Windows 8 (Closer and Closer)
The Windows 8 Consumer Preview is out and available for download by anyone. We're still many months away from release and this is still beta software. The next step in the process, 2 or 3 months from now, will be another general testing release. That will be followed by a release candidate and then, before the end of the year, the new operating system will be released to manufacturing.
[Corrected 3 March 2012 at 13:25:16: In the original edition, I had written that this version is still "alpha" software. It is not. This is a beta version. I regret the error.]
 The new Windows 8 logo was leaked (intentionally or not) before the Consumer preview was released and depending on who's talking, it's a bold step forward or a throwback to 1985. The multi-color logo with the waving flag is gone. Instead, the Windows 8 logo is a cyan window at an angle. That's it over at the right.
The new Windows 8 logo was leaked (intentionally or not) before the Consumer preview was released and depending on who's talking, it's a bold step forward or a throwback to 1985. The multi-color logo with the waving flag is gone. Instead, the Windows 8 logo is a cyan window at an angle. That's it over at the right.
Overall there seem to be more complaints about it than praise but that's to be expected. We all want something new but when that something new comes along, many of us resist it. Eventually we accept it, learn to like it, and by this time next year some of this year's haters will probably be telling us how much they liked it all along.
It is very much a minimalist design but it immediately says "mobile" and "tablet", two pieces of technology that will play large in the upcoming version of Windows. But to some extent it doesn't matter too much whether people like the new logo or detest it. In fact, it's to Microsoft's advantage for both camps to exist because now there's discussion and controversy.
Although TechByter Worldwide is primarily about technology, I have always admired design. For that reason, you probably would expect me to write about the logo. It's also being written about and discussed in various design blogs. But it's also a topic for publications such as PC World where Tony Bradley wrote "The new Windows 8 logo is pure genius. It has captured attention, it is driving discussion, and it has clearly established itself in just a few days as a unique, distinguished symbol of the future of Windows." And David Murphy at PC Mag summarized reactions from various designers and non-designers but carefully avoided saying whether he likes it or not.
The new logo is very plain. It is a gigantic departure from the previous logo just as Windows 8 is a gigantic departure from previous versions of Windows. And in many ways it seems like the perfect choice for Windows 8. My only real question is about the color. Cyan has never been my favorite color but I think a deeper blue would have reminded too many people of IBM. I suppose they could have been really bold and gone with a deep purple logo. Or, because green figures so prominently in the first public test release, maybe a green.
 Would this have been better? I don't think so!
Would this have been better? I don't think so!
Microsoft at Mobile World Conference
Barcelona hosted this week's Mobile World Conference and it appears that two topics were real stand-outs in Spain: Tablets and Windows 8. At the conference, and as suspected, Microsoft announced the Consumer Preview edition of Windows 8 on Leap Day. You can download the Consumer Preview from Microsoft's website. I recommend selecting the ISO option at the bottom of the page. Download the file that's right for your computer (64-bit English is 3.3GB and 32-bit English is 2.5GB). It's also available in Chinese, French, German, and Japanese.
The Windows 8 Consumer Preview is considered to have more bugs than the Developer Preview. That's not a big surprise because the Developer Preview omitted many features and everything that's expected to be in the final version of Windows 8 is in the Consumer Preview. Microsoft has about 3 months to continue working on the operating system before they'll need to produce a true release candidate and another 3 months (more or less) after that to continue squishing bugs and applying tweaks before they'll need to release the code to manufacturing and to the OEMs.
Google's main focus at the show was Android tablets with dozens of tablets and smart phones on a model-railroad-like display.
If you have an Android device today, it's probably running version 2 or 3 of the operating system. Version 4 (Ice Cream Sandwich) is approaching and Google hopes that the new version's features will revive interest in Android. Even so, it appears that there are problems loading this new OS onto smart phones. Most of the "new" smart phones on display at the show were still running much earlier versions of the Android operating system. If that continues to be the case over the next year, Microsoft's Windows Phone 8 could fill an opening in the marketplace.
Downloading and Installing
Use the link above to download the ISO file. Even though you can install over the Internet, I never trust this method. I'd rather download the file to be sure that I have everything before I start. Burn the file to a DVD and boot from it. There are options for dual-booting with an existing Windows 7 (or earlier) installation as well as for updating an existing Windows 8 Developer Edition preview but these options are not clear from the installer and it took a while to confirm the process on Microsoft's website.
Also, you will need an activation key. The key is shown on the download page and I'll repeat it here: DNJXJ-7XBW8-2378T-X22TX-BKG7J.
Microsoft also includes clear warnings on the website about the potential for something to go wrong. I wouldn't install Windows 8 on a production computer unless I had first backed up everything. And I probably wouldn't install it on a production machine even then. Use a secondary computer for testing.
After installing Windows 8 Consumer Preview on the Windows 8 Developer Preview partition, I rebooted the machine, noted the uncommonly attractive dual-boot screen, and selected Windows 7 to confirm that everything was still working as expected. It was.
Another reboot took me to Windows 8 and the end of this account. I haven't seen enough of the Consumer Preview to provide an honest, usable summary. I'll save that for another day.
 One thing I have noticed, though, is that I can't currently use Windows 8 for more than a few minutes. Little frowning face appears with the term "DPC_WATCHDOG_VIOLATION". (Couldn't you guys be more inventive than to steal the "Sad Mac" image from Apple?) Despite saying that the system will restart in 5 seconds, it never does and the only solution is a power-off reset.
One thing I have noticed, though, is that I can't currently use Windows 8 for more than a few minutes. Little frowning face appears with the term "DPC_WATCHDOG_VIOLATION". (Couldn't you guys be more inventive than to steal the "Sad Mac" image from Apple?) Despite saying that the system will restart in 5 seconds, it never does and the only solution is a power-off reset.
Again, it's important to keep in mind that this is beta software and is expected to be buggier than the earlier Developer release. That expectation has certainly been realized.
Previous Windows 8 reports are here.
Nexus File: A Windows Explorer from Korea
I've never been happy with the Windows Explorer. It shows just one panel and doing anything useful requires opening two copies of the application. Now I've found Nexus File, a replacement for Windows Explorer written by a software developer in South Korea. Visually it reminds me of applications from the 1990s but when it comes to performance and functionality, it beats anything Microsoft has ever offered.
I wasn't looking for a new file manager because no "replacement" I've found has ever worked very well but I found myself on Noh JungHoon's website to download Nexus Font, a typeface manager, when I noticed that he offered several other utility programs:
- Nexus Money (an income/expense manager for Iphones): I didn't download it because I have no Iphone to test it with.
- Nexus ToDo (a to-do list): I didn't download it because Outlook does a good job with scheduling and task lists.
- Nexus Image (an image viewer): I've downloaded this but haven't yet tested it.
- Nexus Subway (an Iphone map for subways in Korea): I didn't download this because I don't have an Iphone, I don't live in Korea, and I cannot read Korean.
- Nexus Call (and Iphone dialer): Nope. No Iphone.
- Nexus Font (the font manager I wanted): It turned out to be not what I needed and it seems to lack the essential features of a font manager so I won't be reviewing it.
- Nexus File (the file manager): Consider this a lucky find!
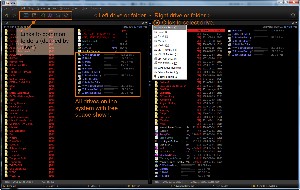 The first thing you'll see when you open Nexus File is that there's a lot of information to see!
The first thing you'll see when you open Nexus File is that there's a lot of information to see!
You'll find icons in the upper left corner for common locations such as Desktop, Documents, Pictures, Music, Videos, and Favorites. These will take you to the Windows defaults unless you change them. That's right: You can change them. I have Pictures take me to the "DIGITAL CAMERAS" directory on drive D, for example. And Music takes me to "F:\Itunes_WFB\iTunes Media\Music".
Another key feature is the list of all drives on the system and an indication of how much space remains on the drive. This is visible regardless of which drives or directories you have selected in either the right or left panel.
The left and right panels make it easy to drag and drop files from one location to another. The inability to do this is one of the major shortcomings on the Windows Explorer.
 Selecting a different disk drive for either the right or left panel is as easy as clicking the icon in the upper left corner of each panel and selecting the drive from the drop-down list. From there, you can easily drill down to any directory.
Selecting a different disk drive for either the right or left panel is as easy as clicking the icon in the upper left corner of each panel and selecting the drive from the drop-down list. From there, you can easily drill down to any directory.
Oh, and you may notice some icons between the two sides. Those allow you to select or deselect files in groups, to click an icon and copy files from left to right or right to left, to sort files, and to define columns that are displayed.
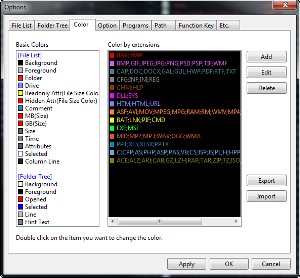
If you don't care for the colors, you can change them to suit your preferences. The color scheme is one of the most complete and robust that I have ever seen. You choose the background and foreground colors, of course, but you can also specify the color used to indicate a folder, a drive, files with read-only or hidden attribute set, directories that are open, and more.
If that's all this Windows Explorer replacement did, it would be well worth the few minutes you would spend downloading it. But there's more.
 I should mention that Noh JungHoon, the author of the program, provides it without cost and without obligation. He does offer a donation option and, of that, he says "Most of my programs are distributed as a freeware. However, if you think that those programs are useful enough and you wish to make a donation...., your donation will help me to run this site and encourage me to develop more useful programs." The donations are handled via PayPal so the process is quick, easy, and secure.
I should mention that Noh JungHoon, the author of the program, provides it without cost and without obligation. He does offer a donation option and, of that, he says "Most of my programs are distributed as a freeware. However, if you think that those programs are useful enough and you wish to make a donation...., your donation will help me to run this site and encourage me to develop more useful programs." The donations are handled via PayPal so the process is quick, easy, and secure.
Using Nexus File
There's no help file but most people probably won't need one. The Help option on the menu takes you to the programmer's website and the page simply says "Coming Soon." But adjacent to that menu option is one called Shortcut Keys. Click that and you'll find a list of at least 100 functions that are assigned or can be assigned to a key press. If you don't like the way Noh JungHoon set up the key assignments, you can change them.
You're probably beginning to see why I consider this such a huge improvement over the Windows Explorer.
Nexus File has 8 options in the Menu bar and each of those has numerous selections and sub-selections under it. I'll skim over the highlights and recommend that you download this application and test drive it. In other words, I won't mention every option on every menu item.
- File Menu: Select a file and press Enter to open it or run it. Pressing Ctrl-Enter allows you to specify parameters for the program (and this works whether it's a program file you're opening or a data file that has a default application association). You can also copy or move the selected file, send it to the Recycle Bin, or shred it. There are rename options. You can change the timestamp or attributes, look at the file's properties, add or edit a comment, or create a shortcut on the Desktop or the Quick Launch area.
- Folder Menu: Need to see the folder tree? A single click provides it and displaying the tree for my music directory that contains more than 30,000 files took less than 30 seconds. You can also move forward or back through the directory structure or even browse a network folder.
- Edit Menu: As expected, here is where you'll find copy, cut, and paste but there's a lot more, including "advanced selection", "advanced deselection", the ability to select all files with the same name (regardless of extension) and all files with the same extension (regardless of name). There's also a "find" option to help you locate files.
- View Menu: This is the menu that controls the user interface. You can change the language or modify the overall look with one of three included skins. You can create a left column for folders, change to a single-folder view, show or hide various program features, view or hide buttons for all system drives, and even create a new tab that subdivides the left or right sections. There are also sorting and display options for the various columns.
- System Menu: This is the menu that gives you immediate access to the key folders (Desktop, Documents, Pictures, Music, Videos, and Favorites) as well as to the Control Panel, the Add/Remove Programs section of the Control Panel, the Recycle Bin, the Temp folder, and even the Command Line.
- Archive Menu: These items are designed to help you work with zip files and other compressed files.
- Network Menu: Nexus File even includes and FTP client that allows you to upload and download files to any site that has an FTP server.
- Tools Menu: Here you can view or edit a text file, compare folders, and establish program defaults.
Additional features and functions exist. You'll find them when you download and install Nexus File.

 If Nexus File Had a Help Menu, It Would Earn 5 Cats
If Nexus File Had a Help Menu, It Would Earn 5 Cats
Four cats is a very solid rating and I'm torn between saying 5 cats because of the enormous range of functions that the Windows Explorer replacement provides and saying 4 cats because some users won't be able to make full use of the program without the help file. If you ever encounter the limitations of the Windows Explorer, do yourself a favor and download Nexus File.
For more information, visit the Nexus website.
Public Computers Are Like Public Bathrooms Only Worse
You're on the road and without a computer, smart phone, or any other device that you can use for Internet access and now you need to access the Internet. You locate an Internet cafe or a library and hustle inside. Now what?
Consider these points: You don't know what kind of security software is installed on this computer. You don't know who used it before you did. You don't know what that person used the computer for or what sites that person might have visited. Does it contain key logger software? What information will you leave behind?
These are all valid questions and they're things that you should think about before using a public computer.
Protect Your Password
Probably the most serious threat would be the presence of a key logger on the public system. Key loggers monitor everything typed on the keyboard and can easily capture user names and password when the user types them. This information is then sent off to someone who will try to use the credentials to empty your bank account or make purchases using you identity.
 A walking advertisement for an Internet café in New York City.
A walking advertisement for an Internet café in New York City.
Photo by
Carl MiKoy. (Creative Commons)
Key loggers are hard to find and, if a hardware key logger has been plugged in, the only way you'll find it is by examining the computer. If you can't avoid making sensitive connections from a public computer, you can at least protect your user name and password. The process is both simple and foolproof.
The key logger can see only what you type. If you copy and paste characters, the key logger will see only the copy and paste operations, not the contents of the buffer. So open an application such as Notepad, type all the upper case letters, all the lower case letters, and any other characters used in your user name and password. Do not type the user name and password, though, because the key logger will record them.
When you need to enter your user name, copy the characters individually from Notepad and paste them into the login dialog.
Keep your online session short and be aware that some spyware can capture periodic screen shots. If the site displays sensitive information on screen, beware.
 An Internet café in India.
An Internet café in India.
Photo by
Mike Cogh. (Creative Commons)
Be sure not to allow the browser to save your user name or password.
The browser will maintain a record of your browsing history, though, and you'll probably want to obliterate that before you leave. Even if the browser has a "private browsing" feature, it's still a good idea to clear the browser's cache and browsing history when you're finished.
Chrome, Firefox, and Internet Explorer all recognize Ctrl+Shift+Del to open the History Deletion dialog. Each browser gives the dialog a different name and the process, once you've opened the dialog, varies among browsers. Just read the instructions and specify that you want to clear ALL history.
And then shut down the browser. You don't have to turn off the computer but it is important to exit the browser. If you don't, the next person who uses the computer can use the Back button to see where you went and, if you neglected to log out, that person could back into a live session that would provide access to private information.
The safest option, of course, is not to use a public computer or, if you must use a public computer, to avoid using it for any activity that involves personally identifiable information (banks, online shopping, and even business or personal e-mail).
If you do need to use the public computer for any of these types of activities, it's a very good idea to change your password when you return to your home or office.
The best defense is a great defense.
Short Circuits
Unlimited Plans That Are Limited
What does "unlimited" mean to you? "Un" is a prefix that negates whatever follows. "Unfriendly" means "not a friend". "Unethical" means a shortage of ethics. "Unhappy" indicates a shortage of joy. Unhappy describes a lot of AT&T customers who felt that the company's "unlimited" data plan with limits was both unfriendly and unethical. AT&T says it will modify its "unlimited" plan -- to be a little less unfriendly.
It's worth noting that AT&T doesn't offer "unlimited" plans any more but about 17 million subscribers have been allowed to keep the "unlimited" plans that they had signed up for.
- Here's what "unlimited" used to mean to AT&T: Anyone who was in the top 5% of data users during a given month and in a given area would see their service speeds throttled back.
- Here's what "unlimited" now means to AT&T: If you use more than 3 gigabytes of your "unlimited" data, limits kick in and throttle back your connection speed.
- Here's what "unlimited" means to most people who speak English: un·lim·it·ed • Adjective • 1. Having no restrictions or controls: an unlimited travel ticket. 2. Having or seeming to have no boundaries; infinite: an unlimited horizon. 3. Without qualification or exception; absolute: unlimited self-confidence. SOURCE: American Heritage Dictionary. Only a US corporation, considered by the Supreme Court to be "a person", could create a definition of an unlimited plan with limits and do so with a straight face.
To quote AT&T: "Our unlimited plan customers have told us they want more clarity around how the program works and what they can expect." Maybe they could just make the plan match its name.
An Iphone user won an $850 claim in a California when the judge agreed that an "unlimited" service shouldn't suffer intentional slowdowns by the provider. AT&T says that it will appeal the verdict.
Anonymous Members Arrested
The group known as Anonymous likes to deface websites, break in to sites with lax security and steal information, and otherwise engage in activities that some people might consider to be less than totally above-board and helpful. Now 25 suspected members of the group have been arrested in Europe and South America.
Four of the 25 people arrested are suspects in attacks on Spanish political party websites according to the Spanish police. They are accused of defacing websites, carrying out denial-of-service attacks, and placing online information about police assigned to the royal palace and the premier’s office.
Anonymous has no structure, no leaders, no managers. Think of a hydra without any centralized command and control. Because of the organization (or lack of it), the arrests will probably have little effect on the group.
Although Anonymous originated in the US, it has become increasingly involved in global actions and, as police agencies have targeted the organization, Anonymous has targeted police. Recently, Anonymous members tapped a conference call between the FBI, Scotland Yard, and other worldwide police agencies as they discussed their investigations of Anonymous.



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
