There's Danger in that Free Wi-Fi Hotspot
As handy as free Wi-Fi hotspots are, they're dangerous unless you're prepared. Being prepared means encrypting the connection and that's not something that most free systems (or even some paid systems) will do. The fix is relatively easy and the cost is low.
Here's the problem: When you connect to a public Wi-Fi hotspot, everything you send and receive is "in the clear", meaning that it's not encrypted and that anyone who has a packet sniffer installed on a nearby computer can see everything you're doing. Packet sniffers are commonly used by network engineers to diagnose network problems so they're easy to find and some are free.
If I were a crook, I might park myself regularly in a large airport and harvest signals. And if you're in an airport that provides only paid-access Wi-Fi, you'll probably also see some apparently free and unsecured networks. Thinking you just beat the airport out of its absurdly high fee, you connect to one of the free hot-spots. Later, while you're on a plane at 35,000 feet, the operator of the phony hot-spot is using your credit card information to buy a new computer or to raid your bank account.
But even if you don't fall for that trick, your information can still be pulled out of the air unless you're careful.
Being Careful
Start by using only the officially provided hot-spot. The provider of the service should post signs with the network ID (SSID) and that's the only network you should connect to. If the sign says the SSID is "BigAirport", be careful not to connect to "Airport" or "BigAerport" or "BigAir". Those would all be phonies hoping to steal your data.
Turn off any feature that automatically connects to "any available network". How this is done varies by operating system and computer so check with the manufacturer.
If you don't need Wi-Fi access, turn off the wireless subsystem. Besides making your computer invisible to all the bad guys, this will also increase the computer's battery life. Some computers use a special key combination to toggle Wi-Fi on and off (usually a Function key in conjunction with the Fn key) while others have a physical switch on the computer's case.
Turn off shared files and folders. If, despite all your precautions, you connect to a rogue system (or it connects to you), this will protect the files on the computer. This is another feature that varies from one operating system to another.
Install virtual private network (VPN) software. Some VPN applications are free but if you travel a lot or use Wi-Fi hotspots regularly, features available from paid services will probably be worth the small monthly fee. (More about VPN in a moment.)
Keep your antivirus and antimalware applications up to date and when you get to your hotel room or when you return home from a trip, it doesn't hurt to run the scan function.
The danger is sufficient that the Federal Trade Commission, the Justice Department, the Department of Homeland Security, and the Commerce Department set up a special website early this year to warn people: The OnGuardOnline.gov. The site says users on public Wi-Fi hotspots should use only sites that are fully encrypted. Encrypted sites will begin with https instead of http and will display an icon that suggests security—often a lock or similar symbol.
Installing a Virtual Private Network
Using a VPN application will make all connections secure by encrypting the transmission and several options are available. There's no shortage of choices.
- ProXPN is my current choice. (Windows, Mac)
There's a free option that's limited to 300Kbps. Compared to dial-up, that's a lot, but compared to broadband, it's not. For $10 per month you'll obtain a far faster connection and additional functional capabilities. - SecurityKiss has similar offerings. (Windows, Mac, Linux)
The free service is functional but limited. For about 4€ per month, you'll have faster access and more features. - Hotspot Shield failed for me. (Windows, Mac)
The application didn't want to work with Windows 7 although it's certified for Windows 7. The free version has limits but you can avoid them by spending a few dollars per month. - ExpatShield is limited. (Windows only)
If you select this one, you'll see ads displayed in your browser. This isn't unusual for free VPN options. - Loki VPN Client (Windows only)
Both free and paid services are limited in terms of bandwidth and transfer. For $6 you get 30 days worth of service (128Kbit bandwidth with a maximum download size of 100MB.)
Those are just some of the options available to you. If you're a casual user, one of the free plans should be sufficient but if you travel a lot or use local Wi-Fi hotspots frequently, you'll probably consider one of the paid services to be a wise investment.
Itunes, Begone! CopyTrans, Welcome!
After a year of trying to deal with Apple's severely defective and deficient Itunes application, I have finally rid myself of it and once again I can update the music on my Ipod Touch and Ipod Nano. The Nano goes to the gym with me. The Touch travels in my briefcase and is always available at the office. Neither has worked properly for the past year because of Itunes.
Trouble began when I updated Windows to a 64-bit operating system. Whenever I attached the Nano to the computer, Itunes would start and then crash. After the crash, the Nano would be empty. Its little screen displayed a forlorn "No Music" message instead of listing the 1500 selections that had been there. To restore the music, I used Winamp.
The Touch also caused Itunes to crash but at least Itunes left the music and the apps I had purchased on the device. But I couldn't add music, update apps, or download and install any software upgrades for the Touch. Apple's software engineers designed the Touch so that Winamp couldn't touch it.
Then I Found CopyTrans
CopyTrans Manager is a free application that allows users add music to Apple devices (including the Iphone and Ipad). So if you're tired of dealing with Apple's bloatware there is finally an option you can choose.
 CopyTrans offers a variety of other applications (not free) that can be used for other management tasks. Currently I'm not using any of them but right now all I need is a way to change the music files on these portable devices until they expire. When that happens, I won't be replacing them with Apple hardware.
CopyTrans offers a variety of other applications (not free) that can be used for other management tasks. Currently I'm not using any of them but right now all I need is a way to change the music files on these portable devices until they expire. When that happens, I won't be replacing them with Apple hardware.
The system is easy to use. Just start the CopyTrans Control Center, which then provides an option for settings and a link to the CopyTrans Manager.
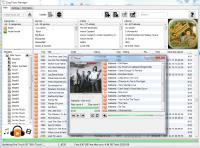 The Manager shows what's on the Ipod and offers the ability to delete existing music from the device, add music to the device, or play selections that are on the device. This is handy because CopyTrans has no built-in player that works with the music on the computer. For that you can use Winamp.
The Manager shows what's on the Ipod and offers the ability to delete existing music from the device, add music to the device, or play selections that are on the device. This is handy because CopyTrans has no built-in player that works with the music on the computer. For that you can use Winamp.
The screen you see here shows the payer (She and I by Alabama is playing) and I'm uploading about 2GB of new selections to the Touch.
 When it comes to playing music from the music library, Winamp is my choice. The Itunes interface is better, but the Itunes annoyances are so severe that the only rational choice, from my point of view, is Winamp.
When it comes to playing music from the music library, Winamp is my choice. The Itunes interface is better, but the Itunes annoyances are so severe that the only rational choice, from my point of view, is Winamp.

 What a Relief! I Can Finally Use My Ipod Again.
What a Relief! I Can Finally Use My Ipod Again.
Itunes is not a particularly beloved application, even among the Mac faithful. Many Mac users refer to Itunes as "bloatware" and disdain the application for its propensity to lose track of music libraries, crash, and otherwise annoy. That became clear in the past year during which I tried to find a solution to the problem by spending time on Itunes discussion forums. So it's both a delight and a relief to find CopyTrans.
For more information, visit the CopyTrans website.
Flying High: The Bat out of Moldova
For more years than I'd like to claim, I've been using The Bat as my primary e-mail program. It's true that I have to use Microsoft Outlook at the office and in an office environment Outlook's calendaring capabilities are a plus; but in any setting other than the office, The Bat wins—wings down. Version 5.0 is even better.
The Bat's developers take an unusual approach: When they release a new version, the previous version's registration key continues to work until they reach version X.1. When I was preparing this review, the version number was 5.0.16 so my version 4 key continues to work and it will continue to work until the developers decide that they've squished enough bugs to name the version 5.1.
The Bat is popular in Europe but has only a small following in the US. Although I understand why (its name is Microsoft), it still strikes me as illogical for people to use an application such as Outlook, Thunderbird, or Microsoft Mail when something much better is available. I give office workers a special dispensation for two reasons:
- Their IT department probably has mandated Outlook.
- In an office environment, Outlook's included calendar, scheduling, and task management options give it advantages no other application has.
A Better Bat Becomes Better Still
Simply put, The Bat is the most flexible e-mail application you'll find. Every time I ask the developers for a new feature, they tell me that they already thought of it and provide the instructions needed to accomplish my goal.
Example: I use a plug-in called Antispam Sniper to segregate the hundreds of spam messages I receive daily. The messages all go to a folder called "Junk". I found that when I deleted messages from that folder they went to the "Trash" folder and recommended to the developers that they make it possible to delete messages from "Junk" without sending them to "Trash" where they must again be deleted.
Александр Петрари replied: "There is an easy way out: open the properties of the "Junk mail" folder and go to the "Deletion" item on the left. Then enable "Use folder-specific deletion settings" and finally enable "Normal deletion -> Mark as deleted, do not use the Trash folder". That is all :)" Problem solved. Everything should be this easy! Every time I want a new feature, it seems that RIT has already thought of it and all that I need are instructions on where to find it.
So on one level I don't understand why this application has only a niche following in the United States. But when I consider that using the application's immense feature base requires a bit of work to learn now the application really works, I do understand. Many computer users are unwilling to expend the effort even though The Bat would make it possible for them to perform actions they would like to perform.
What's new in version 5:
- Developers have completely reworked the program's intercommunication mechanisms. Although The Bat has supported the IMAP protocol, the changes improve IMAP support to make the program more stable and secure.
- Folder information panels are new in version 5 and these display the dynamically updated information of the selected mail folders. Information displayed is interactive so the user can make modifications from this screen such as viewing the account log, editing account templates, and changing the intervals at which the application checks for new messages.
- Display of images in HTML-coded e-mail has always been a security issue and some programs (Outlook, for example) simply block all images. This is what The Bat used to do. In version 4, it became possible to display images on a message-by-message basis. Now users can specify rules based on sender, recipient, folder, or regular expressions to determine when images are displayed.
- Version 5 of The Bat uses Intel's Advanced Encryption Standard (AES) Instructions Set to improve the speed of AES algorithm used in TLS and S/MIME communications.
Catching The Bat in Flight
The Bat is a complicated, complex, feature-rich program that cannot be explained quickly or easily. Despite the fact that I have been using this program for a decade, I still regularly find that it has features I didn't know existed. The ability, as I noted earlier, to control deletions on a per-account basis has been around for a long time. Александр Петрари kindly didn't call that to my attention when he explained how to accomplish what I wanted to do but I know that account-specific settings go back several versions.
So instead of trying to tell you everything there is to know about The Bat, I'll just mention some of the features that are important to me. With this application, my general assumption is this: Whenever I think of something I would like The Bat to do, the program probably already does it.
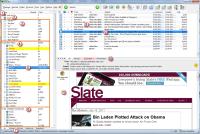 This is the primary view as I use it. The message preview pane can be hidden and messages may be organized in many ways (or even threaded for discussion lists). This is the view I prefer.
This is the primary view as I use it. The message preview pane can be hidden and messages may be organized in many ways (or even threaded for discussion lists). This is the view I prefer.
- A spam add-on created the Junk Mail folder and places any messages it considers to be spam here.
- Trash is the folder common to most e-mail applications where messages go before they are deleted.
- These are virtual folders. Regardless of what e-mail address these people send messages to, they will be caught and referenced here. The folders are not real (which is to say that messages are not duplicated). When I select one of these faux folders I see messages from many folders.
- Here is my main account with some of the sorting folders that I use to keep things in order. Incoming mail is reviewed and then moved to one of the folders shown here.
- The folder highlighted in blue is the one that I'm currently viewing.
- Here's the TechByter folder and its subfolders.
- At the bottom of the list I can select All, Unread, Virtual, Addresses, or Important for different views of all messages in the various mailboxes.
- This is the list of messages in the current folder.
- The blue highlight shows the message I am currently viewing in the preview window at the bottom of the screen.
- The selectors here are similar to those at the bottom of the accounts and folders tree except that these apply only to the current folder.
- This is the message in preview mode, which is what I generally use. I can double-click a message to see it in its own independent window, but my preference is to read it this way most of the time.
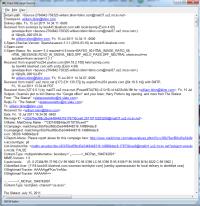 When you view an e-mail message, you see only what the application wants to show you. Most programs allow you to see some or all of the header information but The Bat makes it possible to view the entire e-mail data stream.
When you view an e-mail message, you see only what the application wants to show you. Most programs allow you to see some or all of the header information but The Bat makes it possible to view the entire e-mail data stream.
This view makes it possible to see all parts of a multi-part message exactly as it was transmitted along with the full routing headers. This view often answers questions about the message's origin and its legitimacy. Unfortunately, The Bat is the only e-mail program I know that offers this option.
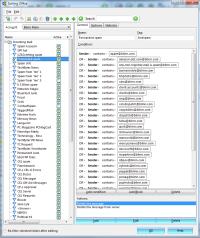 The Bat's filtering is more powerful than anything I've seen in any other e-mail client and this is one of the primary reasons that I use (and strongly recommend) The Bat.
The Bat's filtering is more powerful than anything I've seen in any other e-mail client and this is one of the primary reasons that I use (and strongly recommend) The Bat.
Learning how to create a filter may seem daunting but really it's not particularly difficult. All you need to do is determine what conditions trigger the filter (address, message contents, etc) and what the filter should do with the message (move it, delete it, etc) when the conditions are met.
 And finally, there's the Options section.
And finally, there's the Options section.
If you want an application that is flexible, one that allows you to define how things are supposed to work, The Bat is the only e-mail application you should consider.
This is probably not the e-mail application for everyone but if you want to have control, it's the one for you.

 The Bat Has Been My Choice Since 2000. Should It Be Yours?
The Bat Has Been My Choice Since 2000. Should It Be Yours?
RIT Labs allows users to download and try The Bat before buying it but the upgrade policy is unusual. Those who hold version 4 licenses for The Bat may download and use version 5 without charge. When the version reaches 5.1, version 4 licenses will no longer work. That's a clever way to entice users to upgrade and to gain a lot of real-world testing.
For more information, visit the RIT Labs website.
Short Circuits
Linux 3—Big Deal or Not?
Sometimes it's hard to tell what's going on in the Linux world. The Linux kernel is advancing from version 2 to version 3. Some people say it's a big deal. Mister Linux (Linus Torvalds) says it's not.
The Linux kernel will soon move from version 2.6, the version Linux users have been using for several years, to version 3.0. The Linux community isn't saying much about it. Years ago, when the kernel went from version 1.x to 2.0, it was a big event. Why is this not such a big deal?
But Ubuntu is already at version 11.04. What's all this about version 3?
Ubuntu's numbering system is (shall we say) "unique". It consists of the final 2 digits of the year (2011) and the month (04) that it was released. This number has nothing at all to do with the Linux kernel.
If you want to update the kernel on your Ubuntu system prior to the next Ubuntu release, you'll find instructions on sites such as Ubuntu Guide.
As for whether it's a big deal or not, maybe it depends on what your definition of "a big deal" is.
Different Sound This Week?
 You may notice a somewhat different sound this week on the podcast. It's the result of a new microphone, a ribbon microphone. The microphone I've used since the beginning is an AKG C1000S, which is a great location microphone. It's rugged. It cancels noise in rooms where a lot of people are talking. In other words, it's great for on-scene reporting.
You may notice a somewhat different sound this week on the podcast. It's the result of a new microphone, a ribbon microphone. The microphone I've used since the beginning is an AKG C1000S, which is a great location microphone. It's rugged. It cancels noise in rooms where a lot of people are talking. In other words, it's great for on-scene reporting.
Studio work calls for something with a bit better sound and this week I used a new Cascade Fat Head ribbon mic.
Ribbon microphones are well known for producing rich sound but they are extremely fragile. When not in use, they should be covered or (better yet) stored in the padded box they arrived in. For now, I'm storing it on a mic stand but with the included cloth cover.
You should hear a difference between the podcast itself (on the new mic) and the open and close (on the old mic).
By the way, "fat head" should not in any way be construed to be descriptive of the narrator of the podcast. I've loved the sound of ribbon microphones ever since I encountered an antique RCA 44BX at WTVN in the 1960s. The RCA 44-series microphones date back to the 1930s.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
