As usual, there will be no TechByter Worldwide Thanksgiving week. So in addition to other things you may be thankful for, there's some extra peace and quiet from here.
Passwords and Spam
Has your e-mail account been used by a spammer yet? No, I don't mean just having mail sent so that it claims to come from your address but actually using your e-mail account to send spam. If you routinely re-use passwords and this hasn't happened yet, now would be a good time to change passwords if you want to prevent it.
Within the past 30 days, I have received spams that actually came from accounts of people I know or people who have my e-mail address in their contact list. In many cases, these spams address me by name because the spammer was able to obtain this information from the victim's contact list.
 Some of the messages have served poisoned links. Others have been standard spams. I have discarded all of the messages without following any of the links except for those that I opened with a specialized tool that doesn't allow the site to take over my computer.
Some of the messages have served poisoned links. Others have been standard spams. I have discarded all of the messages without following any of the links except for those that I opened with a specialized tool that doesn't allow the site to take over my computer.
Passwords can be obtained when ...
- The victim uses a simple word that's easily guessed. By "easily guessed", I mean any word that's in a dictionary. You already know that passwords such as "123" or "abc" or "password" are stupid, but so are passwords such as "pusillanimous", "mustard", and "letmein".
- The victim logs on via an unencrypted Wi-Fi link to an account and someone nearby plucks the password out of the air. I wrote about a way to avoid that in September.
- The victim uses the same password at multiple sites. As soon as any one location is compromised (and some have exceedingly lax security) the crook has thousands or millions of passwords and user names that will probably work at other sites. For an explanation of how this works, see this XKCD cartoon.
If you have a favorite password that you use for multiple sites, I encourage you to change it. This is something you should do now, not later.
It's possible to use a favorite password in combination with a prefix, infix, or suffix that you modify from site to site and this produces reasonably strong and secure passwords. Let's say you create a base password "fizzy8beans". You'll use this at various sites, but with a combination of other characters. When you register for a site, you would always use the same base password and combine it with a set-length prefix, suffix, or infix that's always placed at the same location.
If Example.com and TechByter.com required passwords, here's what yours would be:
| Example.com | TechByter.com | |
|---|---|---|
| Option 1 | EXfizzy8beans | TEfizzy8beans |
| Option 2 | fizzyEX8beans | fizzyTE8beans |
| Option 3 | fizzy8EXbeans | fizzy8TEbeans |
| Option 4 | fizzy8beansEX | fizzy8beansTE |
You might use 2 additional characters as shown here, 3, 4, or more. The key is to make the pattern something that will allow you to reconstruct the password from something you see on the page (in this case, I use the domain name).
Other possible patterns:
- 2nd and 3rd characters of the domain name. (XA and EC)
- 1st character of the domain and 1st character of the top-level domain. (XC and TC)
- Last 3 letters before the top-level domain. (PLE and TER)
Although this process will create reasonably strong passwords, passwords for accounts that you consider important (banks, for example) should be both strong and unique. No password should be used for multiple sites.
Please: For your own benefit, don't reuse passwords!
Adobe's InDesign/InCopy Combo Speeds Publications
If you've ever wondered how the creators of Washingtonian Magazine, Business Week, Lenswork, or Fitness Magazine put their publications together, the answer is InDesign and InCopy from Adobe. These applications combine to speed the process of creating newspapers, magazines, brochures, and catalogs because many people can work on a publication simultaneously. And although you might think of this combination as something that only huge corporations would use, it can help in any situation where multiple people have to touch a publication before it goes to the printer.
 Even smaller companies will find that they can get things done faster if they take the time to learn some new tricks. The overarching goal of the InDesign/InCopy workflow is to free designers from having to interpret marked-up page proofs and to allow editors to see instantly both how their words look on the finished page and how they fit the finished page.
Even smaller companies will find that they can get things done faster if they take the time to learn some new tricks. The overarching goal of the InDesign/InCopy workflow is to free designers from having to interpret marked-up page proofs and to allow editors to see instantly both how their words look on the finished page and how they fit the finished page.
In an earlier time, creating something as simple as a newsletter might require several iterations involving writers, editors, typesetters, and proofreaders. The writer would create an article and an editor would modify it. Then the typesetter created a galley proof that allowed the designer to determine whether the copy was too long or too short; in addition, typesetters invariably found errors that the editor had missed and corrected them but created errors of their own.
After several rounds, the copy would be good enough to go to the designer to be pasted up on boards. Any errors found after this point required an X-Acto knife to correct. When the boards were ready, they were delivered to the printer, who made plates.
Many of those steps have been eliminated by electronic typesetting (PageMaker, Ventura Publisher, Quark XPress, Frame, and InDesign). The addition of InCopy, which has been around for several years but is fine-tuned in the CS5 version of Adobe's Creative Suite, advances the entire process.
How InCopy Changes the Workflow
The following 3 illustrations are from one of the first few chapters of Anne Marie Concepcion's Introduction to InCopy at Lynda.com. Adding InCopy to the production process may initially be a challenge because change is always difficult and InCopy makes fundamental changes to the way things are done.
Click any of the smaller images for a full-size view.
 In a traditional workflow, a publication designer is responsible for the layout of the brochure, newspaper, newsletter, or magazine. When the initial layout has been set, printed copies or PDFs are sent to authors, editors, copywriters. These people provide text for the pages. The designer adds the text and sends another round of pages to editors, who mark up the copy and send it back. Several iterations of this process ensue and others are brought into the mix as needed, including fact checkers and proof readers. Eventually the publication is ready for the press.
In a traditional workflow, a publication designer is responsible for the layout of the brochure, newspaper, newsletter, or magazine. When the initial layout has been set, printed copies or PDFs are sent to authors, editors, copywriters. These people provide text for the pages. The designer adds the text and sends another round of pages to editors, who mark up the copy and send it back. Several iterations of this process ensue and others are brought into the mix as needed, including fact checkers and proof readers. Eventually the publication is ready for the press.
InCopy can be used in two primary ways. There are more similarities than differences between the two methods and either will substantially streamline a publication's workflow.
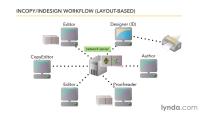 A designer (using InDesign) prepares a publication document on a server. All of the other participants use InCopy to edit the file simultaneously on the server. One InDesign user and any number of InCopy users can have a publication open at the same time but a check-out/check-in mechanism ensures that only one person may be working on any given "story" at a time. To InDesign and InCopy, a story might be something as large as a chapter of a book or as small as a caption for an image.
A designer (using InDesign) prepares a publication document on a server. All of the other participants use InCopy to edit the file simultaneously on the server. One InDesign user and any number of InCopy users can have a publication open at the same time but a check-out/check-in mechanism ensures that only one person may be working on any given "story" at a time. To InDesign and InCopy, a story might be something as large as a chapter of a book or as small as a caption for an image.
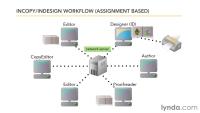 The alternate method, and the one preferred by Adobe, is the "assignment" model. Stories are assigned to individual users, which gives the designer slightly more control over which associates are working with any given story. This is the method that is required if all of the users don't have access to the server where the publication is stored. People who may be working from home can receive stories by e-mail or other means, work on them, and then return them to the designer to be checked in.
The alternate method, and the one preferred by Adobe, is the "assignment" model. Stories are assigned to individual users, which gives the designer slightly more control over which associates are working with any given story. This is the method that is required if all of the users don't have access to the server where the publication is stored. People who may be working from home can receive stories by e-mail or other means, work on them, and then return them to the designer to be checked in.
According to Anne Marie Concepcion, who works with companies that are converting from older systems to InDesign and InCopy, the production process usually takes 50% to 80% less time—start to finish—when the new system has been fully implemented.
A Quick Tour of the InDesign–InCopy Combo
To illustrate how the process works, I created a directory on a desktop computer to play the part of the InDesign server. I then set up a demonstration publication that was provided by Adobe. After installing InCopy on a notebook computer, I connected via the network to the "server" directory on the desktop.
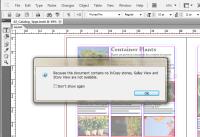 Because I had not yet prepared the document in InDesign for use with InCopy, InCopy could open the publication but no stories were available for editing.
Because I had not yet prepared the document in InDesign for use with InCopy, InCopy could open the publication but no stories were available for editing.
Part of the setup process is creating a user name for the InDesign user and also for each InCopy user.
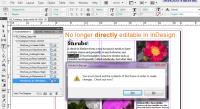 Having prepared the document in InDesign for use by InCopy editors, I found that I could no longer directly edit stories in the publication. That's because anyone who edits a story must first check it out so that only one person can work on it at any given time.
Having prepared the document in InDesign for use by InCopy editors, I found that I could no longer directly edit stories in the publication. That's because anyone who edits a story must first check it out so that only one person can work on it at any given time.
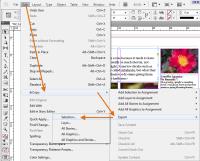 As the designer, I wanted to make the stories available to the editors who are working on the project. Stories may be prepared one at a time (as shown here) or multiple stories (or all stories in the publication) may be prepared simultaneously.
As the designer, I wanted to make the stories available to the editors who are working on the project. Stories may be prepared one at a time (as shown here) or multiple stories (or all stories in the publication) may be prepared simultaneously.
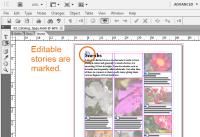 When stories have been prepared to be edited in InCopy, the editor will see a symbol at the top of each editable story.
When stories have been prepared to be edited in InCopy, the editor will see a symbol at the top of each editable story.
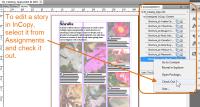 To edit a story, the editor simply selects it from a list of stories that are eligible for editing and checks it out.
To edit a story, the editor simply selects it from a list of stories that are eligible for editing and checks it out.
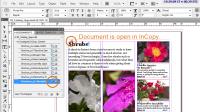 Back at the ranch (which is to say in InDesign), the designer sees that an editor has checked the story out.
Back at the ranch (which is to say in InDesign), the designer sees that an editor has checked the story out.
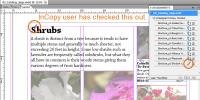 The InCopy user sees a pencil icon that indicates this story is currently open for editing on this computer.
The InCopy user sees a pencil icon that indicates this story is currently open for editing on this computer.
The editor can work in Design View, which is particularly helpful for fitting copy to the available space. This capability alone is probably responsible for a considerable part of the time savings enjoyed by InDesign/InCopy users.
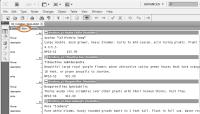 InCopy has 2 alternate views. One is the Story View, which is somewhat like an old-fashioned word processor with fixed-width type. The clear display is ideal when the editor is reviewing spelling and grammar.
InCopy has 2 alternate views. One is the Story View, which is somewhat like an old-fashioned word processor with fixed-width type. The clear display is ideal when the editor is reviewing spelling and grammar.
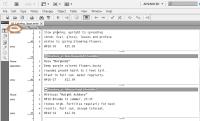 Between Story View and Design View is an option called Galley View. It looks like the Story View, but it accurately represents how lines break and where hyphens will be placed.
Between Story View and Design View is an option called Galley View. It looks like the Story View, but it accurately represents how lines break and where hyphens will be placed.
Most InCopy users switch from one view to another as their needs change.
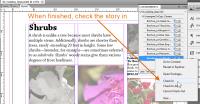 When the InCopy user has finished with the story, it needs to be checked in. This is equivalent to saving the document in InDesign.
When the InCopy user has finished with the story, it needs to be checked in. This is equivalent to saving the document in InDesign.
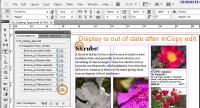 The designer's screen will display new icons to indicate that the editor's work is complete and that the InDesign view is now "out of date".
The designer's screen will display new icons to indicate that the editor's work is complete and that the InDesign view is now "out of date".
The designer simply needs to refresh the publication.
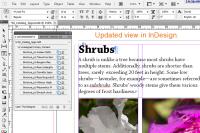 Following the refresh function, the designer can see the changes that the editor made.
Following the refresh function, the designer can see the changes that the editor made.
For extra credit, identify the minor editing error in the illustration at the right. (Hint: It's on the 3rd line.)
 Bottom Line: InCopy is the new way to say "freedom".
Bottom Line: InCopy is the new way to say "freedom".
Designers want to spend time working on the design, not being typists who must interpret arcane editing marks from editors. Editors would prefer to make changes to publications without having to explain what changes need to be made. The InDesign/InCopy workflow frees both designers and editors to do what they want to do.
For more information, visit the Adobe InCopy website.
Short Circuits
Still Paying for Cable TV?
Yeah, so am I, but I'm not sure why. I really don't watch television although my wife does, so I guess that's one good reason to keep it running. When I watch a TV series, I binge-watch. For example, I heard an interview on NPR's Fresh Air with Victor Garber, who portrayed Jack Bristow on the program Alias. He made the series sound interesting, so I ordered the DVDs from Netflix and watched the entire series in a couple of weeks.
The advantage is that I don't lose the thread from week to week or during the summer. Everything is compressed. I've done this with several programs because I really don't like wasting my time sitting in front of the television while it spews advertisements.
Netflix (DVD and streaming video), Hulu, Apple, VeriFone, Oodle and others are making it possible to enjoy more entertainment at a lower cost. At greatest risk, according to a recent research report, are "basic" cable subscribers. SNL Kagan says cable companies lost nearly three quarters of a million such subscribers in the third quarter of 2010.
Hulu launched its "Plus" service this week. For $8 per month, you have access to current programs from ABC, Fox, and NBC, along with some other options.
The overall outlook for cable TV would seem to be cloudy at best.
Be Careful What You Say Online
A Chinese woman will spend a year in a labor camp because she forwarded a satirical Twitter message that urged recipients to attack the Japanese pavilion at the Shanghai World Expo. Does this sound terrible? What about this: A medic who posted a disparaging comment about her boss on Facebook has been fired.
Dawnmarie Souza, a medic with American Medical Response, was fired after she posted a less-than-complementary comment about her supervisor on Facebook.
The ambulance company that Souza worked for fired her, but the National Labor Relations Board (NLRB) says that the company's action was unwarranted. This will eventually play out in court.
But getting back to China, Cheng Jianping was accused of "disturbing social order" because she forwarded a message from her fiancé that mocked those who held anti-Japanese rallies in several cities last month. Cheng added "Charge, angry youth" to the message she forwarded, ironically suggesting that protesters do more than just smash Japanese products.
As a result, Cheng will spend the next year in the Shibali River women's labor camp. Her finacé says that Cheng has begun a hunger strike in a bid to serve her sentence in a camp that's not so far from her home.
Microsoft Security Essentials or Norton Internet Security?
More than a year ago, I said that Norton Internet Security was the winner and at that time it was true. Since then Microsoft's operating-system-based security system has come a long way. I've always said that security should be a part of the operating system and that may be the case—if not now, then eventually.
When it comes to desktop computer operating systems, Microsoft owns the market. And Microsoft tends to expand into other areas, taking over functions that have been provided by smaller companies.
In the 1980s, I was a Symantec fan, but the company's bloatware made it impossible to use the its security applications. As of 2010, the Symantec offerings are very good—good enough that they're what I use on a daily basis.
But Microsoft is moving forward. The latest (free) anti-malware application is delivered via Microsoft Update and proves to be a workable application.
Now Microsoft Security Essentials (MSE) is becoming a threat to third-party providers such as Symantec, McAfee, and Trend Micro. MSE isn't (currently) the best security application available, but it might be "good enough". It's easy to use. It's essentially part of the operating system. You don't have to do anything special to use it. And it's "free".
I'm not yet quite ready to dump Symantec's products (still licensed for more than a year), but I can foresee a time when the provider of the operating system is also the provider of the security suite.


 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
