is slower than what I'm paying a whole lot more than $0 for. If you're in another city where Google offers the free 5Mbps plan, you should probably expect that it will be eliminated before too long.
Except for confirming the changes, Google hasn't said anything about its reasons for the change. The free plan required a $300 installation fee. Google called it a "construction fee", so the very people who would be most likely to want a free service probably had trouble coming up with the "construction fee". And Google Fiber won't tell anyone how many customers it has on the "free" plan.
For the standard services, Google would normally charge an installation fee of $100, but those fees have been waived for at least the next year. Google, when are you coming to Central Ohio?
Fiber users who are on the free plan have until May 19 to decide what to do. Apparently Google is committed to continuing the free service for 7 years and the first "free" subscribers signed on in 2012.
Ransomware is big news and big business. It's big news because several hospitals have been victims of ransomware attacks. Some have paid the ransom. Some have managed to recover without paying the ransom. Some, undoubtedly, have not admitted that their systems have been compromised. It's big business because the crooks can extort a lot from a hospital.
Malwarebytes published guidelines this week on its blog to avoid being victimized.

"As dangerous as ransomware can be," Malwarebytes points out, "it’s not insurmountable. So instead of closing your eyes and praying it all goes away soon, take a look at this infographic to see what you can do to protect your business from this pervasive threat."
The infographic points out that "[the] FBI and other law enforcement officials might encourage individuals and businesses to pay the ransom—it's the quickest way to retrieve your files. However, cybersecurity professionals don't recommend it. There's no guarantee that paying the ransom will give you access to your files again. Also, it makes you a target for future malware infection."
Clearly, prevention is better, but there's good news even if ransomware gets through. The good news is that "if you've been responsibly backing up your files, not all hope is lost. Scan your backups for malware on another PC that isn't infected. Then run a scan on the infected machine to clean any traces of ransomware or other malware. If your backups are clean, you can restore them to your computer."
The company recommends a 4-step approach:
Step 2 is one of the most important steps. A large company I'm familiar with received hundreds of spams this month. Each message referred to an invoice and told the user to open the attached document. The document was a Microsoft Word file with macros enabled. A single glance should have made it obvious that the sender was up to no good: You've never heard of the company, you don't deal with accounts payable for the company, and the attached document is macro enabled (the extension is "docm"). Would you open this attachment? The right answer is NO.
You might consider step 4 to be somewhat self-serving because Malwarebytes provides anti-exploit, anti-malware, and anti-ransomware applications. I consider it to be good advice whether you use Malwarebytes applications or not. In addition to the anti-virus application installed on my computers, I use Malwarebytes as an extra layer of security.
Apple stood up for privacy, but the FBI found a workaround. Now Microsoft is fighting back against what some privacy experts see as government threats that, while intended to make us safer, might actually have the opposite effect.
Microsoft is suing the Justice Department over the use of secrecy orders that bar Microsoft from telling people when the government obtains a warrant to examine data stored on Microsoft's cloud servers. Microsoft filed the suit in Seattle Federal District Court, claiming that the gag order statute in the Electronic Communications Privacy Act of 1986 is unconstitutional as it is being applied.
The suit says that the law violates the Fourth Amendment right of its customers to know if the government searches or seizes their property and that it violates Microsoft's First Amendment right to speak to its customers.
Microsoft's goal apparently is to stimulate discussion about the frequent use of secrecy orders in government investigations. The FBI can compel a company to provide information and also prohibit the company from advising its customers that the agency has access to their phone, e-mail, and calendar information.
Electronic search and seizure differs from what happens in the physical world. If the FBI wants to see papers stored in your filing cabinet or documents on a hard drive in your computer, you'll know about it. Electronic information in the cloud isn't like that. A government agency can review every record you have and, unless somebody tells you about it, you'll never know.
Don't expect this suit to be settled anytime soon.
Possibly the most interesting data point from research by the British Broadcasting Corporation into the purchase of vinyl records is that 7% of purchasers don't even own a turntable. About half (52%) have a turntable that they use and 41% have a turntable, but don't use it. Why are these folks buying music on vinyl disks?
The BBC says a survey shows that half of consumers say they have listened to an album on-line before buying a vinyl copy. The survey was conducted by ICM. "But 48% of people who bought vinyl last month admit they have yet to play it." The BBC report quoted a student in Manchester: "I have vinyls in my room but it's more for decor. I don't actually play them. It gives me the old-school vibe. That's what vinyl's all about."
Who buys vinyl records? Well, it's certainly not those of us who grew up with them and realize the advantages of digital recordings. About one third of the sales are to people in the 25-34 year age range and 90% of sales are to those under the age of 55.