Serious Threats to Your E-mail Account
This is important! The thieves who use other people's e-mail accounts to send spam seem to be making a concerted effort to use your e-mail account. And mine. And everyone else's. This week I received a message from someone who frequently sends documents by using one of the transfer services. The service sends an e-mail with a link to the document. At first glance, it was clear to me that the message was a fraud: First, it wasn't from the service he uses. Second, despite the fact that the message had clearly come from his G-mail account, it wasn't written the way he writes. And third, when I hovered the mouse cursor over the link, I noticed that it pointed to a location several levels below the Wordpress administrator directory on a domain I'd never heard of. Apparently the owner of the site is a soccer player who knows nothing about website security. The was a fourth clue, but I didn't notice that until later: I had received 5 copies of the e-mail, one to each account that were in the victim's list of contacts.
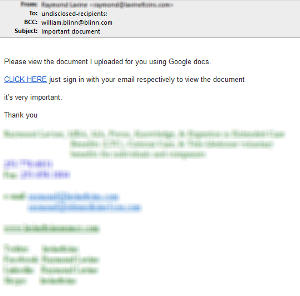 Click the message to see it full size. I've obscured the sender's name, e-mail address, phone numbers, and handles on services such as Twitter, LinkedIn, Facebook, and Skype. They are all legitimate because this message came from his G-mail account and used his standard signature.
Click the message to see it full size. I've obscured the sender's name, e-mail address, phone numbers, and handles on services such as Twitter, LinkedIn, Facebook, and Skype. They are all legitimate because this message came from his G-mail account and used his standard signature.
The implications of this are clear: Not everyone is as suspicious of unexpected attachments as I am. It's particularly serious because this person actually does send information to people using this technique and some of the recipients might be expecting a document from him.
What Happens if You Click?
Well, I certainly wasn't going to click the link to find out! But I know how to view the code on a website without allowing it to do any harm to my computer. I've described that process before and it involves using Microsoft's Powershell command line utility to load the index page of the site into a variable and then examining the contents of the variable.
I used that method to follow the link. Fortunately, the cybercrooks weren't trying to install malware. Unfortunately, they had established a way to steal the victim's user name and password.
After displaying a Remax (real estate company) logo, the rogue site asks for the victim's e-mail address and password. The process even includes some sophisticated error checking designed to make sure the e-mail address is valid.
If you enter this information, the crooks will have immediate access to your e-mail account and will be able to use it to send anything they want to everyone on your contact list.
That caused me to think about my own G-mail security. Although G-mail isn't my primary e-mail client, I do forward all e-mail from my techbyter.com and blinn.com addresses there for backup and long-term reference. Additionally, I sometimes use G-mail to send and receive messages when I'm using a computer that I don't own.
The password that I created for G-mail is moderately secure: 2 capital letters, 7 lower case letters, and 1 number. But is that good enough? And what if I fall prey to an attack such as the this one in which I willingly, if accidentally, give my user name and password to the bad guys?
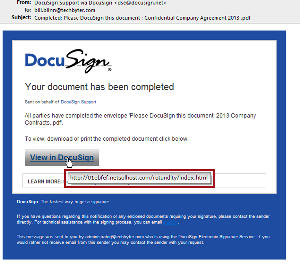 It's easier than you might expect. Here's yet another highly convincing fraud. I've hovered the mouse over the clickable link. See where it wants to take me?
It's easier than you might expect. Here's yet another highly convincing fraud. I've hovered the mouse over the clickable link. See where it wants to take me?
Google has an answer for that but, before I get to that, this kind of attack clearly illustrates why it's essential to use different user names and passwords for each important account you have. By "important", I mean those that would cause problems for you if somebody else had the credentials. By definition, that would be any financial account. And although the safest option involves having unique credentials for every account, even most security experts are willing to give users a pass when they use the same credentials for trivial accounts such as newspaper logins.
When crooks obtain user names and passwords, one of the first things they do is try to use them at bank websites. So if you give away your G-mail credentials and you use the same credentials at the Grand Mammoth Bank, you're in trouble.
Google's Safety Net
It's called 2-step verification and it adds an extra layer of security to G-mail and all other Google services that you use. When you log on with your user name and password from a computer that Google hasn't seen before, Google will send a verification code to your cell phone, wired phone, or Google's own mobile app that doesn't require cell phone service.
When you receive the code, a 6 digit number, and enter it, you'll be logged on. If the computer is one you trust (a home PC or your own notebook computer, for example), you can tell Google to trust the computer and never ask for another verification code. But if you log on from a public computer, you won't designate it as "trusted".
And if a crook has your user name and password, he (or she) won't have a way to obtain the verification code unless the crook also has your cell phone.
What happens if somebody steals a trusted computer? Easy. Use any other computer to log on and tell Google to stop trusting that computer.
Considering the process of setting this up takes only a few minutes and setting each computer to trusted status consumes less than one minute per computer, it seems like a good trade-off between security and ease of use.
How to Set Up 2-Step Verification
Google has made the process extremely simple.
First you'll want to confirm that the phone number you have provided is one that you have access to and that you want to receive authentication codes on. You also need to decide whether you want Google to send the code using SMS text messaging, voice, or Google's mobile app.
Have Google send a verification code. You'll receive it about 2 seconds after you issue the request. Enter the code and click Verify. This step confirms that you have access to the phone number you claim to have access to.
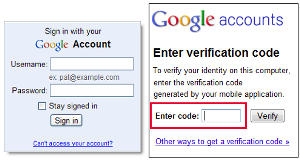 If you are using your own computer, you'll want to indicate that it's trusted so that you won't have to provide a new verification code every time you log on. If the computer isn't one that you own, leave the Trusted check box unchecked and you'll be asked for a new code every time you use the computer.
If you are using your own computer, you'll want to indicate that it's trusted so that you won't have to provide a new verification code every time you log on. If the computer isn't one that you own, leave the Trusted check box unchecked and you'll be asked for a new code every time you use the computer.
And that's it. You'll need to validate each new computer you log on from but this is a one-time process for trusted computers and the extra step takes just seconds when you log on from a computer you haven't trusted.
 You'll see something like this on your phone.
You'll see something like this on your phone.
You may note that I don't have a smart phone. You may also note that the phone I do have is about half a dozen years out of date.
This is the phone that I selected last year to replace my 10-year-old cell phone.
As much as I would like to have instant access to the Internet from everywhere, I have found that I prefer more to have access to about $50 per month that I would otherwise have to pay for a smart phone and the attendant data service required by the phone.
To misquote Freud, Sometimes a phone is just a phone.
What You'll See Along the Way
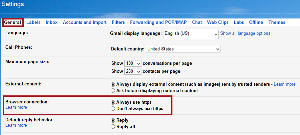 Click the little gear icon in the upper right corner (below your name) and choose Settings. This will open the General settings page.
Click the little gear icon in the upper right corner (below your name) and choose Settings. This will open the General settings page.
Before going any further, check the Always use HTTPS setting and then click the Save button at the bottom of the page. This isn't related to Google's 2-step authentication, but it's another worthwhile security measure.
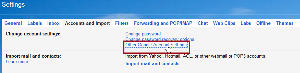 Next, select Accounts and Import from the menu and, when that page opens, click Other Google Account Settings.
Next, select Accounts and Import from the menu and, when that page opens, click Other Google Account Settings.
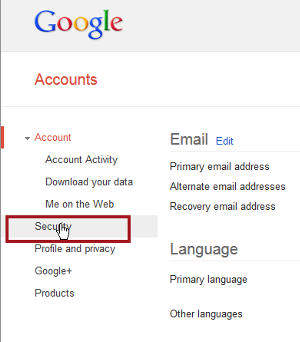 Now you'll finally be on the page from which you can access the Security settings.
Now you'll finally be on the page from which you can access the Security settings.
Question: Why does Google make this important setting so obscure?
Answer: I have no idea.
Click the Security option.
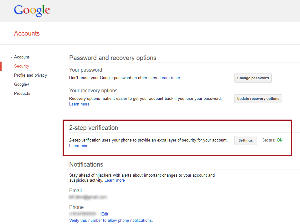 You'll see the 2-step verification section. If the status shown is OFF, you should turn it on by clicking the Settings button.
You'll see the 2-step verification section. If the status shown is OFF, you should turn it on by clicking the Settings button.
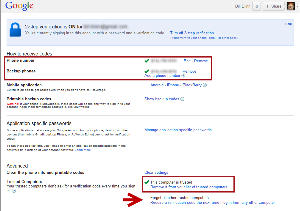 This is control central for 2-step verification. You must specify at least one phone number and it's a good idea to specify more than one. I use a cell phone and a wired phone. If you have a smart phone, select a mobile application.
This is control central for 2-step verification. You must specify at least one phone number and it's a good idea to specify more than one. I use a cell phone and a wired phone. If you have a smart phone, select a mobile application.
Google also can provide a list of one-time codes that you can use if you need to log on from a non-trusted computer but you're in a location that has no cellular service. Print the list and carry it with you. Each code on the list can be used only once.
At the bottom of the page, you'll see whether the computer is trusted or not and you can remove just this computer from the list of trusted computers or remove all computers from the trusted group.
In short, the hardest part about setting up Google's 2-step authentication may be finding the right place in the interface to start!
Maybe Being All Thumbs Isn't So Bad
ThumbsPlus is a small application that plays a big part in TechByter Worldwide every week. Nearly every image you see has been touched by ThumbsPlus because it makes the process of creating two copies of each file—the smaller image that's embedded in each report and the larger image that appears when you click the smaller one—easy. The new version has some enhanced capabilities.
Cerious Software, unlike a firm such as Adobe that has hundreds of developers who work in teams, seems to have just one developer. That makes it easy to maintain a constant vision but it also makes the development process slow. Both the current version (9) and the previous version were in development for an extraordinarily long time and version 8 was probably released before it should have been because its operation was always somewhat quirky.
Version 9 takes care of that and adds some useful features.
 At its center, ThumbsPlus is designed to manage a graphics library. You can have it scan individual directories, an entire disk drive, or multiple drives to create a thumbnail view for every image it finds. Directories that contain images are highlighted so you'll know exactly which directories contain images.
At its center, ThumbsPlus is designed to manage a graphics library. You can have it scan individual directories, an entire disk drive, or multiple drives to create a thumbnail view for every image it finds. Directories that contain images are highlighted so you'll know exactly which directories contain images.
The feature I use the most is the ability to define a series of steps that will be performed on any number of selected images. The largest images I use on the TechByter site are 1000 pixels wide and the thumbnails that are included in articles are 300 pixels. In most cases, the original image is larger than 1000 pixels, so each image must be processed twice, once for each size. Repetitive tasks such as this wear on me so I'm happy that ThumbsPlus offers a quick and easy solution.
The two images have similar names (picture.jpg and picture_sm.jpg, for example) and the thumbnail image has the "_sm" suffix. The automatic process uses the original PNG image's file name, converts the new images to jpg, resizes them as needed, applies "_sm" to the smaller image, and stores them in a staging directory where I can review them before moving the images to the website development directory. An opportunity exists, with each step, for a human to make an error. ThumbsPlus does the same time every time.
The process wouldn't be at all tedious for a single image but some of the weekly programs contain 20 or 30 images. Selecting all and running the processes, whether for 3 images or 30, takes only a few seconds.
 ThumbsPlus can acquire images directly from a camera or scanner (although not my scanner, which predates even Vista and has no drivers for Windows 7 or Windows 8). ThumbsPlus can edit images, convert them to other formats, create galleries, create thumbnails, and password protect images. You can create slide shows or select an image and set it as the Desktop wallpaper. If you need a Web page to display a catalog of your images, ThumbsPlus can do that, too.
ThumbsPlus can acquire images directly from a camera or scanner (although not my scanner, which predates even Vista and has no drivers for Windows 7 or Windows 8). ThumbsPlus can edit images, convert them to other formats, create galleries, create thumbnails, and password protect images. You can create slide shows or select an image and set it as the Desktop wallpaper. If you need a Web page to display a catalog of your images, ThumbsPlus can do that, too.
A new feature allows ThumbsPlus to log in to your Facebook account so that you can browse and update photo albums.
Much of the application's functionality is controlled by Python, a programming language that Cerious has exposed for users to modify. Facebook access, for example, uses Python and the developer plans to convert more of the program's features to Python. Users can create their own actions using Python and the result could be a growing library of user-written functions.
ThumbsPlus is not Photoshop but it does include some basic editing tools such as red-eye removal and the ability to rotate, flip, resize images or convert them to black and white or sepia.

 ThumbsPlus is a handy way to manage lots of images.
ThumbsPlus is a handy way to manage lots of images.
If you're looking for basic photo organization and the ability to create Web pages and sample sheets of your images, ThumbsPlus is a good choice. You won't have the extensive set of features provided by Photoshop but the learning process will be a lot easier and faster, too. ThumbsPlus is the right tool for a lot of tasks.
For more information, visit the ThumbsPlus website.
Short Circuits
The Battle Between Privacy and Security Continues
As the first step in what will be a push by Google to make it harder for law enforcement agencies to obtain from Google information about users of the company's applications, Google has released a high profile "Transparency Report" that explains the circumstances that must exist when Google gives investigators your information.
The report by Google says that there has been a steady increase in government requests for users’ information. Google says that it has reported on these requests since 2010 and that the goal is to make the report more informative.
For the first time, Google has included a breakdown of the kinds of legal processes that government entities in the US use when compelling communications and technology companies to hand over user data.
From July through December 2012, Google says that 68% of information requests were in the form of subpoenas issued under the Electronic Communications Privacy Act (ECPA). Subpoenas are relatively easy to obtain because, in most cases, no judge needs to be involved. Another 22% used ECPA search warrants that are typically issued by judges based on a demonstration of "probable cause" to believe that certain information related to a crime is presently in the place to be searched. And the final 10% were court orders issued under ECPA by judges or other processes that Google says are difficult to categorize.
Requests for data have increased by more than 70% since 2009. In total, Google received 21,389 requests for information about 33,634 users during the period.
Now Google has announced that it will lobby federal legislators to make it harder for law enforcement authorities to gain access to e-mails and other digital messages. According to Google's chief legal officer, David Drummond, this would require modification of the 1986 US Electronic Communications Privacy Act.
The Internet has changed a lot since 1986 and the existing law does not require government investigators to have a search warrant when requesting access to old e-mails and messages when they have been stored online. A search warrant is required for letters that you have stored in a box or a file drawer as well as for e-mail messages you may have saved on a computer's hard drive.
In 2012, Senator Patrick Leahy, who chairs the Senate Judiciary Committee, introduced a bill that would have updated the current law but law enforcement agencies and the FBI expressed concerns that any new restrictions would slow crime investigations and might even endanger victims. The legislation went nowhere.
Leahy says that the law hasn't kept up with technology and updating privacy laws is one of his top priorities this year.
Paid Content May Be Coming to YouTube
AdAge magazine is reporting that YouTube has plans to offer paid subscriptions for some of its content. The change is expected to occur sometime this year but no date has been set. YouTube is owned by Google.
According to the magazine account, YouTube has asked several video producers to submit applications for-pay "channels". AdAge said that information was provided by sources who did not want to be named. AdAge suggested that individual channels could be offered before mid year and could have prices ranging from $1 to $5 per month.
YouTube currently includes some high-quality video in addition to the thousands of amateur videos of cats being cute and stupid people being injured after trying a stunt that is often preceded by the words "Hey! Watch this!" The high-quality videos are supported by advertising so the paid channels would be a new business model for YouTube.
This isn't the first time that YouTube and paid video have been used in the same sentence but it's the first time that the idea seems to have sufficient traction to move forward.
Apple Trademarks its Stores
Apple has been granted a trademark on the design of its stores. So now anybody who wants to open a store that has "a clear glass storefront surrounded by a paneled facade", particularity if the interior includes an oblong table with stools in front of video screens that have been flush mounted to the back wall, will have to obtain clearance from Apple.
Asking the US Patent and Trademark Office for help is apparently Apple's response to a phony but authentic looking Apple store in Kunming, China. When the store opened, the customers thought that they were buying Apple products and even the employees thought they were working for Apple. Since then, Chinese authorities have forced the store to close and, with it, more than a dozen more that were selling Apple products but without Apple's permission.
In 2003, Apple received a patent on the glass staircases that are present in many Apple stores. When I visited one of the Apple stores in New York City, I thought that the glass stairs were simply a nod as the glass walkways that connect the opposite sides of Grand Central Terminal. Jobs is listed as the inventor of the glass staircase even though the glass walkway preceded him by decades.
US trademark rights do not extend outside the country so Apple couldn't use approval by US authorities to fight a competitor in China. Apple has about 250 retail stores around the United States and operates stores in about a dozen other countries.
