"lol is this your new profile pic?"
If you're a Skype user and you followed a link that came with a message such as this, your computer may have been compromised. Antivirus maker Sophos says that thousands of unsuspecting users have clicked the links and, as a result, were offered a malicious file.
This week's program has an underlying security theme because security is becoming increasingly important. People who want to steal anything you have, from passwords to money, will attempt to use any application on your computer to achieve their goals.
Graham Cluley at Sophos says that the process is simple. Those who click the poisoned link are given a zip file that typically includes the words "skype" and "image", along with some random numbers. The zip file isn't dangerous in its own right but it contains executable files that are.
Sophos says that running the executable file will install a Trojan horse application that provides full access to all data on your computer.
The malware installs in the Application Data directory of the current user's profile and then adds an auto-run instruction to the Registry. Each time you start the computer, the malware will load.
Then What?
 The malware is a variant of the Dorkbot worm and it can steal passwords, enroll your computer as a member of a botnet, or set you up for installation of what's called "ransomware", fake security applications that claim to have found threats on your computer and will remove them only when you pay.
The malware is a variant of the Dorkbot worm and it can steal passwords, enroll your computer as a member of a botnet, or set you up for installation of what's called "ransomware", fake security applications that claim to have found threats on your computer and will remove them only when you pay.
Clueley says that many variants of the Dorkbot attack have been spotted recently and that they commonly use social media such as Facebook and Twitter but "The threat can also spread via USB sticks, and various instant messaging protocols."
Instant messages via Skype are less common than those on Facebook and many Skype users seem to be less suspicious of such threats than are Facebook users, many of whom have learned the hard way that being suspicious of links is a virtue.
Email Continues to be a Popular Malware Vector
This week I received a message from a cousin who lives in Connecticut. The message said "You're here because someone you know nominated you for a discount" and offered a link to click.
I didn't click the link but I did let the cousin know that her e-mail account had been compromised.
This isn't an unusual situation, either. It's a rare week when I fail to receive at least one message from an acquaintance whose e-mail account has been taken over by a rogue application. In some cases, I've seen this happen to the same person several times.
ANOTHER GOOD SOURCE OF INFORMATION
Symantec maintains a large database of vulnerabilities (more than 47 thousand records over the past 20 years) and Symantec released a report earlier this year on security threats.
Download Symantec's report (PDF) here.
Graham Cluley at Sophos says that it's important to be suspicious of unsolicited out-of-character messages sent to you by online friends. The "out-of-character" part is important: If your cousin normally addresses you by name, sends chatty messages, and has never sent you a link before, then trusting a message that says "Check this link!!!!!!!" would probably be ill-advised. More exclamation points are good indicators of bad messages, too.
When you receive a message that seems to come from a friend, you don't know that the friend actually sent it. Because the "from" part of an e-mail is easy to forge, you don't even know if the message came from their computer. And when malware is installed on the friend's computer, even the routing headers will be legitimate. A message may have come from your friend's machine but it may not be the friend who sent it.
As I've mentioned before, Skype users who expose their addresses to the world (as I do out of necessity) will receive numerous fraudulent messages. Even so, Clueley says that Skype claims to take security seriously. He cites the following message from Skype: "Skype takes the user experience very seriously, particularly when it comes to security. We are aware of this malicious activity and are working quickly to mitigate its impact. We strongly recommend upgrading to the newest Skype version and applying updated security features on your computer. Additionally, following links – even when from your contacts – that look strange or are unexpected is not advisable."
Smart Phones: A New Malware Vector
If you own a smart phone that has any means of connecting to your desktop or laptop computer, you also have a new and attractive way for fraudsters to inject malware. That's a comforting thought, isn't it?
 A few years ago, security experts were warning that malware would eventually begin appearing on mobile devices. That warning has now been modified so that the verb is in the present tense rather than the future tense.
A few years ago, security experts were warning that malware would eventually begin appearing on mobile devices. That warning has now been modified so that the verb is in the present tense rather than the future tense.
SMSZombie has infected half a million phones and tablets. Currently this threat is active primarily in China but it's particularly problematic because it has built-in defenses and, once installed, it's difficult to remove. SMSZombie is an Android application and it serves as a proof-of-concept for malware designers who want to improve the potency of their programs.
A few weeks ago, I described Lookout Mobile Security, a service with both free and paid versions that keeps an eye on the security of mobile devices. Lookout was the first to spot an Android malware application that has come to be called "NotCompatible". Android users who visit an infected website will have the application installed. It's disguised as a security update as a social engineering tactic designed to convince users to allow the installation.
NotCompatible should be of concern to businesses and to anyone who operates a home network because it can gain access to private networks by making the Android phone or tablet appear to be a proxy server. The proxy sees all network traffic and can grab user names, passwords, or any other data.
One of the most "popular" mobile malware applications worldwide is called FakeInst SMS Trojan. It has many variants and can be found lurking in Instagram, Skype, and even the Opera browser. This one can cost the user a lot of money by sending SMS messages to numbers that charge the caller a fee.
"Popular" might be somewhat of an understatement. Some security experts estimate that more than half of all Android malware applications are variants of this one even though the basic FakeInst SMS Trojan infection exists in Russia and Eastern Europe.
Lucky Cat is another harbinger of things to come. It is what's called an advanced persistent threat (APT), the first such malware to attack Android devices. Lucky Cat is not, however, limited to Android devices. At its most basic, it's simply a Trojan horse that steals information but the cat's footprints are on Japan's energy and aerospace industries; it has also been used to collect data from activists in Tibet, which raises questions about its origins.
Some malware applications, when installed on a mobile device, can obtain sufficient information about the user's other electronic devices that these can be indirectly exposed to danger.
You may be old enough to remember when computers had no anti-malware applications. Then, only those who engaged in unsafe computing practice needed protections and the definitions were updated only once per quarter. Anyone who operates a computer today without a robust suite of anti-malware applications simply doesn't understand how the world has changed.
That same line of progression is happening in the world of smart phones but it's moving much faster than when the primary target was just computers.
Free Software: You May Get More than You Wanted
There's no shortage of "WAREZ" sites on the Internet. These are places where you can go to download commercial software for free. Microsoft, Adobe, and most other software publishers have processes in place to ensure that their applications are installed on a limited number of computers. The WAREZ sites offer software with these features removed but often with other features added. According to a Microsoft report, about three quarters of the people who install WAREZ also install malware that comes with the stolen applications.
Microsoft publishes its Security Intelligence Report twice per year and you can download the 146-page report here. There's also a shorter 16-page report of key findings.
The report is intended to provide a clear assessment of the threats that exist so that IT professionals can protect against them. Volume 13 covers January through June of this year.
According to Tim Rains, the director of Microsoft's Trustworthy Computing project, "One of the most interesting trends to surface out of the latest report was the surge in software activation key generators being used as a mechanism to distribute malware. In the first six months of 2012, the threat family Win32/Keygen, representing software activation key generators, was detected nearly five million times. Keygen detections have increased by a factor of 26 since the first half of 2010 and today Keygen is the number one consumer threat family worldwide, rising above other prevalent threat families like Pornpop, Blacole, Conficker, and FakePAV. The prevalence of Keygen varies from location to location, however it is listed as a top 10 threat for 103 of the 105 countries/regions studied in [the report]. That means Keygen is in the top 10 list of threats for 98% of the locations we provide analysis for in [the report]."
Win32/Keygen generates keys for many publishers' applications and is not, by itself, malicious. But it is often included with malware, Microsoft classifies it as "potentially unwanted software". The report says that 76% of computers reporting Keygen detections in the first half of 2012 also reported detections of other malware families. This is a good indication that Keygen is often bundled with, or leads to, malware infections.
Short Circuits
Fewer PCs This Year
Research by IHS ISuppli says that fewer personal computers will be sold this year than last year. If the forecast proves to be true, this will be the first time since 2001 that year-over-year computer sales will have declined. But not by much.
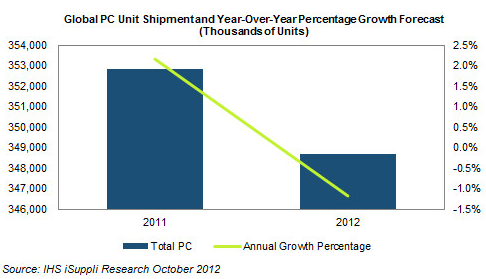
Despite the dramatic image that shows what appears to be a precipitous drop in computer sales, note the percentage scale on the right. The actual drop is forecast to be one percent (1%). Looking at raw numbers, ISuppli says it expects 349,000,000 computers will be sold this year, down from about 353,000,000 last year. The change appears larger when considered in light of the fact that computer sales have been rising every year for 11 years.
Additionally, PC makers expected sales of lightweight laptops ("ultrabooks") would improve sales but the real growth has been in smart phones and tablet computers. In many cases, the new portable devices are displacing notebook computers. And some buyers might simply be waiting for computers that run Microsoft's Windows 8 operating system to be ready.
You'll be seeing a lot of Windows 8 in the next year because, except for Apple and Android devices, some version of Windows 8 will be found on just about any computing device you buy, from smart phones and tablets to notebook computers, desktops, and servers.
The long anticipated post-desktop-computer world seems to be arriving.
Hewlett-Packard Falls out of First Place
For many years Hewlett-Packard was the number one personal computer maker but that is no longer the case. And, depending on how you define "personal computer", maybe it never was. If that term means any personal computer regardless of operating system, then Apple is number one, has been for many years, and will undoubtedly continue to be for a long time.
Even though far fewer Apple computers are sold than are computers that run Windows, Apple is the only hardware manufacturer that manufactures Apple computers while several huge operations (HP, Dell, and Lenovo, for example), dozens of smaller companies (such as Acer, Asus, and Toshiba), and thousands of smaller shops all build personal computers that are based on processors by AMD and Intel and run the Windows operating system.
For the first time in 5 years, it appears that HP will be in the number 2 slot behind China's Lenovo, heir to the IBM PC. Gartner Research says that Lenovo has just under 15.7% of the market and notes that HP was a close second at 15.5% but to reach those relative positions, Lenovo's sales grew by 10% and HP's sales dropped by more than 16%.
A second research firm offered similar numbers but maintained that HP was still in the lead by 15.9% to 15.7%.
According to Gartner, worldwide PC shipments were down 8% in the 3rd quarter from last year.
Who Are All These People and Why Are They Endorsing Me?
For the past several weeks, I've been receiving "endorsements" from people on LinkedIn. In many cases these endorsements have been issued by people I know only casually and for whom I have never done any work. So what's going on here?
It's a new "feature" from LinkedIn. The business social media company characterizes it as a watered-down recommendation. LinkedIn has allowed recommendations since the beginning but a recommendation required that the person offering the recommendation actually say something of value about the person being recommended. For endorsements, it's the quantity that counts, not the quality. Maybe that's why one person "endorsed" me more than a dozen times.
What am I supposed to do—endorse everyone who has endorsed me? And should I endorse the person who endorsed me a dozen times more than the others? I'm so confused.
Apparently I'm not alone. LinkedIn's David Breger has written about it on the company blog. Endorsements, he says, allow users to recognize acquaintances for their skills and expertise. "With just one click, you can now endorse your connections for a skill they've listed on their profile or recommend one they haven't added yet."
Currently this feature is available only in the English-language version and only in the US, India, New Zealand, and Australia. More locations are languages are planned.
Endorsements could be something more for a potential employer to examine. How many endorsements do you have? Are they from competent and qualified people? The endorsements can be issued for specific skills that the LinkedIn user has specified so a company that's looking for a project manager might consider more favorably a candidate who has hundreds of timeliness endorsements over another who has just a few. It's not the kind of thing that would make or break the hiring decision but it could be an indicator that pushes the needle up or down a bit.



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
