Giving Away Your Identity
 I love public Wi-Fi locations. My city provides Wi-Fi on the street (the main street; not my street) for free. I can also connect from the library or the community center. It's not city-wide Wi-Fi, but it's easily available nonetheless. "The City of Worthington's outdoor wireless network is free to users and is accessible along High Street between South Street and North Street and in both Worthington Libraries locations. The Wi-Fi network is provided by HarborLink Network and is supported through advertising and sponsorships." Using public Wi-Fi is also an outstanding way to give your e-mail address, login name, and password to unsavory characters lurking nearby. But there's an easy solution to that problem.
I love public Wi-Fi locations. My city provides Wi-Fi on the street (the main street; not my street) for free. I can also connect from the library or the community center. It's not city-wide Wi-Fi, but it's easily available nonetheless. "The City of Worthington's outdoor wireless network is free to users and is accessible along High Street between South Street and North Street and in both Worthington Libraries locations. The Wi-Fi network is provided by HarborLink Network and is supported through advertising and sponsorships." Using public Wi-Fi is also an outstanding way to give your e-mail address, login name, and password to unsavory characters lurking nearby. But there's an easy solution to that problem.
Worthington warns me that "the system is public, free, and not secure. If your e-mail is not encrypted, sending a note about a dinner meeting is fine; sending your accountant your Social Security number is not. Also, do not enter credit cards or other personal account information on Web sites. Your screen can be visible to passers-by. Surf sites appropriate for all eyes. Update your spyware and antivirus software. Just like with any connection, you can catch nasty bugs coming off the Internet. If you need additional security, please obtain independently."
Access points are located in both the Old Worthington Library and Northwest Library, as well as at the Griswold Senior Center and along the mast arms of the city's traffic signals. The access points create a wireless local area network and this is one of the advantages of living in an urban area where the government understands the importance of the Internet.
But ....
To avoid giving away your identity, you need to create a virtual private network (VPN) and if that sounds complex and confusing, it is. But it's not. If you use an application such as Hotspot Shield, your connections (wired and wireless) will be secure and you'll hardly notice any change. Well, except for the advertisements. Hotspot Shield works for both Windows and Mac operating systems, including Windows 7 and Apple's OS X Snow Leopard.
The problem with basic Wi-Fi is that everything is sent "in the clear". Anyone who's nearby and who has even the most basic understanding of network topology will be able to see everything your computer sends and receives.
A program such as Hotspot Shield will protect you by ensuring that all transactions are secured through secure HTTP and by making your identity invisible to third-party websites and ISPs. AnchorFree's Hotspot Shield keeps your Internet connection secure, private, and anonymous by creating a VPN between your computer and AnchorFree's Internet gateway.
Because all communications are encrypted, nobody can view the data sent from or received by your PC. The application runs on PCs with Windows 2000, Windows XP, Vista, or Windows 7 as well as Macs with any version of OS X from 10.4 or higher.
Free Solutions. Paid Solutions.
Hotspot Shield is adware, which means that by accepting the application for "free", you give the company permission to bombard you with ads: "9.1 Advertisements. AnchorFree may deliver third-party advertisements ('Advertisements') within the content of any web page accessed. Advertisements may be injected into the top of the page, inserted directly into the page content, or even displayed to overlay the page."
Hot Spot VPN doesn't have ads, but you'll pay $90 per year for it. If you're an infrequent user of hotspots, you'll probably be able to bear the advertisements. The most annoying feature is that some of the ads have music and sound. You'll also want to opt out of anything you're offered during the installation process. By default, the program will offer you a browser tool bar and will become your default search provider and home page. I also turned off the instant Hotspot Shield "privacy and security alerts" and an option to fix page-not-found errors.
 Although I wanted to test another free application for this report, iPIG WiFi Hotspot VPN Security, the provider's website was unable to respond when I tried to create an account
Although I wanted to test another free application for this report, iPIG WiFi Hotspot VPN Security, the provider's website was unable to respond when I tried to create an account
 According to the developers, "Unfortunately, commercial support for iPig is no longer available for new users/customers. But if you are a developer, you might be interested to know that the full iPig source code (including the iPig driver) is available at http://www.iopus.com/ipig/". So if you're a programmer who's itching to work on an interesting open-source project, this could be it.
According to the developers, "Unfortunately, commercial support for iPig is no longer available for new users/customers. But if you are a developer, you might be interested to know that the full iPig source code (including the iPig driver) is available at http://www.iopus.com/ipig/". So if you're a programmer who's itching to work on an interesting open-source project, this could be it.
Up and Running with Hotspot Shield
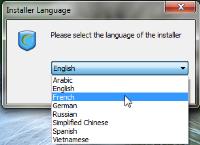 After downloading the installer, your first choice is the language to use. English is the default.
After downloading the installer, your first choice is the language to use. English is the default.
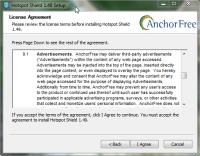 This is the section of the agreement that says you understand ads will be served on the Web pages you view.
This is the section of the agreement that says you understand ads will be served on the Web pages you view.
 Another panel provides "FREE Software Offers". Whenever you see this kind of offer during an installation, consider it a strong warning to sit up, read everything, and pay close attention to what's happening.
Another panel provides "FREE Software Offers". Whenever you see this kind of offer during an installation, consider it a strong warning to sit up, read everything, and pay close attention to what's happening.
 The toolbar will be selected by default. This is not a necessary component. If you install it, the toolbar probably will get in your way.
The toolbar will be selected by default. This is not a necessary component. If you install it, the toolbar probably will get in your way.
Deselect it even though it's shown as "recommended". Who's recommending it? The people with a fiscal interest, of course.
 Four other options will be selected by default, too. Deselect at least the first and second options.
Four other options will be selected by default, too. Deselect at least the first and second options.
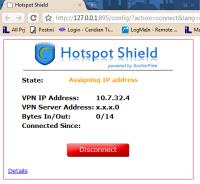 Following the installation, Hotspot Shield creates a secure connection and starts encrypting all traffic to or from your computer.
Following the installation, Hotspot Shield creates a secure connection and starts encrypting all traffic to or from your computer.
 Next, Hotspot shield will open your browser and start playing a commercial. In my case, it was a loud and annoying advertisement for a laundry product.
Next, Hotspot shield will open your browser and start playing a commercial. In my case, it was a loud and annoying advertisement for a laundry product.
The Wi-Fi Connection
If you've never used a Wi-Fi connection you might wonder how the process works. If you have a Windows 7 computer, a computer with many versions of Linux, or a Mac with any version of OS X released in the past 5 or 6 years, it's extremely easy. Earlier versions of Windows can be more challenging. The process is about the same for all operating systems, but various components may have different names.
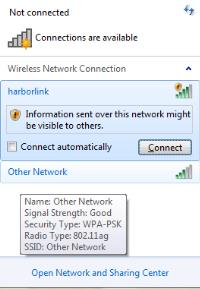 Start by making sure that Wi-Fi is turned on and then open the network connection wizard. I'm showing you the Worthington Wi-Fi as it appears in the main library. The computer sees the network and asks if I want to connect to it.
Start by making sure that Wi-Fi is turned on and then open the network connection wizard. I'm showing you the Worthington Wi-Fi as it appears in the main library. The computer sees the network and asks if I want to connect to it.
Next, you may see a message that tells you to open a browser. You'll need to do this even if all you plan to do is use an e-mail program that's not browser based.
Open the browser and try to navigate to any website. Which one doesn't matter. That will cause the Wi-Fi system to display the agreement page. This is where you agree that you understand the system is open and that anyone in the vicinity with a packet sniffer can see everything you're doing.
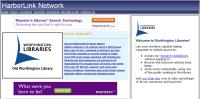 Once you've accepted the agreement, many Wi-Fi systems will then display the host's page. That's the case with the Worthington Public Library. At an airport, you might see the current list of arrivals and departures. That's the case at Port Columbus because the Wi-Fi is provided free by the airport.
Once you've accepted the agreement, many Wi-Fi systems will then display the host's page. That's the case with the Worthington Public Library. At an airport, you might see the current list of arrivals and departures. That's the case at Port Columbus because the Wi-Fi is provided free by the airport.
That's it. You're now connected, but there's one more step. Now's the time to fire up Hotspot Shield. An advertising page will open, but you can close it immediately if you wish. You'll see the same page later when you disconnect from Hotspot Shield.
 Bottom Line: Even though it's adware, Hotspot Shield is a good deal.
Bottom Line: Even though it's adware, Hotspot Shield is a good deal.
If I needed to use Wi-Fi hotspots frequently, Hotspot Shield's advertisements might be too in-my-face. In that case, $90 per year for a paid service would probably be money well spent. But for occasional use, you can't beat this service. Initially I had given Hotspot Shield a 3-cat ("solid") rating, but after using it in "in the wild", I decided that it really deserves a 4-cat rating. Hotspot Shield makes protection so easy that nobody should be without it.
For more information, visit the Hotspot Shield website.
Fun—Useful—Amusing—Silly
Wandering around the Internet continues to amuse me. It's like wandering through a library or book store, picking up a book at random, and reading a bit. When you depend on serendipity, there's no telling what you'll find. You might find some of the websites I've wandered into to be useful. Or silly. Or fun. Or ....
Old computer ads. Pictures of old computers. (Has it really been nearly 30 years since I purchased that Atari 800?) Facts. (The Apple Lisa [1983] was the first successful computer with a graphical user interface [GUI] and a mouse. It cost $10,000.) If you have any interest in computers you'll have trouble leaving this website. Absolutely fascinating.
The OTR.Network Library is a free resource for Old Time Radio (OTR) fans. You'll find more that 12,000 OTR shows available for instant listening. You'll need to have the Real player installed and you'll need to use a compatible browser. Abbot and Costello, The Bickersons, Jack Benny, The Lone Ranger, Jack Armstrong, and many more are all available for immediate listening. (Warning: This site requires Real Media, which will try to take over your computer. If you don't like Real Media, don't bother visiting this site.)
http://blogs.denverpost.com/captured/2010/07/26/captured-america-in-color-from-1939-1943/
Maybe you thought color photography wasn't available in the 1930s, but it was and some of the outstanding images from the era were captured on color slide film. The Denver Post provides a series of 70 images from the late 1930s and early 1940s. Many of the images show government-sponsored building projects.
http://www.sacbee.com/static/weblogs/photos/2010/04/shuttle-discoverys-15-day-miss.html
NASA makes a lot of images available and the NASA site is well worth the time you spend there, but this link leads to a review of one specific mission.
http://www.luciddreamguru.com/
Did you see the movie "Inception"? Dreams are the major plot device of this film and perhaps not too surprisingly, there are websites that discuss dreams. Lucid Dreaming is a particularly interesting concept and you're probably already familiar with it. A lucid dream is a dream where the person sleeping becomes conscious and aware that they are dreaming. Once this consciousness is achieved, the dreamer is able to engage and even manipulate the dream as they desire. Since the dream is a re-creation from the dreamer's own mind, the possibilities of what can be done in the dream is limited only by their own imagination. I haven't yet been able to manipulate my dreams, but I've been able to realize that I am dreaming.
http://www.collegehumor.com/video:1925309
Do you wonder why "news" is so absurd? Maybe this review of the Beatles will help you to understand.
http://www.boingboing.net/2010/07/14/improv-everywhere-st.html
I love Improv Everywhere. This link leads to an episode in which the group recreates a Darth Vader sequence with Princess Leia on the 6 train, but anything by Improv Everywhere is worth watching. If you realize that you're on a subway train with a bunch of these people and you get off the train, you may need to have your sense of humor adjusted.
The Windows Firewall is Blocking
What happens when your firewall notifies you that it has blocked something? My general response to messages of this sort has been to consider what application is asking for access. If the program is one that I've just launched and the request seems reasonable, I often tell the firewall to allow the connection. Sometimes I tell others to do the same thing, but that's not always the best advice. In fact, a case could be made that this is never the best advice.
A much better recommendation comes from Andrew Warren at Synaptics and I asked for his permission to share it with you.
Firewall warnings should be read carefully and responded to even more carefully. You absolutely should not click "Allow" just because you recognize the blocked application as one that you use.
Connections between your computer and the Internet can be made two ways: You can initiate the connection FROM your computer TO the Internet by typing an address into your Web browser, requesting e-mail from your ISP's mail server, signing in to an instant-message service, etc., or someone else can initiate the connection FROM the Internet TO your computer.
The connections that you initiate are "outgoing" connections; they're required by nearly all programs that access the Internet. The others are "incoming" connections; they're required only by "server" applications, which you're unlikely to be running on your machine.
Examples of programs that use outgoing connections:
- E-mail clients (Outlook, Eudora, Pegasus, etc.)
- Web browsers (Internet Explorer, Firefox, Opera, etc.)
- Instant message clients (AIM, Yahoo Messenger, MSN Messenger, etc.)
- Online games (WoW, etc.)
Examples of programs that use incoming connections:
- Web servers
- FTP servers
- Some remote-desktop programs
Windows Firewall (at least for XP) always allows all outgoing connections. The logic is that if a malicious program is on your PC, it could disable any firewall rule that would otherwise prevent it from calling out anyway, so there's little point in trying to stop it. The only connections blocked by Windows Firewall are incoming connections that are required by a only few types of programs, none of which you're likely to be running on a regular basis.
So here's how you figure out what to do when your firewall warns that it's blocking an incoming connection and asks whether you want to allow it:
- If you don't know for sure, don't click "allow"! If you find out later that you really should have allowed it, you can go into the Firewall Control Panel and allow it from there. You can't fix things so easily if you err in the other direction and allow your computer to be infected by a worm.
- Consider what you were doing just before the warning appeared. If you're expecting an incoming connection -- like, say, you're on the phone with a Microsoft customer-service rep who just said that he was going to access your desktop remotely to fix a problem -- and if the firewall warning looks consistent with that (i.e., Windows Firewall has blocked Remote Desktop Server from accepting connections), then it's probably safe to click "allow". If you've been quietly editing a Word doc for two hours and suddenly see Windows Firewall has blocked File Sharing Service from accepting connections from the Internet, click "Block".
- Pay attention to what's happening on your screen. If the firewall warning appears and the Internet program you were running freezes as though it's waiting for a connection, it MIGHT be OK to click "Allow". Since you're not sure, though, click "block". If the program you're using then fails and displays an error message such as Can't establish connection - check your firewall, then you should go to the Firewall Control Panel and allow that program to accept incoming connections. If, on the other hand, your program continues to work as expected even after you click "block" -- the way Skype will, for instance -- then leave the connection blocked.
- Do some research. You're not the only person running Windows; whatever your problem is, someone else has probably already experienced it, found an answer, and posted the answer somewhere. Google will have indexed that answer. Search for
skype "windows firewall"
You'll quickly see that Skype does not need to accept incoming connections. It does this to allow Skype to use your computer as a "supernode" to relay other people's conversations. If you don't want your PC to be used that way, block the connection and, depending on your version of Skype, also go into its settings and keep it from automatically adding itself to the Firewall Exception List.
Besides being much better advice than what I generally offer with regard to firewall warnings, Andrew's comments point up yet another reason to be suspicious of Skype. I have written before about some of Skype's default settings.
Consumer beware!
Short Circuits
Palo Alto Research Center Turns 40; Looks to the Future
A little more than a decade ago, I read Dealers of Lightning, a book by Michael Hiltzik about the Palo Alto Research Center (PARC). Now the center is 40 years old and hasn't been owned by Xerox since 2002. PARC invented the personal computer, the laptop computer, the laser printer (HP licensed the technology from PARC), and much of the Internet. Now it's specializing in solar power and other future technologies.
Xerox never managed to make much money on the inventions that flowed from PARC, but if Xerox hadn't funded the operation, things would be a lot different today.
Engineers at PARC gave Xerox know-how the company could have used to introduce the personal computer three years before IBM's PC. PARC is responsible for the mouse, responsible (by an indirect route) for Ethernet, and largely responsible for the graphical user interface. Both Apple and Microsoft stole the idea from PARC. It was the laser printer that made PARC financially viable because of its licensing deal with HP.
In the mid 1970s I wrote a research paper for a class at OSU. I talked about computers in homes, but my vision was of a desk-size device. About the same time, Alan Kay at PARC was trying to figure out how a computer might be placed in a container the size of a pizza box. In those days a cabinet with 64 KB of memory weighed 10 pounds or more, cost thousands of dollars, and required a locker-size cabinet for housing. I was looking just a few years into the future but these guys were seeing what might be possible in 1990.
Charles Geschke and John Warnock left PARC to be the co-founders of Adobe Systems. Gary Starkweather worked for Apple and then moved to Microsoft after leaving PARC. Alan Kay went to Atari from PARC, then to Apple, then to Disney, and is now president of the Viewpoints Research Institute and an adjunct professor of computer science at UCLA. John Elenby left Xerox to form Grid, one of the earliest makers of laptop computers, then pioneered wireless networking at Agilis Technology until he and his two sons started GeoVector, a company that develops technology for hand-held devices.
PARC was a hotbed of research that advanced the science of computing. If you can find a copy of Dealers of Lightning (ISBN 0-88730-891-0), I think you'll find it a worthwhile read.
Lay In a Few Extra Hors D'œuvres!
What if you're planning to have a few friends over for your 15th birthday, but you accidentally make the Facebook invitation public? Very public. What happens is that instead of 15 RSVPs, you receive 21,000. Granted, most of the people won't really show up, but police in the teen's town have been notified and they'll be watching in October. What happened next borders on the absurd.
The girl who created the event listing on Facebook, instead of limiting the invitation to her 15 friends, accidentally made the event public. That immediately exposed her home address and telephone number to the world.
If you go, the birthday party is off. And police will be watching. And the girl won't be going near the Internet for a while. Her mother told the London Telegraph that her daughter "did not understand the privacy settings and she has lost her Internet as a result of that. (Emphasis mine.) I've taken away her computer," the girl's mother said, "so she won't make that mistake again."
Hey, mom! If your daughter doesn't understand something and makes a mistake, try using it as an opportunity to teach. All you're showing her by taking away her computer is that adults can be stupid and vindictive.
According to Facebook, when someone creates an event on Facebook it clearly says "anyone can view and RSVP (public event). If you leave this checked then it is a public event so anyone can view the content and respond."
Facebook has been criticized previously for overstepping the bounds of decency and it seems that now is a good time to repeat that criticism.
Hey, Facebook: Do you think you owe this girl an apology? Why don't you make messages such as this PRIVATE by default and allow users to create a WORLD-VIEWABLE EVENT only if they want to?
Or would that make too much sense?



 The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
The author's image: It's that photo over at the right. This explains why TechByter Worldwide was never on television, doesn't it?
