Normally the main section of the weekly report contains 2 or 3 articles, but this week there's just one. That's because this is an uncommonly important topic. The message you need to take away from today's program is this: Never open an attachment without first confirming that it's safe. If you practice safe computing, it's unlikely that you'll ever be forced to pay several hundred dollars just to regain control of your files.
File Encryption You Don't Want
Those who use notebook computers that contain proprietary business data have heard about the importance of encryption and may have installed an application such as TrueCrypt to perform that task. But just as a hammer can be used to build a comfortable home or to kill someone, encryption technology can be used to protect proprietary data or to hijack files and hold them for ransom.
Encrypting files and demanding a ransom isn't exactly new, but malware called "CryptoLocker" by its developers is all but unbeatable. This is something that you don't want to see.
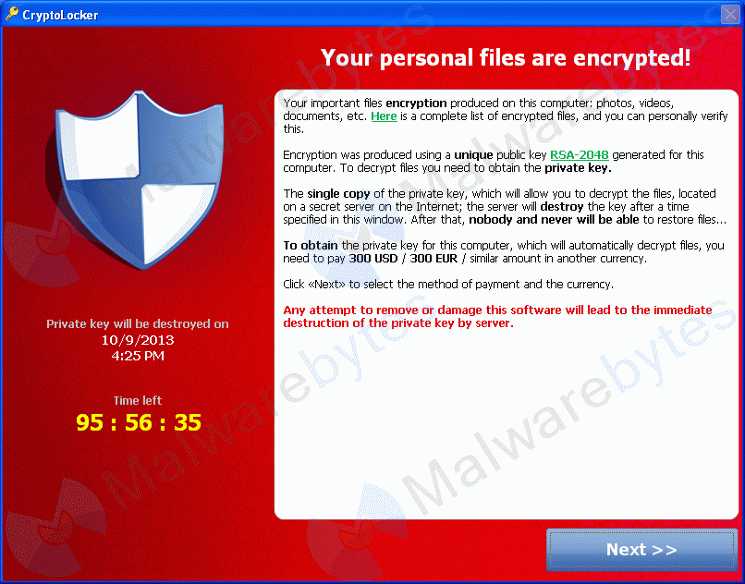
Image provided by Malwarebytes.
CryptoLocker encrypts your personal files and then demands ransom to make them available again. Initially, the thieves wanted $100 to decrypt the files, but a new variant demands $300.
One of the most useful sites on the Internet when it comes to solving problems with computers is Bleeping Computer, run by Larry Abrams, who took some time out of his busy schedule to talk about this threat. The first thing I asked about, though, was how long Bleeping Computer has been around ...
If your computer doesn't support Flash, you'll find the interview here.
Why Backups Are Essential
If you see a message such as the one shown here, you have three options:
- Ignore the message, wipe the drive on the computer, reinstall your applications, and kiss all of your data files goodbye.
- Pay the ransom and hope that the crooks will release your files unharmed and, if they do, that they won't encrypt them again and demand another $300.
- Ignore the message, clean the machine, and restore data files from backup.
Clearly, the third option is the best one, but many individuals and far too many small businesses don't have current backups.
The thieves don't encrypt everything. After all, they want the computer to run and be able to start applications. They encrypt only the data files that you'll need. Files with extensions such as 3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, and xlsx.
If you don't read extensions fluently, the ones shown here cover files created by the most popular programs — Microsoft Office files, Libre Office files, Adobe Creative Suite files, raw file formats used by cameras, various accounting application files. In short, this could render every file on your computer inaccessible.
The method that the thieves use to encrypt files is known as "asymmetric encryption", which simply means that one key (a public key) is used to encrypt the files and a second key (a private key) is required to decrypt the files. This technique is commonly used for secure file transfers. Microsoft provided this diagram that illustrates the process.
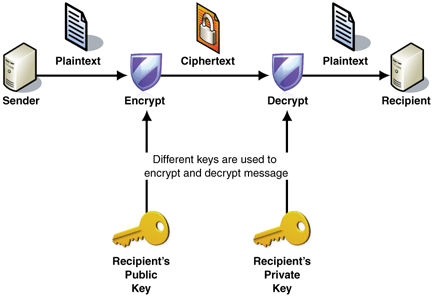
Image provided by Microsoft.
So if you see a threat such as the one shown and you don't have a complete backup, your only option, if you want to retrieve your files, is to pay the ransom. Most people who have paid report that their files are decrypted, but common sense would suggest that any recovered files should immediately be copied to a safe location and tested. Then the infected computer should have it's disk formatted so that everything can be installed anew.
The infection can be removed easily, but removing it doesn't decrypt the files.
How to Avoid CryptoLocker
The primary infection vectors for CryptoLocker are believe to be:
- Via corporate e-mail addresses with messages that pretend to be customer support related issues from FedEx, UPS, DHL, and others. The messages would contain a poisoned attachment.
- Via PDF attachments that contain Zbot infections.
- Via exploit kits located on hacked web sites to trick your computer into installing the malware.
- Via Trojans that pretend to be programs required to view online videos.
In other words, all of the infection vectors are well known and are relatively easy to avoid.
Once installed, the CryptoLocker infection will install itself into the root of the user's AppData folder. The file name is uses varies from one machine to the next. It will also create an autostart application in the Registry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "CryptoLocker"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "*CryptoLocker"
Researchers are trying to find a way to undo the encryption, but don't expect success anytime soon. Decrypting CryptoLocker files requires access to both the public and private keys used to encrypt them. Maybe the NSA can decrypt your files, but nobody else will be able to do so.
BleepingComputer puts it this way: "Unfortunately at this time there is no way to retrieve the key used to encrypt your files. Brute forcing the encryption key is realistically not possibly due to the length of time required to break the key. Any decryption tools that have been released by various companies will not work with this infection. The only method you have of restoring your files is from a backup, or if you have System Restore, through the Shadow Volume copies that are created every time a system restore is performed."
For more information about this threat, how to avoid it, and how to recover, see the Bleeping Computer CryptoLocker Guide.
You might be wondering if the crooks behind CryptoLocker will be caught. If you're interested in my opinion, I think that it will depend on them. The people behind the operation will make an enormous amount of money in a relatively short time. If they decide to call it quits in the next few weeks, they will probably just disappear without a trace. But if they choose to continue running the exploit long enough, they'll leave a large enough trail that some law enforcement agency will find them.
But whether they're caught or not, what worries me is the next threat. For more than 30 years, the aviation industry accepted the occasional airliner hijacking as nothing more than a political statement or a way to extort money from an airline. Then came the four hijackings in September of 2001. The kinds of people who exploited our general understanding of airline hijackings are looking for new ways to cause trouble and I can't think of a better method than this.
What would you do if all of your company's files were suddenly unusable and the people who made them unusable weren't interested in unlocking them for any price?
Pleasant dreams ......
Short Circuits
Blockbuster Goes Bust
In 2004, Blockbuster had 9000 stores around the country. Now, to the great surprise of approximately 3 people, Blockbuster's owner, Dish Network, is closing most of the final few hundred stores. In other words, Netflix has won the race.
Blockbuster was bankrupt in 2011, which is when Dish Network acquired the company. At that time, Blockbuster was down to 1700 stores and the path was already clear then. Blockbuster has a disc-by-mail service and that will also be terminated. About 50 Blockbuster stores will remain open because they are operated by franchisees.
The CEO of Dish, Joseph P. Clayton, says that the company still sees value in the Blockbuster brand. "We expect to leverage that brand as we continue to expand our digital offerings,” Clayton said.
Blockbuster still has a streaming service, Blockbuster @Home, via its satellite service and there's Blockbuster on Demand, which competes with Apple's Itunes store.
Amazon Makes Nice with Book Stores (Sort of)
People who own book stores generally don't like Amazon. That is perhaps an understatement. To say that book store owners loathe Amazon would be somewhat less of an understatement. But now Amazon wants independent book stores to sell Kindles and profit from ebook sales.
Amazon has announced a program that would put Kindles in book stores and the stores would earn a commission on all e-books sold for the device during the following 2 years. In general, the owners of book stores seemed unimpressed.
Amazon sells more books than any competitor. Independent book stores sell far fewer books per year than Amazon and fewer books than chain stores such as Barnes and Noble. Before Amazon opened, the independent stores had about a quarter of the market.
The new Amazon program allows stores to buy Kindles at a 6% discount and then be paid a 10% royalty on all books sold for the device within 2 years, or at a 9% discount, but without any additional payment.
