Spear Phishing: Smarter and More Dangerous
The message appeared to come from the IT department at Jeff’s company. The IT manager, whose office is in a distant state, said that a security problem had been detected on the corporate LAN. The problem had been resolved but all users should follow the attached link to a security partner’s website to confirm that their computer had not been infected. What should Jeff do?
Better yet, what would you do?
The message could be legitimate or it might be a “spear phishing” attempt. You’re probably familiar with “phishing”, the process of sending broadcast spams that seek to acquire information that cyber-criminals can use. Spear phishing is the smarter, more concentrated method.
 Routine phishing messages are sent to hundreds of thousands of people. As a result, I might receive a phishing message that claims to come from the Bank of America even though I’ve never had a BoA account. Over the years, the crooks have gotten better by picking small, local banks and sending messages to limited geographic areas.
Routine phishing messages are sent to hundreds of thousands of people. As a result, I might receive a phishing message that claims to come from the Bank of America even though I’ve never had a BoA account. Over the years, the crooks have gotten better by picking small, local banks and sending messages to limited geographic areas.
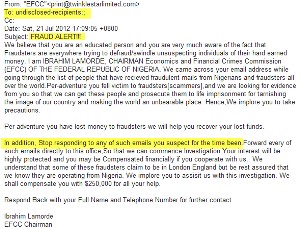
The message shown here purports to be from the Economic and Financial Crimes Commission of Nigeria and it's a typical and largely unremarkable example, except that it's one of a relatively new strain that warns against dealing with fraudsters and promises compensation if you work with the sender.
The messages typically include graphics stolen from legitimate messages and, in recent years, the text has begun to look more like something that a reasonably intelligent native speaker of American English would write. But there’s always a flaw that exposes the ruse for what it is: The message or the website that the victim is directed to will always ask for information that the sender will already have.
Spear phishing takes the threat to a new level. Customers of a telecommunications firm might receive an e-mail that says there was a problem with a recent order or a bill payment. To remedy the problem, you should visit company’s website (“just click this link”) and respond to a few questions.
 Spear phishing looks like this. ADP is a company with some 50 thousand employees worldwide and it processes payroll checks for millions of people. This message not only includes the ADP logo (conveniently linked from an ADP website) but it also looks and feels like a corporate communication.
Spear phishing looks like this. ADP is a company with some 50 thousand employees worldwide and it processes payroll checks for millions of people. This message not only includes the ADP logo (conveniently linked from an ADP website) but it also looks and feels like a corporate communication.
The message is plausible in that it describes security updates that are planned and simply asks the recipient to read more about the service and then view a 15-minute program. These are typical requests but hovering a mouse over any of the links would reveal that they do not point to ADP websites.
Following any of the links would almost certainly result in what's called a "drive-by" malware attack. I don't know that with certainty, though, because the site had been taken down before I had a chance to investigate further.
Never follow a suspect link with a browser! Instead, if you want to see the raw HTML and any other code that the site will serve, use Microsoft PowerShell (installed on any Vista or Windows 7 computer and available for XP) to make a webclient call and read the entire page into a variable. Once you've done that, you can safely inspect the contents of the variable on screen or write it to a text file and open it in Notepad or UltraEdit.
In this case, though, the page was gone.![]()
Sometimes the crooks target people who have accounts with a specific cell phone company and send a message that says a bill has just been paid or is due. Usually the amount is $1000 or more, which is enough to get the victim's undivided attention.
In Jeff’s case, criminals might be directing an attack at users within a specific company. The fraudulent message might not be sent to everyone. Instead, the crooks might be engaged in corporate espionage so they could be looking only for mid-level managers and above who might reasonably have accounts that would give them access to the company’s proprietary information.
The FBI explains it this way: “Instead of casting out thousands of e-mails randomly hoping a few victims will bite, spear phishers target select groups of people with something in common—they work at the same company, bank at the same financial institution, attend the same college, [or] order merchandise from the same website. The e-mails are ostensibly sent from organizations or individuals the potential victims would normally get e-mails from, making them even more deceptive.”
Obtaining information that can be exploited is easier than you might think. Possibly the crooks have cracked a social media site where the company’s employees hang out. Or they’ve sifted through your public website to scrape names and e-mail addresses from the code.
When they have the information they need, the crooks send e-mails that appear legitimate to targeted victims. The message may sound urgent and legitimate so a certain number of busy employees will simply respond to the message or click the link without even thinking about the possible dangers.
Once on a phony but realistic-looking website, they will be asked to provide passwords, account numbers, user IDs, access codes, PINs, and whatever else the crooks think they can exploit.
The FBI cautions that spear phishing can also trick you into downloading malicious code or malware after you click on a link embedded in the e-mail. This is an especially useful tool in crimes like economic espionage where sensitive internal communications can be accessed and trade secrets stolen. Malware can also hijack your computer and make it part of a malevolent network that is used to send spam, house stolen software, or participate in distributed denial of service attacks.
So What Should Jeff Do?
Common sense is the best defense. Most companies, banks, and agencies, don’t request personal information via e-mail.
Instead of clicking the link, pick up your phone and call the sender. Use your corporate directory, though, instead of any phone number provided in the e-mail. Those are usually just as phony as the e-mail and the website.
And never follow a link from an e-mail that warns about a security problem. Security experts will never include links. Instead, they will depend on you to know how to navigate to the bank or corporate website. Keep in mind that even legitimate-looking links might actually be frauds.
Phone Phishing
Threats can arrive by telephone, too. If you use Skype, you’ve probably seen “Urgent” messages that appear to come from Skype. They don’t, of course, and typing the URL that the recorded message provides will lead you to a site that dispenses malware.
But a phisher might also pose as a support-team member at your ISP and send an instant message that asks for your password. You’ll be told that they simply need to “verify your account” or maybe that they want to “confirm your billing information.”
Once you’ve provided the information the thief needs, he can access your account for fraudulent purposes or spamming.
It’s possible to avoid (or at least mitigate) phishing attempts by changing your browsing habits. If you receive a message that says your account needs to be “verified”, simply contact the company from which the e-mail apparently originates to check that the e-mail is legitimate. Do this without using any of the contact information provided in the message.
Nearly all legitimate e-mail messages from companies to their customers contain an item of information that is not readily available to phishers. PayPal, for example, will always address you by name and not as “Dear Customer”. The name PayPal uses will be the exact name that you provided when you signed up for the service.
E-mails from banks and credit card companies often include partial account numbers and thieves have figured out that many consumers don’t understand the difference between the first 4 digits of the account (which identify a bank) and the final 4 digits (which identify an individual). If the message calls out your credit card that begins with 4640, it’s a fraud. All Visa numbers begin with 4 and 4640 identifies Chase Bank. Hundreds of thousands of people who have Amazon Visa cards will have numbers that begin with 4640.
So before Jeff does anything (or before you do anything) it’s important to confirm that the request is legitimate and the only way to do that is to contact the sender using a method that has not been disclosed in the e-mail.
Mountain Lion Beats Microsoft to the Finish Line
In a year of low-priced major operating system upgrades, Apple's Mountain Lion beat Microsoft's Windows 8 if the two companies were competing for release dates. Maybe they were, but who knows. The Windows update will cost as little as $40. Apple's Mountain Lion, which became available this week, costs just $20. And that's a win for Apple, too.
And that $20 price tag is for ALL of the computers you own that are associated with your Itunes account and that are running one of the two most recent versions of the operating system, Snow Leopard or Lion. Some of the earlier upgrades cost more than $100 per computer.
In recent months I've mentioned Windows 8 many times but Mountain Lion (and the previous Lion) only in passing. In large part that is because the TechByter Worldwide budget doesn't currently allow for the acquisition and maintenance of a second testing platform. But even though I no longer have an Apple computer that would run a current version of the operating system, it's important to note Mountain Lion's arrival.
Not surprisingly, Apple's different world view is taking the company and its operating system in a direction that differs from Microsoft's. Microsoft's world view sees Windows on devices ranging from phones to servers. Apple's IOS operating system runs on handheld devices and OSX runs on desktop and notebook computers.
Both of these approaches are valid and it will be interesting to see which resonates more with buyers. In recent years, Apple has been making slow but steady inroads into the notebook and desktop market.
But just as Microsoft, in Windows 8, combined tablet-centric techniques for desktop and notebook computers, so is Apple bringing to its desktop and notebook operating system features that premiered on the Ipad. Two years ago, Apple named the event at which it previewed Mountain Lion's predecessor "Back to the Mac". The implication was that portable-device features were being ported back to the larger operating system.
Mountain Lion has built-in speech recognition but those who have used it compare the function more to Dragon Dictate, circa 1999. Dedicated speech recognition programs such as current versions of Dragon Naturally Speaking allow the user to speak more or less naturally while Mountain Lion wants ... the ... user ... to ... speak ... each ... word ... carefully ... and ... distinctly. And you have to be online for this to work because the actual processing isn't done on your computer.
This seems like an incredibly poor alternate solution to a problem that was solved a decade ago.
Apple says Mountain Lion includes more than 200 new features but there's one important feature that lives in Cupertino: Apple is encouraging (requiring?) developers to digitally sign their applications. This is a good way to mitigate the threat of malware being distributed via applications sold at the Mac App Store. Apple already exercises strong controls over applications sold in its store and this simply improves safety and security. Microsoft and Google (Android) would do well to follow Apple's lead.
Short Circuits
Number 2 Must Try Harder
Remember the old Avis commercials about how #2 tries harder. Microsoft seems to have taken that lesson to heart. The Microsoft Apps Store, available under Windows 8 will offer real trial periods. The Microsoft store will be #2 behind Apple's store or maybe #3 behind Android's store. Download an app. Try it out. If you don't like it, you don't pay for it. This apparently is a concept that's well beyond either Apple or Google.
Apps that you purchase from the Microsoft store will include a 7-day trial period. How does that compare with trials offered by Apple's Apps Store or Google's Android store?
- Apple: No trial period. You want to try it, you buy it; don't like it? Tough.
- Google's Android Store: Sure you can try it. We'll give you 15 minutes.
Neither of these policies seems to fit well with either company's public profile.
As with most trials, features may be limited during Microsoft's trial period. If you choose to upgrade to the full application, any customizations, settings, or data you've created during the trial period will persist. And if you have a trial application that's about to expire Windows 8 will remind you to upgrade.
Going to Kansas City
If you want fast and reasonably priced Internet service, Kansas City might be where you should live. Google will soon being providing gigabit Internet service for $70 per month. That compares to my $100-per-month service that runs at a small fraction of that speed
Google is using Kansas city to show what's possible by going around local cable and phone companies. Instead, Google will use its own optical fiber in the "Fiber for Communities" broadband service.
If you want cable TV with your Internet service, kick in an extra $50 per month and Google will include Nickelodeon, Discovery, Bravo, and Starz. Showtime is available for an extra fee but AMC, HBO, CNN, Fox News, and ESPN are missing. Google plans to expand the lineup but there's no publicly-available schedule.
Gigabit. 1000 megabits. My home service was recently expanded (with great fanfare) to 15 Megabits and a service that's now twice as fast as it once was is welcome but I'd sure like to have a service that 50 times faster than even my "faster" service.
Google is doing this to show how faster Internet service can be used. Verizon has a similar, but much slower, program. The Verizon FiOS (fiber optic) connections are available in several cities, including some parts of Manhattan, but the speed is about what I get at home -- 15 Megabits per second. Verizon has stopped expanding it's low-speed fiber network because it hasn't proved to be popular with consumers.
It Was a Dark and Stormy Night (Thursday, 26 Jul 2012)
I certainly am glad to know that this climate change stuff is all a hoax. Bad science. Nonsense invented by Al Gore to stifle free enterprise. Otherwise, I might be sitting here in the dark on a Thursday night writing about climate change instead of putting the final touches on the weekly program summary.
So the fact that I'm sitting in the dark and typing on an Android tablet (sure am glad I decided to buy the keyboard!) is apparently a figment of my overstimulated imagination. It's the second time I've had this particular hallucination in about a month, though, and I find it a bit tiresome.
When this happens a year from now, I might be typing on a Microsoft tablet if I can find a way to work it into the budget. That's what I was discussing with a co-worker earlier today--the fact that tablets aren't going to be used for writing novels or by editors who are working on 500-page non-fiction books or by programmers who are developing new applications or even for creating websites.
These uses all require too much keyboard and mouse interaction to be candidates for tablets. As useful as as a tablet is, it's not a full computer. It can be used to read a document, to add or delete bits of text, to look up information on the Web, to create a query that will be submitted to a MySQL database or Access, to run applications designed for the tablet, and to perform hundreds of other useful functions; but a tablet is not a workstation.
On last week's program I discussed the next version of Microsoft Office and earlier on this program I noted the new release of Apple's operating system along with the approaching release of Microsoft's new operating system so there's no point in rehashing that here. But I will say that it's a good thing that Microsoft and Apple and Google (and others we don't yet know about) are thinking about how we use computing devices now and how we might use them in the future. It makes the future exciting.
Somebody may have the answer. It might not be Microsoft. It might not be Apple. And when "the answer" is found it might be "the answer" for only a year or two. That's what's so interesting about technology. Better solutions are developed every day. Today's giants stand on the shoulders of yesterday's giants. And who knows what tomorrow will bring.
Probably more storms and power outages. At least if you believe that most scientists are right. If you believe that it's all nonsense, carry on.



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
