Hobby Website Operators Need to Consider Security, Too
Your website doesn’t sell any product or service directly. You don’t accept online payments. No credit card information is stored on your site. You don’t even ask people to register their name or e-mail address. It's just a site for club members or a place where you can show off your hobby. So security is no big deal, right? Wrong.
In fact, your site might be an ideal target for cyber-crooks. Not for the valuable data they can find and carry away (we’ve already said that there isn’t any). Instead, the crooks will find security holes in your site and exploit them to plant malware on visitors’ computers. Or they’ll surreptitiously create a directory or a sub-site on your server and use it for their illegal acts.
This will not be popular with the people who visit your site.
If you are a subscriber to my nLightened Thoughts newsletter, this article will be familiar because it is a slightly expanded version of my article in the June issue. I don't often duplicate content, but this topic is sufficiently important that I wanted to be sure both audiences saw the information.
The Open Web Application Security Project (OWASP) Top Ten Project lists the 10 most serious threats each year and each new year’s report bears a distressing similarity to the previous year’s report. Actually, this is to be expected because the report doesn’t list specific exploits that take advantage of a particular piece of software or hardware, but instead focuses on types of errors that can be exploited.
OWASP is a non-profit organization that was founded in 2001 and counts 36,000 participants worldwide. OWASP’s mission involves explaining online security threats, particularly those that are Web based, and providing crowd-based guidance for mitigating the problems.
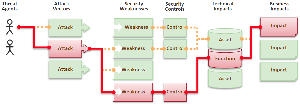 Most of the top ten threats have been the top ten threats for the last ten years and there’s no likelihood that they’ll fade away anytime soon even though they’ve been well identified. Programmers, being both human and creatures of habit, tend to make the same kinds of mistakes year after year. Hence the similarities from year to year in OWASP’s report. And the bad guys, being persistent, won't stop trying if their first attempt is blocked. Instead, they'll try other known vulnerabilities and other known functions. All that's needed in one small hole.
Most of the top ten threats have been the top ten threats for the last ten years and there’s no likelihood that they’ll fade away anytime soon even though they’ve been well identified. Programmers, being both human and creatures of habit, tend to make the same kinds of mistakes year after year. Hence the similarities from year to year in OWASP’s report. And the bad guys, being persistent, won't stop trying if their first attempt is blocked. Instead, they'll try other known vulnerabilities and other known functions. All that's needed in one small hole.
OWASP Wants to Help
First released in 2003, the goal of the Top 10 project is to raise awareness about application security by identifying some of the most critical risks facing organizations. It’s really only the beginning, though. OWASP says: “There are hundreds of issues that could affect the overall security of a Web application.” In fact, neither the overall Internet nor the area known as the Web was designed with security in mind. Initially, these were technologies designed for sharing information and there was no expectation that they would be used for commerce.
Whatever security measures exist have been bolted on later as an afterthought. This alone explains why so many problems exist. The best solution would be simply to start over and design a secure network from the ground up. Clearly that’s not going to happen anytime soon, if ever, so the second best solution is for developers to place security ahead of functionality. Unfortunately, because functionality that provides known benefits has more intrinsic appeal that protecting against unknown threats, that rarely happens.
So realistically, all we can hope for is an environment in which developers carefully assess the risk of each type of technology they use and actively build in protections that mitigate the threats.
For starters, any application or website should be reviewed to ensure that the OWASP Top 10 threats have been resolved. These aren’t obscure or unknown threats and most of them have clear strategies for remediation.
Why So Many Problems?
It’s difficult to understand why some of the attack vectors continue to be in the top 10 year after year. Take, for example, the number 1 threat, “Injection”. An injection occurs when untrusted data is sent to a command interpreter. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing unauthorized data.
Example: A website form asks for a name, a phone number, or an e-mail address and depends solely on browser-based validation. When the value entered by the user reaches the Web server, it is passed to the database server without further testing. In this scenario, a crook can include a bit of punctuation and a command that would cause the server to return a dump of the database.
The solution is simple: Regardless of any validation that’s performed in the browser, all data that arrives at the server must be considered suspect. The developer simply creates what’s called a white list of acceptable characters. Only those characters (typically numbers, upper- and lower-case letters, and specific punctuation characters) are accepted. Everything else is removed before the value is passed on to the database.
The other primary vulnerabilities range from broken authentication and cross-site scripting to security misconfiguration and failure to install security updates.
Many of the threats are difficult for people who are not developers to understand without complex and ponderous explanations, but security updates are both critically needed and easy to comprehend.
 Most website hosting companies offer various add-ons. BlueHost, for example, offers a service called Simple Scripts that provides several dozen applications ranging from content management systems and guest books to forums, surveys, and full website development tools. Each of these applications is routinely updated.
Most website hosting companies offer various add-ons. BlueHost, for example, offers a service called Simple Scripts that provides several dozen applications ranging from content management systems and guest books to forums, surveys, and full website development tools. Each of these applications is routinely updated.
Some of the functions that can be installed on your website have more potential vulnerabilities and are therefore updated more frequently. WordPress, for example, is a popular target because it is a complex piece of software that is used on hundreds of thousands of websites, sometimes by people who have no understanding of security.
Simply put: No application is ever perfect. When an application is updated, install the update.
Website Attacks
Installing updates is one of the easiest but most critical safeguards; make sure that anything installed on your Web server is up to date.
BlueHost, the service most of my clients use, does an excellent job of keeping the base software patched and updated. As with virtually all site hosting services, BlueHost runs open-source software that is frequently updated.
It’s good that the code is open-source because the good guys can look for weaknesses that might be exploited and fix them. It’s also bad that the code is open-source because the bad guys can look for weaknesses that might be exploited and use them. That’s why updates are so important.
Few, if any, hosting operations will update any applications that you have installed. You can, for example, install WordPress manually or via the Simple Scripts interface, but then it’s up to you to check for updates regularly and install them. The hosting companies won’t do this because updates can break existing installations if those installations have been improperly modified by the user.
Some content management systems such as WordPress accept plug-ins that can improve security, but these need to be updated frequently, too. Or you might consider SiteLock, a third-party service that’s offered by many hosting companies. SiteLock monitors your site daily to detect malware, identify vulnerabilities, and scan for any virus code that may have been planted on your site.
Quick Security Lesson: 777 is Not a Lucky Number
Most websites reside on Linux severs and Linux controls folder and file access by assigning what are called read, write, and execute permissions for each of 3 classes of users: 777 means everyone can do anything to the file.
 The classes are used to identify the file or folder owner, the group that the file owner belongs to, and everyone else (aka “the world”).
The classes are used to identify the file or folder owner, the group that the file owner belongs to, and everyone else (aka “the world”).
Permissions are stated numerically: 4 means the user can read the file or folder, 2 allows writing, 1 indicates execute permission, and 0 (as you probably expect) means no privileges.
Each of the 3 user types is represented by a single number: 751, for example, means that the file owner can read, write, and execute the file (7=4+2+1), the group can read and execute the file but not modify it (5=4+1), and all other users may only execute the file but not read or write it.
Inexperienced website developers sometime try to install a Perl script (Perl is a scripting language that’s commonly used on websites), finds that the script won’t run because of a problem with permissions and sets the file and the directory that contains it to 777. Bad move! Now anyone who has access to the site can modify the file.
In most cases, folders should be set to 755 and files to 644.
Acceptable Risks
Some risks are acceptable. We live in a world of acceptable risks.
When we drive across town, we know that we could be run over by a large truck or hit by a falling meteor. Both of these are unlikely, so most of us accept the risk. With websites, there are acceptable risks, too, but any exploit that has been clearly defined—and particularly those in the OWASP Top 10—must be eliminated.
The threats are real. Don’t be sorry.
Magix Video Pro X5 Brings Power at a Surprising Price
In an increasingly crowded marketplace, Magix has released Video Pro X5. Magix, although very well known in Europe, is less familiar in the United States. Video Pro is available with a 30-day trial, after which you can license one of the three versions or uninstall it.
Be careful during the installation process to select the custom installation process. If you don't, you'll get an extra browser toolbar that you don't want and a system cleaning utility. This is a despicable practice and one that I feel should be made illegal. If you choose the custom installation process, you can deselect both; otherwise, they'll be added without warning.
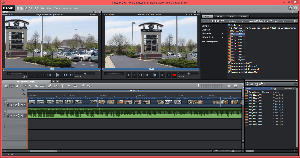 When you start Video Pro, you can watch an introductory video, open an existing project, or create a new project using a template or from scratch. If youy've used any video editing application previously, you'll be familiar with the layout: Preview and source sections in the top half of the screen, a timeline at the bottom and a viewing area in the middle.
When you start Video Pro, you can watch an introductory video, open an existing project, or create a new project using a template or from scratch. If youy've used any video editing application previously, you'll be familiar with the layout: Preview and source sections in the top half of the screen, a timeline at the bottom and a viewing area in the middle.
As with most editing applications, you can view the timeline in a traditional editing layout or as a series of thumbnail views, somewhat like a storyboard. Icons are provided to allow adding text, adjusting the volume of the sound, and inserting transitions between clips.
A razor icon provides the ability to trim video clips, with options to simply split the clip, split and remove either everything before the cut or everything after the cut, delete the entire scene, or split the movie. There's also a fine-tuning option that allows for more precise placement of the edit point.
The Magix Magic
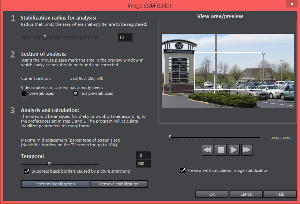 Most of us haven't invested in a Steadicam and we can't hold the camera steady. This is particularly true in my quick 30-second test video. A nearby shopping mall is undergoing renovation and I walked over one day with a point-and-shoot camera. Holding a camera away from your body, as is required with such cameras, makes the situation even worse.
Most of us haven't invested in a Steadicam and we can't hold the camera steady. This is particularly true in my quick 30-second test video. A nearby shopping mall is undergoing renovation and I walked over one day with a point-and-shoot camera. Holding a camera away from your body, as is required with such cameras, makes the situation even worse.
Video Pro offers Stabilization, which is a remarkable function for a $400 application. Yes, that's considerably more that other video applications from Magix, some of which are well under $100. But $400 for image stabilization would have been unthinkable not many years go.
I created two versions, before and after. Even with minimal stabilization, the difference is astounding and despite warnings from the program that applying stabilization might take a long time, it was surprisingly fast.
This is the version before stabilization.
And here's the version following stabilization.
Video Pro allows for a picture-in-picture effect, provides color correction capabilities, makes it possible to slow or speed scenes, and add text bubbles or other hokey items to your video. And, of course, there are transition effects. As always, my warning here is that a simple cut or fade is almost always the best choice. Select one of the special effects only when you can clearly state to yourself why you need to use it.
The software lets you export your edited digital movie in a wide array of formats as well as burn movies to disc in Blu-ray, AVCHD, or DVD format.

 Powerful Video Editing at a Reasonable Price
Powerful Video Editing at a Reasonable Price
Not everyone will consider $400 to be a reasonable price, but the powerful features offered in Magix Video Pro X5 could cost a lot more. And, if the price is a bit too high for your budget, Magix offers other options for beginner or mid-range video enthusasts.
For more information, visit the Magix website.
Short Circuits
Did Adobe Perform any Market Research Before Launching Creative Cloud?
This is another of those occasional opinion pieces. There's no question that Adobe Creative Cloud offers some real advantages. Among these advantages is lower cost for people who upgrade to each new version and, given the speed with which things change in the graphic arts industry, I expected that would describe most users. It seems that I was wrong and the push-back from Adobe users looks a lot like the push back Microsoft is receiving from Windows users.
I have heard from people who are active in the graphics community but who are nearing retirement age. "I guess I'll stick with CS6," is what they generally say, and I found that not to be too surprising. What did surprise me is that I'm hearing the same thing from people who are active in the graphics community, but who are nowhere near retirement age.
These are people who might choose to upgrade their Adobe applications every other release, or maybe every third release. If you upgrade every other release, the new Creative Cloud offering will actually cost you less. Every third release — well, maybe you'll pay a little more that way but at least you'll have the opporunity to download the latest version of every application.
The trouble is that people don't like to feel as if they're being forced to make a change, even if it's good for them.
Look at Windows 8: It's faster, it's more secure, but there's no Start Menu. The push-back from Windows users has been so strong that Microsoft appears to be ready to retreat in version 8.1 and restore the Start Menu even though it's completely unnecessary.
Will Adobe suffer the same fate?
It seems to me (here's the opinion part) that it's better to allow applications to evolve. Allow people who want to buy (license) one version of the software and then stick with it for 12 or 18 or 24 months to do exactly that. When they decide to upgrade, it will cost them more. OK. So what? At least they'll feel like they're in control.
Initially, which is to say "several weeks ago", I thought that Adobe had made a good decision, but I came to that conclusion without the benefit of any market analysis. In fact, I assumed that Adobe had done its homework and had found that offering only the Creative Cloud would be popular with all (or at least a majority) of Adobe users.
 Based on what I've heard from those users, Adobe has made a potentially serious marketing error and companies such as OnOne are moving to take advantage of it. An e-mail message from the maker of the Perfect Photo Suite, which works with Photoshop, says that the latest version of the software will work with or without Photoshop: If you're moving to Creative Cloud, "Perfect Photo Suite is the perfect complement to your Photoshop workflow, giving you an easy way to do things that are difficult and time-consuming to do in Photoshop. The Suite also works perfectly with the new Lightroom 5," according to the message.
Based on what I've heard from those users, Adobe has made a potentially serious marketing error and companies such as OnOne are moving to take advantage of it. An e-mail message from the maker of the Perfect Photo Suite, which works with Photoshop, says that the latest version of the software will work with or without Photoshop: If you're moving to Creative Cloud, "Perfect Photo Suite is the perfect complement to your Photoshop workflow, giving you an easy way to do things that are difficult and time-consuming to do in Photoshop. The Suite also works perfectly with the new Lightroom 5," according to the message.
On the other side, the message continues, "If you think Photoshop is too cumbersome and complicated, or if you find Photoshop Creative Cloud unappealing, you can use Perfect Photo Suite to do many tasks that normally require Photoshop. And Lightroom users (including version 5) will find that the Suite is the perfect companion product."
I suspect that some of the other makers of plug-ins will move to make their applications work in a stand-alone mode, too.
2013 Looks Like the Year of the Tablet
PC sales, both for desktop systems and notebooks are down considerably and continue to drop, but sales of tablets are headed for the roof. International Data Corporation (IDC) tracks computer sales and earlier had predicted a drop of about one and one-half percent from last year's sales, but this week it changed the estimate to predict a drop of nearly 8 percent.
Tablet computers are on track to outsell other types of computers for the first time this year. IDC expected that to happen, but not until next year.
The estimates suggest that about 230 million tablet computers will be sold, and that's almost 60% higher than last year. Notebook computer sales will drop to about 190 million, down from about 201 million last year. IDC says that by 2015 tablets will probably sell more units than desktop and notebook computers combined.
This is not to suggest that desktop and notebook computers are going to vanish as a breed; after all, some applications need the power and storage that only a larger computer can provide. But tablets offer near-PC-like capabilities for people who are on the go. Many people who put off purchasing new computers during the worst of the recession are buying again, but they're adding tablets instead of replacing desktops or notebooks. IDC says that it expects sales of more traditional computers to begin increasing again in 2015 with gains in the notebook market coupled with continuing declines in the sales of desktop systems.
Facebook Can't Find a Way to Rid Itself of Hate Speech
Eliminating hate speech from services such as Facebook isn't censorship and it's not being "politically correct". Free speech is not guaranteed on forums that are owned and operated by any company or individual: If you use the service, you're obliged to play by the rules. Likewise, there are legal prohibitions against hate speech.
But Facebook says the process it uses to eliminate hate speech hasn't worked as well as expected. As a result, advertisers are reacting to pushback from women's groups are are dropping their Facebook ads.
A blog post by Facebook's safety team said that the company had been working to improve their system and to respond to reports of violations. The systems haven't eliminated all content that violates Facebook's standards, the post said, and then promised to do better.
A group called Women, Action & the Media has asked Facebook to work with advertisers whose ads appear on pages that feature hate speech. The group released an open letter that says Facebook needs to improve its efforts to remove content that "trivializes or glorifies violence against girls or women."
Speaking of Facebook, remember the initial public offering that was widely considered to have been botched? Now Nasdaq says that it will pay a $10 million fine resulting from that IPO.
The US Securities and Exchange Commission says that several decisions by Nasdaq on the day of the IPO last year created several regulatory violations. Nasdaq will pay the fine to settle civil charges.
The exchange's errors caused more than 30,000 Facebook orders to sit without action for 2 hours. The orders should have been executed or canceled. As a result of the errors, investors lost some $500 million. As is usual in events such as this, Nazdaq agreed to pay the fine but without admitting guilt or problem.
