The Bat Roars Back
Around 1997, I discovered version 1.0 of The Bat (styled as "The Bat!" by publisher RIT Labs in Moldova) and considered it to be an interesting program, but not yet quite ready for mass distribution. In 2000, I recommended it. I have continued to recommend it enthusiastically since then, except the time from mid 2011 through the end of 2013. Well, The Bat is back!
In the early days, there were lots of e-mail programs, both free and commercial products. How many of these do you remember? Alpine, Elm, Mulberry, Mutt, Calypso, SeaMonkey, SquirrelMail, Foxmail, Inky, i.Scribe, WordPerfect Mail, IBM Notes, InScribe, Microsoft Outlook, Novell GroupWise, Eureka, Forté Agent, Gemini, Pocomail, The Bat!, Pegasus, cc:Mail, Claris Emailer, Courier, Cyberjack, Eudora, Hula, Microsoft Entourage, Outlook Express, Pine, and POPmail. And there were lots more. Today, the list is much smaller and yet The Bat remains the most powerful e-mail application available, if not always the most user friendly.
The Bat has always had a relatively strong following in Europe, but much less so in North America. Given the advantages this application brings to users, I've never understood why. From the beginning the software engineers at RIT Labs have focused on security and highly customizable mail handling. No other program matches the mail organization capabilities The Bat had in 2000, much less what the program can to today.
The time during which I recommended The Bat with reservations coincided with versions 5.0 and 5.1. Although most of the features still worked well, creating new messages and replying to messages became a problem because the message templates (what Outlook would call "Stationery") failed to maintain the proper typeface. A small point, perhaps, but annoying nonetheless.
Version 6 resolves that problem and it adds features that make it the one e-mail application that I can recommend without reservation.
New in Version 6
First and foremost, security is even better than before. At a time when e-mail continues to be the single most common vector for malware, security is more important than ever. The Bat provides improved protection against malware because it continues to use its own internal HTML viewer. Any graphics or other components that have been embedded in the message will be displayed only when the user permits them to be displayed.
Although both GnuPG and S/MIME are still so complex that most average users won't invest the time needed to master them, The Bat allows messages to be encrypted if the user takes the time to read though the documentation and perform the steps necessary to implement one of these features.
The Bat makes it possible for users to sign messages with a self-issued certificate instead of using services such as Comodo, Thawte, or Verisign to create a certificate.
The Bat is able to connect to multiple servers simultaneously, which is a significant advantage for people who have more than one account.
Several new features provide improved usability. More filter functions in the Sorting Office, for example, so that messages may be sorted automatically to specific folders, marked, exported, or printed without user intervention.
A Quick Reply option allows users to send a fast reply without the need to open the message in a separate window. If a message requires a simple answer such as "Yes" or "See you then," just type the brief response in the panel below the message and click Send.
Looking to the future, The Bat now understands Unicode. Unlike the current ASCII standard, Unicode can represent tens of thousands of characters used by most of the written languages on the planet. This feature may be of only minor interest to those in the United States, but it's an important consideration in much of the rest of the world.
The developers are working on a 64-bit version of the program, which is currently available to beta testers. It has not yet been released. RIT Labs says that the 64-bit version of The Bat will be able to work with a Microsoft Exchange Server if the 64-bit version of Outlook is installed. Except for that, the developers list no other advantages for the 64-bit version.
In 1997, a VGA monitor (1024x768) was considered to be high-resolution. Today it's not uncommon for people to have monitors that are nearly quadruple that resolution or even higher. The Bat has been modified be more legible on these high-DPI monitors.
Fourteen years ago, I said that the built-in documentation was lacking and quoted one of the developers, "Programmers rarely write complete documentation because they feel that the operation of some functions is obvious and because they'd rather write code to improve the program than to write documentation describing the program." The documentation is far better now and users should be able to find answers to their questions in the Help file.
One thing is certain about The Bat, though: If there's something that you wish the program could do, it probably can. It's up to you to find out how.
Dealing with The Bat's Many Settings
Most e-mail applications allow users to create signatures that are attached to each message, but The Bat makes it possible to create entire message templates not just for each e-mail account, but for each folder within the account. So if you subscribe to a discussion list and have The Bat sort those messages into a specific folder, you might have a generic template for most of your messages, but a completely different template for messages that go to the list.
Additionally, a built-in macro language allows users to set non-standard headers within the messages and then to use those headers to control what happens to the message when you send it.
The Transport panel is where you set up the inbound and outbound servers.
For users who specify different servers for inbound and outbound messages, The Bat offers an easy method for selecting which server should be used at any time. This is a feature that anyone who uses a portable computer will find useful.
In addition to settings that apply to a specific e-mail account or to just a single folder within the account, there are also application-wide settings.
One panel provides selelctions for the language and date format that the user prefers. In this case, I have told The Bat to ignore the Windows Regional settings and use the language I've specified in The Bat's setup. I have set a custom date format and, when The Bat displays messages from the current day, it will show the time the message was received instead of the date.

 The Bat is still the champion for power users
The Bat is still the champion for power users
The Bat isn't for everyone, I suppose, although it could be. The basic installation and configuration are easy enough if you want a plain e-mail application. But it's the unquestioned stand-out for those who want a secure e-mail application that has the built-in features needed to handle even complex automated tasks. The developers seem to operate on the principle that "good enough" never is and they continue to make The Bat more of a powerhouse with each subsequent version.
Additional details are available on the The Bat (RIT Labs) website. Because the program is a shareware application, you can download it and use it for a month without cost or obligation
 A Cautionary Tale
A Cautionary Tale
Occasionally I run a Malwarebytes scan. When I ran a scan this week, I found 10 questionable files on the notebook computer and that didn't surprise me. I was surprised when one file turned up on the desktop computer, though, and even more surprised when it led to a hidden directory with more than 500 files.
I had installed the video player DivX on the notebook computer, so I wasn't surprised to find that the Conduit Search "tool" that I wrote about last September had been downloaded even though I had explicitly told the DivX installer that I didn't want it. The Conduit application hadn't been installed, but the installer files had been downloaded. I still consider DivX to be unacceptable for this reason even though Conduit isn't malware in the typical meaning of the term.
Malwarebytes quickly and easily disposed of those 10 files on the notebook and I didn't expect it to find any problems on the desktop, but there was one. The file it didn't like was "C:\Users\Bill Blinn\KHSRB\SRKBE.exe". That's an odd location for a file to be located so I thought I'd take a look before I allowed Malwarebytes to delete it. When I navigated to to the directory with my name, no KHSRB directory was visible.
Directories can easily be hidden, so I tried unhiding it. No luck. That must mean that it's a system directory and that's easy enough to fix, too:attrib -h -s khsrb did the trick. The -h argument removes the "hidden" attribute and -s removes the "system" attribute. Now the directory was visible and I thought I'd take care of it easily with rd khsrb, but "The directory is not empty" was the system's response.
All right, del khsrb/*.*, then. "No files found."
So I navigated to the KHSRB directory and issued a command to make the files visible: attrib -h -s -r *.*. The -h and -s arguments work the same as for directories and I added -r to remove the read-only attribute just in case. Then I listed the files in the directory. What I didn't expect was a list of 518 files. That's it over there at the right. Most of the files were just a few bytes long and most of the ones I checked contained only a number. But there was a Visual Basic script that called one of the files in the directory and I presume that when used together these files would have combined the 500+ files to accomplish something nasty.
The files are no longer present. Once I rendered them visible, I could delete them. And I did.
What was this?
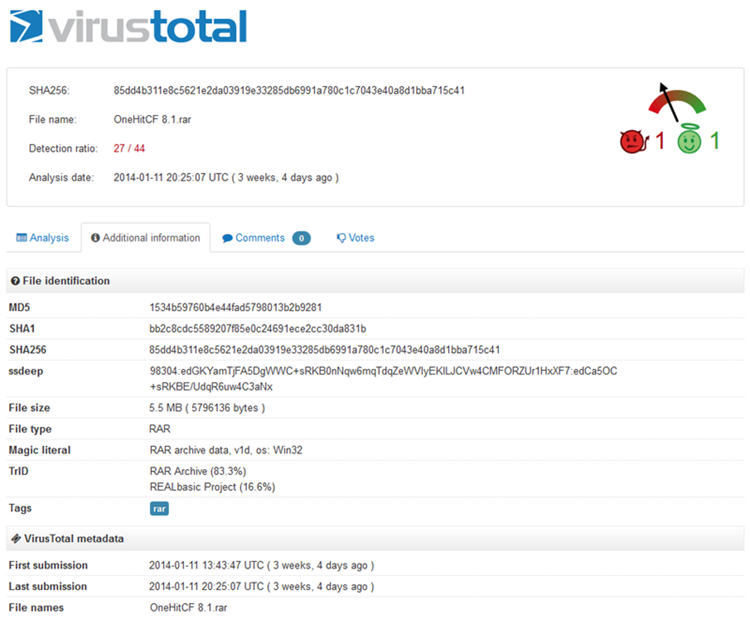
It seems to be a relatively new exploit and possibly not a particularly dangerous one.
Dangerous or not, I certainly didn't want it on the computer and it's gone.
The main point is that this was a stealthy application. Because it consisted of a bunch of seemingly harmless text files, it was able to infiltrate the system and be planted in a location where it might have done some real harm if I hadn't noticed it. Or, more accurately, if Malwarebytes hadn't noticed it.
I've said many times that it's the user's responsibility to maintain security and there's no way that I can blame the presence of this malware on a system failure. It was cleverly designed and didn't raise any warnings, but clearly I let my guard down.
Subsequent scans have shown no lasting effects.
And I'm allowing that long list of files to continue until it runs out of file names as a reminder that we can never be too careful.
Fraudsters on the Loose
The number of fraudulent messages is increasing daily. Fortunately, my anti-spam measures are sufficient to keep the crap off my computer, except when I decide to let some through to see what the thieves of the world are doing. In recent weeks, there's been a flood of phony coupons.
Some examples ...
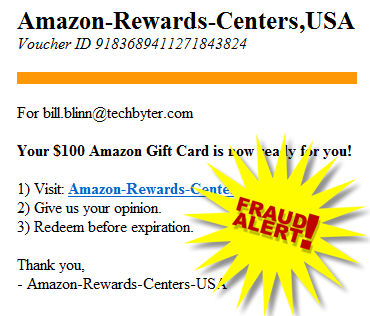
Just about everybody seems to buy something, at least occasionally, from Amazon, so you might reasonably conclude that Amazon is rewarding your loyalty by sending you some bonus bucks. In this case, I'm being offered $100 by "Amazon-Rewards-Centers". Amazon has a rewards program, but it's not called "Amazon-Rewards-Centers".
Follow the link and what happens? I don't know, but these generally don't try to plant malware on users' computers. Instead, you'll probably be presented with a "registration" form. That should immediately cause some alarms to sound. If these guys are sending you a gift card, don't you think they already know who you are, where you live, what your phone number is, and how to contact you by phone.
What's the point? If they ask for your phone number, your name, and your e-mail address, it must mean that they don't have it. Provide this information and you'll find yourself on the receiving end of even more spam and robo calls.
Here's one that claims to be from Wendy's. The fast food company is remodeling its stores and has expanded its menu, so it seems reasonable that they would send out coupons for free food, doesn't it?
This is another scam to harvest your phone number, e-mail, and other information. Sometimes these sites actually do provide a coupon that you can print. It might even look legitimate. But when you try to redeem it, you'll find that it's worthless.
It's Not Always E-Mail

Your phone rings. Once. What do you do? If you still have a phone like the one in the picture, there's not much that you can do. But if the call came to your cell phone, you have the number of the caller.
You probably know not to answer calls from numbers that are blocked, but this number is displayed, so it must be OK. Should you call the number to see what the mystery caller wanted? Emphatically, NO! The Better Business Bureau even has a name for it: This crooked ploy is called The One-Ring Scam.
The BBB says that the scam relies on consumers calling back missed calls. What happens next is you're connected to a paid international adult entertainment service, a chat line, or other some other "premium" service located outside the country. You might be hit with a $20 international call fee or the line may charge you several dollars per per minute. The fee can be large, but most of the crooks are smart enough to keep the fees relatively low and counting on most people not closely examining their phone statements. And even those who do look might be inclined to just assume that a small charge is probably legitimate.
According to the Better Business Bureau, the calls usually originate outside the United States. Some of the locations that have been reported include area code 268 (Antigua and Barbuda), 809 (the Dominican Republic), 876 (Jamaica), 285 (the British Virgin Islands), and 473 (Grenada).
These countries all share a country code with the United States and Canada (+1), so the numbers look like they're standard long-distance calls and not international calls. Because the calls go to locations outside the United States, organizations such as the Federal Trade Commission have no jurisdiction.
The solution is simple: If you don't recognize the calling number, don't call back. If do review your phone statements for unexpected charges, speak up as soon as you see one. The earlier you identify and report the fraud, says the BBB, "the better your chances of having some or all of the charges removed."
Short Circuits
Changes Planned for Broadband Internet in Schools
Digital Learning Day was this week and the head of the Federal Communications Commission says that his agency plans to modify taxes that are used to provide money that pays for high-speed Internet service in schools.
Maybe the very existence of a "Learning Day" explains why the position of the United States among intelligent nations seems to be slipping. Many countries devote more than a single day to learning. (OK, so that was a joke. Well, maybe not really.)
FCC Chairman Tom Wheeler says that the agency will consider increasing the taxes paid by phone companies (and, of course, ultimately by consumers when the phone companies pass the taxes on). Currently the FCC collects a little less than $2.5 billion per year and uses about half of that to pay for what's called the E-rate program.
Some of the money is used to pay for dial-up Internet service in some areas and a bit even pays for pagers. Who uses pagers these days?
Wheeler was quoted as saying that the agency has found ways to make the program more efficient and to improve "the way funds are deployed." In English, he said that the FCC has an idea how it could spend money better. He was speaking at the Library of Congress. On the subject of additional taxes, Wheeler said "Should it be necessary to increase the permanent funding levels for the E-rate program, we will do what is appropriate." In English, that means the rates will be going up.
The FCC plans to increase its spending to provide high-speed Internet connections in schools and libraries to achieve the stated goal of the Obama administration to give nearly all students access to high-speed Internet connections within the next 5 years.
The FCC can increase spending because it has collected money in recent years that has not been spent.
E-rate is paid for from money collected as part of the "Universal Service Fund". In addition to broadband Internet connections in schools and libraries, the fund is used to pay for service in rural areas. An approximately 15% tax is levied on some aspects of wired and wireless phone service. It's not 15% on the total bill, so most of us pay only a few dollars per month.
Yahoo Tries to Recover from Another Hacker Attack
In 2012, hackers broke in to servers at an organization that's associated with Yahoo and made off with credentials for about 400,000 users. Now it's happened again, and once again the attack didn't target Yahoo's servers, but those of some other company.
Attackers have been trying to gain access to Yahoo accounts by using credentials they obtained by breaking into the other company's servers.
What other company? Yahoo doesn't know.
How many accounts might have been affected? No idea.
If nothing else, this attack once again illustrates why user names and passwords that you set up for one account should never be used for any other account.
Yahoo has already reset the passwords for all accounts that they believe were affected.
Earlier this year, crooks manage to serve malware via advertisements that were served on Yahoo's site. In that case, the malware looked specifically for Bitcoins.
Rumors of a New High-End Nexus Tablet
Sources in Taiwan say that a new high-end Nexus tablet will show up on store shelves later this year—probably by Fall. The rumors say that HTC will work with Google to create the next version of a premium Nexus tablet.
You want more information, of course. So does everyone else and none of the companies involved are willing to say anything on the record. Or off the record, for that matter.
HTC and Google worked together a few years ago to create the Nexus One, a smart phone, but it's Asus that makes the 7-inch and 10-inch Nexus tablets.
The company stumbled with its 7-inch Flyer and 10-inch Jetstream tablets, and it's not in a particularly strong financial position now. That raises some questions about why Google would want either to replace Asus or create competition for Asus units.
So we'll keep watching the tea leaves and see if anything surfaces.
