Normally TechByter Worldwide doesn't report on legal and political issues because legal reporting is a highly specialized undertaking. However, a case involving the company that developed an e-mail program called The Bat in 1998 came to my attention and it's a story that I'd like to share with you.
There are two players with similar names: RitLabs (SRL) is the original company that's located in Moldova. RitLabs (Inc) was founded in the United States by one of the three people who formed the original company, apparently without knowledge of the other founders.
Late in 2015, the developer of e-mail program The Bat, RitLabs, filed a complaint with the European Court of Human Rights asking that authorities in Moldova be ordered to enforce judgments from a US court in favor of the company and to stop what the complaint calls "unlawful harassment of RitLabs" by Moldovan prosecutors. There's a long story behind this.
Let's start with some history. I first encountered The Bat in about 1999. At that time, there were a lot of e-mail client programs. For example, Eudora, Pine, and Elm were still active then. Calypso had a good following. There's Outlook, of course. Pegasus and Forte Agent handled both e-mail and newsgroup protocols. Except for The Bat and Outlook, most of these applications no longer exist. Over the years, The Bat earned a loyal following.
 There have been many political and economic changes since 1998 when the company was formed. Moldova was a Soviet republic and it's located between Ukraine and Romania, north of the Black Sea.
There have been many political and economic changes since 1998 when the company was formed. Moldova was a Soviet republic and it's located between Ukraine and Romania, north of the Black Sea.
In 1998, Maxim Masiutin, Stefan Tanurcov, and Sergei Demcenko formed the company, Masiutin and Tanurcov each with a 30% share in the company, Demcenko with 40%. Demcenko was a director until late in 2011 when he was removed. According to court records I have reviewed from the United States District Court for the Eastern District of Virginia, the Moldovan company accused Demcenko of establishing a shell company in the United States, illegally obtaining the ritlabs.com domain, and siphoning off funds from the operation of the US company.
Of the 8 claims in the suit, the United States District Court for the Eastern District of Virginia ruled for the plaintiff on 5 in August of 2012. In November 2012, US District Judge Anthony J Trenga signed a court order formalizing the judgment and awarding the plaintiffs $108,637.82. Since then, things have gotten strange.
Demcenko left the United States and returned to Moldova. RitLabs, SRL, the Moldovan company, asked courts in Moldova to enforce the US ruling. The courts in Moldova refused and police opened a criminal investigation, not into Demcenko's actions, but into the remaining directors of RitLabs. On September 14, 2015, police searched the company's offices and seized computer hardware. On December 4, the judge who authorized the police search blocked the company's bank accounts.
RitLabs director Maxim Masiutin says that the company filed an appeal on December 8 and the Appeals Chamber ordered that the company's bank accounts be released. No written order was provided, though, so the bank could not release any funds. Masiutin says that the company has fully recovered access to the ritlabs.com domain name, is still being squeezed by Moldovan authorities.
Masiutin has reached out to users of the software for help. US citizens can help by contacting Senate members, particularly those on the Commerce Committee, and asking that they contact the Moldovan embassy in Washington and request that Moldovan authorities recognize due process rights.
If your browser doesn't support Flash, here is a direct link.
The US District Court's memorandum option is available on-line.
If you use The Bat or if you're just someone who believes that someone who has been found guilty of attempting to harm his former company shouldn't be allowed to continue to do so, reaching out to members of the Senate Commerce Committee or to your state's senators, even if they're not on the Commerce Committee would be welcome.
Stefan Tanurcov says that Demcenko is attempting to generate various criminal cases because he "wants to simply destroy RitLabs as a company." Both Masiutin and Tanurcov say that they believe any cases against them will not stand because they are "rubbish". But, says Tanurcov, "when it comes to a company, it becomes too easy to break a company's work-flow [and] this is why we are asking for your help."
When I spoke with Maxim Masiutin via Skype this week, we also talked about the company's history as a small organization that has succeeded by developing an e-mail application that they would want to use themselves. We also addressed security and privacy on the Internet. The Bat has always treated security as a top priority.
If your browser doesn't support Flash, here is a direct link.
Maxim Masiutin, director of RitLabs, SRL, in Moldova.
According to the US Senate website, the Commerce Committee includes these senators: John Thune - Chairman (SD), Bill Nelson - Ranking Member (FL), Kelly Ayotte (NH), Richard Blumenthal (CT), Roy Blunt (MO), Cory Booker (NJ), Maria Cantwell (WA), Ted Cruz (TX), Steve Daines (MT), Deb Fischer (NE), Cory Gardner (CO), Dean Heller (NV), Ron Johnson (WI), Amy Klobuchar (MN), Joe Manchin (WV), Edward Markey (MA), Claire McCaskill (MO), Jerry Moran (KS), Gary Peters (MI), Marco Rubio (FL), Brian Schatz (HI), Dan Sullivan (AK), Tom Udall (NM), and Roger Wicker (MS).
Vlad Turcanu, press secretary to the president of Moldova was offered an opportunity to comment on this issue or to provide a government contact who could comment on the issue, but no response has been received.
My wife posted a message to Facebook this week warning about a phony JetBlue promotion. A Facebook page claiming to be JetBlue Airways was offering give free flights "for an entire year to 800 of our lucky fans." Really?
The old joke goes something like this: "Did you hear they took 'gullible' out of the dictionary?" I do not understand how people can fall for phony offers such as this, but the page garnered more than 45,000 likes before Facebook shut it down.
I've also seen offers for 30% or more off your entire order at big box stores. Click a link with an offer like that and what you get won't be pleasant. Liking the phony JetBlue page, for example, prompts users to invite their friends to the like the page.
A JetBlue spokesperson said that the promotion is not real and encouraged people to report suspect pages or promotions through Facebook's reporting tools instead of sharing them.
The same day I received a message from a Yahoo account.
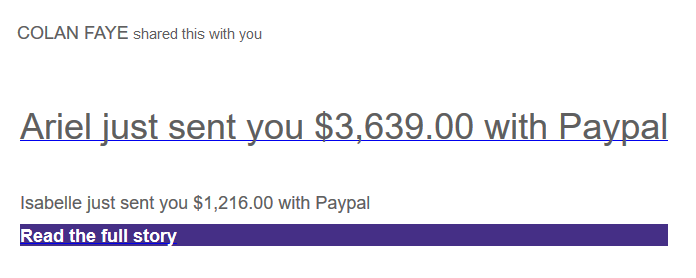
Should I click the link? Short answer: HELL NO!
Microsoft wants you to associate your Windows account with an Outlook account and there are good reasons to do this, but it can be a pain. After all, you want the Outlook account to have a strong password and having to type that password whenever you log in is a problem for those who use tablets and other mobile devices.
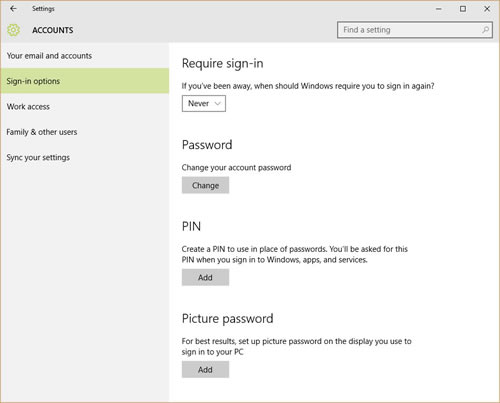 That's not the only option, though. You can log in with your face or with a 4-digit PIN. This is a "PIN", by the way, not a PIN number. The "N" in PIN stands for "number", so "PIN number" is really saying "personal identification number number". Compare this to "DMZ zone" (demilitarized zone zone), "Rio Grande River" (big river river), or "the La Brea Tar Pits" (the the tar tar pits).
That's not the only option, though. You can log in with your face or with a 4-digit PIN. This is a "PIN", by the way, not a PIN number. The "N" in PIN stands for "number", so "PIN number" is really saying "personal identification number number". Compare this to "DMZ zone" (demilitarized zone zone), "Rio Grande River" (big river river), or "the La Brea Tar Pits" (the the tar tar pits).
To set up the PIN, start at Settings, click Accounts, and then select Sign-in Options. The PIN option will be there. You'll be asked for your password first. Then enter your new PIN, twice. Although the default option for a PIN is four digits, you can create a longer one. Just don't use something obvious like your birthday or street address.
And if you want to use your face to log in, you'll need to be using a computer that had a camera. You'll see that option on the Sign-In Options screen, too.
After creating a PIN or a "Hello Login" (what Microsoft calls the face recognition authentication), you can switch back at any time to your long and secure password by clicking the Sign-in options button on the Accounts screen.
Kaspersky Lab suggests that parents "question their teen's on-line habits" to see if they've raised a hacker. I still don't like using the term "hacker" to describe a miscreant. Hackers have a long and honorable history. It's "crackers" that you need to watch out for, but the term "hackers" has been prostituted to mean "anyone who does bad things with code". I still don't like it, but apparently that's the term we use now.
Research by Kaspersky Lab reveals that 12% of 16 to 19 year olds know somebody who has engaged in on-line activity that could be deemed illegal. The poll was conducted in the UK, but results in the US would probably be similar. Many respondents (35%) said that they would be impressed if a friend hacked a bank's website and replaced the homepage with a cartoon. About 10% said that they would be impressed if a friend hacked the air traffic control systems of a local airport.
The average age of a cyber-criminal is now 17 years old. There's nothing new in teenagers being rebellious and pushing boundaries, but what is new is how they are unwittingly involving themselves in the far more serious threats and dangers that lurk in the world of cybercrime.
Dimitrios Tsivrikos, Consumer and Business Psychologist at University College London, says that rebellion, curiosity, and an urge to demonstrate their independence are natural characteristics of the age group. "As the first truly digital native generation, rebelling has simply become another aspect of their lives that can go digital," he says. "Cyber-crimes represent an attack on the 'system' and allow individuals to express their teenage angst."
Kaspersky Lab's principal researcher David Emm says that special browsers required to gain access to what's called the "dark web" are freely available on-line and discussion groups used by cybercriminals are often open to outsiders. He says that young people exploring, experimenting, or taking their first steps towards making some easy money on-line can easily find these sites. "Once in," he says, "they are vulnerable to exploitation for more complex schemes, perhaps being drawn into a fraudulent activity by playing the role of a money mule, or being asked to create a malicious program."
The research shows that most (95%) understand cyberbullying and (82%) trolling. Surprisingly, less than half (41%) know about malware or (44%) phishing and even fewer (24%) know about distributed denial of service (DDoS) attacked.
The survey asked what the respondent would do if a friend was doing things on-line that could be illegal and found that most teens don't know what the right thing to do is. About half would tell their friend to stop, but would do nothing else. Nearly a quarter would ask for details but not get involved. About a quarter would report the issue to a teacher or parent and just over 20% say they would report illegal activity to police.
Apple says it will not create a "back door" that would allow police and prosecutors to decrypt information on Apple phones. A court order this week demanded that Apple develop a way for investigators to read information on the phone of the the man who, with his wife, killed 14 people and injured 22 others in California.
Apple CEO Tim Cook says the order would require Apple software engineers to create the equivalent of a back door that could be used against any IOS device. Investigators say that the court order is narrow and addresses just one Iphone.
The order would require that Apple create a special version of IOS that would run only on the Iphone 5C that belonged to Syed Rizwan Farook. Farook and his wife, Tashfeen Malik, staged an attack in San Bernadino.
The FBI wants access any information on the phone. Sounds reasonable. The phone is locked, though, and the FBI has been unable to break the encryption. Apple's built-in security limits the number of guesses investigators can make in an attempt to unlock the phone. After receiving a certain number of incorrect passwords, the phone might automatically delete all data.
The Justice Department wants a special version of IOS that would eliminate the restrictions so that password attempts could be entered more quickly and so that the phone wouldn't automatically destroy any saved information. The court order also requires that the phone be able to accept personal identification numbers via Bluetooth or Wi-Fi.
The court ordered that the software would work only Farook's phone. All of that seems reasonable, particularly because Farook is now dead. The problem is that something created to run on one phone could undoubtedly be modified to run on some other IOS device.
That's why Apple's CEO is opposed. Once the djini is out of the bottle, what's to keep governments in China or Russia from requiring access to the technology? In other words, the court order seems to be badly written and based on a request by people who don't understand technology.
Had the court order been written in a way that would require Apple software engineers to find a way to extract data from this one phone and then turn that information over to investigators, it's more likely that Apple CEO Tim Cook would have gone along with it.